Configure permission classifications
In this article, you learn how to configure permissions classifications in Microsoft Entra ID. Permission classifications allow you to identify the impact that different permissions have based on your organization's policies and risk evaluations. For example, you can use permission classifications in consent policies to identify the set of permissions that users are allowed to consent to.
Three permission classifications are supported: "Low," "Medium" (preview), and "High" (preview). Currently, only delegated permissions that don't require admin consent can be classified.
The minimum permissions needed to do basic sign-in are openid, profile, email, and offline_access, which are all delegated permissions on the Microsoft Graph. With these permissions an app can read details of the signed-in user's profile, and can maintain this access even when the user is no longer using the app.
Prerequisites
To configure permission classifications, you need:
- An Azure account with an active subscription. Create an account for free.
- One of the following roles: Application Administrator, or Cloud Application Administrator
Manage permission classifications
Follow these steps to classify permissions using the Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > Consent and permissions > Permission classifications.
- Choose the tab for the permission classification you'd like to update.
- Choose Add permissions to classify another permission.
- Select the API and then select one or more delegated permissions.
In this example, we classify the minimum set of permission required for single sign-on:
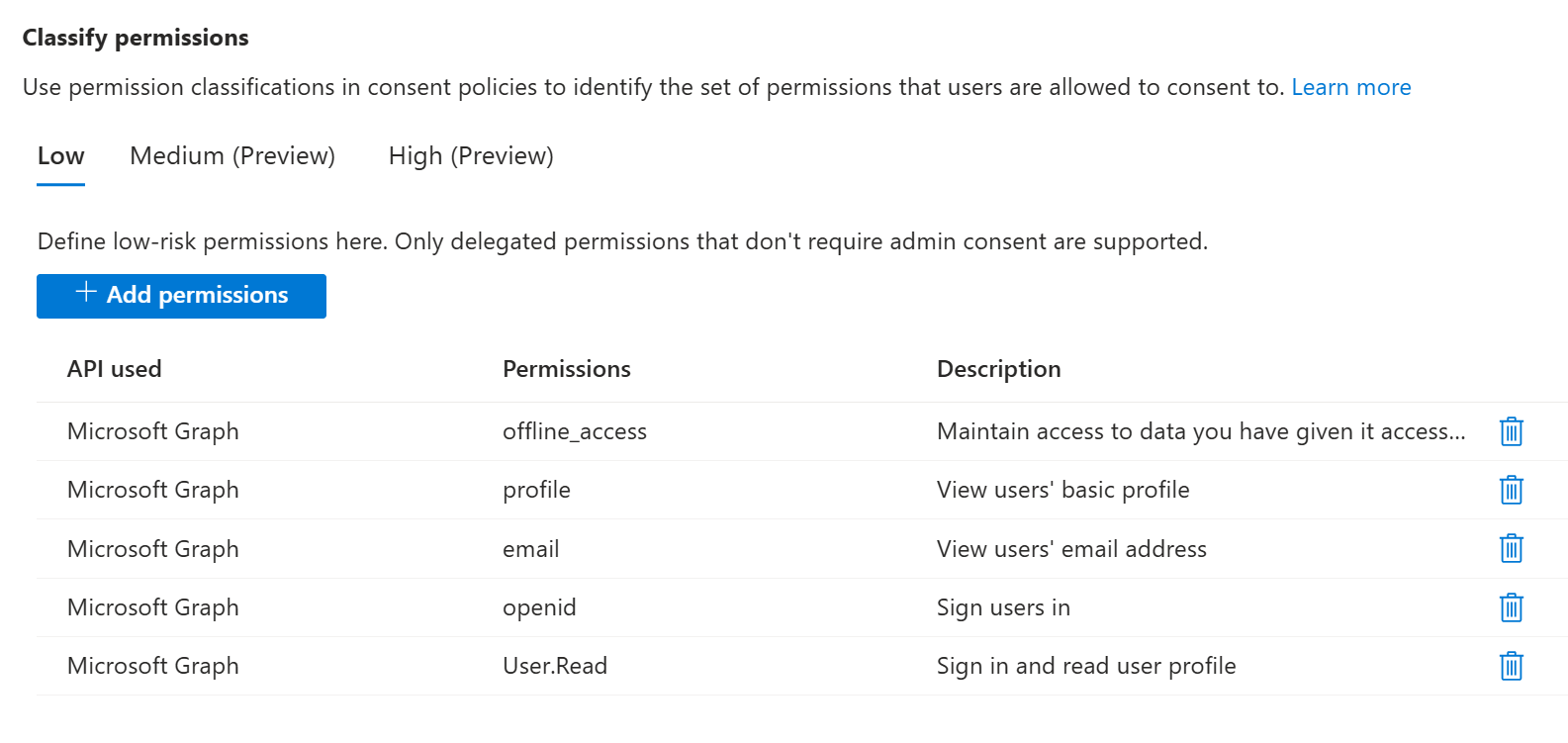
You can use the latest Microsoft Entra PowerShell to classify permissions. Permission classifications are configured on the ServicePrincipal object of the API that publishes the permissions.
Run the following command to connect to Microsoft Entra PowerShell. To consent to the required scopes, sign in as at least a Cloud Application Administrator.
Connect-Entra -scopes "Policy.ReadWrite.PermissionGrant", "Application.Read.All"
List the current permission classifications using Microsoft Entra PowerShell
Retrieve the ServicePrincipal object for the API. Here we retrieve the ServicePrincipal object for the Microsoft Graph API:
$serviceprincipal = Get-EntraServicePrincipal ` -Filter "servicePrincipalNames/any(n:n eq 'https://graph.microsoft.com')"Read the delegated permission classifications for the API:
Get-EntraServicePrincipalDelegatedPermissionClassification ` -ServicePrincipalId $serviceprincipal.ObjectId | Format-Table Id, PermissionName, Classification
Classify a permission as "Low impact" using Microsoft Entra PowerShell
Retrieve the ServicePrincipal object for the API. Here we retrieve the ServicePrincipal object for the Microsoft Graph API:
$serviceprincipal = Get-EntraServicePrincipal ` -Filter "servicePrincipalNames/any(n:n eq 'https://graph.microsoft.com')"Find the delegated permission you would like to classify:
$delegatedPermission = $serviceprincipal.oauth2PermissionScopes | Where-Object { $_.Value -eq "User.ReadBasic.All" }Set the permission classification using the permission name and ID:
Add-EntraServicePrincipalDelegatedPermissionClassification ` -ServicePrincipalId $serviceprincipal.ObjectId ` -PermissionId $delegatedPermission.Id ` -PermissionName $delegatedPermission.Value ` -Classification "low"
Remove a delegated permission classification using Microsoft Entra PowerShell
Retrieve the ServicePrincipal object for the API. Here we retrieve the ServicePrincipal object for the Microsoft Graph API:
$serviceprincipal = Get-EntraServicePrincipal ` -Filter "servicePrincipalNames/any(n:n eq 'https://graph.microsoft.com')"Find the delegated permission classification you wish to remove:
$classifications = Get-EntraServicePrincipalDelegatedPermissionClassification ` -ServicePrincipalId $serviceprincipal.ObjectId $classificationToRemove = $classifications | Where-Object {$_.PermissionName -eq "User.ReadBasic.All"}Delete the permission classification:
Remove-EntraServicePrincipalDelegatedPermissionClassification ` -ServicePrincipalId $serviceprincipal.ObjectId ` -Id $classificationToRemove.Id
You can use Microsoft Graph PowerShell, to classify permissions. Permission classifications are configured on the ServicePrincipal object of the API that publishes the permissions.
Run the following command to connect to Microsoft Graph PowerShell. To consent to the required scopes, sign in as at least a Cloud Application Administrator.
Connect-MgGraph -Scopes "Policy.ReadWrite.PermissionGrant", "Application.Read.All"
List current permission classifications for an API using Microsoft Graph PowerShell
Retrieve the servicePrincipal object for the API:
$serviceprincipal = Get-MgServicePrincipal -Filter "displayName eq 'Microsoft Graph'"Read the delegated permission classifications for the API:
Get-MgServicePrincipalDelegatedPermissionClassification -ServicePrincipalId $serviceprincipal.Id
Classify a permission as "Low impact" using Microsoft Graph PowerShell
Retrieve the servicePrincipal object for the API:
$serviceprincipal = Get-MgServicePrincipal -Filter "displayName eq 'Microsoft Graph'"Find the delegated permission you would like to classify:
$delegatedPermission = $serviceprincipal.Oauth2PermissionScopes | Where-Object {$_.Value -eq "openid"}Set the permission classification:
$params = @{ PermissionId = $delegatedPermission.Id PermissionName = $delegatedPermission.Value Classification = "Low" } New-MgServicePrincipalDelegatedPermissionClassification -ServicePrincipalId $serviceprincipal.Id -BodyParameter $params
Remove a delegated permission classification using Microsoft Graph PowerShell
Retrieve the servicePrincipal object for the API:
$serviceprincipal = Get-MgServicePrincipal -Filter "displayName eq 'Microsoft Graph'"Find the delegated permission classification you wish to remove:
$classifications = Get-MgServicePrincipalDelegatedPermissionClassification -ServicePrincipalId $serviceprincipal.Id $classificationToRemove = $classifications | Where-Object {$_.PermissionName -eq "openid"}Delete the permission classification:
Remove-MgServicePrincipalDelegatedPermissionClassification -DelegatedPermissionClassificationId $classificationToRemove.Id -ServicePrincipalId $serviceprincipal.id
To configure permissions classifications for an enterprise application, sign in to Graph Explorer as at least a Cloud Application Administrator.
You need to consent to the Policy.ReadWrite.PermissionGrant and Application.Read.All permissions.
Run the following queries on Microsoft Graph explorer to add a delegated permissions classification for an application.
List current permission classifications for an API using Microsoft Graph API
List current permission classifications for an API using the following Microsoft Graph API call.
GET https://graph.microsoft.com/v1.0/servicePrincipals(appId='00000003-0000-0000-c000-000000000000')/delegatedPermissionClassifications
Classify a permission as "Low impact" using Microsoft Graph API
In the following example, we classify the permission as "low impact."
Add a delegated permission classification for an API using the following Microsoft Graph API call.
POST https://graph.microsoft.com/v1.0/servicePrincipals(appId='00000003-0000-0000-c000-000000000000')/delegatedPermissionClassifications
Content-type: application/json
{
"permissionId": "b4e74841-8e56-480b-be8b-910348b18b4c",
"classification": "low"
}
Remove a delegated permission classification using Microsoft Graph API
Run the following query on Microsoft Graph explorer to remove a delegated permissions classification for an API.
DELETE https://graph.microsoft.com/v1.0/servicePrincipals(appId='00000003-0000-0000-c000-000000000000')/delegatedPermissionClassifications/QUjntFaOC0i-i5EDSLGLTAE