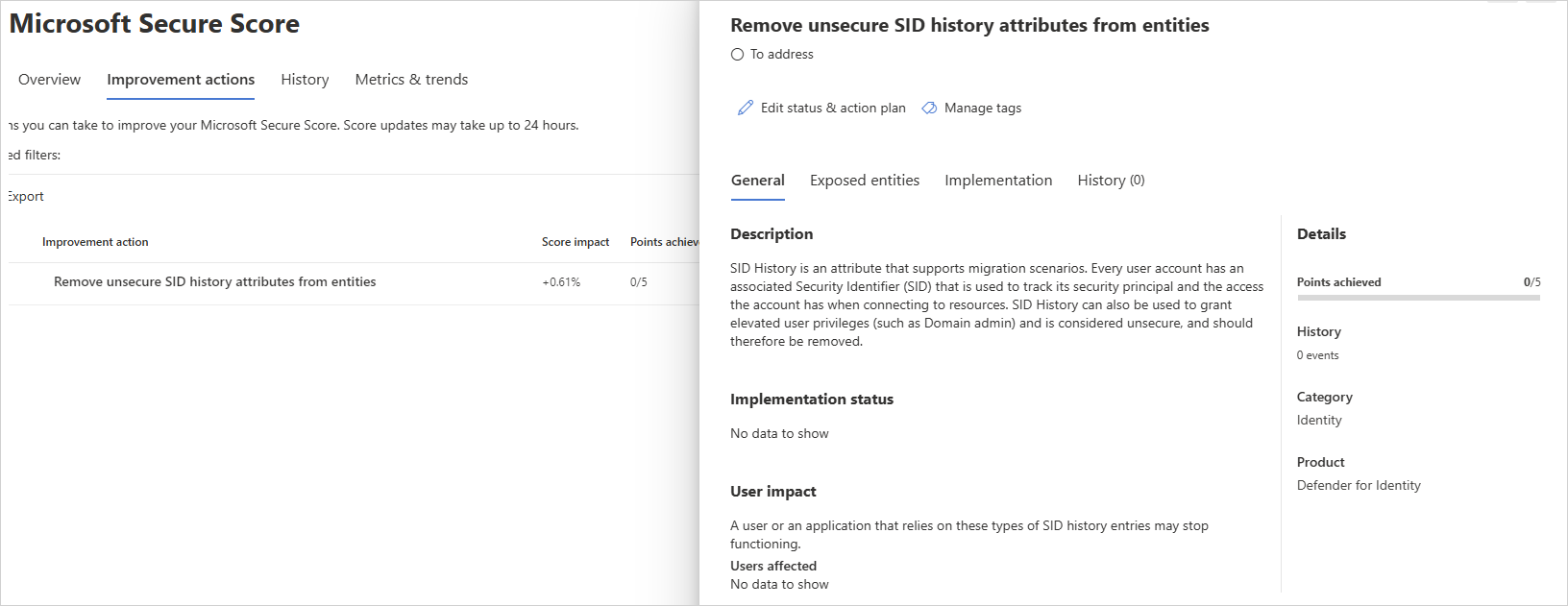
安全性評量:不安全的 SID 歷程記錄屬性
什麼是不安全的 SID 記錄屬性?
SID 歷程記錄是支援 移轉案例的屬性。 每個用戶帳戶都有相關聯 的安全性 IDentifier (SID) ,用來追蹤安全性主體以及帳戶連線到資源時的存取權。 SID 歷程記錄可讓另一個帳戶的存取權有效地複製到另一個帳戶,而且非常適合確保使用者在將 (從一個網域移轉) 到另一個網域時保留存取權。
評量會檢查具有 SID 歷程記錄屬性的帳戶,其 適用於身分識別的 Microsoft Defender 有風險的配置檔。
不安全的 SID 歷程記錄屬性會造成什麼風險?
無法保護其帳戶屬性的組織會讓惡意執行者的門解除鎖定。
惡意執行者很像垃圾,通常會在任何環境中尋找最簡單且最無訊息的方式。 使用不安全的 SID 歷程記錄屬性所設定的帳戶是攻擊者機會的視窗,而且可能會暴露風險。
例如,網域中的非敏感性帳戶在其 SID 歷程記錄中可以包含來自 Active Directory 樹系中另一個網域的企業 管理員 SID,因此會將用戶帳戶的存取權「提升」至樹系中所有網域中的有效網域 管理員。 此外,如果您有未啟用 SID 篩選的樹系信任, (也稱為隔離) ,則可以從另一個樹系插入 SID,並在驗證並用於存取評估時,將它新增至使用者令牌。
如何? 使用此安全性評估?
檢閱 中的建議動作 https://security.microsoft.com/securescore?viewid=actions ,以探索哪些帳戶具有不安全的 SID 歷程記錄屬性。
使用下列步驟,採取適當動作,從使用PowerShell的帳戶移除 SID 歷程記錄屬性:
識別帳戶上 SIDHistory 屬性中的 SID。
Get-ADUser -Identity <account> -Properties SidHistory | Select-Object -ExpandProperty SIDHistory使用稍早識別的 SID 移除 SIDHistory 屬性。
Set-ADUser -Identity <account> -Remove @{SIDHistory='S-1-5-21-...'}
注意事項
當評量以近乎即時的方式更新時,每隔 24 小時就會更新一次分數和狀態。 雖然受影響的實體清單會在您實作建議的幾分鐘內更新,但狀態可能需要一些時間,直到標示為已 完成為止。