Deploy Microsoft Defender for Endpoint on Linux manually
Applies to:
- Microsoft Defender for Endpoint Server
- Microsoft Defender for Servers
Want to experience Defender for Endpoint? Sign up for a free trial.
Tip
Looking for advanced guidance on deploying Microsoft Defender for Endpoint on Linux? See Advanced deployment guide on Defender for Endpoint on Linux.
This article describes how to deploy Microsoft Defender for Endpoint on Linux manually. A successful deployment requires the completion of all of the following tasks:
- Prerequisites and system requirements
- Configure the Linux software repository
- Application installation
- Download the onboarding package
- Client configuration
Prerequisites and system requirements
Before you begin, see Microsoft Defender for Endpoint on Linux for a description of prerequisites and system requirements for the current software version.
Warning
Upgrading your operating system to a new major version after the product installation requires the product to be reinstalled. You need to Uninstall the existing Defender for Endpoint on Linux, upgrade the operating system, and then reconfigure Defender for Endpoint on Linux following the below steps.
Configure the Linux software repository
Defender for Endpoint on Linux can be deployed from one of the following channels (denoted as [channel]): insiders-fast, insiders-slow, or prod. Each of these channels corresponds to a Linux software repository. The instructions in this article describe configuring your device to use one of these repositories.
The choice of the channel determines the type and frequency of updates that are offered to your device. Devices in insiders-fast are the first ones to receive updates and new features, followed later by insiders-slow and lastly by prod.
In order to preview new features and provide early feedback, it's recommended that you configure some devices in your enterprise to use either insiders-fast or insiders-slow.
Warning
Switching the channel after the initial installation requires the product to be reinstalled. To switch the product channel: uninstall the existing package, reconfigure your device to use the new channel, and follow the steps in this document to install the package from the new location.
RHEL and variants (CentOS, Fedora, Oracle Linux, Amazon Linux 2, Rocky, and Alma)
Install
yum-utilsif it isn't installed yet:sudo yum install yum-utilsLocate the correct package for your distribution and version. Use the following table to help guide you in locating the package:
Distro & version Package Alma 8.4 and higher https://packages.microsoft.com/config/alma/8/prod.repo Alma 9.2 and higher https://packages.microsoft.com/config/alma/9/prod.repo RHEL/Centos/Oracle 9.0-9.8 https://packages.microsoft.com/config/rhel/9/prod.repo RHEL/Centos/Oracle 8.0-8.10 https://packages.microsoft.com/config/rhel/8/prod.repo RHEL/Centos/Oracle 7.2-7.9 & Amazon Linux 2 https://packages.microsoft.com/config/rhel/7.2/prod.repo Amazon Linux 2023 https://packages.microsoft.com/config/amazonlinux/2023/prod.repo Fedora 33 https://packages.microsoft.com/config/fedora/33/prod.repo Fedora 34 https://packages.microsoft.com/config/fedora/34/prod.repo Rocky 8.7 and higher https://packages.microsoft.com/config/rocky/8/prod.repo Rocky 9.2 and higher https://packages.microsoft.com/config/rocky/9/prod.repo Note
For your distribution and version, identify the closest entry for it (by major, then minor) under
https://packages.microsoft.com/config/rhel/.In the following commands, replace [version] and [channel] with the information you've identified:
sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/rhel/[version]/[channel].repoTip
Use hostnamectl command to identify system related information including release [version].
For example, if you're running CentOS 7 and want to deploy Defender for Endpoint on Linux from the
prodchannel:sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/rhel/7/prod.repoOr if you wish to explore new features on selected devices, you might want to deploy Microsoft Defender for Endpoint on Linux to insiders-fast channel:
sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/rhel/7/insiders-fast.repoInstall the Microsoft GPG public key:
sudo rpm --import https://packages.microsoft.com/keys/microsoft.asc
SLES and variants
Note
For your distribution and version, identify the closest entry for it (by major, then minor) under https://packages.microsoft.com/config/sles/.
In the following commands, replace [distro] and [version] with the information you've identified:
sudo zypper addrepo -c -f -n microsoft-[channel] https://packages.microsoft.com/config/[distro]/[version]/[channel].repoTip
Use SPident command to identify system related information including release [version].
For example, if you're running SLES 12 and wish to deploy Microsoft Defender for Endpoint on Linux from the
prodchannel:sudo zypper addrepo -c -f -n microsoft-prod https://packages.microsoft.com/config/sles/12/prod.repoInstall the Microsoft GPG public key:
sudo rpm --import https://packages.microsoft.com/keys/microsoft.asc
Ubuntu and Debian systems
Install
curlif it isn't installed yet:sudo apt-get install curlInstall
libplist-utilsif it isn't installed yet:sudo apt-get install libplist-utilsNote
For your distribution and version, identify the closest entry for it (by major, then minor) under
https://packages.microsoft.com/config/[distro]/.In the following command, replace [distro] and [version] with the information you've identified:
curl -o microsoft.list https://packages.microsoft.com/config/[distro]/[version]/[channel].listTip
Use hostnamectl command to identify system related information including release [version].
For example, if you're running Ubuntu 18.04 and wish to deploy Microsoft Defender for Endpoint on Linux from the
prodchannel:curl -o microsoft.list https://packages.microsoft.com/config/ubuntu/18.04/prod.listInstall the repository configuration:
sudo mv ./microsoft.list /etc/apt/sources.list.d/microsoft-[channel].listFor example, if you chose
prodchannel:sudo mv ./microsoft.list /etc/apt/sources.list.d/microsoft-prod.listInstall the
gpgpackage if not already installed:sudo apt-get install gpgIf
gpgisn't available, then installgnupg.sudo apt-get install gnupgInstall the Microsoft GPG public key:
For Debian 11 and earlier, run the following command.
curl -sSL https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/microsoft.gpg > /dev/nullFor Debian 12 and later, run the following command.
curl -sSL https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor | sudo tee /usr/share/keyrings/microsoft-prod.gpg > /dev/null
Install the HTTPS driver if not already installed:
sudo apt-get install apt-transport-httpsUpdate the repository metadata:
sudo apt-get update
Mariner
Install
dnf-plugins-coreif it isn't installed yet:sudo dnf install dnf-plugins-coreConfigure and enable the required repositories.
Note
On Mariner, Insider Fast Channel isn't available.
If you want to deploy Defender for Endpoint on Linux from the
prodchannel. Use the following commandssudo dnf install mariner-repos-extras sudo dnf config-manager --enable mariner-official-extrasOr if you wish to explore new features on selected devices, you might want to deploy Microsoft Defender for Endpoint on Linux to insiders-slow channel. Use the following commands:
sudo dnf install mariner-repos-extras-preview sudo dnf config-manager --enable mariner-official-extras-preview
Application installation
Use the commands in the following sections to install Defender for Endpoint on your Linux distribution.
RHEL and variants (CentOS, Fedora, Oracle Linux, Amazon Linux 2, Rocky, and Alma)
sudo yum install mdatp
Note
If you have multiple Microsoft repositories configured on your device, you can be specific about which repository to install the package from. The following example shows how to install the package from the production channel if you also have the insiders-fast repository channel configured on this device. This situation can happen if you're using multiple Microsoft products on your device. Depending on the distribution and the version of your server, the repository alias might be different than the one in the following example.
# list all repositories
yum repolist
...
packages-microsoft-com-prod packages-microsoft-com-prod 316
packages-microsoft-com-prod-insiders-fast packages-microsoft-com-prod-ins 2
...
# install the package from the production repository
sudo yum --enablerepo=packages-microsoft-com-prod install mdatp
SLES and variants
sudo zypper install mdatp
Note
If you have multiple Microsoft repositories configured on your device, you can be specific about which repository to install the package from. The following example shows how to install the package from the production channel if you also have the insiders-fast repository channel configured on this device. This situation can happen if you're using multiple Microsoft products on your device.
zypper repos
...
# | Alias | Name | ...
XX | packages-microsoft-com-insiders-fast | microsoft-insiders-fast | ...
XX | packages-microsoft-com-prod | microsoft-prod | ...
...
sudo zypper install packages-microsoft-com-prod:mdatp
Ubuntu and Debian systems
sudo apt-get install mdatp
Note
If you have multiple Microsoft repositories configured on your device, you can be specific about which repository to install the package from. The following example shows how to install the package from the production channel if you also have the insiders-fast repository channel configured on this device. This situation can happen if you're using multiple Microsoft products on your device.
cat /etc/apt/sources.list.d/*
deb [arch=arm64,armhf,amd64] https://packages.microsoft.com/config/ubuntu/18.04/prod insiders-fast main
deb [arch=amd64] https://packages.microsoft.com/config/ubuntu/18.04/prod bionic main
sudo apt -t bionic install mdatp
Note
Reboots are NOT required after installing or updating Microsoft Defender for Endpoint on Linux except when you're running auditD in immutable mode.
Mariner
sudo dnf install mdatp
Note
If you have multiple Microsoft repositories configured on your device, you can be specific about which repository to install the package from. The following example shows how to install the package from the production channel if you also have the insiders-slow repository channel configured on this device. This situation can happen if you're using multiple Microsoft products on your device.
sudo dnf config-manager --disable mariner-official-extras-preview
sudo dnf config-manager --enable mariner-official-extras
Download the onboarding package
Download the onboarding package from the Microsoft Defender portal.
Warning
Repackaging the Defender for Endpoint installation package is not a supported scenario. Doing so can negatively impact the integrity of the product and lead to adverse results, including but not limited to triggering tampering alerts and updates failing to apply.
Important
If you miss this step, any command executed shows a warning message indicating that the product is unlicensed. Also the mdatp health command returns a value of false.
In the Microsoft Defender portal, go to Settings > Endpoints > Device management > Onboarding.
In the first drop-down menu, select Linux Server as the operating system. In the second drop-down menu, select Local Script as the deployment method.
Select Download onboarding package. Save the file as
WindowsDefenderATPOnboardingPackage.zip.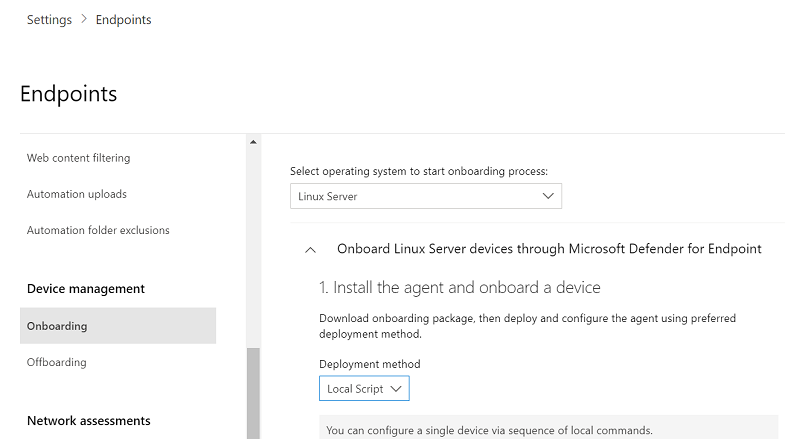
From a command prompt, verify that you have the file, and extract the contents of the archive:
ls -ltotal 8 -rw-r--r-- 1 test staff 5752 Feb 18 11:22 WindowsDefenderATPOnboardingPackage.zipunzip WindowsDefenderATPOnboardingPackage.zipArchive: WindowsDefenderATPOnboardingPackage.zip inflating: MicrosoftDefenderATPOnboardingLinuxServer.py
Client configuration
Copy
MicrosoftDefenderATPOnboardingLinuxServer.pyto the target device.Note
Initially the client device isn't associated with an organization and the orgId attribute is blank.
mdatp health --field org_idRun one of the below scenarios.
Note
To run this command, you must have
pythonorpython3installed on the device depending on the distro and version. If needed, see Step-by-step Instructions for Installing Python on Linux.To onboard a device that was previously offboard, you must remove the mdatp_offboard.json file located at /etc/opt/microsoft/mdatp.
If you're running RHEL 8.x or Ubuntu 20.04 or higher, you need to use
python3. Run the following command:sudo python3 MicrosoftDefenderATPOnboardingLinuxServer.pyFor the rest of distros and versions, you need to use
python. Run the following command:sudo python MicrosoftDefenderATPOnboardingLinuxServer.pyVerify that the device is now associated with your organization and reports a valid organization identifier:
mdatp health --field org_idCheck the health status of the product by running the following command. A return value of
truedenotes that the product is functioning as expected:mdatp health --field healthyImportant
When the product starts for the first time, it downloads the latest anti-malware definitions. This process might take up to a few minutes depending on the network connectivity. During this time, the command mentioned earlier returns a value of
false. You can check the status of the definition update using the following command:mdatp health --field definitions_statusYou might also need to configure a proxy after completing the initial installation. See Configure Defender for Endpoint on Linux for static proxy discovery: Post-installation configuration.
Run an antivirus detection test to verify that the device is properly onboarded and reporting to the service. Perform the following steps on the newly onboarded device:
Ensure that real-time protection is enabled (denoted by a result of
truefrom running the following command):mdatp health --field real_time_protection_enabledIf it isn't enabled, execute the following command:
mdatp config real-time-protection --value enabledTo run a detection test, open a Terminal window. and then run the following command:
curl -o /tmp/eicar.com.txt https://secure.eicar.org/eicar.com.txtYou can run more detection tests on zip files using either of the following commands:
curl -o /tmp/eicar_com.zip https://secure.eicar.org/eicar_com.zip curl -o /tmp/eicarcom2.zip https://secure.eicar.org/eicarcom2.zipThe files should be quarantined by Defender for Endpoint on Linux.
Use the following command to list all the detected threats:
mdatp threat list
Run an EDR detection test and simulate a detection to verify that the device is properly onboarded and reporting to the service. Perform the following steps on the newly onboarded device:
Verify that the onboarded Linux server appears in Microsoft Defender XDR. If this is the first onboarding of the machine, it can take up to 20 minutes until it appears.
Download and extract the script file to an onboarded Linux server, and then run the following command:
./mde_linux_edr_diy.shAfter a few minutes, a detection should be raised in Microsoft Defender XDR.
Look at the alert details, machine timeline, and perform your typical investigation steps.
Microsoft Defender for Endpoint package external package dependencies
The following external package dependencies exist for the mdatp package:
- The mdatp RPM package requires
glibc >= 2.17,policycoreutils,selinux-policy-targeted,mde-netfilter - For DEBIAN the mdatp package requires
libc6 >= 2.23,uuid-runtime,mde-netfilter - For Mariner the mdatp package requires
attr,diffutils,libacl,libattr,libselinux-utils,selinux-policy,policycoreutils,mde-netfilter
Note
Beginning with version 101.24082.0004, Defender for Endpoint on Linux no longer supports the Auditd event provider. We're transitioning completely to the more efficient eBPF technology.
If eBPF isn't supported on your machines, or if there are specific requirements to remain on Auditd, and your machines are using Defender for Endpoint on Linux version 101.24072.0001 or lower, the following other dependencies on the auditd package exist for mdatp:
- The mdatp RPM package requires
audit,semanage. - For DEBIAN, the mdatp package requires
auditd. - For Mariner, the mdatp package requires
audit.
The mde-netfilter package also has the following package dependencies:
- For DEBIAN, the
mde-netfilterpackage requireslibnetfilter-queue1,libglib2.0-0 - For RPM, the
mde-netfilterpackage requireslibmnl,libnfnetlink,libnetfilter_queue,glib2 - For Mariner, the
mde-netfilterpackage requireslibnfnetlink,libnetfilter_queue
If the Microsoft Defender for Endpoint installation fails due to missing dependencies errors, you can manually download the prerequisite dependencies.
Troubleshoot installation issues
For details on how to find the log that's generated when an installation error occurs, see Log installation issues.
For information about common installation issues, see Installation issues.
If the health of the device is false, see Investigate agent health issues.
For product performance issues, see Troubleshoot performance issues for Microsoft Defender for Endpoint on Linux.
For proxy and connectivity issues, see Troubleshoot cloud connectivity issues for Microsoft Defender for Endpoint on Linux.
To get support from Microsoft, open a support ticket, and provide the log files created by using the Microsoft Defender for Endpoint client analyzer tool.
How to switch between channels
For example, to change channel from Insiders-Fast to Production, do the following:
Uninstall the
Insiders-Fast channelversion of Defender for Endpoint on Linux.sudo yum remove mdatpDisable the Defender for Endpoint on Linux Insiders-Fast channel
sudo yum-config-manager --disable packages-microsoft-com-fast-prodReinstall Microsoft Defender for Endpoint on Linux using the
Production channel, and onboard the device in the Microsoft Defender portal.
How to configure policies for Microsoft Defender for Endpoint on Linux
You can configure antivirus and EDR settings on your endpoints. For more information, see the following articles:
- Set preferences for Microsoft Defender for Endpoint on Linux describes the available settings
- Security settings management describes how to configure settings in the Microsoft Defender portal.
Uninstall Microsoft Defender for Endpoint on Linux
For manual uninstallation, execute the following command for your Linux distribution.
sudo yum remove mdatpfor RHEL and variants(CentOS and Oracle Linux).sudo zypper remove mdatpfor SLES and variants.sudo apt-get purge mdatpfor Ubuntu and Debian systems.sudo dnf remove mdatpfor Mariner
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.