Migrate Microsoft Entra Connect Sync Group Writeback v2 to Microsoft Entra Cloud Sync
Important
The public preview of Group Writeback v2 in Microsoft Entra Connect Sync is no longer available as of June 30, 2024. This feature was discontinued on this date, and you're no longer supported in Microsoft Entra Connect Sync to provision cloud security groups to Active Directory. The feature continues to operate beyond the discontinuation date; however, it no longer receives support and might cease functioning at any time without notice.
We offer similar functionality in Microsoft Entra Cloud Sync called Group Provision to Active Directory that you can use instead of Group Writeback v2 for provisioning cloud security groups to Active Directory. We're working on enhancing this functionality in Microsoft Entra Cloud Sync along with other new features that we're developing in Microsoft Entra Cloud Sync.
Customers who use this preview feature in Microsoft Entra Connect Sync should switch their configuration from Microsoft Entra Connect Sync to Microsoft Entra Cloud Sync. You can choose to move all your hybrid sync to Microsoft Entra Cloud Sync (if it supports your needs). You can also run Microsoft Entra Cloud Sync side by side and move only cloud security group provisioning to Active Directory onto Microsoft Entra Cloud Sync.
For customers who provision Microsoft 365 groups to Active Directory, you can keep using Group Writeback v1 for this capability.
You can evaluate moving exclusively to Microsoft Entra Cloud Sync by using the user synchronization wizard.
This article describes how to migrate Group Writeback by using Microsoft Entra Connect Sync (formerly Azure Active Directory Connect) to Microsoft Entra Cloud Sync. This scenario is only for customers who are currently using Microsoft Entra Connect Group Writeback v2. The process outlined in this article pertains only to cloud-created security groups that are written back with a universal scope.
This scenario is only supported for:
- Cloud-created security groups.
- Groups written back to Active Directory with the scope of universal.
Mail-enabled groups and distribution lists written back to Active Directory continue to work with Microsoft Entra Connect Group Writeback but revert to the behavior of Group Writeback v1. In this scenario, after you disable Group Writeback v2, all Microsoft 365 groups are written back to Active Directory independently of the Writeback Enabled setting in the Microsoft Entra admin center. For more information, see Provision to Active Directory with Microsoft Entra Cloud Sync FAQ.
Prerequisites
A Microsoft Entra account with at least a Hybrid Identity administrator role.
An on-premises Active Directory account with at least domain administrator permissions.
Required to access the
adminDescriptionattribute and copy it to themsDS-ExternalDirectoryObjectIdattribute.On-premises Active Directory Domain Services environment with Windows Server 2016 operating system or later.
Required for the Active Directory Schema attribute
msDS-ExternalDirectoryObjectId.Provisioning agent with build version 1.1.1367.0 or later.
The provisioning agent must be able to communicate with the domain controllers on ports TCP/389 (LDAP) and TCP/3268 (global catalog).
Required for global catalog lookup to filter out invalid membership references.
Naming convention for groups written back
By default, Microsoft Entra Connect Sync uses the following format when naming groups are written back:
- Default format:
CN=Group_<guid>,OU=<container>,DC=<domain component>,DC=\<domain component> - Example:
CN=Group_3a5c3221-c465-48c0-95b8-e9305786a271,OU=WritebackContainer,DC=contoso,DC=com
To make it easier to find groups being written back from Microsoft Entra ID to Active Directory, Microsoft Entra Connect Sync added an option to write back the group name by using the cloud display name. To use this option, select Writeback Group Distinguished Name with Cloud Display Name during initial setup of Group Writeback v2. If this feature is enabled, Microsoft Entra Connect uses the following new format instead of the default format:
- New format:
CN=<display name>_<last 12 digits of object ID>,OU=<container>,DC=<domain component>,DC=\<domain component> - Example:
CN=Sales_e9305786a271,OU=WritebackContainer,DC=contoso,DC=com
By default, Microsoft Entra Cloud Sync uses the new format, even if the Writeback Group Distinguished Name with Cloud Display Name feature isn't enabled in Microsoft Entra Connect Sync. If you use the default Microsoft Entra Connect Sync naming and then migrate the group so that it's managed by Microsoft Entra Cloud Sync, the group is renamed to the new format. Use the following section to allow Microsoft Entra Cloud Sync to use the default format from Microsoft Entra Connect.
Use the default format
If you want Microsoft Entra Cloud Sync to use the same default format as Microsoft Entra Connect Sync, you need to modify the attribute flow expression for the CN attribute. The two possible mappings are:
| Expression | Syntax | Description |
|---|---|---|
Cloud sync default expression by using DisplayName |
Append(Append(Left(Trim([displayName]), 51), "_"), Mid([objectId], 25, 12)) |
The default expression used by Microsoft Entra Cloud Sync (that is, the new format). |
Cloud sync new expression without using DisplayName |
Append("Group_", [objectId]) |
The new expression to use the default format from Microsoft Entra Connect Sync. |
For more information, see Add an attribute mapping - Microsoft Entra ID to Active Directory.
Step 1: Copy adminDescription to msDS-ExternalDirectoryObjectID
To validate group membership references, Microsoft Entra Cloud Sync must query the Active Directory global catalog for the msDS-ExternalDirectoryObjectID attribute. This indexed attribute replicates across all global catalogs within the Active Directory forest.
In your on-premises environment, open ADSI Edit.
Copy the value that's in the group's
adminDescriptionattribute.Paste the value in the
msDS-ExternalDirectoryObjectIDattribute.
You can use the following PowerShell script to help automate this step. This script takes all of the groups in the OU=Groups,DC=Contoso,DC=com container and copies the adminDescription attribute value to the msDS-ExternalDirectoryObjectID attribute value. Before you use this script, update the variable $gwbOU with the DistinguishedName value of your group writeback's target organizational unit (OU).
# Provide the DistinguishedName of your Group Writeback target OU
$gwbOU = 'OU=Groups,DC=Contoso,DC=com'
# Get all groups written back to Active Directory
$properties = @('displayName', 'Samaccountname', 'adminDescription', 'msDS-ExternalDirectoryObjectID')
$groups = Get-ADGroup -Filter * -SearchBase $gwbOU -Properties $properties |
Where-Object {$_.adminDescription -ne $null} |
Select-Object $properties
# Set msDS-ExternalDirectoryObjectID for all groups written back to Active Directory
foreach ($group in $groups) {
Set-ADGroup -Identity $group.Samaccountname -Add @{('msDS-ExternalDirectoryObjectID') = $group.adminDescription}
}
You can use the following PowerShell script to check the results of the preceding script. You can also confirm that all groups have the adminDescription value equal to the msDS-ExternalDirectoryObjectID value.
# Provide the DistinguishedName of your Group Writeback target OU
$gwbOU = 'OU=Groups,DC=Contoso,DC=com'
# Get all groups written back to Active Directory
$properties = @('displayName', 'Samaccountname', 'adminDescription', 'msDS-ExternalDirectoryObjectID')
$groups = Get-ADGroup -Filter * -SearchBase $gwbOU -Properties $properties |
Where-Object {$_.adminDescription -ne $null} |
Select-Object $properties
$groups | select displayName, adminDescription, 'msDS-ExternalDirectoryObjectID', @{Name='Equal';Expression={$_.adminDescription -eq $_.'msDS-ExternalDirectoryObjectID'}}
Step 2: Place the Microsoft Entra Connect Sync server in staging mode and disable the sync scheduler
Start the Microsoft Entra Connect Sync wizard.
Select Configure.
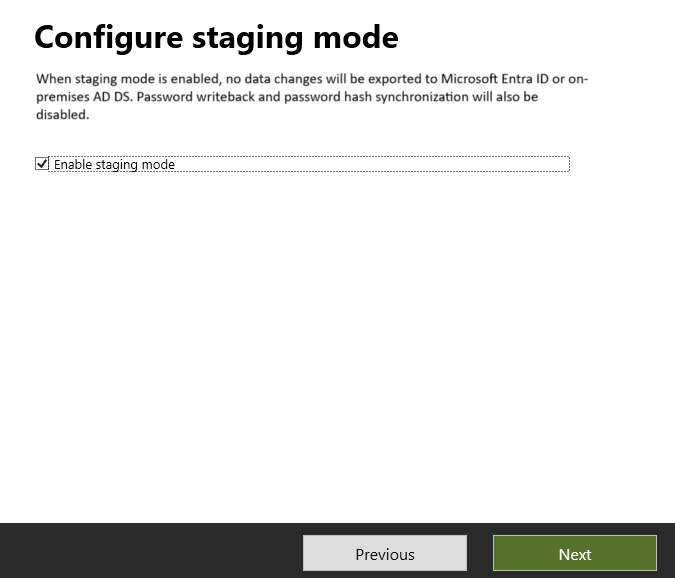
Select Configure staging mode and select Next.
Enter Microsoft Entra credentials.
Select the Enable staging mode checkbox and select Next.
Select Configure.
Select Exit.
On your Microsoft Entra Connect server, open a PowerShell prompt as an administrator.
Disable the sync scheduler:
Set-ADSyncScheduler -SyncCycleEnabled $false
Step 3: Create a custom group inbound rule
In the Microsoft Entra Connect Synchronization Rules Editor, you create an inbound sync rule that filters out groups that have NULL for the mail attribute. The inbound sync rule is a join rule with a target attribute of cloudNoFlow. This rule tells Microsoft Entra Connect not to synchronize attributes for these groups. To create this sync rule, you can opt to use the user interface or create it via PowerShell with the provided script.
Create a custom group inbound rule in the user interface
On the Start menu, start the Synchronization Rules Editor.
Under Direction, select Inbound from the dropdown list, and select Add new rule.
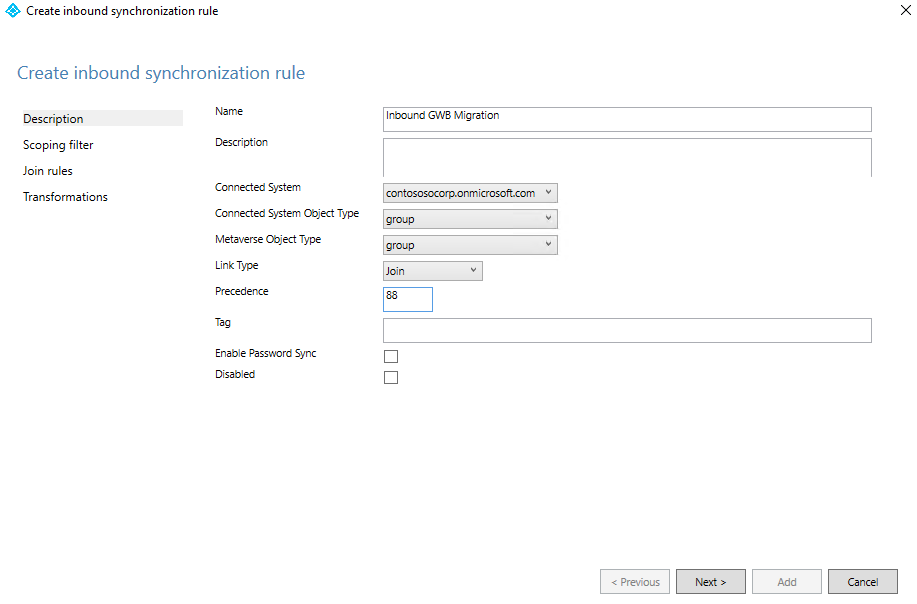
On the Description page, enter the following values and select Next:
- Name: Give the rule a meaningful name.
- Description: Add a meaningful description.
- Connected System: Choose the Microsoft Entra connector for which you're writing the custom sync rule.
- Connected System Object Type: Select group.
- Metaverse Object Type: Select group.
- Link Type: Select Join.
- Precedence: Provide a value that's unique in the system. We recommend that you use a value lower than 100 so that it takes precedence over the default rules.
- Tag: Leave the field empty.
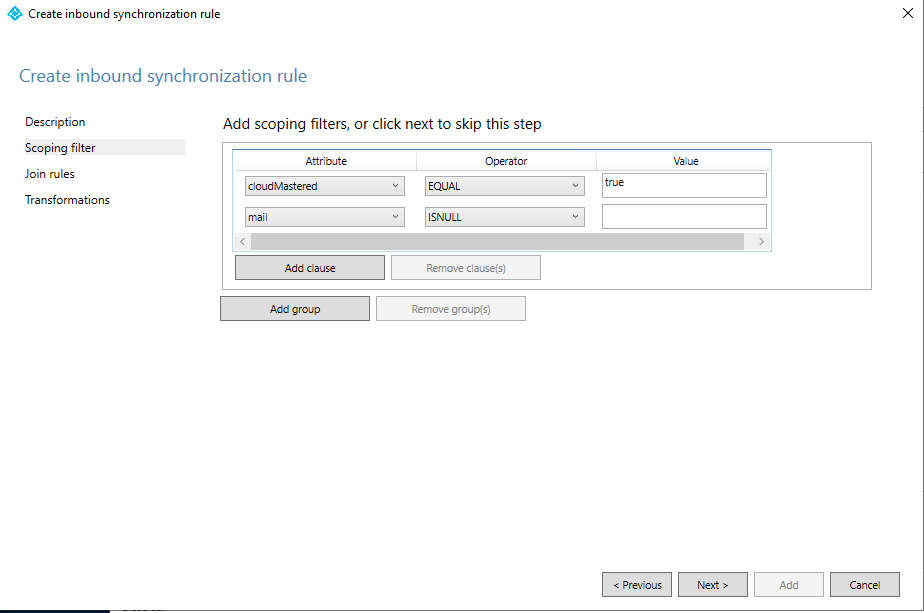
On the Scoping filter page, add the following values and select Next:
Attribute Operator Value cloudMasteredEQUALtruemailISNULLOn the Join rules page, select Next.
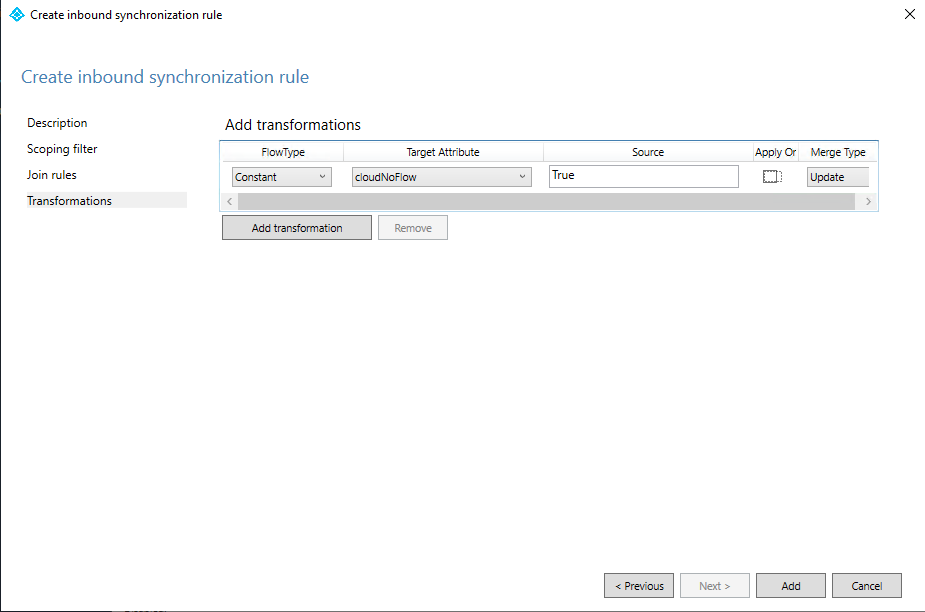
On the Add transformations page, for FlowType, select Constant. For Target Attribute, select cloudNoFlow. For Source, select True.
Select Add.
Create a custom group inbound rule in PowerShell
On your Microsoft Entra Connect server, open a PowerShell prompt as an administrator.
Import the module.
Import-Module ADSyncProvide a unique value for the sync rule precedence (0-99).
[int] $inboundSyncRulePrecedence = 88Run the following script:
New-ADSyncRule ` -Name 'In from AAD - Group SOAinAAD coexistence with Cloud Sync' ` -Identifier 'e4eae1c9-b9bc-4328-ade9-df871cdd3027' ` -Description 'https://learn.microsoft.com/entra/identity/hybrid/cloud-sync/migrate-group-writeback' ` -Direction 'Inbound' ` -Precedence $inboundSyncRulePrecedence ` -PrecedenceAfter '00000000-0000-0000-0000-000000000000' ` -PrecedenceBefore '00000000-0000-0000-0000-000000000000' ` -SourceObjectType 'group' ` -TargetObjectType 'group' ` -Connector 'b891884f-051e-4a83-95af-2544101c9083' ` -LinkType 'Join' ` -SoftDeleteExpiryInterval 0 ` -ImmutableTag '' ` -OutVariable syncRule Add-ADSyncAttributeFlowMapping ` -SynchronizationRule $syncRule[0] ` -Source @('true') ` -Destination 'cloudNoFlow' ` -FlowType 'Constant' ` -ValueMergeType 'Update' ` -OutVariable syncRule New-Object ` -TypeName 'Microsoft.IdentityManagement.PowerShell.ObjectModel.ScopeCondition' ` -ArgumentList 'cloudMastered','true','EQUAL' ` -OutVariable condition0 New-Object ` -TypeName 'Microsoft.IdentityManagement.PowerShell.ObjectModel.ScopeCondition' ` -ArgumentList 'mail','','ISNULL' ` -OutVariable condition1 Add-ADSyncScopeConditionGroup ` -SynchronizationRule $syncRule[0] ` -ScopeConditions @($condition0[0],$condition1[0]) ` -OutVariable syncRule Add-ADSyncRule ` -SynchronizationRule $syncRule[0] Get-ADSyncRule ` -Identifier 'e4eae1c9-b9bc-4328-ade9-df871cdd3027'
Step 4: Create a custom group outbound rule
You also need an outbound sync rule with a link type of JoinNoFlow and the scoping filter that has the cloudNoFlow attribute set to True. This rule tells Microsoft Entra Connect not to synchronize attributes for these groups. To create this sync rule, you can opt to use the user interface or create it via PowerShell with the provided script.
Create a custom group outbound rule in the user interface
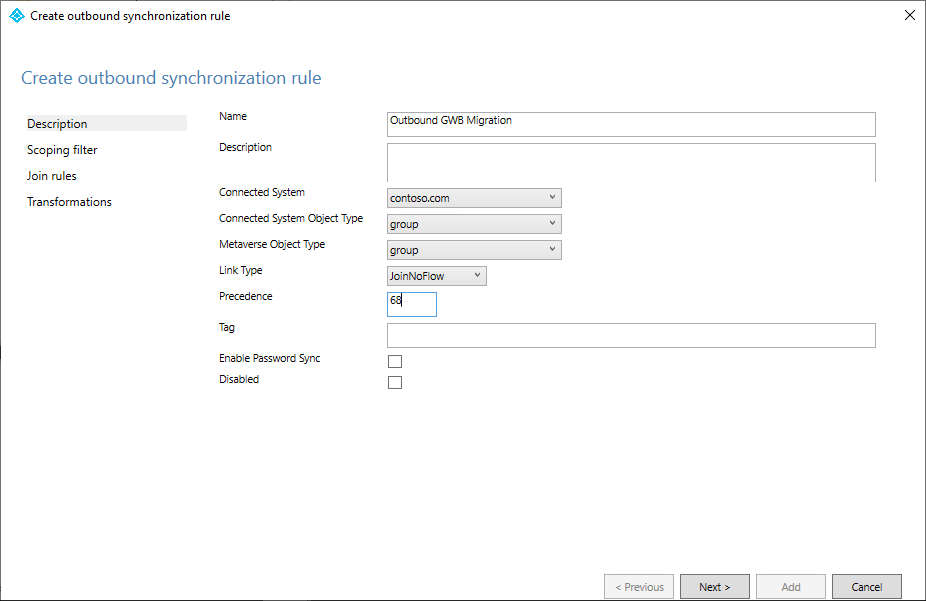
Under Direction, select Outbound from the dropdown list, and then select Add rule.
On the Description page, enter the following values and select Next:
- Name: Give the rule a meaningful name.
- Description: Add a meaningful description.
- Connected System: Choose the Active Directory connector for which you're writing the custom sync rule.
- Connected System Object Type: Select group.
- Metaverse Object Type: Select group.
- Link Type: Select JoinNoFlow.
- Precedence: Provide a value that's unique in the system. We recommend that you use a value lower than 100 so that it takes precedence over the default rules.
- Tag: Leave the field empty.
On the Scoping filter page, for Attribute, select cloudNoFlow. For Operator select EQUAL. For Value, select True. Then select Next.
On the Join rules page, select Next.
On the Transformations page, select Add.
Create a custom group inbound rule in PowerShell
On your Microsoft Entra Connect server, open a PowerShell prompt as an administrator.
Import the module.
Import-Module ADSyncProvide a unique value for the sync rule precedence (0-99).
[int] $outboundSyncRulePrecedence = 89Get the Active Directory connector for Group Writeback.
$connectorAD = Get-ADSyncConnector -Name "Contoso.com"Run the following script:
New-ADSyncRule ` -Name 'Out to AD - Group SOAinAAD coexistence with Cloud Sync' ` -Identifier '419fda18-75bb-4e23-b947-8b06e7246551' ` -Description 'https://learn.microsoft.com/entra/identity/hybrid/cloud-sync/migrate-group-writeback' ` -Direction 'Outbound' ` -Precedence $outboundSyncRulePrecedence ` -PrecedenceAfter '00000000-0000-0000-0000-000000000000' ` -PrecedenceBefore '00000000-0000-0000-0000-000000000000' ` -SourceObjectType 'group' ` -TargetObjectType 'group' ` -Connector $connectorAD.Identifier ` -LinkType 'JoinNoFlow' ` -SoftDeleteExpiryInterval 0 ` -ImmutableTag '' ` -OutVariable syncRule New-Object ` -TypeName 'Microsoft.IdentityManagement.PowerShell.ObjectModel.ScopeCondition' ` -ArgumentList 'cloudNoFlow','true','EQUAL' ` -OutVariable condition0 Add-ADSyncScopeConditionGroup ` -SynchronizationRule $syncRule[0] ` -ScopeConditions @($condition0[0]) ` -OutVariable syncRule Add-ADSyncRule ` -SynchronizationRule $syncRule[0] Get-ADSyncRule ` -Identifier '419fda18-75bb-4e23-b947-8b06e7246551'
Step 5: Use PowerShell to finish configuration
On your Microsoft Entra Connect server, open a PowerShell prompt as an administrator.
Import the
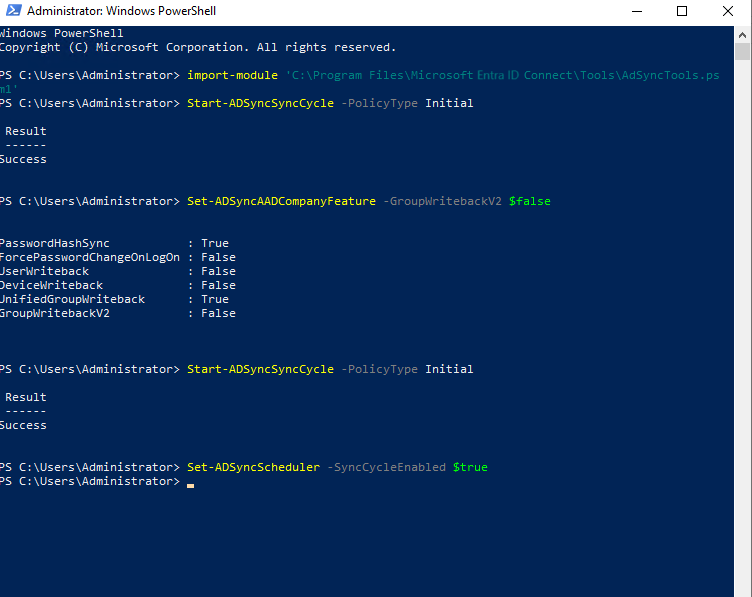
ADSyncmodule:Import-Module ADSyncRun a full sync cycle:
Start-ADSyncSyncCycle -PolicyType InitialDisable the Group Writeback feature for the tenant.
Warning
This operation is irreversible. After you disable Group Writeback v2, all Microsoft 365 groups are written back to Active Directory, independently of the Writeback Enabled setting in the Microsoft Entra admin center.
Set-ADSyncAADCompanyFeature -GroupWritebackV2 $falseRun a full sync cycle again:
Start-ADSyncSyncCycle -PolicyType InitialReenable the sync scheduler:
Set-ADSyncScheduler -SyncCycleEnabled $true
Step 6: Remove the Microsoft Entra Connect Sync server from staging mode
- Start the Microsoft Entra Connect Sync wizard.
- Select Configure.
- Select Configure staging mode and select Next.
- Enter Microsoft Entra credentials.
- Clear the Enable staging mode checkbox and select Next.
- Select Configure.
- Select Exit.
Step 7: Configure Microsoft Entra Cloud Sync
Now that the groups are removed from the synchronization scope of Microsoft Entra Connect Sync, you can set up and configure Microsoft Entra Cloud Sync to take over synchronization of the security groups. For more information, see Provision groups to Active Directory by using Microsoft Entra Cloud Sync.