Deploy AppLocker Policies to only allow Microsoft/Citrix signed code and Store apps
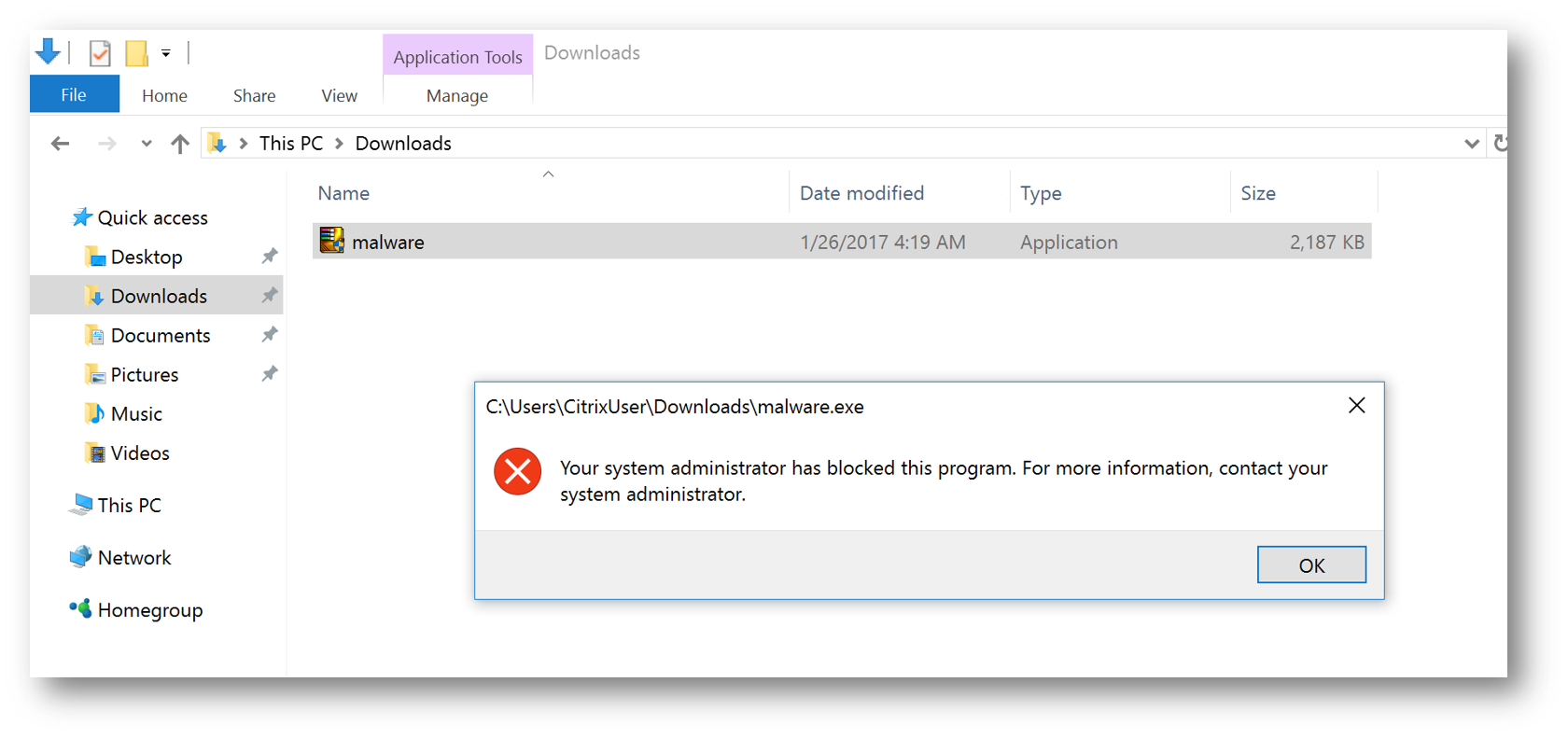
In some scenarios there's a demand for an increased security on Windows 10. Recently we worked on a scenario where only Microsoft code, Citrix code and Store Applications could run. Combined with no-local administrator privileges this creates a highly secure platform. Malware typically isn't signed (and especially not by Microsoft or Citrix, if so we have bigger problems) and therefore unable to run on PC's configured in this scenario.
Configure Microsoft Intune policies
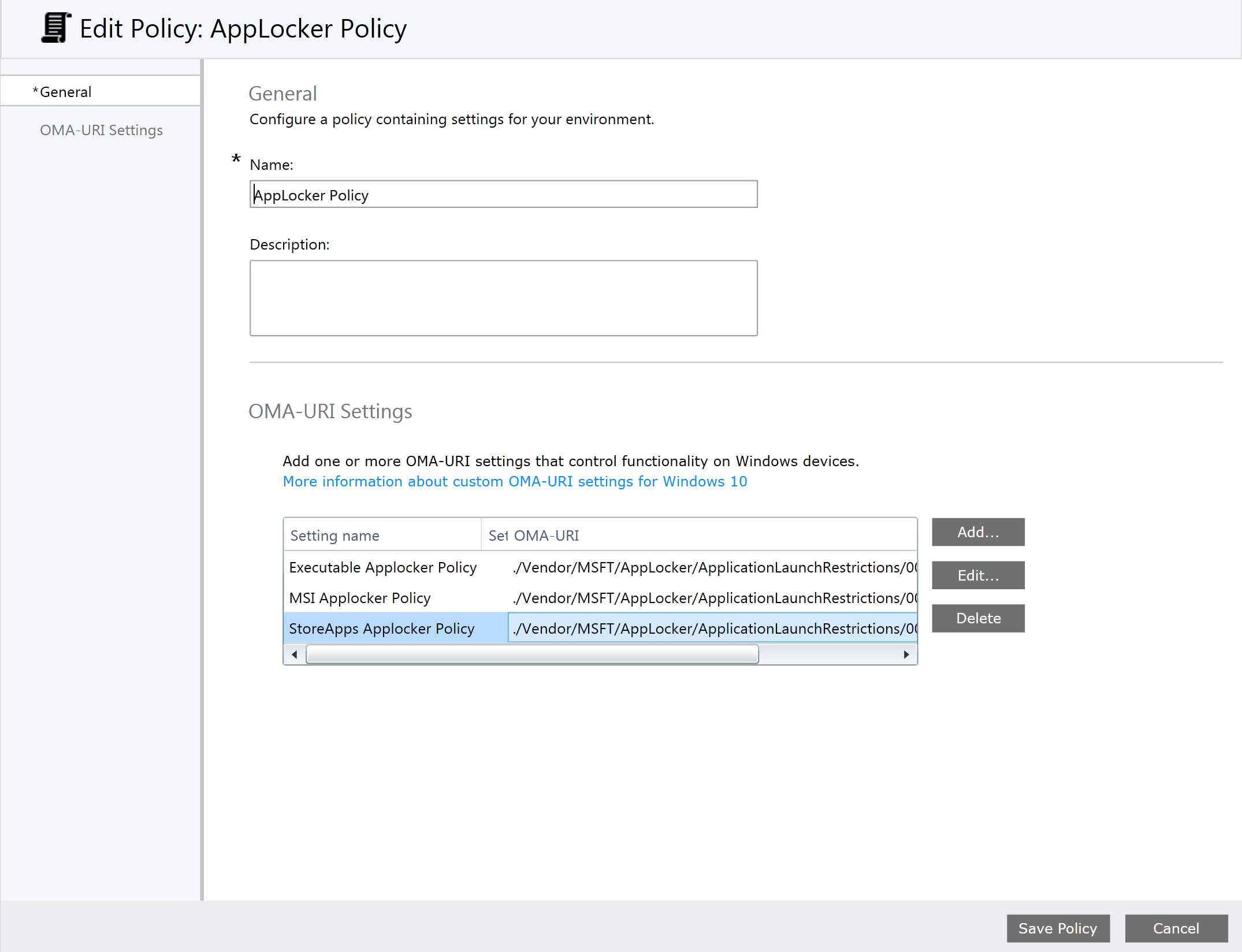
Open the Microsoft Intune management console, navigate to Policy > Configuration Policies > Add > Windows > Custom Configuration (Windows 10 Desktop and Mobile and later) Give the Policy a descriptive name (e.g. AppLocker) and select Add. We will define three AppLocker Policies, one for Executables, MSI and AppX. Please pay special attention, most values are case sensitive.
-------------------------------------------------------------------------------------------------------------------------------------------------
Setting Name: Executable AppLocker Policy
Data Type: String
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/000000001/EXE/Policy
Value:
<RuleCollection Type="Exe" EnforcementMode="Enabled"> <FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePathCondition Path="%PROGRAMFILES%\*" /> </Conditions> </FilePathRule> <FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePathCondition Path="%WINDIR%\*" /> </Conditions> </FilePathRule> <FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow"> <Conditions> <FilePathCondition Path="*" /> </Conditions> </FilePathRule> <FilePublisherRule Id="274fd9f6-d906-43ad-ad2f-e0152a209add" Name="Program Files (x86): MICROSOFT® WINDOWS® OPERATING SYSTEM signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="MICROSOFT® WINDOWS® OPERATING SYSTEM" BinaryName="*"> <BinaryVersionRange LowSection="10.0.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="56735fab-e02e-4e2e-af47-c2d02ec61ebc" Name="Program Files (x86): INTERNET EXPLORER signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="INTERNET EXPLORER" BinaryName="*"> <BinaryVersionRange LowSection="11.0.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePathRule Id="f747fe36-a2be-4236-9be1-3c1a556ca121" Name="Program Files (x86): %PROGRAMFILES%\COMMON FILES\MICROSOFT SHARED\MSINFO\*" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePathCondition Path="%PROGRAMFILES%\COMMON FILES\MICROSOFT SHARED\MSINFO\*" /> </Conditions> </FilePathRule> <FilePublisherRule Id="a7f07120-c355-4d80-a537-1be387f85d87" Name="Program Files (x86): CITRIX ICA CLIENT signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="CITRIX ICA CLIENT" BinaryName="*"> <BinaryVersionRange LowSection="14.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="d5b5f9bb-7d06-4df0-82f8-7596bce8a664" Name="Program Files (x86): CITRIX RECEIVER signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="CITRIX RECEIVER" BinaryName="*"> <BinaryVersionRange LowSection="4.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="07afdd14-6bea-4166-befb-9cb0c2c9280d" Name="Program Files (x86): CITRIX WEB HELPER signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="CITRIX WEB HELPER" BinaryName="*"> <BinaryVersionRange LowSection="4.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="ae34303b-e724-4883-ae4e-bdbabae4fb15" Name="Program Files (x86): CITRIX XENAPP signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="CITRIX XENAPP" BinaryName="*"> <BinaryVersionRange LowSection="14.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="10a713e2-8f45-46d1-a9f7-dbbbcef14949" Name="Program Files (x86): RECEIVER signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="RECEIVER" BinaryName="*"> <BinaryVersionRange LowSection="4.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="979ca13f-cebb-4d20-9b07-1342e8c4aa86" Name="Program Files (x86): CEIP signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="CEIP" BinaryName="*"> <BinaryVersionRange LowSection="4.5.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> </RuleCollection>
Setting Name: MSI Applocker Policy
Data Type: String
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/000000002/MSI/Policy
Value:
<RuleCollection Type="Msi" EnforcementMode="Enabled"> <FilePublisherRule Id="31a7ad3a-d7b3-4e3e-9df0-fe7972f77437" Name="Signed by O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="O=CITRIX SYSTEMS, INC., L=SANTA CLARA, S=CALIFORNIA, C=US" ProductName="*" BinaryName="*"> <BinaryVersionRange LowSection="*" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> </RuleCollection>
Setting Name: StoreApps Applocker Policy
Data Type: String
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/000000003/StoreApps/Policy
Value:
<RuleCollection Type="Appx" EnforcementMode="Enabled"> <FilePublisherRule Id="bae41f27-df1e-4bfd-8f1c-80034807bc74" Name="Signed by *" Description="" UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*"> <BinaryVersionRange LowSection="*" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> </RuleCollection>
Deploy the policies to a specific user and you will receive the policies shortly after. The user will be unable to launch anything other than signed Microsoft/Citrix code and Store Applications.
Thanks Erik Radix for working on this together.
Please consider leaving a reply in case this post helped.
Comments
- Anonymous
February 09, 2017
Great blog Pieter :-) But how did you remove the local administrator privilege?