Setting Up Windows Intune/ConfigMgr 2012 R2 with ADFS On-Prem and Azure Lab - Part 2
Setting Up Windows Intune/ConfigMgr 2012 R2 with ADFS On-Prem and Azure Lab - Part 2
Ok, to quickly recap what we did in Part 1, we installed and configured a RRAS server in the home intranet lab, created a new DNS primary zone (where applicable), created our DNS entries for the to-be ADFS service name, and created our DNS conditional forwarders to route traffic out of the intranet lab.
Additional Links to Other Parts of the Blog Series.
Part 1 – Home Intranet Lab Setup
Part 3 – Install ADFS On-Prem and Install ADFS WAP on Azure VM
Part 4 – Configuring Intune and ConfigMgr 2012 R2
Part 5 - Enrolling the Different Device Types in Intune (Windows Phone, Android, iOS) - Coming Soon!
Next up, we need to setup our Azure network and provision our Azure VM. Let’s get going!
Part 2 – Create and Configure Azure Network and Provision Azure VM
Step 1:
Log into Azure by going to https://manage.windowsazure.com . Enter your subscription credentials to access the Azure portal. Within the Azure portal, in the left pane, click Networks. This will bring up the Azure network options in the middle pane. At the bottom of the screen, there will be a black bar with some options. Click the New button to create a new Azure network. NOTE: Pay no attention to the fact I have a network already created. Unless you have created an Azure network already, you will not have any networks configured yet.
Once you click New, a pop-up menu from the bottom of the screen will appear with Virtual Network already highlighted. Choose the option “Custom Create” from the list of options.
The Create a Virtual Network screen will appear. In the Name field, name your new Azure Virtual Network that is intuitive to identify it as your Azure network. As you saw in a previous screenshot, I named my network Azure. In the Region drop-down, if in the United States, choose either East US or West US. In the Affinity Group Name field, type in a name for the new Affinity Group. For my environment, I named my Affinity Group the same as my intranet domain. Click the arrow icon in the lower right corner to go to the next screen.
On the DNS Servers and VPN Connectivity screen, there are quite a few options. First, under the DNS servers section, in the Name field, type in the name of your intranet domain controller or DNS server. In the field to the right of the Name field, type in the intranet IP address of the domain controller or DNS server. As you are entering this information, a new set of fields will appear below. In the new fields, in the Name field, type in “Internet DNS” and provide the IP address of one of the conditional forwarders configured in Part 1. To the right of this section are a couple check boxes. Select the “Configure a site-to-site VPN” checkbox. When complete, your screen should look similar to the screenshot below. Click the right-arrow icon to continue.
The Site-To-Site Connectivity screen will appear. In the Name field, type in a name that intuitively identifies your home intranet lab. In the VPN Device IP Address field, type in the IP address of your home modem.
NOTE: This is the IP received from your ISP that is assigned to your modem. If you do not know this information, go to www.speedtest.net . When the page load if look in the middle left of your screen, you will see an IP address. This is the IP address you need to enter in this field).
To the right of those fields are some Address Space fields. Input the address space of your INTRANET NETWORK. For example, if your home router uses the 192.168.1.1 address space, input 192.168.1.2 in the Starting IP field and change the CIDR (Address Count) field to /24. When complete, the screen will look similar to the screenshot below. If you wish, you can add more address spaces, but in a lab setup, you typically only require one address space. Notice the diagram that gets created as you step through the wizard. It starts to make a little more sense now. Click the right-arrow icon to continue.
The Virtual Network Address Spaces screen will appear. This screen is a little more confusing. These address spaces will represent the IP addresses that will be assigned to VMs created in Azure and assigned to the virtual network. Again, you can create as many address spaces that you want. However, in the lab setup, only 1 address space, put a gateway subnet is necessary.
Out beside the address space defined at the top, 10.0.0.0, in the Starting IP field, type in 10.10.0.0. Change the CIDR (Address Count) field to /22
In the Subnets section, replace the name Subnet-1 with “Azure-Infra”. Change the Starting IP to 10.10.1.0 and change the CIDR (Address Count) field to /24.
Click Add Gateway Subnet. Name the Gateway Subnet “Gateway”. Change the Starting IP to 10.10.2.0 and change the CIDR (Address Count) field to /29.
When complete, the screen will look similar to the screenshot below. Click the checkmark icon to create the Azure Virtual Network. NOTE: The numbers out beside the CIDR /22, /24, /29, may be different from the screenshot. This is of no concern.
Back on the Azure Networks screen, the Azure Virtual Network will get created. It make take some time to create the Virtual Network. When it is created, you’ll the little green “squigglies” to the bottom right in the black bar stop moving. Click the green “squigglies” and you’ll see a message that says the virtual network was successfully created. Click the OK checkmark icon to close the notification. Then click the newly created virtual network.
The Azure Virtual Network Configuration screen will appear. In the top menu area, click Dashboard. And you should see a screen similar to the screenshot below. When ready, go ahead and click on the Create Gateway button in the bottom black bar menu and choose Dynamic Routing from the pop-up once clicked. When it prompts you if you want to create the gateway, click the Yes icon.
The gateway creation process can take up to 15 minutes. So now would be a good time to go grab a Coke and a candybar! As this process is going on, you’ll see the diagram above change a bit to something like the screenshot below:
Once the gateway has been created successfully, you’ll see a screen like below, showing that while the Azure Virtual Network is now successfully provision, it is not connected to the home intranet lab yet. The next steps will walk you through that process to connect up your home intranet lab to the Azure Virtual Network.
On the right hand side, click the Download VPN Device Script link. The Download a VPN Device Configuration Script window will appear. In the Vendor drop-down menu, choose Microsoft Corporation. In the Platform drop-down, choose RRAS. And finally, in the Operating System drop-down, choose Windows Server 2012. When complete, click the checkmark icon to continue.
You’ll be prompted to download a file called VpnDeviceScript.cfg. Save this file to a location that is accessible by the home intranet lab domain controller where the RRAS service was installed or copy the script to the domain controller.
Copy the script locally to the domain controller/RRAS server. Change the filename extension of the script to .PS1. Open Powershell as an Adminstrator. Navigate to the script location, type in the name the script and press Enter to execute the script.
NOTE: If you receive an error, you may need to change the Powershell Execution Policy on the server for the script to execute successfully.
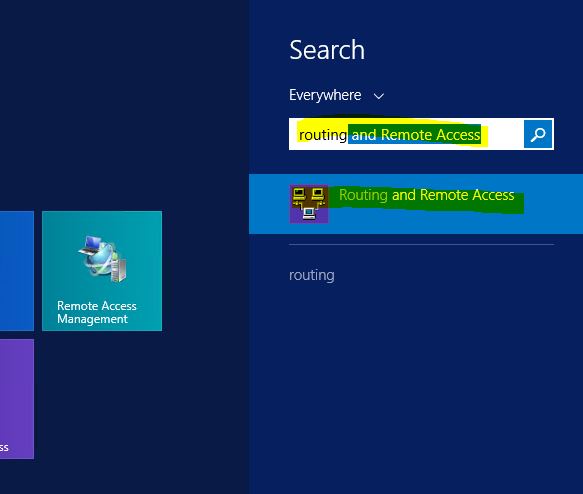
Once the script executes successfully, close the Powershell window and open up the Routing and Remote Access console. Go to the server start screen and type Routing and the Routing and Remote Access console will pop-up in the available items to click on.
In the Routing and Remote Access console, expand the node named after the server and click on Network Interfaces. In the right pane, you should see a new entry labeled after the IP address of the Azure Gateway you created earlier. At first, the connection will show as disconnected. However, after about 5 minutes, the connection will be established and your home intranet lab will now be connected to the Azure Virtual Network. Pretty cool!
Back on the Azure web portal, click on Networks in the left pane, then click the Azure Virtual Network you created earlier in the middle pane, then click Dashboard in the top-area menu and you’ll eventually see something like the screenshot below, indicating your home intranet network and the Azure Virtual Network are now connected and “talking” to each other.
Now, I have switched the screenshots out to show the original Azure Virtual Network I created. You will not see as much data in and data out at first like you see above. As you can see, I’ve had a good bit of data going back and forth between my Azure Virtual Network and my home lab. Notice the gateway IP above is the same as the name of the new interface entry in the intranet RRAS console. In the Resource section, you can see the virtual machines I’ve already created in Azure and have assigned to the Azure Virtual Network.
NOTE: If after 5 minutes, the portal, nor the RRAS console indicate the interface is connected, give it a kick by right-clicking on the interface in the RRAS console and choosing Connect from the context menu.
That was a lot right? We are almost through with the Azure setup piece. Now, we just need to provision our Azure VM. Ready? Let's do it!
Step 2 – Provision the Azure VM
Inside the Azure web portal, on the left hand menu, click on Virtual Machines. In the bottom-left black bar, click the New icon.
A pop-up menu will appear. From the list of items, toward the middle-right, click From Gallery.
A wizard will appear. On the Choose an Image screen, choose Windows Server 2012 R2 Datacenter and click the right-arrow icon in the bottom-right part of the screen.
On the Virtual Machine Configuration screen, in the Virtual Machine Name field, give the VM a name that will identify it as the Azure VM that will host your ADFS WAP service. In the Size field, choose the option with 3.5GB memory. Fill in the New User Name, New Password, and Confirm Password fields as well. The User Name will be the local admin on the VM. When complete, click the right-arrow icon to continue. NOTE: As the VM name is public, it must be completely unique.
On the next screen of the Virtual Machine Configuration, in the Region/Affinity Group/Virtual Network drop-down menu, choose the virtual network you created earlier. In the Virtual Network Subnets drop-down, ensure it is assigned to the “Azure-Infra” subnet. In the Endpoints section, from the open drop-down, select HTTPS. When finished, click the right-arrow icon to continue.
NOTE: You must configure the Endpoints. Think of Endpoints on Azure VMs as opening up a port a firewall. If HTTPS is not configured, any external ADFS request will never reach the Azure VM that will be configured as the ADFS WAP.
NOTE: Please disregard the 2nd screenshot below that shows HTTP in addition to HTTPS. HTTP is not necessary.
On the next screen, just click the checkmark icon and Azure will provision the VM!
It will take a few minutes for Azure to provision the VM. Similar to provisioning of other items in Azure, there is a notification bar at the bottom of the screen. When complete, the green “squigglies” will stop moving, indicating Azure has completed the task. Once the VM has been provisioned, you can click VM’s name to view the dashboard and other configurations. To access the VM, click on any other field in the same row as the name to highlight the machine (literally click where the screenshot below says) and click the Connect icon in the bottom black bar.
Once you click connect, you will receive a prompt to open up an RDP session. Click Open to open the session or you can click Save to create an RDP file that you can use to access straight from your laptop or other device.
The RDP session will open, log in with the credentials you specified earlier when provisioning the machine and voila! You’re now logged into your Azure VM. Sweet!
Ok, that about wraps up things for now. In the next part of this series, we’ll install and configure ADFS in the home intranet lab, also install and configure the ADFS WAP on the Azure VM, make some changes to public DNS manager where you registered your Internet domain name, and test everything to see if we can access the ADFS service in the home intranet lab externally from the Internet.
Till next time...
Comments
- Anonymous
May 23, 2014
Hello all,
It's been quite some time since I've wrote a blog, almost a year! I can say - Anonymous
May 24, 2014
Pingback from Search this blog Search all blogs | FlipsPops - Anonymous
May 24, 2014
Pingback from Search this blog Search all blogs | FlipsPops - Anonymous
May 24, 2014
Pingback from Search this blog Search all blogs | LikeOuts - Anonymous
May 24, 2014
Pingback from Search this blog Search all blogs | NextOff - Anonymous
May 25, 2014
Pingback from Setting Up Windows Intune/ConfigMgr 2012 R2 with ADFS On-Prem and Azure Lab | MS Tech BLOG - Anonymous
November 25, 2014
Setting Up Windows Intune/ConfigMgr 2012 R2 with ADFS On-Prem and Azure Lab - Part 3
Ok, to quickly - Anonymous
November 25, 2014
Setting Up Windows Intune/ConfigMgr 2012 R2 with ADFS On-Prem and Azure Lab - Part 4
Additional