Updating passwords on SharePoint 2010
Today’s entry in the “Sean’s simple question about why a KB article had not been updated leads to a lot of research and learning” post is courtesy of managed accounts and password changes with SharePoint 2010.
History
With SharePoint 2007, instructions on changing service accounts and passwords could be found in the appropriately named KB article:
The steps in the KB article would walk you through the individual STSADM commands that were necessary to update the password for the following accounts on every server in the SharePoint Farm:
- Farm account
- Application pool account(s)
- Windows SharePoint Services Help Search Service
- Content access account (used by the Windows SharePoint Services Help Search Service)
- Shared Services Provider (SSP) account(s)
- Office SharePoint Server Search service
Other accounts had to be changed from within Central Administration:
- Microsoft single sign-on password
- Default Content Access account used by the Office SharePoint Server Search service
- Content Access accounts used by crawl rules
The KB article included a sample script that could be used to automate password changes; combining the given stsadm commands into a batch script that accepted a username and password as input parameters. The script assumed that all services on the farm were running with the same domain account, which may be a standard configuration for a standalone development server, but is not realistic in a production SharePoint Farm. As there was no centralized management and deployment of passwords across a SharePoint 2007, the password updates for service accounts had to be entered on every server in the SharePoint farm.
Imagine a scenario where a SharePoint Administrator is asked to improve security and ensure application isolation so that all web applications and services running on the farm machines are using different domain accounts (for a total of 10 accounts, used across 5 separate servers in the SharePoint farm). In this scenario with SharePoint 2007, password changes required the SharePoint Administrator to:
- Reset the password for each service account in Active Directory
- Store the passwords for each service account (ideally long, random, secure passwords) in an accessible but secure location
- Manually update the password for each service account on each server.
In this scenario, with 10 accounts to be updated on 5 servers, there are 50 passwords that need to be updated with STSADM or through Central Administration. This required a significant amount of manual work, and was prone to human error in entering the STSADM commands required. As a result, it was tempting for SharePoint administrators to check the “password does not expire” box for the service accounts in Active Directory (which is a bad idea from a security perspective), or to use a single Active Directory account for all services running on the SharePoint farm. Neither option is a good idea from a security or isolation perspective.
A Better Way
There is not a SharePoint 2010 equivalent to the “How to change service accounts and service account passwords in SharePoint Server 2007 and in Windows SharePoint Services 3.0” article, due to some significant improvements that have been introduced to allow service accounts and passwords to be easily managed in SharePoint farms of all sizes. In short, assuming all SharePoint service accounts for a SharePoint 2010 farm are using a single account, the entire script from the KB article could be replicated with the following Windows PowerShell command:
Set-SPManagedAccount –Identity domain\user –NewPassword “password”.
Benefits of Managed Accounts
- Managed accounts (mapped to one or many services as above) can have their passwords updated from a single location, and have the changes rolled out to all servers in the farm that use that managed account
- Password changes can be scheduled to automatically take place, either according to a schedule, or based on the password expiry policy set in Active Directory.
- SharePoint can generate very long, cryptographically random passwords for all accounts
Note: Windows Server 2008 R2 includes managed accounts at the operating system level. Do not use Windows Server 2008 R2 managed accounts for managing SharePoint accounts. They are not compatible with SharePoint Server managed accounts. Although the concept is similar, SharePoint has no way of knowing when a password has been changed for an account managed by Windows Server 2008 R2, and will not roll the password change to all servers in the farm.
Using Managed Accounts
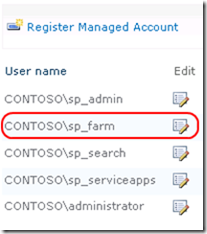
Managed Accounts on SharePoint 2010 can be mapped to one, many, or all of the following on SharePoint 2010:
- Farm Account
- Windows Services used by SharePoint
- Web Applications
- Service Application Pools
The following screenshot shows an example of accounts that would be mapped to managed accounts on a typical SharePoint 2010 farm.
Passwords for the following cannot be mapped to managed accounts, and must be manually changed when necessary:
- SQL Server services (which should be changed from within SQL Server Configuration Manager. Read more in the following MSDN article: SQL Server Configuration Manager)
- The default content access account, or any content access accounts used with SharePoint Search crawl rules
- Credentials that are used to access external data sources and are stored in the Secure Store service application. (See Configure the Secure Store Service (SharePoint Server 2010) for more information about how to change credentials to access external data sources.)
Configuring New Managed Accounts
The steps to configure managed accounts and automatic password changes can be found in the TechNet article: Configure automatic password change (SharePoint Server 2010):
To configure managed account settings by using Central Administration
1. Verify that the user account that is performing this procedure is a member of the Farm Administrators SharePoint group.
2. On the Central Administration Web site, select Security.
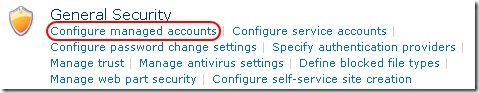
3. Under General Security, click Configure managed accounts.
4. On the Managed Accounts page, click Register Managed Account.
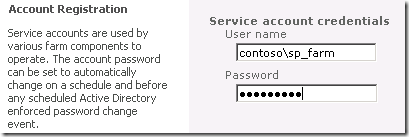
5. In the Account Registration section of the Register Managed Account page, enter the service account credentials.
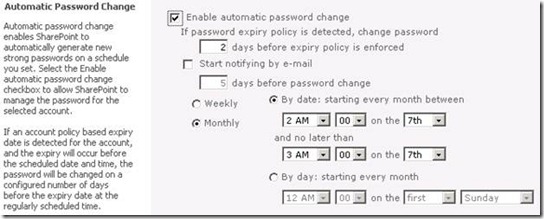
6. In the Automatic Password Change section, select the Enable automatic password change check box to allow SharePoint Server 2010 to manage the password for the selected account. Next, enter a numeric value that indicates the number of days prior to password expiration that the automatic password change process will be initiated.
7. In the Automatic Password Change section, select the Start notifying by e-mail check box, and then enter a numeric value that indicates the number of days prior to the initiation of the automatic password change process that an e-mail notification will be sent. You can then configure a weekly or monthly e-mail notification schedule.
8. Click OK.
Mapping Managed Accounts to Service Accounts
1. Verify that the user account that is performing this procedure is a member of the Farm Administrators SharePoint group.
2. On the Central Administration home page, click Security, and then in the General Security section, click Configure service accounts.
3. On the Service Accounts page, in the Credential Management section, in the upper drop-down list, click the service for which you want to update credentials.
4. In the Select an account for this component list, click the domain account that you want to associate with this service.
5. If you want to register the account that you selected on the SharePoint Server 2010 farm, click Register Managed Account.
6. Click OK.
Credential Management
Once managed accounts have been registered and mapped to services, there are four ways to update the password. Automatic Password Change was discussed in the Configuring New Managed Accounts section above, and now we will discuss:
- Generating a new (long and cryptographically random) password
- Setting the account password to a new value
- Updating the account password in SharePoint if it has been changed elsewhere (such as directly in Active Directory)
To configure managed account settings by using Central Administration
1) Verify that the user account that is performing this procedure is a member of the Farm Administrators SharePoint group.
2) On the Central Administration Web site, select Security.
3) Under General Security, click Configure managed accounts.
4) Click the Edit button next to the account that you want to change.
In the Credential Management section of the resulting page, there are 3 options:
If the Change password now checkbox is checked, then additional controls in the section are enabled which can be used to select of one of three password change mechanisms outlined below:
Generate new password
If the administrator wants the password changed to an automatically generated password, the “generate new password” option will immediately initiate the password creation and roll process upon page submit.
Set account password to new value
If the administrator wants to manually change the service password to a specific value, selecting the “set account password to new value” option and then entering the password will immediately initiate the password change process using the specified service account password upon page submit.
Use existing password
If the administrator has already manually changed the service password, selecting the “use existing password” option and then entering the password will immediately initiate the password roll process using the specified service account password upon page submit.
Common Error
Many organizations have the “Minimum password age” password policy set to a value greater than 1.
As discussed in the TechNet Article Enforcing Strong Password Usage Throughout Your Organization
Minimum password age determines how many days a user must keep new passwords before they can change them. This setting is designed to work with the Enforce password history setting so that users cannot quickly reset their passwords the required number of times and then change back to their old passwords. The value of this setting can be between 0 and 999; if it is set to 0, users can immediately change new passwords. The Microsoft recommendation for this value is 2 days.
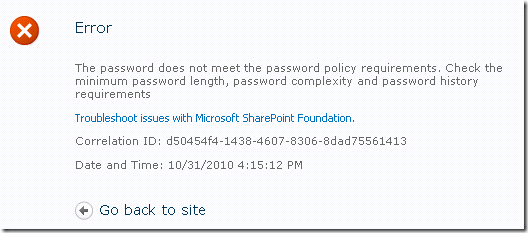
If a password already been changed in Active Directory, updating the managed account value under “Set account password to new value” section will often trigger the following error. This is due to the fact that SharePoint is attempting to update a password that has already been updated within the “Minimum password age” policy.
Error: The password does not meet the password policy requirements. Check the minimum password length, password complexity and password history requirements.
The solution to this problem is enter the updated password in the “Use existing password” section of Credential Management.
Account Information
Directly underneath the Automatic Password Management section of the Managed Account page is Account Information. The account information section displays information about the last and next password change and the list of farm components currently mapped to this managed account.
Removing Managed Accounts
The managed account can be removed only if no items are set to use the account within the farm. When an administrator chooses to remove a managed account, they will be presented with the Remove Managed Account page. The administrator has the option of changing the password before removing the account in order set it to a known value. This page does not actually delete an account in active directory or on the local machine, but it instead only allows an existing account to be removed from registration in the SharePoint farm.
If you attempt to remove a managed account that is still mapped to a SharePoint component, you will receive an error like the following. In order to remove the managed account, you must unmap the managed account from any associated services.
Managing Managed Accounts with Windows PowerShell
<note: The samples below are courtesy of my non-developer brain. While they work fine for me, they may eat all the cookies in your house, erase your SharePoint farm, or date your girlfriend behind your back. They probably need to be modified to work in your environment, and appropriate caution should be exercised before copying and pasting code from any website, especially anything written by me. The scripts below and require you to manually enter the domain\user of the managed account. If there is someone that knows Powershell better than me, it would be nice to have the script to run get-SPManagedAccount, pipe the results to a screen allowing you to choose the account, rather than having to manually type it in, and then loop at the end to ask if there are any more accounts you would like to change the password for. If you figure out how to do that, please post the solution in the comments!>
Managed Accounts can be created, removed, and updated with Windows PowerShell, using the following cmdlets. I have provided some samples of managed account credential management, which can be tweaked to fit your situation. The TechNet reference for the Windows PowerShell cmdlets are available at the following links:
Note: the sample scripts below must be run from the SharePoint 2010 Management Shell (which adds the SharePoint cmdlets to Windows PowerShell). From your Start menu select “SharePoint 2010 Management Shell” or Start, “Microsoft SharePoint 2010 Products”, “SharePoint 2010 Management Shell”.
If running Windows PowerShell natively, the following lines should be added to the beginning of the script:
$ver = $host | select version
if ($ver.Version.Major -gt 1) {$Host.Runspace.ThreadOptions = "ReuseThread"}
Add-PsSnapin Microsoft.SharePoint.PowerShell
Set-location $home
Set a new password for Managed Account
#Input the Managed Account
#If there is only one managed account, the following line could be written as:
#$inputManagedAcct = Get-SPManagedAccount
$inputManagedAcct = Read-Host "Enter managed account as Domain\User"
#Input the desired new password
$inputPasswd = Read-Host "Enter new password for managed account" –AsSecureString
#Change the password for the managed account to the new value
Set-SPManagedAccount -Identity $inputManagedAcct -NewPassword $inputPasswd
To update the account password to a new automatically generated value, from the Windows PowerShell command prompt, type the following:
Set-SPManagedAccount –Identity domain\user -AutoGeneratePassword $true
Update the password for a Managed Account that has already been reset through Active Directory
If the password for a managed service account has been manually changed outside of SharePoint (such as directly in Active Directory), you can update the password to the new value in SharePoint 2010 as follows
#Input the Managed Account
#If there is only one managed account, the following line could be written as:
#$inputManagedAcct = Get-SPManagedAccount
$inputManagedAcct = Read-Host "Enter managed account as Domain\User:"
#Input the Managed Account
$inputPasswd = Read-Host "Enter password from Active Directory for managed account:" –AsSecureString
#Change the password in SharePoint for the managed account to the new value
Set-SPManagedAccount -Identity $inputManagedAcct -ExistingPassword $inputPasswd –UseExistingPassword $true
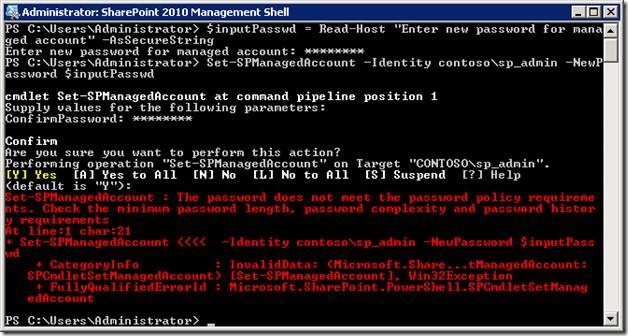
Command-line confusion
This is the command-line equivalent to the password policy error shown in the Graphical User Interface (GUI) above. Specifically, the error occurs when choosing between the –NewPassword and –ExistingPassword options for the Set-SPManagedAccount PowerShell cmdlet, if a password has already been changed in Active Directory.
The resulting error message is:
Set-SPManagedAccount : The password does not meet the password policy requirements. Check the minimum password length, password complexity and password history requirements.
If the password has already been reset in Active Directory and just needs to be updated in SharePoint, use the –ExistingPassword parameter. If the password needs to be changed in both SharePoint and Active Directory, use the –NewPassword parameter.
References and More Reading
- How to change service accounts and service account passwords in SharePoint Server 2007 and in Windows SharePoint Services 3.0
- Plan for administrative and service accounts (Office SharePoint Server)
- Administrative and service accounts required for initial deployment (SharePoint Server 2010)
- Windows PowerShell cmdlet reference: Get-SPManagedAccount
- Windows PowerShell cmdlet reference: Set-SPManagedAccount
- Stsadm to Windows PowerShell mapping (SharePoint Server 2010)
- Plan automatic password change (SharePoint Server 2010)
- Configure automatic password change (SharePoint Server 2010)
- Change passwords used for administration accounts (SharePoint Server 2010)
- Change passwords for SQL Server services (SharePoint Server 2010)
- Change the password for the default content access account (SharePoint Server 2010)
- Managed Accounts in SharePoint 2010 (Bill Baer TechNet Blog)
Comments
Anonymous
January 01, 2003
We offer a sharepoint add-ons (www.sharepointadd-ons.com/sharepoint-password-change-expiration) which can change password. With customizable e-mail notifications when password is about to expire.Anonymous
April 05, 2011
I get error for this command: Set-SPManagedAccount -Identity $inputManagedAcct -ExistingPassword $inputPasswd –UseExistingPassword $true It works if i change it to: Set-SPManagedAccount -Identity $inputManagedAcct -ExistingPassword $inputPasswd





![clip_image002[1] clip_image002[1]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/54/20/metablogapi/4540.clip_image002%5B1%5D_thumb.png)
![clip_image003[1] clip_image003[1]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/54/20/metablogapi/3884.clip_image003%5B1%5D_thumb.png)