Implementing VPN split tunneling for Microsoft 365
Note
This article is part of a set of articles that address Microsoft 365 optimization for remote users or when you implement network optimizations that involve IP prefix-based routing to bypass congestion points in your network infrastructure.
- For an overview of using VPN split tunneling to optimize Microsoft 365 connectivity for remote users, see Overview: VPN split tunneling for Microsoft 365.
- For a detailed list of VPN split tunneling scenarios, see Common VPN split tunneling scenarios for Microsoft 365.
- For guidance on securing Teams media traffic in VPN split tunneling environments, see Securing Teams media traffic for VPN split tunneling.
- For information about how to configure Stream and live events in VPN environments, see Special considerations for Stream and live events in VPN environments.
- For information about optimizing Microsoft 365 worldwide tenant performance for users in China, see Microsoft 365 performance optimization for China users.
Microsoft suggests a strategy to improve connectivity quickly and efficiently. This involves a few simple steps to update your network routes, allowing certain key endpoints to bypass congested VPN servers. By applying a similar or better security model at different layers, there's no need to secure all traffic at the corporate network's exit point and you can route Microsoft 365 traffic using shorter and more efficient network paths. This can usually be done within hours and can be scaled to multiple Microsoft 365 workloads as needed.
Implement VPN split tunneling
In this article, you'll find the simple steps required to migrate your VPN client architecture from a VPN forced tunnel to a VPN forced tunnel with a few trusted exceptions, VPN split tunnel model #2 in Common VPN split tunneling scenarios for Microsoft 365.
The following diagram illustrates how the recommended VPN split tunnel solution works:
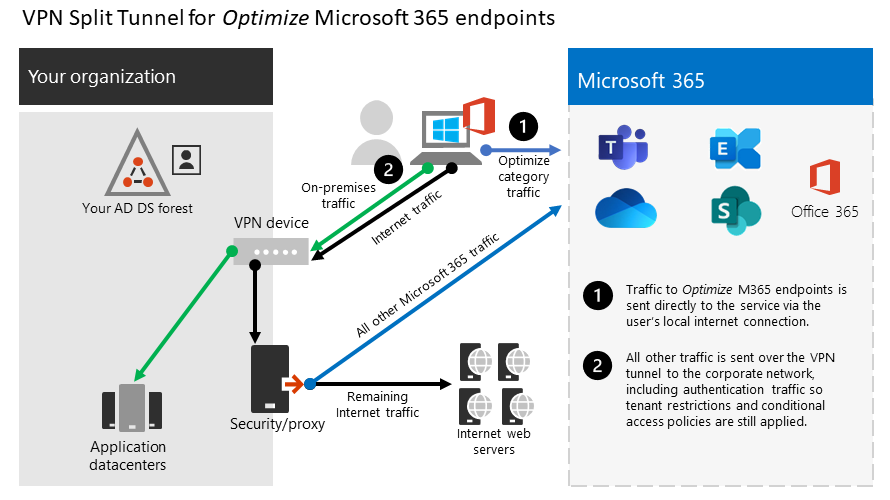
1. Identify the endpoints to optimize
In the Microsoft 365 URLs and IP address ranges article, Microsoft clearly identifies the key endpoints you need to optimize and categorizes them as Optimize. This small group of endpoints accounts for around 70% - 80% of the volume of traffic to the Microsoft 365 service including the latency sensitive endpoints such as those for Teams media. Essentially this is the traffic that we need to take special care of and is also the traffic that will put incredible pressure on traditional network paths and VPN infrastructure.
URLs in this category have the following characteristics:
- Are Microsoft owned and managed endpoints, hosted on Microsoft infrastructure
- Have published IP addresses that are dedicated for specific services
- Low rate of change
- Are bandwidth and/or latency sensitive
- Are able to have required security elements provided in the service rather than inline on the network
- Account for around 70-80% of the volume of traffic to the Microsoft 365 service
For more information about Microsoft 365 endpoints and how they're categorized and managed, see Managing Microsoft 365 endpoints.
Under most circumstances, you should only need to use URL endpoints in a browser PAC file where the endpoints are configured to be sent direct, rather than to the proxy. If you need just the URLs for the Optimize category, use the first query, or use the second query for IP prefixes.
Optimize URLs
(invoke-restmethod -Uri ("https://endpoints.office.com/endpoints/WorldWide?clientrequestid=" + ([GUID]::NewGuid()).Guid)) | ?{$_.category -eq "Optimize" -and $_.urls} | select -unique -ExpandProperty urls
Optimize IP address ranges
(invoke-restmethod -Uri ("https://endpoints.office.com/endpoints/WorldWide?clientrequestid=" + ([GUID]::NewGuid()).Guid)) | ?{$_.category -eq "Optimize" -and $_.ips} | select -unique -ExpandProperty ips
2. Implementing split tunnel for Microsoft 365 endpoints
Now that we have identified these critical endpoints, we need to divert them away from the VPN tunnel and allow them to use the user's local Internet connection to connect directly to the service. The manner in which this is accomplished will vary depending on the VPN product and machine platform used but most VPN solutions allow some configuration of policy to apply this logic. For information VPN platform-specific split tunnel guidance, see HOWTO guides for common VPN platforms.
If you wish to test the solution manually, you can execute the following PowerShell example to emulate the solution at the route table level. This example adds a route for each of the Teams Media IP subnets into the route table. You can test Teams media performance before and after using the Teams network assessment tool and observe the difference in routes for the specified endpoints.
Example: Add Teams Media IP subnets into the route table
$intIndex = "" # index of the interface connected to the internet
$gateway = "" # default gateway of that interface
$destPrefix = " 52.112.0.0/14, 52.122.0.0/15, 2603:1063::/38" # Teams Media endpoints
# Add routes to the route table
foreach ($prefix in $destPrefix) {New-NetRoute -DestinationPrefix $prefix -InterfaceIndex $intIndex -NextHop $gateway}
In the preceding script, $intIndex is the index of the interface connected to the internet (find by running get-netadapter in PowerShell; look for the value of ifIndex) and $gateway is the default gateway of that interface (find by running ipconfig in a command prompt or (Get-NetIPConfiguration | Foreach IPv4DefaultGateway).NextHop in PowerShell).
Once you have added the routes, you can confirm that the route table is correct by running route print in a command prompt or PowerShell.
To add routes for all current IP address ranges in the Optimize category, you can use the following script variation to query the Microsoft 365 IP and URL web service for the current set of Optimize IP subnets and add them to the route table.
Example: Add all Optimize subnets into the route table
$intIndex = "" # index of the interface connected to the internet
$gateway = "" # default gateway of that interface
# Query the web service for IPs in the Optimize category
$ep = Invoke-RestMethod ("https://endpoints.office.com/endpoints/worldwide?clientrequestid=" + ([GUID]::NewGuid()).Guid)
# Output only IPv4 Optimize IPs to $optimizeIps
$destPrefix = $ep | where {$_.category -eq "Optimize"} | Select-Object -ExpandProperty ips | Where-Object { $_ -like '*.*' }
# Add routes to the route table
foreach ($prefix in $destPrefix) {New-NetRoute -DestinationPrefix $prefix -InterfaceIndex $intIndex -NextHop $gateway}
If you inadvertently added routes with incorrect parameters or simply wish to revert your changes, you can remove the routes you just added with the following command:
foreach ($prefix in $destPrefix) {Remove-NetRoute -DestinationPrefix $prefix -InterfaceIndex $intIndex -NextHop $gateway}
The VPN client should be configured so that traffic to the Optimize IPs are routed in this way. This allows the traffic to utilize local Microsoft resources such as Microsoft 365 Service Front Doors such as the Azure Front Door that delivers Microsoft 365 services and connectivity endpoints as close to your users as possible. This allows us to deliver high performance levels to users wherever they are in the world and takes full advantage of Microsoft's world class global network, which is likely within a few milliseconds of your users' direct egress.
HOWTO guides for common VPN platforms
This section provides links to detailed guides for implementing split tunneling for Microsoft 365 traffic from the most common partners in this space. We'll add more guides as they become available.
- Windows 10 VPN client: Optimizing Microsoft 365 traffic for remote workers with the native Windows 10 VPN client
- Cisco Anyconnect: Optimize Anyconnect Split Tunnel for Office365
- Palo Alto GlobalProtect: Optimizing Microsoft 365 Traffic via VPN Split Tunnel Exclude Access Route
- F5 Networks BIG-IP APM: Optimizing Microsoft 365 traffic on Remote Access through VPNs when using BIG-IP APM
- Citrix Gateway: Optimizing Citrix Gateway VPN split tunnel for Office365
- Pulse Secure: VPN Tunneling: How to configure split tunneling to exclude Microsoft 365 applications
- Check Point VPN: How to configure Split Tunnel for Microsoft 365 and other SaaS Applications
Related articles
Overview: VPN split tunneling for Microsoft 365
Common VPN split tunneling scenarios for Microsoft 365
Securing Teams media traffic for VPN split tunneling
Special considerations for Stream and live events in VPN environments
Microsoft 365 performance optimization for China users
Microsoft 365 Network Connectivity Principles
Assessing Microsoft 365 network connectivity
Microsoft 365 network and performance tuning
Enhancing VPN performance at Microsoft: using Windows 10 VPN profiles to allow auto-on connections
Running on VPN: How Microsoft is keeping its remote workforce connected