Curtain Raiser for securing IIS 6.0 from DOS (Denial of Service) Attack
The architectural changes in IIS 6.0 compare to earlier versions make IIS a more secure platform. Worker processes run in user mode and therefore can’t access privileged items in the kernel. They also run in the context of the Network Service account with relatively low privileges. Built-in ASP functions run in the context of the IUSR_machine account
Your capability to configure application pools enables you to limit the kernel request queue size, limit CPU utilization, and apply other restrictions to help ensure that an attack, when it comes, will have its impact minimized on the server overall. To help combat buffer overflow attacks, IIS 6.0 monitors incoming requests to identify unusually large transaction requests that are indicative of an attack. You can also configure IIS 6.0 to recycle worker processes if they consume too much physical or virtual memory based on limits that you specify on a per-application-pool basis, reducing the impact of memory overflow exploits. Your capability to isolate sites and applications using multiple application pools and to configure recycling parameters for those pools helps reduce the effect of denial-of-service attacks.
Also as we see in below IIS6 architecture image the http.sys takes the credit for securing the IIS from Denial of Service attack by restricting the connection limit. But Http.sys is kernel component and hence if its affected by flood of million connections means your whole box is affected. In case of Attack, the http.sys will accept only configured connection and rest of these connections will be rejected by IIS 503 error. Only configured connections will be send to the application pool to serve the requests.
.gif)
Denial of Service (DOS) attack symptoms:
==========================================
A Denial of Service (DOS) attack is made up of excessive successful or unsuccessful attempts to access the Web server or site with HTTP, File Transfer Protocol (FTP), or another protocol from a single IP address with the possible intention of increasing network traffic and denying access to other users.
Possible Actions to prevent the attacks
==========================================
· Install URLScan and configure DenyUrlSequences to deny /. This will typically be implemented by the security team at your end. The following URL describes in detail about what URLSCAN is and how to configure it
https://msdn.microsoft.com/en-us/library/aa302368.aspx
· Prevent Denial of Service (DOS) attacks in your web application
· For this type of attempt, set the firewall policy or TCP/IP filtering to block the IP. If the IP is internal, take the computer off the network to determine why it is trying to access the HTTP or FTP services of the Web server excessively.
https://msdn.microsoft.com/en-us/library/aa302363.aspx
· ISA Server Network Protection: Protecting Against Floods and Attacks
https://technet.microsoft.com/en-us/library/bb794735.aspx
· Restrict the connection to a particular number of connections. The number of connection is something which you need to decide on the basis of your infrastructure and threat model.
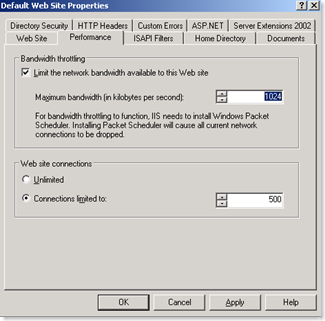
· Building Secure Web Services