Stop Phishing Attacks with Mail Flow Rules in Exchange Online
Companies are more concerned than ever about email security. Targeted phishing attacks are becoming more calculated and frequent for large companies. My customers are reporting that HR users are receiving emails from what appear to be the CEO asking for an export of all employees and Social Security Numbers while Finance users are being asked for tax documents. In some cases these emails look legitimate.
There are some out of the box solutions that exist. Turning on SPF (sender policy framework) hard fail works but has larger implications. Outlook offers safety tips but users can still be taken advantage of. Spoof Intelligence is being enhanced but requires E5 licensing. Below is a quick mail flow rule I've shared with several customers to help combat phishing attacks.
The rule is simple... if an email originates from outside the organization, but has a sender that inside the organization... do something.
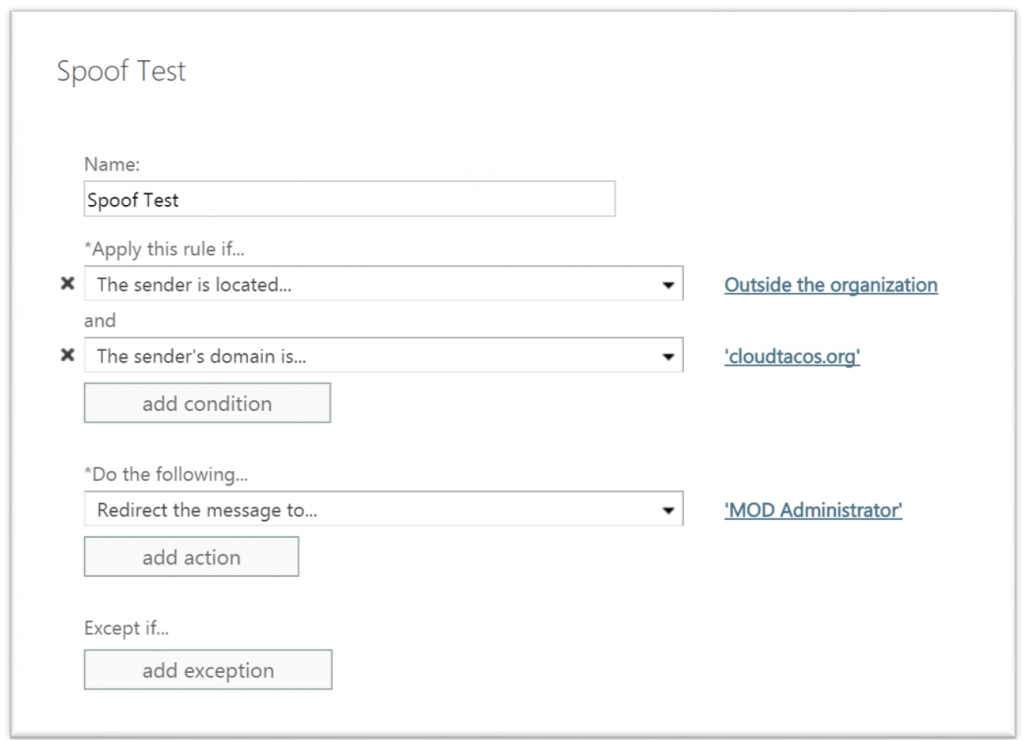
Considerations
- If you have 3rd parties who send on your behalf (HR, Corp Comm, Surveys, etc.), you'll want to make exceptions accordingly.
- Test the rule first. Either target the rule to a specific group of users or run it in test mode.
- If you are concerned about users sending out sensitive information, consider a DLP policy that would look for SSN's leaving the company.
Comments
- Anonymous
July 12, 2018
Do you need RMS licensing for this?