Using the Dictionary for Fun and Profit
In my previous post, I discussed using the new Attack Simulator for crafting phishing campaigns against your users. If you haven't tried it out yet, I'd heartily recommend it. It's more fun than a barrel of monkeys.
For this post, we're going to shift into slightly more traditional attack strategies. Another one of the features in the new attack simulator is running a dictionary or wordlist attack against your user accounts. While this is nothing new in the on-premises world when using tools supplied by third party vendors, this is somewhat of a new territory for us.
Setup
Like the other attacks, this one requires you to be running it from an account with multifactor access enabled. If you haven't done so already, you'll need to configure it. You can check out this link for our support article on configuring it from the Admin Portal, or, from a PowerShell session, run this quick chunk of code:
$auth = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$auth.RelyingParty = "*"
$auth.State = "Enabled"
$auth.RememberDevicesNotIssuedBefore = (Get-Date)
Set-MsolUser -UserPrincipalName <youraccount@tenant.onmicrosoft.com> -StrongAuthenticationRequirements $auth
Once you've got your multifactor auth, you'll also need to make sure you've clicked the Setup Now link on the Threat Management | Attack Simulator page to activate it in your tenant:

After both of those prerequisites are met, you are ready to get cracking, both literally and figuratively.
Launching a Brute Force Dictionary Attack
Dictionary attacks (sometimes known as word list attacks) try every word in a large list of common words or passwords against a set of users. In this example, I'm using a trimmed down word list I found on the internet. In my testing, it looks like the service can process about 1,765 passwords (19kb file).
- From the Threat Management | Attack Simulator page, under the Brute Force Password (Dictionary Attack) section, click the Launch Attack button.
- Name your attack, and then click Next.
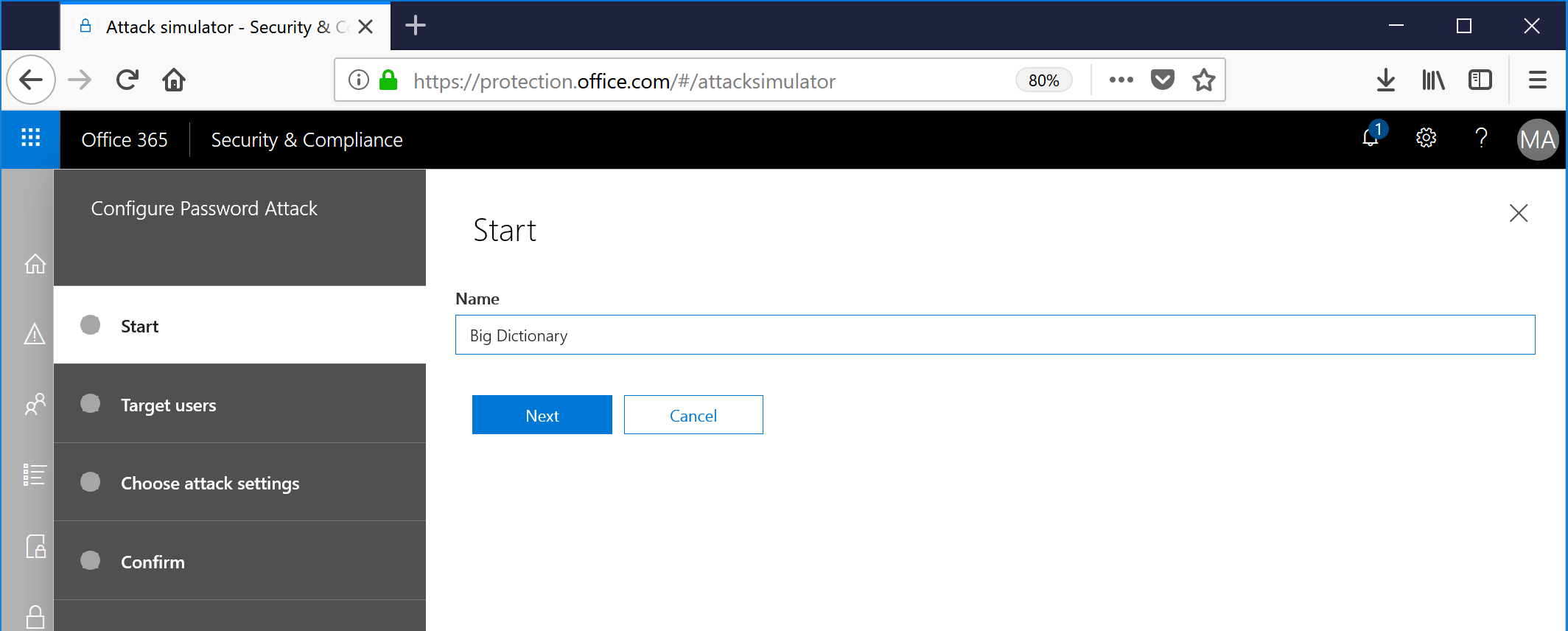
- Select users to try the attack against. In this case, I just want to test a single user with my ginormous word list. After your users and groups have been selected, click Next.
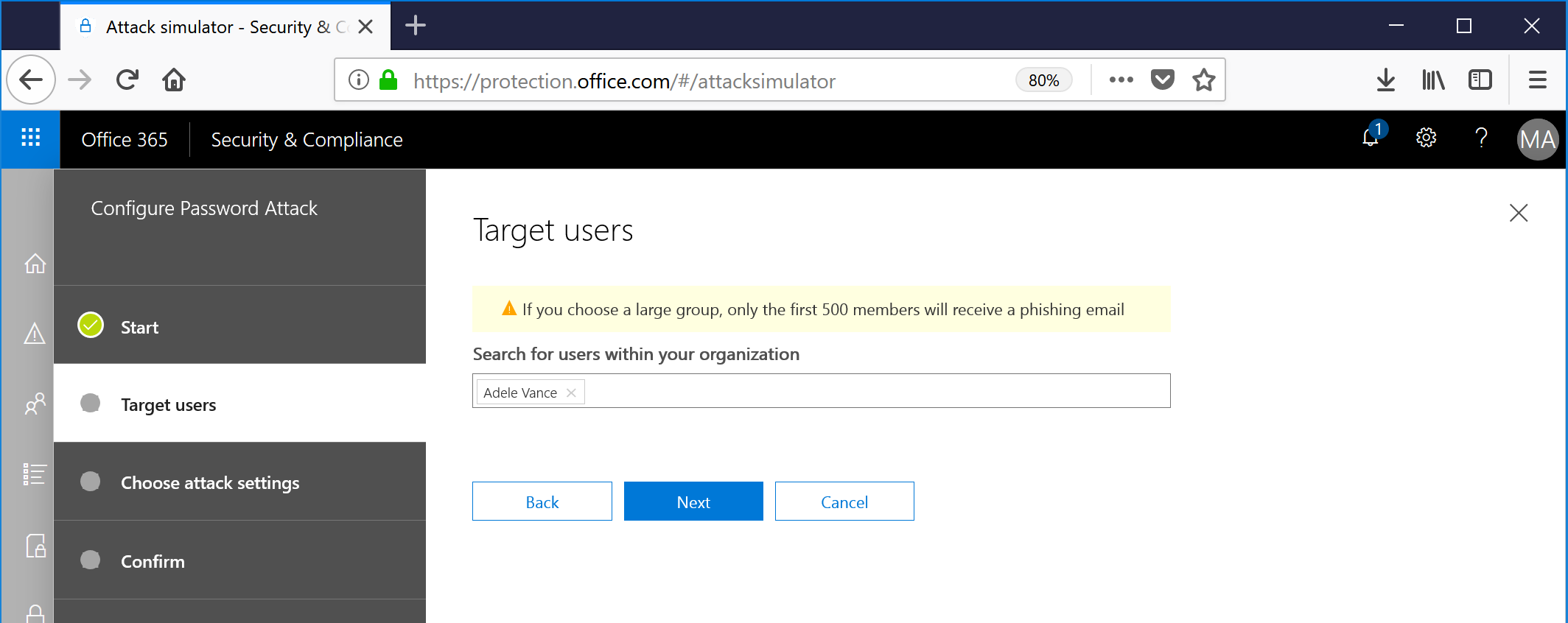
- Click Upload to browse to the dictionary or word list text file. The text file should be formatted so that it has one entry per line. Click next after the upload has completed.
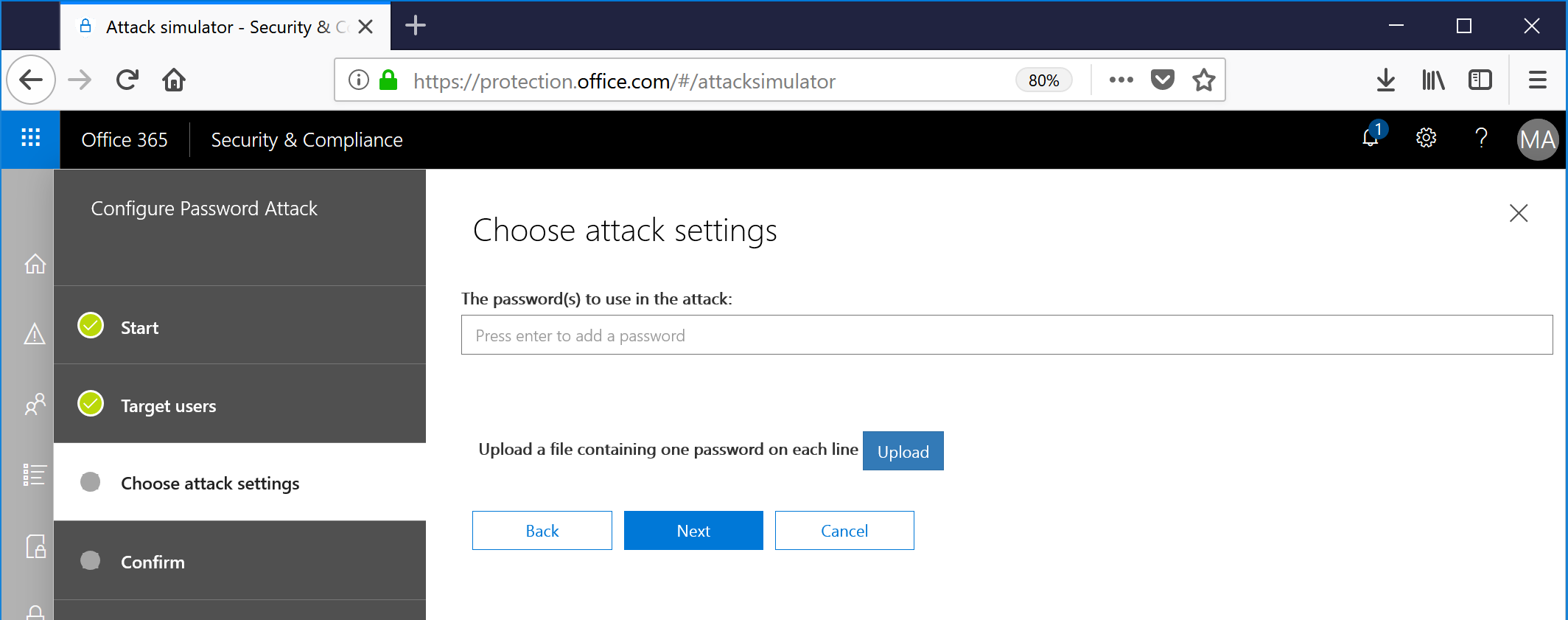
- Navigate back to Threat management | Attack Simulator, and then select View Report to view the completed report.
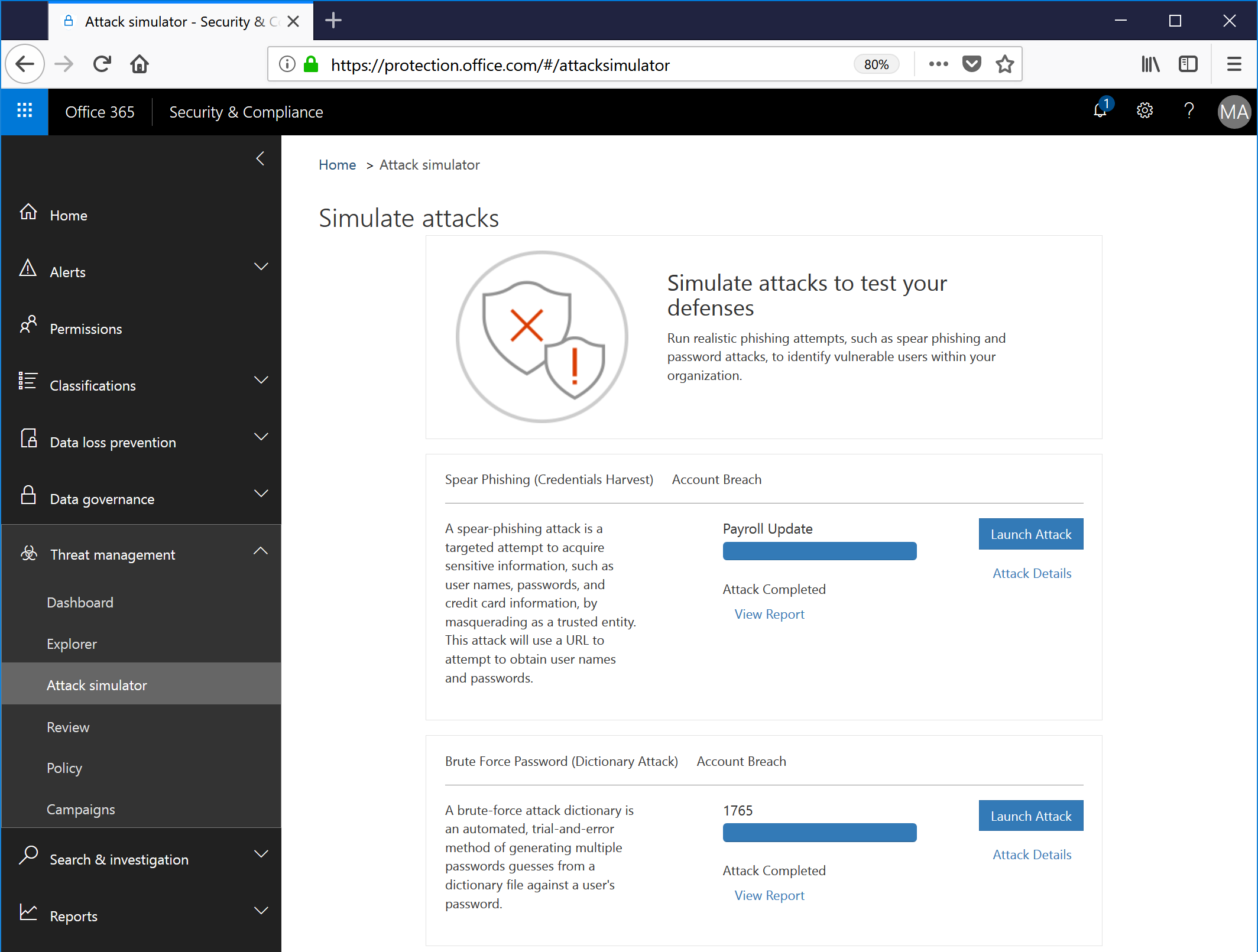
- The report page will show any compromised accounts. Note: Only the accounts for which passwords attempts were successful are displayed; the matching password is not.
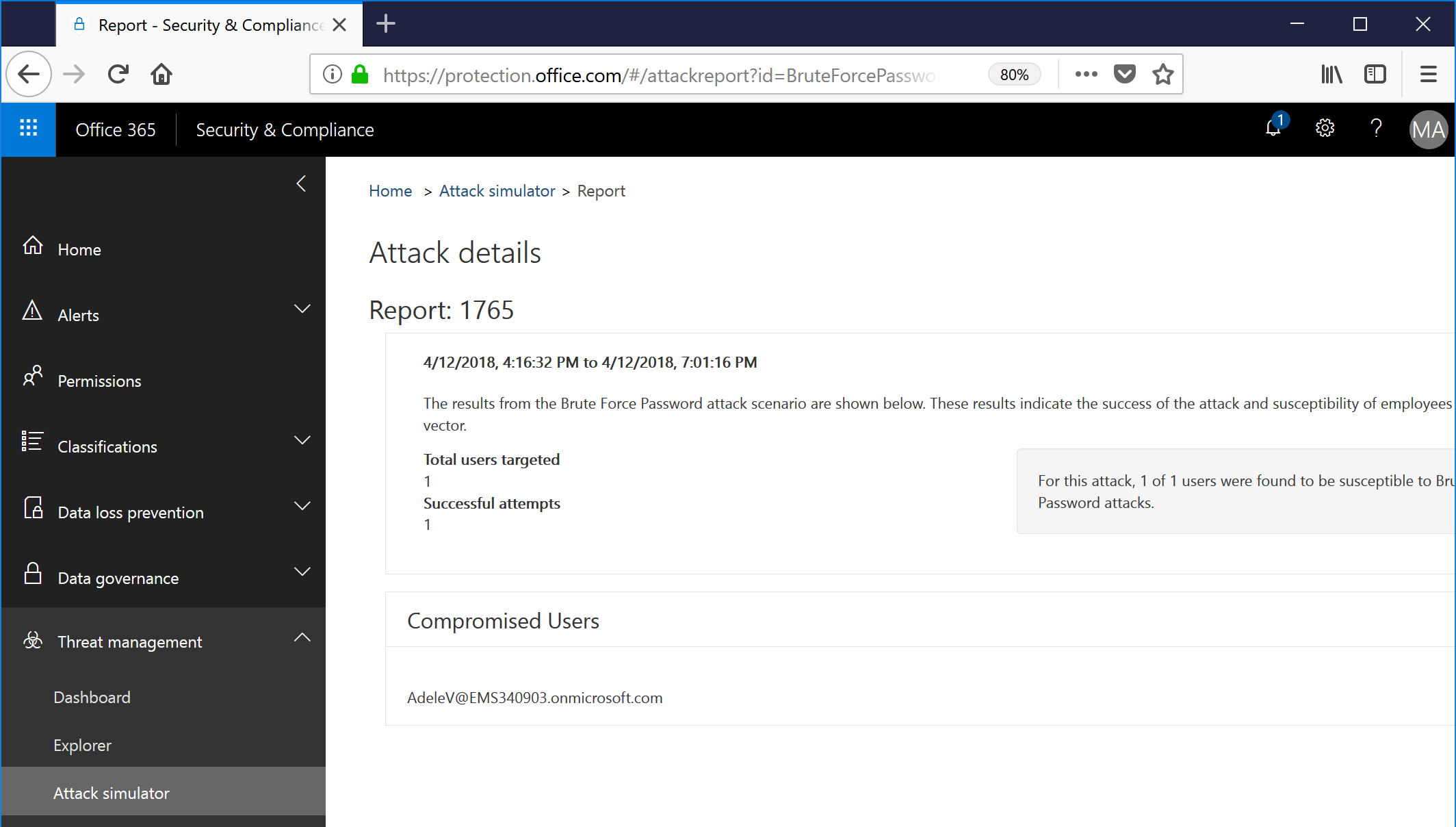
Crack on!
Comments
- Anonymous
August 23, 2018
The comment has been removed- Anonymous
August 23, 2018
Are you selecting the Dictionary Attack or the password spray?
- Anonymous