Implementing Secure Wireless Networking - Part 1
So I've got a few blog posts which piece together something I've been trying to do (and finally got working) since moving to Seattle. Namely - set up a secure wireless network. Now, I did have a wireless network at home when I was in England, but it wasn't secure. Well, it was, just not quite as secure as I could achieve with the infrastructure I have running (namely AD and a host of virtual machines running all sorts of services).
Some of this may be old news, some new to you. However, if you're a novice at setting up WPA, I hope this will help. Now of course, I didn't want just WPA, I wanted "guest" machines to be able to connect to the network - guests as in non-domain joined machines, or more accurately guest machines which are joined to another domain (such as my corporate laptop), running Windows Vista (of course) to also be able to connect to the network.
The first step in all of this is obviously the hardware. I bought a relatively new Linksys Wireless G box which supported WPA.
The basics are fairly obvious, such as giving it a static IP address in your subnet, putting a secure password on the administration access, an SSID, the wireless channel (best not to clash with neighbours) and (optionally, but useful) configuring a host name in your internal DNS server. Much nicer to be able to go https://wireless than https://192.168.x.x. Some pople would also advocate hiding the SSID from broadcast. Personally, if you've secured the back-end, I don't see there's a lot of value in this considering it's just too easy to use off the shelf tools to find hidden networks.
At this stage, you're on to configuring WPA itself. The first step in this is making sure your wireless box is configured for WPA-Enterprise mode with TKIP encription and pointing at a RADIUS server on your network. In my case, I have a couple of RADIUS servers, both on DCs. Unfortunately, the Linksys configuration doesn't allow for a backup RADIUS server (some DLink boxes do - worth checking first if this is important to you). Important - make sure you choose a REALLY secure shared secret password. A random password generator is recommended. Also, copy it to notepad somewhere so you can paste it later. Your screen should look similar to below at this point.
The next stage (if you haven't already done so) is to install the Internet Authentication Service (IAS) to provide RADIUS services on an appropriate machine on your network. It's hidden away under add/remove programs, Windows Components, Networking Services
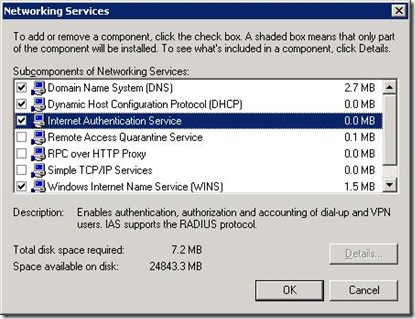
In the next part, I'll walk you through configuring the IAS server.
Cheers,
John.
Comments
- Anonymous
August 16, 2006
The comment has been removed - Anonymous
August 16, 2006
Good question, Adam - not sure I have a good answer to your question though. I was planning (at some point) to seperate the wireless subnet and have that secured through NAP or whatever the latest and greatest technology will be in Longhorn Server - TBH, since changing roles, I haven't had the time to keep up with things as much as I'd like as it isn't my day job anymore. But, yes, I do have an L2TP VPN in place so there may be some mileage in it. However, if wireless is on another subnet and I've got ISA 2006 (yippee) securing that subnet from the main "corpnet" and am implementing NAP, that hopefully should be sufficient. After all, I'm not guarding the crown jewels or Microsoft source code.... Oh for the 48hour day to invented to play with this stuff more ;)
Cheers,
John.
