All About "Application Locked"
I have been working on this post slowly for several days, but Reed and Steve are seriously kicking my butt on posting solid developer-focused technical security content. Read their blog - they covered a lot of this material sooner and better than I did.
Some non-touchscreen Windows Mobile devices ship with a set of security policies that prevents developers from adding their own codesigning certificates. I don't know of any touchscreen devices that ship like that - it's possible to configure those devices to be locked down but none ship like that by default as far as I know. For some of these devices, it's possible to tweak the security policies via supported methods so you can install development certs,debug, and develop privileged applications. Internally we call this "the user is manager" meaning that the user has the ability to freely modify any software setting on the phone. In this post I'll describe how to figure out the security policies on your device and how to figure out if you are "application locked" or not.
For this post I'll assume that the end goal is to get the SDK certificates (sdkcerts.cab) installed on the phone. Once you've done that, you can run the remote registry editor from the SDK, develop and sign your own programs and do whatever you want.
Try This First
Let me get to the point first - I'd recommend two things, in order of likelihood of success
- Use the Device Security Manager. It has a great facility for inspecting the security policies and cert stores of a connected device, and even has a menu option to install the SDK certs for you.
- Try installing the unsigned sdkcerts.cab on the device. There are a few cases where the Security Manager tool errs on the side of caution and tells you that you can't install the certs, but they will really work via unsigned cab. I'll describe this case below.
If either of those work, the SDK certs are installed and you can now develop, change security policies, do whatever you want.
Local security policies
There are several security policies that come into play here. To install the SDK certs you need the highest level of trust on the device. (manager)
Unsigned CAB policy: If policy is set to 0, then unsigned CABs won't install. The typical role is User Auth which means the CABs will install but they have a similar set of privileges as code running at the Normal level. If this policy is set to Manager, then the unsigned CABs have all privileges, and you can use the unsigned cab technique to change any setting.
Two-tier security policy: If this is set to "One-tier" then CAB files and programs have the ability to change any setting on the device. Some smartphone devices ship in one-tier mode. Those phones are definitely not application locked - you can use the unsigned cab technique to apply any setting.
Grant Manager policy: This policy contains a list of roles that are elevated to manager. If this role contains "User Auth" then every action taken by the user has full administative access. Installing the setup XML from a cab file counts as one of those actions, so if grant manager contains User Auth, you can again use the unsigned cab technique to change any setting.
RAPI security policy: I think it's pretty uncommon for this policy to be open when the previous policies are be locked down, but if this policy is set to Open (2) then all of the API calls over Activesync are processed as trusted/manager, so you'll be able to change any setting or security policy using RAPI.
Inspecting security policies with the Device Security Manager
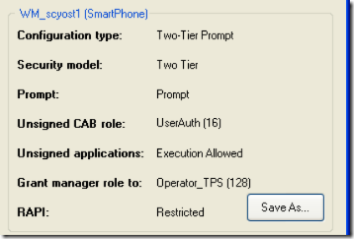
Here's the default configuration for a Windows Mobile "Standard" non-touch-screen device. All of the security policies mentioned above are in their restricted state. You won't be able to install the SDK certs onto a phone like this. It is possible to run unsigned untrusted code, so you can write some classes of apps, but the development and debugging experience is not great. The Device Security Manager will tell you that it can't install the SDK certs on a device like this. This is typically what most people mean when they say "Application Locked".
Here's another possible configuration. On this phone, the Grant Manager policy is set to "User Auth". This means that an unsigned cab will install with full privilege, after the prompt. The Device Security Manager still thinks this phone is locked down, so you'll need to install the unsigned cab by hand.
For a default Windows Mobile 6 SDK install, the SDKCerts cab is located at "C:\Program Files\Windows Mobile 6 SDK\Tools\Security\SDK Development Certificates\Certs.cab". Copy this CAB to a device configured like the above, and it will successfully install. Once the SDK certs are installed, you can write your own programs and use all the development tools that ship with the SDK.
Comments
Anonymous
May 30, 2007
so short of using the unlocking app that is floating around, how do you remove the app lock?Anonymous
June 01, 2007
If the device is configured like the "locked" state again then that was the choice of the mobile operator or OEM. If there were a way to circumvent the policy I wouldn't be able to discuss it here anyway.Anonymous
June 01, 2007
There is a debate going on several fora on whether WM5 can be upgarded to WM6 on motorala q phones: http://www.everythingq.com/forum/software/upgrading-wm-5-wm-6-moto-q-8031.html#post50941 Can you guys comment anonymously if such an upgrade is doable?Anonymous
June 01, 2007
Sorry, that paragraph refers to the location of the CAB when you have installed the SDK on a desktop machine. It has nothing to do with an install of a new operating system on the device.Anonymous
June 08, 2007
The comment has been removedAnonymous
June 09, 2007
i used this to application unlock my spv e650 but once i clicked provision it said ur device is two-tier and to contact the mobile provider, i wish i had got the vox instead of the spv, as ive heard application unlock on that is a lot easier....Anonymous
July 04, 2007
Hi. Can you help me please with a provisioning problem on Windows Mobile 6? I tried to send a NET setting on HTC S710 and the phone can't recieve the setting. If I send the setting with RapiConfig, then the setting is saved correctly. If I sent on my old HTC Excalibur this setting it worked fine. Do you know which security policie values have to modify to be able to provisioning the phone under Windows Mobile 6? (I allready modified the 4097, 4101,4102, 4119, 4122, 4123 values but nothing changed :( ) Thx. Frida (fridahauler@vipmail.hu)Anonymous
September 03, 2007
Frida - you could connect your device to Visual Studio "Orcas" and open Device Security Manager (if you don't have Visual Studio installed, you could use the powertoy available separately for download) and check what configuration your phone currently has. Using the same Device Security Manager, you can provision your phone to allow CABs to get installed. AarthiAnonymous
October 18, 2007
how do i unlock the wing.its asking for password.but i found the phone.please someone helpAnonymous
February 19, 2008
I found a wing a couple of months ago and it is password protected. I just had a friend who now has a charger that works with it. How do I unlock the phone?Anonymous
February 27, 2008
Wraz z systemami Windows Mobile 5.0 i Windows Mobile 6 wprowadzono nowych model zabezpieczeń (securityAnonymous
March 17, 2008
I am very disappointed at you to choose this kind of security model. It makes things hard for consumers to get any application running on their phones and it's actually just all about business and purchasing certificates that would allow the applications to run in the system. I have to say that i regret buying Windows Mobile. I wish i had known that when it comes to Microsoft it will never work.