iSCSI: Latest Apple Peripheral or Easy SAN? (Continued Discussion of Server Clusters)
While iSCSI might have the little "i" so common in Apple's naming schemes, it has nothing to do with Mr. Jobs. In this case, the "i" stands for "Internet." SCSI (Small Computer System Interface) is an interface used for connecting PCs to peripherals such as hard drives. SCSI is nothing new. It's been around for a long time. It is, in fact, a preferred choice for production environments because of its performance. iSCSI adds a new dimension to the SCSI interface. It allows the SCSI commands to be sent via existing network cabling. What does this mean? It means that you can easily create a SAN (Storage Area Network) using your existing network infrastructure. (A SAN is an integral part of a clustered server setup.)
How Does it Work?
iSCSI requires the installation of a special piece of software, called an initiator, on the host machine. This allows the host to accommodate incoming iSCSI commands. Microsoft has released a free download for Server 2000 and Server 2003. Server 2008 comes with the iSCSI initiator included out of the box. The initiator, installed on the host, initiates and receives requests from the iSCSI target via the IP network.
In Plain English, Please?
It sounds more complicated than it is. The host machine (running the iSCSI initiator) is connected to your network. It sends special network traffic to the target machine (where the iSCSI devices are installed) to access the storage devices. The data being written to and read from the drive is encapsulated within that network traffic and sent back to the host machine. In essence, it's like having a really, really long drive cable connected from your host machine to your target machine. Since it all runs over TCP/IP (which is the same protocol used by most web traffic), there's no need to install specialized networking gear to make iSCSI work.
It Sounds Too Good to Be True!
Like a lot of innovative technology, this does sound too good to be true, which doesn't stop it from actually being true. Considerations must be taken to ensure that the performance of your iSCSI SAN meets your needs and expectations. While you don't need specialized networking hardware, you do want to use high-speed dedicated hardware for the SAN. This means gigabit Ethernet cards in your target and host machines. (This gigabit card should be in addition to the existing network card being used to access the public/internal networks.) Having such a card dedicated to the SAN traffic will help you achieve optimal performance. Isolating the SAN traffic onto a private network will also help boost your SAN's performance. Dual processors are also recommended in all of your iSCSI hosts.
Security is also a concern. By default, no security protocol is in place for IP traffic, even that being carried over an iSCSI connection. This is an obvious concern. Fortunately, CHAP and IPSec can be used to maintain security of your data being transmitted. CHAP is used as a negotiation between the host and target. If the host and target both know the secret password, the connection is established. If not, the connection is terminated. This prevents unauthorized machines from accessing your data via a direct connection, but does not protect your encapsulated data while it is in transit. For that, IPSec is required. IPSec is a security method which can be implemented on your iSCSI network to encrypt the traffic as it flows from point A to point B, protecting it from people attempting to intercept it.
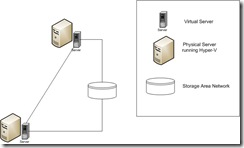
SAN and Clustering
Clustering servers requires that they have access to the same shared storage. If we go back to the diagrams from the last post, we can see that centralized storage is an integral part of the clustering scenarios I outlined.
The SAN allows both clustered servers to access the data being written. If the storage were local to one of the servers and that server failed... you can see where that goes. It renders your cluster ineffective. Thus, centralized SAN storage becomes imperative to redundancy.
You can find more information on iSCSI SAN solutions and how to set them up here. Jose Barreto, member of the Storage Solutions Division, has some great blog posts on this subject, which begin here.
Technorati Tags: iSCSI,clustering,cluster,Server 2008,virtualization
Comments
Anonymous
January 01, 2003
You can try StarWind SAN software: http://www.starwindsoftware.com/starwindAnonymous
January 01, 2003
I like to use iSCSI Target, is a free version of iSCSI Target: http://www.kernsafe.com/product.aspx?id=5 It is powerful and beautifulAnonymous
January 01, 2003
PingBack from http://www.gg-opisy.co.cc/2009/01/06/iscsi-latest-apple-peripheral-or-easy-san-continued-discussion-of-server-clusters/Anonymous
January 01, 2003
If you are an MSDN or TechNet Plus subscriber, you can now get Windows Storage Server 2008 and the Microsoft iSCSI Software Target 3.2: http://blogs.technet.com/josebda/archive/2009/05/16/windows-storage-server-2008-with-the-microsoft-iscsi-software-target-3-2-available-to-msdn-and-technet-plus-subscribers.aspxAnonymous
August 02, 2015
http://www.whatsapprank.com/2015/06/new-best-whatsapp-status-quotes-messages.html
http://www.whatsapprank.com/Anonymous
September 08, 2015
http://www.roshhashanah2015i.com/2015/09/rosh-hashanah-2015-traditional-jewish.html
http://www.roshhashanah2015i.com/2015/09/rosh-hashana-famous-quotes-messages.html
http://www.roshhashanah2015i.com/2015/09/rosh-hashanah-2015-candle-lighting.html
http://www.roshhashanah2015i.com/2015/09/jewish-new-year-2015-facebook-timeline.html
http://www.roshhashanah2015i.com/2015/07/rosh-hashanah-2015-greetings-jewish-new.htmlAnonymous
October 01, 2015
thanks for the nice post
http://www.easypnrstatus.inAnonymous
February 08, 2016
The comment has been removedAnonymous
March 05, 2016
http://www.statuswhatsapp99.org/
http://www.statuswhatsapp99.org/2014/12/best-exam-whatsapp-status.html
http://www.statuswhatsapp99.org/2014/12/very-nice-status-for-whatsapp.html
http://www.statuswhatsapp99.org/2014/11/parents-status-for-whatsapp.html
http://www.statuswhatsapp99.org/2014/10/best-whatsapp-status_8.html