你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
查看从建议免除的资源
在 Microsoft Defender for Cloud 中,可以从 Defender for Cloud 安全建议中豁免受保护的资源。 本文介绍如何查看和使用免除的资源。
在门户中查看免除的资源
某个资源被豁免后,它将不再被纳入安全建议的考虑范围。 你可以查看豁免的资源,并在 Defender for Cloud 门户中管理每个资源。
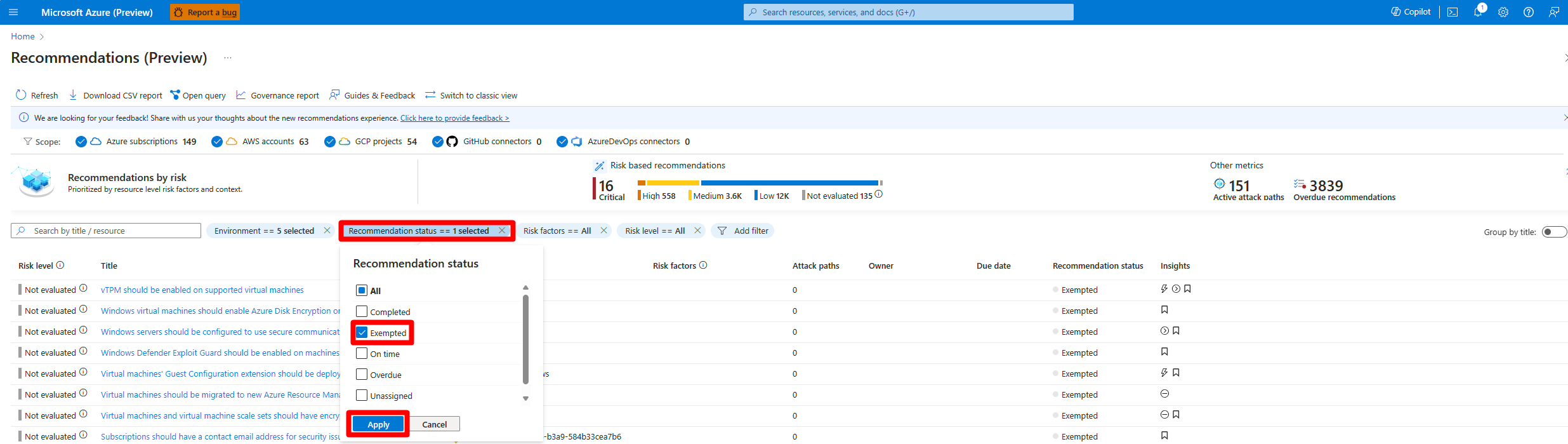
在建议页面上查看豁免的资源
若要查看豁免的资源,请执行以下操作:
登录 Azure 门户。
导航到“Defender for Cloud”>“建议”。
选择“建议状态”。
选择“已豁免”。
选择“应用”。
选择一个资源来查看它。
在清单页面上查看豁免的资源
还可以在“库存”页面上找到豁免一个或多个建议的所有资源。
查看 Defender for Cloud 的库存页面上的豁免资源:
登录 Azure 门户。
导航到“Defender for Cloud”>“清单”。
选择“添加筛选器”
选择“包含豁免”。
选择是。
选择“确定”。
使用 Azure Resource Graph 查看免除的资源
使用 Azure Resource Graph (ARG),可以通过可靠的筛选、分组和排序功能,快速访问你的云环境中的资源信息。 这是使用 Kusto 查询语言 (KQL) 查询信息的快速且高效的方法。
若要查看所有具有免除规则的建议:
在“建议”页中,选择“打开查询”。
输入以下查询并选择“运行查询”。
securityresources | where type == "microsoft.security/assessments" // Get recommendations in useful format | project ['TenantID'] = tenantId, ['SubscriptionID'] = subscriptionId, ['AssessmentID'] = name, ['DisplayName'] = properties.displayName, ['ResourceType'] = tolower(split(properties.resourceDetails.Id,"/").[7]), ['ResourceName'] = tolower(split(properties.resourceDetails.Id,"/").[8]), ['ResourceGroup'] = resourceGroup, ['ContainsNestedRecom'] = tostring(properties.additionalData.subAssessmentsLink), ['StatusCode'] = properties.status.code, ['StatusDescription'] = properties.status.description, ['PolicyDefID'] = properties.metadata.policyDefinitionId, ['Description'] = properties.metadata.description, ['RecomType'] = properties.metadata.assessmentType, ['Remediation'] = properties.metadata.remediationDescription, ['Severity'] = properties.metadata.severity, ['Link'] = properties.links.azurePortal | where StatusDescription contains "Exempt"
创建免除时收到通知
为跟踪用户从建议豁免资源的方式,我们创建了 Azure 资源管理器 (ARM) 模板,该模板可部署逻辑应用 Playbook 和所有必需的 API 连接,以便在创建豁免后向你发送通知。
- 在 TechCommunity 博客“如何在 Microsoft Defender for Cloud 中跟踪资源免除”中详细了解 playbook。
- 在 Microsoft Defender for Cloud GitHub 存储库中找到 ARM 模板。
- 使用此自动化过程以部署所有组件。