轉換至 Microsoft Defender 弱點管理
適用於雲端的 Microsoft Defender 會統一所有弱點評估解決方案,以使用 Microsoft Defender 弱點管理 弱點掃描器。
Microsoft Defender 弱點管理會跨許多雲端原生使用案例整合,例如容器寄送和執行階段案例。
適用於雲端的 Defender 容器弱點評估 (由 Qualys 提供) 現已淘汰。 如果您尚未轉換至針對 Azure 使用 Microsoft Defender 弱點管理進行弱點評估,請遵循頁面上的步驟進行轉換。
步驟 1:確認掃描已啟用
針對適用於容器的 Defender、適用於容器登錄的 Defender 和 Defender 雲端安全性狀態管理,預設會啟用由 Microsoft Defender 弱點管理所提供的容器弱點評估掃描。 停用的組織必須重新啟用其中一個方案中的無代理程式容器弱點評估切換。 這會自動反映任何已啟用上述計劃。
如需啟用 Microsoft Defender 弱點管理掃描的詳細資訊,請參閱啟用由 Microsoft Defender 弱點管理所提供的弱點評估。
步驟 2:(選用) 更新 REST API 和 Azure Resource Graph 查詢
如果您透過 Azure Resource Graph (ARG) Rest API 或 Subassessment REST API 或 ARG 查詢,藉由 Qualys 以程式設計方式存取容器弱點評估結果,則必須更新現有的查詢,以符合新容器弱點評估 (由 Microsoft Defender 弱點管理提供) 所提供的新結構描述和/或 REST API。
下一節包含一些範例,可協助您了解 Qualys 支援供應項目的現有查詢應如何轉譯為與 Microsoft Defender 弱點管理所提供的對等查詢。
ARG 查詢範例
任何用於報告的 Azure Resource Graph 查詢都應該更新,以反映先前所列的 Microsoft Defender 弱點管理 assessmentKeys。 下列是協助您轉換至 Microsoft Defender 弱點管理查詢的範例。
顯示狀況不良的容器映像
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.status.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.displayName,
patchable = properties.additionalData.patchable,
cve = properties.additionalData.cve,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Unhealthy'
Microsoft Defender 弱點管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.additionalData.vulnerabilityDetails.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.description,
fixStatus = properties.additionalData.softwareDetails.fixStatus,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Unhealthy'
顯示健康狀況的容器映像
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Healthy'
Microsoft Defender 弱點管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Healthy'
依嚴重性計算易受攻擊的映像
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend status = tostring(parse_json(properties).status.code)
| extend severity = tostring(parse_json(properties).status.severity)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
Microsoft Defender 弱點管理
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend severity = tostring(properties.additionalData.vulnerabilityDetails.severity)
| extend status = tostring(parse_json(properties).status.code)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
檢視 AKS 叢集上執行中易受攻擊映像的 Pod、容器和命名空間
Qualys
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id),
subAssessmentId = tostring(properties.id),
parentResourceId = extract("(.+)/providers/Microsoft.Security", 1, id)
| extend resourceId = extract(@'(?i)(.*?)@([^/]+)', 1,tostring(properties.resourceDetails.id))
| extend severity = tostring(parse_json(properties).status.severity)
| extend VulnId = tostring(parse_json(properties).id)
| extend status = tostring(parse_json(properties).status.code)
| where assessmentKey == "41503391-efa5-47ee-9282-4eff6131462c"
| extend resourceId = tostring(properties.resourceDetails.id),
parsedJson = parse_json(tostring(properties.additionalData))
| extend containerData = parse_json(tostring(parsedJson.data.Containers))
| mv-expand containerDetails = containerData to typeof(dynamic)
| extend ContainerName = tostring(containerDetails.Name),
ContainerPod = tostring(containerDetails.Pod.Name),
Namespace = tostring(containerDetails.Pod.Namespace),
ControllerType = tostring(containerDetails.Pod.ControllerType),
ControllerName = tostring(containerDetails.Pod.ControllerName)
| where status == 'Unhealthy'
|project Image=resourceId, VulnId,severity, Namespace, ContainerName, ContainerPod,ControllerName,ControllerType
Microsoft Defender 弱點管理
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| extend azureClusterId = tostring(properties.additionalData.clusterDetails.clusterResourceId)
| extend cve =tostring(properties.id)
| extend status = properties.status.code
| extend severity=tostring(parse_json(properties).additionalData.vulnerabilityDetails.severity)
| where status == "Unhealthy"
| extend azureImageId = tostring(properties.resourceDetails.id)
| extend severity = tolower(properties.additionalData.vulnerabilityDetails.severity)
| extend kubernetesContext = properties.additionalData.kubernetesContext
| mv-expand workload = kubernetesContext.workloads
| mv-expand OwnedResource = workload.ownedResources
| mv-expand OwnedContainer = OwnedResource.containers
| mv-expand Container = workload.containers
| extend isController = isnotempty(workload.ownedResources)
| extend namespace = tostring(workload.namespace)
| extend podName = iff(isController, tostring(OwnedResource.name), workload.name)
| extend containerName = iff(isController, tostring(OwnedContainer.name), Container.name)
| extend controllerName = iff(isController, tostring(workload.name),"")
| extend controllerType = iff(isController, tostring(workload.kind),"")
| extend imageName = extract("(.+)@sha256:", 1, azureImageId)
| project imageName, cve, severity, clusterId = azureClusterId, containerName, podName, controllerName, controllerType, namespace
步驟 3:(選用) 容器安全性報告
適用於雲端的 Microsoft Defender 透過 Azure 活頁簿提供現成的報告,包括容器安全性活頁簿。
此活頁簿包含來自登錄和執行階段的容器弱點掃描結果。
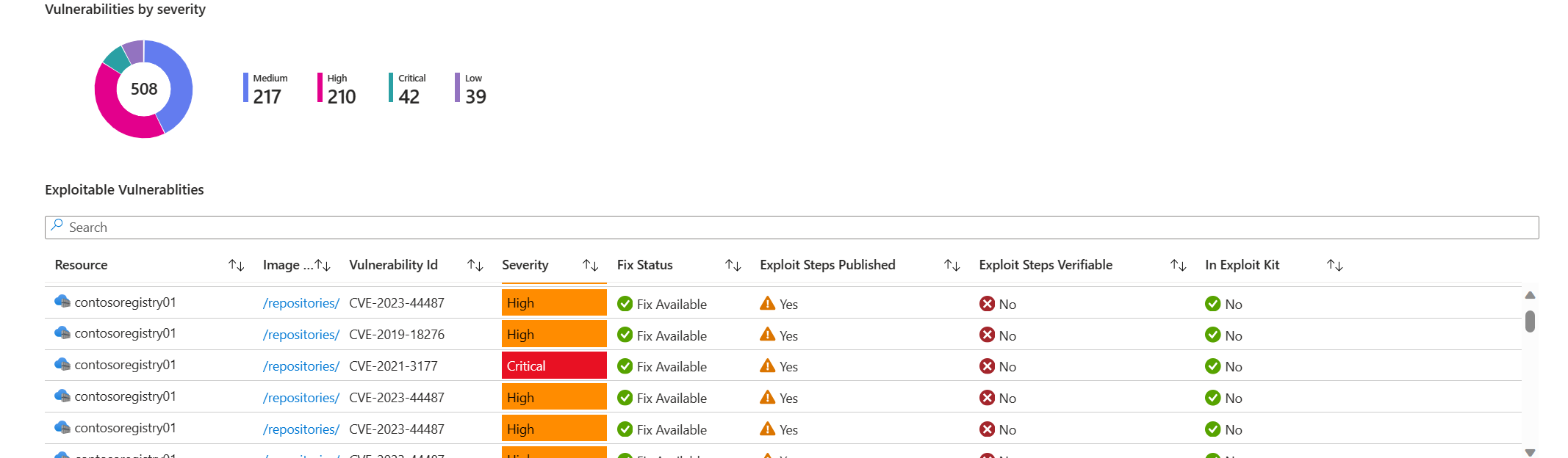
活頁簿提供來自 Microsoft Defender 弱點管理掃描的結果,提供 Azure 登錄容器映像內所偵測到弱點的全面概觀。 容器安全性活頁簿提供下列容器弱點評估的優點:
所有弱點概觀:檢視在 Azure 容器登錄中偵測到的所有弱點,並在 AKS 叢集上執行。
惡意探索弱點儀表板:專用區段,強調已知惡意探索的弱點,讓安全性小組能夠專注於有高風險惡意探索的弱點。 僅搭配由 Microsoft Defender 弱點管理所提供的容器弱點評量的掃描可用。
其他 ARG 查詢:您可以使用此活頁簿來檢視更多範例,了解如何查詢 Qualys 與 Microsoft Defender 弱點管理之間的 ARG 資料。 如需如何編輯活頁簿的詳細資訊,請參閱適用於雲端的 Microsoft Defender 中的活頁簿資源庫。
![在設定中啟用 [無代理程式容器弱點評估] 的螢幕擷取畫面。](media/transition-to-defender-vulnerability-management/enable-agentless-container-vulnerability-assessment.png)