Using PowerShell to filter IIS Failed Request Tracing files
Failed Request Tracing is very helpful and easy way to troubleshooting errors, slow requests and unexpected IIS response.
Sometimes I received too many tracing files. I hate to open them one by one to find out the trace file I am interesting and this is time consuming.
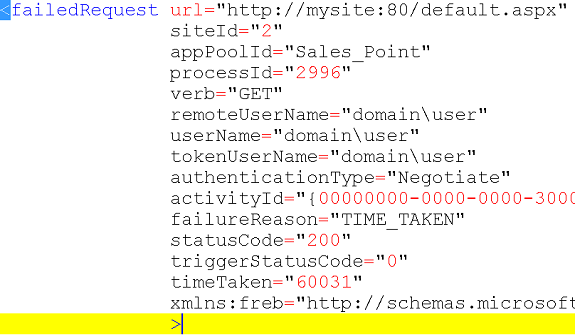
The trace file itself is XML file, here is the root node and its attributes.
So, we can filter request tracing files based on the XML attributes.
Sample 1:
Here is a sample I used to find out request files which requests took more than 50 seconds. It uses the “timeTaken” attribute of the root node.
$files = Get-Item e:\temp\fr*.xml
foreach ($file in $files)
{
$xmldata = [xml](Get-Content $file.FullName)
if ([int]$xmldata.failedRequest.timeTaken -gt 50000)
{
write-host "=======" $file.Name "========"
write-host "Request URL:`t" $xmldata.failedRequest.url
write-host "Time-Taken:êo`t`t" $xmldata.failedRequest.timeTaken
write-host "Failure Reason:êo`t" $xmldata.failedRequest.failureReason
write-host "`n"
}
}
Sample Output:
======= fr000458.xml ========
Request URL: https://MySite:80/default.aspx
Time-Taken: 60609
Failure Reason: TIME_TAKEN
Sample 2:
Here is another sample I frequently used, it find out the files which the requests were come from a specific IP.
$files = Get-Item e:\temp\fr*.xml
foreach ($file in $files)
{
$xmldata = [xml](Get-Content $file.FullName)
$eventList = $xmldata.GetElementsByTagName("Event")
foreach ($event in $eventList)
{
$eventData = $event.EventData
foreach ($data in $eventData.ChildNodes)
{
if ($data.Name -eq "RemoteAddress")
{
if ( $data.InnerText -eq "10.17.205.79")
{
write-host "=======" $file.Name "========"
write-host "Request URL: " $xmldata.failedRequest.url
write-host "`n"
}
}
}
}
}
Sample output:
======= fr000433.xml ========
Request URL: https://MySite:80/PageTracker.aspx?nav=selectmenuBack('D','7');
RemoteAddress: 10.17.205.79
======= fr000434.xml ========
Request URL: https://MySite:80/PageTracker.aspx?nav=selectmenuBack('MO','81|7');
RemoteAddress: 10.17.205.79
======= fr000435.xml ========
Request URL: https://MySite:80/default.aspx
RemoteAddress: 10.17.205.79
Sample 3:
The last sample, it finds out the requests with a special HTTP header (From XMLHTTPRequest).
$files = Get-Item e:\temp\fr*.xml
foreach ($file in $files)
{
$xmldata = [xml](Get-Content $file.FullName)
$eventList = $xmldata.GetElementsByTagName("Event")
foreach ($event in $eventList)
{
$eventData = $event.EventData
foreach ($data in $eventData.ChildNodes)
{
if ($data.Name -eq "Headers")
{
if ( $data.InnerText.Contains("X-Requested-With: XMLHttpRequest"))
{
write-host "=======" $file.Name "========"
write-host "Request URL: " $xmldata.failedRequest.url
write-host "`n"
}
}
}
}
}
Sample Output:
======= fr001921.xml ========
Request URL: https://MySite:80/Data/GetLocalAuthorities
See you next time,
Wei from APGC DSI Team