Tutorial: Configure Conditional Access policies in Cloudflare Access
With Conditional Access, administrators enforce policies on application and user policies in Microsoft Entra ID. Conditional Access brings together identity-driven signals, to make decisions, and enforce organizational policies. Cloudflare Access creates access to self-hosted, software as a service (SaaS), or nonweb applications.
Learn more: What is Conditional Access?
Prerequisites
- A Microsoft Entra subscription
- If you don't have one, get an Azure free account
- A Microsoft Entra tenant linked to the Microsoft Entra subscription
- One of the following roles: Cloud Application Administrator, or Application Administrator.
- Configured users in the Microsoft Entra subscription
- A Cloudflare account
- Go to
dash.cloudflare.comto Get started with Cloudflare
- Go to
Scenario architecture
- Microsoft Entra ID - Identity Provider (IdP) that verifies user credentials and Conditional Access
- Application - You created for IdP integration
- Cloudflare Access - Provides access to applications
Set up an identity provider
Go to developers.cloudflare.com to set up Microsoft Entra ID as an IdP.
Note
It's recommended you name the IdP integration in relation to the target application. For example, Microsoft Entra ID - Customer management portal.
Configure Conditional Access
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > App registrations > All applications
Select the application you created.
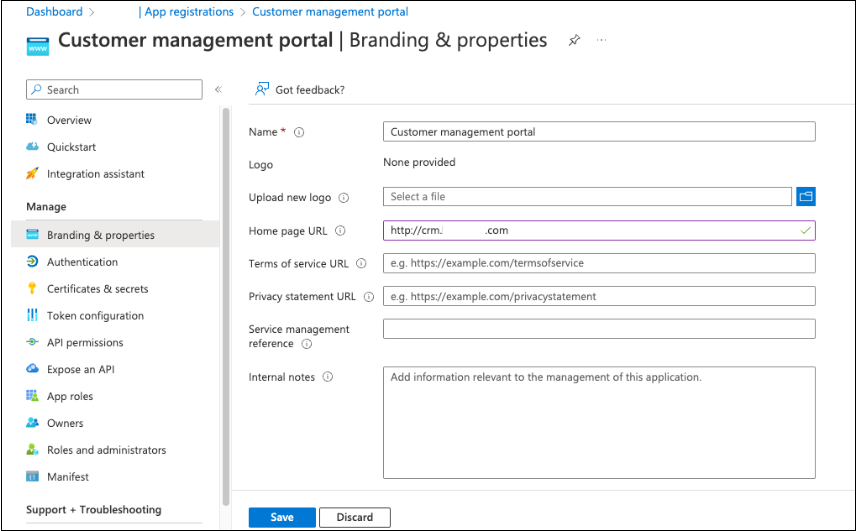
Go to Branding & properties.
For Home page URL, enter the application hostname.
Browse to Identity > Applications > Enterprise applications > All applications.
Select your application.
Select Properties.
For Visible to users, select Yes. This action enables the app to appear in App Launcher and in My Apps.
Under Security, select Conditional Access.
Create and enable other policies for the application.
Create a Cloudflare Access application
Enforce Conditional Access policies on a Cloudflare Access application.
Go to
dash.cloudflare.comto sign in to Cloudflare.In Zero Trust, go to Access.
Select Applications.
In Application domain, enter the protected application target URL.
For Identity providers, select the IdP integration.
Create an Access policy. See, Access policies and the following example.
Note
Reuse the IdP integration for other applications if they require the same Conditional Access policies. For example, a baseline IdP integration with a Conditional Access policy requiring multifactor authentication and a modern authentication client. If an application requires specific Conditional Access policies, set up a dedicated IdP instance for that application.