角色定義是可以執行的許可權限集合,例如讀取、寫入和刪除。 它通常只稱為角色。 Azure 角色型訪問控制 (Azure RBAC) 有超過 120 個內建角色,或者您可以建立自己的自定義角色。 本文說明如何列出可用來授與 Azure 資源的存取權的內建和自定義角色。
若要查看Microsoft Entra標識符的系統管理員角色清單,請參閱 entra ID Microsoft 中的系統管理員角色許可權。
角色定義是可以執行的許可權限集合,例如讀取、寫入和刪除。 它通常只稱為角色。 Azure 角色型訪問控制 (Azure RBAC) 有超過 120 個內建角色,或者您可以建立自己的自定義角色。 本文說明如何列出可用來授與 Azure 資源的存取權的內建和自定義角色。
若要查看Microsoft Entra標識符的系統管理員角色清單,請參閱 entra ID Microsoft 中的系統管理員角色許可權。
請遵循下列步驟來列出 Azure 入口網站 中的所有角色。
在 Azure 入口網站 中,按兩下 [所有服務],然後選取任何範圍。 例如,您可以選取 [管理群組]、[訂用帳戶]、[資源群組]或資源。
按一下特定資源。
按一下 [存取控制 (IAM)]。
按一下 [角色] 索引標籤以查看所有內建與自訂角色清單。
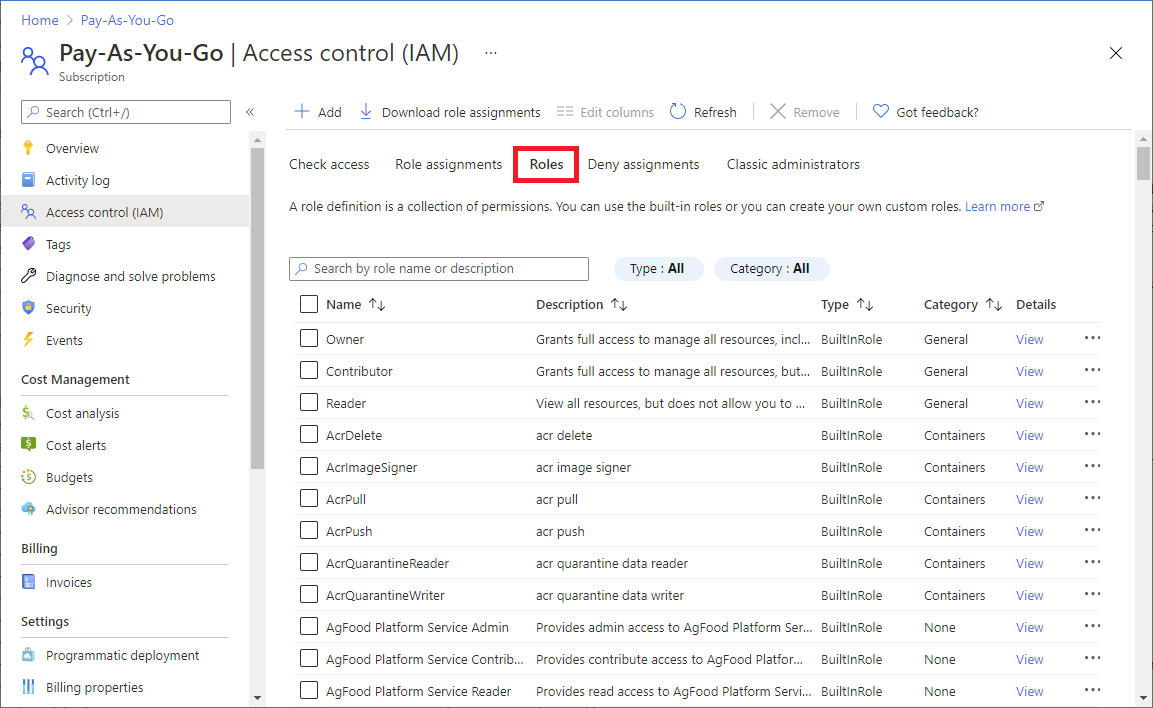
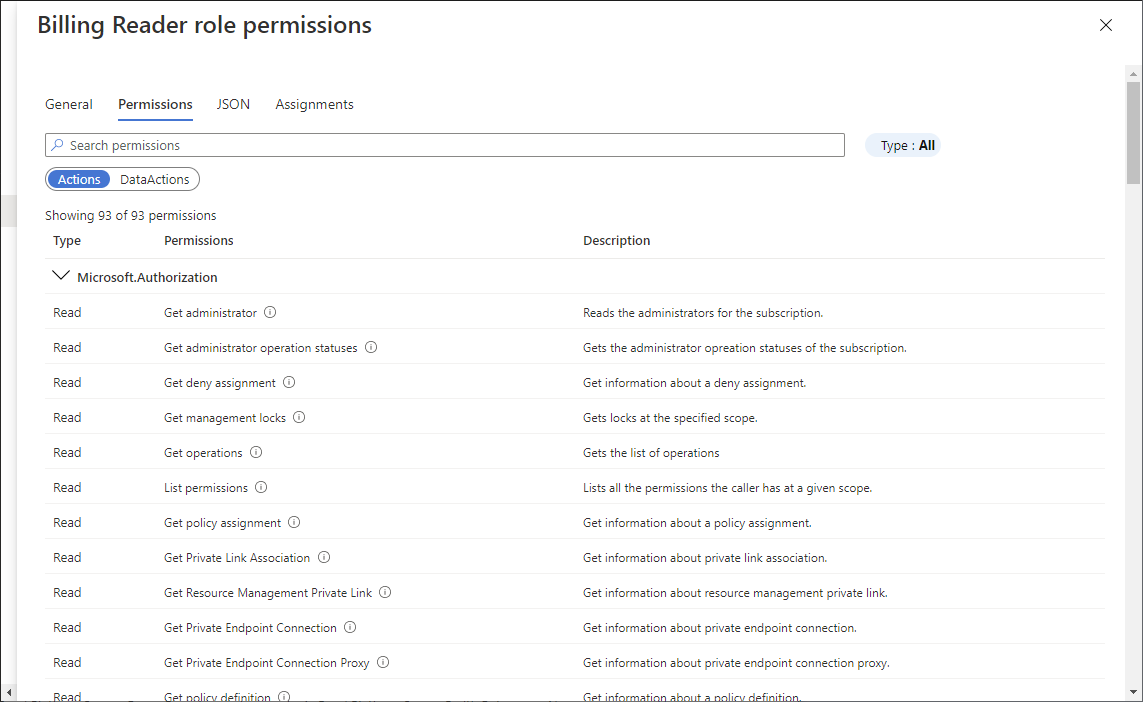
若要查看特定角色的許可權,請在 [詳細數據] 數據行中,按兩下 [檢視] 連結。
許可權窗格隨即出現。
按兩下 [ 許可權] 索引標籤,以檢視並搜尋所選角色的許可權。
若要列出 Azure PowerShell 中的所有角色,請使用 Get-AzRoleDefinition。
Get-AzRoleDefinition | FT Name, Description
AcrImageSigner acr image signer
AcrQuarantineReader acr quarantine data reader
AcrQuarantineWriter acr quarantine data writer
API Management Service Contributor Can manage service and the APIs
API Management Service Operator Role Can manage service but not the APIs
API Management Service Reader Role Read-only access to service and APIs
Application Insights Component Contributor Can manage Application Insights components
Application Insights Snapshot Debugger Gives user permission to use Application Insights Snapshot Debugge...
Automation Job Operator Create and Manage Jobs using Automation Runbooks.
Automation Operator Automation Operators are able to start, stop, suspend, and resume ...
...
若要列出特定角色的詳細數據,請使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name>
PS C:\> Get-AzRoleDefinition "Contributor"
Name : Contributor
Id : b24988ac-6180-42a0-ab88-20f7382dd24c
IsCustom : False
Description : Lets you manage everything except access to resources.
Actions : {*}
NotActions : {Microsoft.Authorization/*/Delete, Microsoft.Authorization/*/Write,
Microsoft.Authorization/elevateAccess/Action}
DataActions : {}
NotDataActions : {}
AssignableScopes : {/}
若要以 JSON 格式列出角色,請使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name> | ConvertTo-Json
PS C:\> Get-AzRoleDefinition "Contributor" | ConvertTo-Json
{
"Name": "Contributor",
"Id": "b24988ac-6180-42a0-ab88-20f7382dd24c",
"IsCustom": false,
"Description": "Lets you manage everything except access to resources.",
"Actions": [
"*"
],
"NotActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/"
]
}
若要列出特定角色的許可權,請使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name> | FL Actions, NotActions
PS C:\> Get-AzRoleDefinition "Contributor" | FL Actions, NotActions
Actions : {*}
NotActions : {Microsoft.Authorization/*/Delete, Microsoft.Authorization/*/Write,
Microsoft.Authorization/elevateAccess/Action,
Microsoft.Blueprint/blueprintAssignments/write...}
(Get-AzRoleDefinition <role_name>).Actions
PS C:\> (Get-AzRoleDefinition "Virtual Machine Contributor").Actions
Microsoft.Authorization/*/read
Microsoft.Compute/availabilitySets/*
Microsoft.Compute/locations/*
Microsoft.Compute/virtualMachines/*
Microsoft.Compute/virtualMachineScaleSets/*
Microsoft.DevTestLab/schedules/*
Microsoft.Insights/alertRules/*
Microsoft.Network/applicationGateways/backendAddressPools/join/action
Microsoft.Network/loadBalancers/backendAddressPools/join/action
...
若要列出 Azure CLI 中的所有角色,請使用 az role definition list。
az role definition list
下列範例會列出所有可用角色定義的名稱和描述:
az role definition list --output json --query '[].{roleName:roleName, description:description}'
[
{
"description": "Can manage service and the APIs",
"roleName": "API Management Service Contributor"
},
{
"description": "Can manage service but not the APIs",
"roleName": "API Management Service Operator Role"
},
{
"description": "Read-only access to service and APIs",
"roleName": "API Management Service Reader Role"
},
...
]
下列範例會列出所有內建角色。
az role definition list --custom-role-only false --output json --query '[].{roleName:roleName, description:description, roleType:roleType}'
[
{
"description": "Can manage service and the APIs",
"roleName": "API Management Service Contributor",
"roleType": "BuiltInRole"
},
{
"description": "Can manage service but not the APIs",
"roleName": "API Management Service Operator Role",
"roleType": "BuiltInRole"
},
{
"description": "Read-only access to service and APIs",
"roleName": "API Management Service Reader Role",
"roleType": "BuiltInRole"
},
...
]
若要列出角色的詳細數據,請使用 az role definition list。
az role definition list --name {roleName}
下列範例會列出 參與者 角色定義:
az role definition list --name "Contributor"
[
{
"assignableScopes": [
"/"
],
"description": "Lets you manage everything except access to resources.",
"id": "/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c",
"name": "b24988ac-6180-42a0-ab88-20f7382dd24c",
"permissions": [
{
"actions": [
"*"
],
"dataActions": [],
"notActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
],
"notDataActions": []
}
],
"roleName": "Contributor",
"roleType": "BuiltInRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
]
下列範例只會列出參與者角色的動作和 notActions。
az role definition list --name "Contributor" --output json --query '[].{actions:permissions[0].actions, notActions:permissions[0].notActions}'
[
{
"actions": [
"*"
],
"notActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
]
}
]
The following example lists just the actions of the Virtual Machine Contributor role.
az role definition list --name "Virtual Machine Contributor" --output json --query '[].permissions[0].actions'
[
[
"Microsoft.Authorization/*/read",
"Microsoft.Compute/availabilitySets/*",
"Microsoft.Compute/locations/*",
"Microsoft.Compute/virtualMachines/*",
"Microsoft.Compute/virtualMachineScaleSets/*",
"Microsoft.Compute/disks/write",
"Microsoft.Compute/disks/read",
"Microsoft.Compute/disks/delete",
"Microsoft.DevTestLab/schedules/*",
"Microsoft.Insights/alertRules/*",
"Microsoft.Network/applicationGateways/backendAddressPools/join/action",
"Microsoft.Network/loadBalancers/backendAddressPools/join/action",
...
"Microsoft.Storage/storageAccounts/listKeys/action",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Support/*"
]
]
您必須使用以下版本:
2015-07-01 (含) 以後版本如需詳細資訊,請參閱 Azure RBAC REST API 的 API 版本。
若要列出租使用者中的角色定義,請使用 角色定義 - 列出 REST API。
下列範例會列出租使用者中的所有角色定義:
要求
GET https://management.azure.com/providers/Microsoft.Authorization/roleDefinitions?api-version=2022-04-01
回應
{
"value": [
{
"properties": {
"roleName": "Billing Reader Plus",
"type": "CustomRole",
"description": "Read billing data and download invoices",
"assignableScopes": [
"/subscriptions/473a4f86-11e3-48cb-9358-e13c220a2f15"
],
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.Billing/*/read",
"Microsoft.Commerce/*/read",
"Microsoft.Consumption/*/read",
"Microsoft.Management/managementGroups/read",
"Microsoft.CostManagement/*/read",
"Microsoft.Billing/invoices/download/action",
"Microsoft.CostManagement/exports/*"
],
"notActions": [
"Microsoft.CostManagement/exports/delete"
],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "2021-05-22T21:57:23.5764138Z",
"updatedOn": "2021-05-22T21:57:23.5764138Z",
"createdBy": "68f66d4c-c0eb-4009-819b-e5315d677d70",
"updatedBy": "68f66d4c-c0eb-4009-819b-e5315d677d70"
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/17adabda-4bf1-4f4e-8c97-1f0cab6dea1c",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "17adabda-4bf1-4f4e-8c97-1f0cab6dea1c"
},
{
"properties": {
"roleName": "AcrPush",
"type": "BuiltInRole",
"description": "acr push",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"Microsoft.ContainerRegistry/registries/pull/read",
"Microsoft.ContainerRegistry/registries/push/write"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "2018-10-29T17:52:32.5201177Z",
"updatedOn": "2021-11-11T20:13:07.4993029Z",
"createdBy": null,
"updatedBy": null
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/8311e382-0749-4cb8-b61a-304f252e45ec",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "8311e382-0749-4cb8-b61a-304f252e45ec"
}
]
}
若要列出角色定義,請使用 角色定義 - 列出 REST API。 若要精簡您的結果,請指定範圍和選擇性篩選條件。
從下列要求著手:
GET https://management.azure.com/{scope}/providers/Microsoft.Authorization/roleDefinitions?$filter={$filter}&api-version=2022-04-01
針對租用戶層級範圍,您可以使用此要求:
GET https://management.azure.com/providers/Microsoft.Authorization/roleDefinitions?filter={$filter}&api-version=2022-04-01
在 URI 中,將 {scope} 取代為您要列出角色定義的範圍。
| 範圍 | 類型 |
|---|---|
providers/Microsoft.Management/managementGroups/{groupId1} |
管理群組 |
subscriptions/{subscriptionId1} |
訂用帳戶 |
subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1 |
資源群組 |
subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1 |
資源 |
在上一個範例中,microsoft.web 是參考 App Service 執行個體的資源提供者。 同樣地,您可以使用任何其他資源提供者並指定範圍。 如需詳細資訊,請參閱 Azure 資源提供者和類型以及支援的 Azure 資源提供者作業。
將 {filter} 取代為您想要套用以篩選角色定義清單的條件。
| 篩選 | 描述 |
|---|---|
$filter=type+eq+'{type}' |
列出指定型別的角色定義。 角色的類型可以是 CustomRole 或 BuiltInRole。 |
$filter=roleName+eq+'{roleName}' |
列出具有指定角色名稱的角色定義,例如「虛擬機參與者」。 |
下列範例會列出租使用者中的所有自定義角色:
要求
GET https://management.azure.com/providers/Microsoft.Authorization/roleDefinitions?$filter=type+eq+'CustomRole'&api-version=2022-04-01
回應
{
"value": [
{
"properties": {
"roleName": "Billing Reader Plus",
"type": "CustomRole",
"description": "Read billing data and download invoices",
"assignableScopes": [
"/subscriptions/473a4f86-11e3-48cb-9358-e13c220a2f15"
],
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.Billing/*/read",
"Microsoft.Commerce/*/read",
"Microsoft.Consumption/*/read",
"Microsoft.Management/managementGroups/read",
"Microsoft.CostManagement/*/read",
"Microsoft.Billing/invoices/download/action",
"Microsoft.CostManagement/exports/*"
],
"notActions": [
"Microsoft.CostManagement/exports/delete"
],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "2021-05-22T21:57:23.5764138Z",
"updatedOn": "2021-05-22T21:57:23.5764138Z",
"createdBy": "68f66d4c-c0eb-4009-819b-e5315d677d70",
"updatedBy": "68f66d4c-c0eb-4009-819b-e5315d677d70"
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/17adabda-4bf1-4f4e-8c97-1f0cab6dea1c",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "17adabda-4bf1-4f4e-8c97-1f0cab6dea1c"
}
]
}
若要列出特定角色的詳細數據,請使用 角色定義 - 取得 或 角色定義 - 依標識元 取得 REST API。
從下列要求著手:
GET https://management.azure.com/{scope}/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}?api-version=2022-04-01
針對租用戶層級角色定義,您可以使用此要求:
GET https://management.azure.com/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}?api-version=2022-04-01
在 URI 中,將 {scope} 取代為您要列出角色定義的範圍。
| 範圍 | 類型 |
|---|---|
providers/Microsoft.Management/managementGroups/{groupId1} |
管理群組 |
subscriptions/{subscriptionId1} |
訂用帳戶 |
subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1 |
資源群組 |
subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1 |
資源 |
將 {roleDefinitionId} 取代為角色定義標識符。
下列範例會列出 讀者 角色定義:
Request
GET https://management.azure.com/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7?api-version=2022-04-01
Response
{
"properties": {
"roleName": "Reader",
"type": "BuiltInRole",
"description": "View all resources, but does not allow you to make any changes.",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"*/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "2015-02-02T21:55:09.8806423Z",
"updatedOn": "2021-11-11T20:13:47.8628684Z",
"createdBy": null,
"updatedBy": null
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "acdd72a7-3385-48ef-bd42-f606fba81ae7"
}