Integrate Web App with Azure Virtual Network by Point-to-Site VPN
It is a common scenario that we want to use VNet Integration to enable our web app access a database or other services running on a virtual machine in an Azure virtual network. With VNet Integration, we don't need to expose a public endpoint for applications on the virtual machine but can use the private non-internet routable addresses instead. This requirement can be achieved easily as long as the virtual network has a point-to-site VPN which is configured with a Dynamic routing gateway instead of static routing.By building on point-to-site technology we can limit network access to just the virtual machine hosting the app. Access to the network is further restricted on those app hosts so that the applications can only access the networks that we configure them to access. Based on the VNet Integration feature, we can further make our virtual network connect to our on-premises network via a Site to Site VPN, then our apps can have access to on-premises resources as well.
Now, let's firstly create a virtual network with the following configurations, I will not show details about how to make it as there have been a lot of introductions for that.
Virtual Network Address Block: 10.1.0.0/16
Default Subnet Address Block: 10.1.0.0/24
Gateway Subnet Address Block: 10.1.1.0/28
Next, we need create a new Virtual Network Gateway for the VNet above, this could take for a while. After that, click "Point to site configuration" to configure the VPN, set Point-to-site Address Block as 172.16.0.0/24 in this example. This is the point to site IP address space for the VNet. Our web apps will show communication as coming from one of the IPs in this address space. In addition, make sure IKEv2 Tunnel Type is not checked shown below as currently Azure web app vnet intetration doesn't support IKEv2 yet.

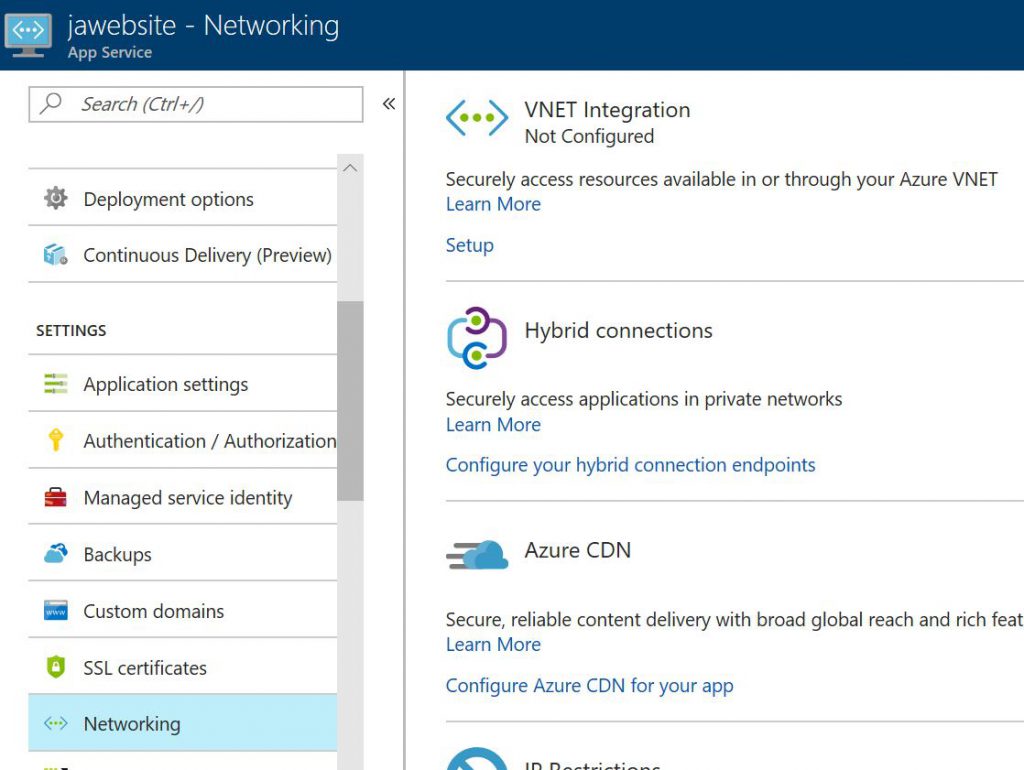
Here, just please understand SSTP is an SSL-based VPN tunnel that is supported only on Windows client platforms and it can penetrate firewalls, which makes it an ideal option to connect to Azure from anywhere. On the other hand, IKEv2 VPN is a standards-based IPsec VPN solution and it can be used to connect from Mac devices as well. Lastly, we can go to Web App's blade, select Networking, click Setup and finish the all.
If you have an existing virtual network and it throws errors such as "Adding network jac-vnet to web app jawebsite failed.: Legacy Cmak generation is not supported for gateway id /subscriptions/subscriptionid/resourceGroups/javnetrg/providers/Microsoft.Network/virtualNetworkGateways/p2sgateway when IKEV2 or External Radius based authentication is configured. Please use vpn profile package option instead" when you integrate your web app to the virtual network, a common problem is the existing virtual network supports both of SSTP and IKEv2. In order to fix that, run the below Powershell script to check the cause and limit VPN client protocol to SSTP only if needed.
$gateway = Get-AzureRmVirtualNetworkGateway -ResourceGroupName groupname -Name vpngatewayname
$gateway.VpnClientConfiguraiton.VpnClientProtocols
Set-AzureRmVirtualNetworkGateway -VirtualNetworkGateway $gateway -VpnClientProtocol "SSTP"
Comments
- Anonymous
May 21, 2018
Very useful post, thanks!!