You probably don't need ACCTINFO2.DLL
Hi folks, Ned here again. Customers periodically ask us for a rumored replacement for the Windows 2000 acctinfo.dll that works on 64-bit Windows 7 and Windows Server 2008 R2 . That old DLL added an extra tab to the Active Directory Users and Computers snap-in to centralize some user account info:
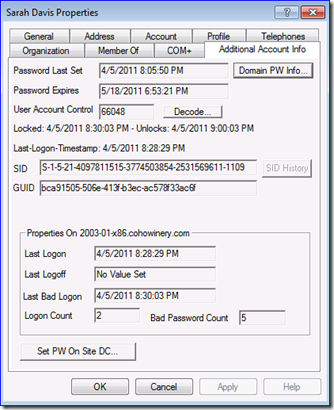
Pretty cool. You can see account lockout status, last logon time, account is locked out, and other goo.
Even though that newer unsupported acctinfo2.dll file exists - yes, even in x64 format - there is a supported way to see this info as long as your admins use Win7 + RSAT or Win2008 R2.
Some Background
Windows Server 2008 R2 introduced a new service called the Active Directory Management Gateway (also called the AD Web Service). AD PowerShell uses this component as a sort of proxy into Active Directory. This is fine if you are native Windows Server 2008 R2 and Windows 7, but for most companies, that's going to take a while. While this includes quasi-web traffic - the .Net Negotiated Stream protocol - we sign and seal all LDAP traffic. You can further secure the traffic by deploying Domain Controller or Domain Controller Auth certificates - something that happens automatically with the deployment of an Enterprise PKI in your domain.
Knowing this, we released an out of band version of this service - you can grab it here. Install it and its support files on Windows Server 2003 or Windows Server 2008 and your shiny new Win7 clients can run AD PowerShell even if you don't have a single Win2008 R2 server in the forest. The service is fine to install only a few DCs as well - as long as those are up and routable to Win7 clients, you’re good to go; not all DCs need run the service. Your Windows 7 clients will find the updated servers automatically, or you can point to them specifically.
The New Way to Look at Users
The Active Directory Administrative Center is another new component introduced by Windows Server 2008 R2. Many admins gave it a glance, thought to themselves "another ADUC, why bother?", and went back to their familiar old tool. If you like acctinfo.dll though, you should like ADAC.
With Win7 RSAT installed and the AD tools enabled (or RDP'ed into your Win2008 R2 servers for AD administration), run DSAC.EXE. You'll see this:
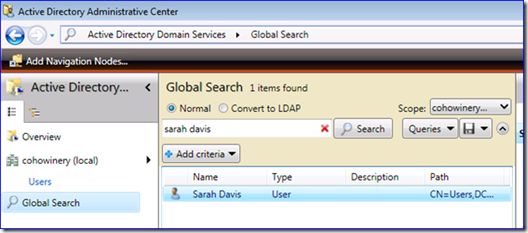
You can browse to users or search for them. I'll search for Sarah Davis:
I open the user and so far, it looks pretty much like ADUC.
It saved me a click of the "Account" tab to see things like logon name and password options. However, I want all that account status goo!
Say, what does that little nubbin arrow icon down in the lower left do?
<Clickity click>
Blammo!
Compare that to the old acctinfo.dll. :) Password info, lockout info, and logon info. Even the SID and GUID. There are a few things missing like "account unlocks at such and such date" but their usefulness is questionable - if you care that someone is locked out, you mostly care about seeing when they locked and unlocking now. Acctinfo2.dll doesn't show that either, btw. Moreover, if you want to change someone's password on a certain DC, just retarget to that DC. Better yet, always target the PDCE; DCs contact the PDCE after a failed logon for another try, as it is likely to have the latest password from so-called urgent replication. In addition, account lockouts should be the most up to date on a PDCE.
Oh, and stop using account lockout policy anyway, it's vile. Use complex passwords and get ACS to track for brute force bad password attempts. Turning on account lockouts is a way to guarantee someone with no credentials can deny service to your entire domain. Locking out your boss' account will be a very convincing demonstration… mmm, maybe just a test admin account. J
While we're in here
Need to see the “Attribute Editor” extension on RSAT client versions of ADAC to get more "ADUC parity" at examining users? You can enable that tab by adding the {c7436f12-a27f-4cab-aaca-2bd27ed1b773} displayspecifier with these steps (again, using my sample domain cohowinery.com as the example):
1. Logon as an enterprise admin.
2. Run ADSIEDIT.MSC and connect to the Configuration Partition.
3. Navigate to:
CN=user-Display,CN=409,CN=DisplaySpecifiers,CN=Configuration,DC=cohowinery,DC=com
Note: 409 is "US English". You will need to repeat all these steps for any other languages used in your environment.
4. Edit user-Display container.
5. Edit the adminPropertyPages attribute.
6. Determine the highest index value listed. For example in mine, it was 10.
7. Add the GUID {c7436f12-a27f-4cab-aaca-2bd27ed1b773} set with the next highest index number. For example, here I added:
11,{c7436f12-a27f-4cab-aaca-2bd27ed1b773}
8. Close adsiedit. Replicate this value to all DCs in the forest through natural convergence or forcing with repadmin.exe.
9. Once done replicating to all DCs, anytime you start DSAC.EXE all users will show the Attribute Editor.
Note: before you get all froggy about these steps - if you end up using acctinfo2.dll you will have to modify its displaySpecifier data as well. :)
Update 12/10/2012
Your feedback in the Comments was heard in Windows Server 2012. ADAC now also shows Password Last Set and Password Expiration info:
A final note
You will find a great many copies of acctinfo2.dll floating around, but none hosted on Microsoft websites (we never released it publically, it was just a side-project for a Support engineer here in Charlotte). Before you install those, consider this: you plan to load a DLL from some random place on the Internet into one of your most powerful AD admin tools, and then run that tool as a Domain Admin. And you have no way to know if that's some leaked MS version of the file or one adulterated by hackers.
Still sound like a good plan?
If you absolutely must use this DLL, you should only get it by contacting MS through a support case. If I wrote malware, an admin-only file injected into AD management tools would be my first choice for pwnage.
Until next time.
Ned "the guy that wrote acctinfo2.dll has ostrich legs" Pyle
Comments
Anonymous
April 12, 2011
The comment has been removedAnonymous
April 12, 2011
You and me both. :-DAnonymous
April 13, 2011
The comment has been removedAnonymous
April 13, 2011
Good call, those would be: 969429 Windows 7 clients cannot locate the Active Directory Management Gateway service that is installed on Windows Server 2003-based domain controllers support.microsoft.com/default.aspx 967574 Windows 7 clients cannot locate the Active Directory Management Gateway Service installed on Windows Server 2008-based domain controllers support.microsoft.com/default.aspx Thanks David!Anonymous
April 14, 2011
The comment has been removedAnonymous
April 14, 2011
Thanks Santhosh :-DAnonymous
April 25, 2011
So ADAC looks pretty cool, but one thing I liked about acctinfo2.dll was the Password Last Set and Password Expires information nuggets. Am I just not seeing that in the new location or is it just not part of the ADAC tool?Anonymous
April 25, 2011
Good and bad news. :-/ You can see Password Last Set easily if you just turn on the attribute editor -it will display PwdLastSet in human-reable plain text and show date, time, and time zone. But Password Expires will require mental gynamstics. "She set her password on the April 25th 2011 and we have a 42 day max password age so it will require change on Sunday June 6." My main question would be: why do I care? The user will be warned in advance at every logon once their password is close to expiration and when it expires, they will have a very clear message (for them or their help desk) explaining why they cannot logon and that they are required to change their password. Are you mainly looking for feature parity or do you have a business process that makes this useful? If the latter I'd like to hear about it so I can get DSAC improved.