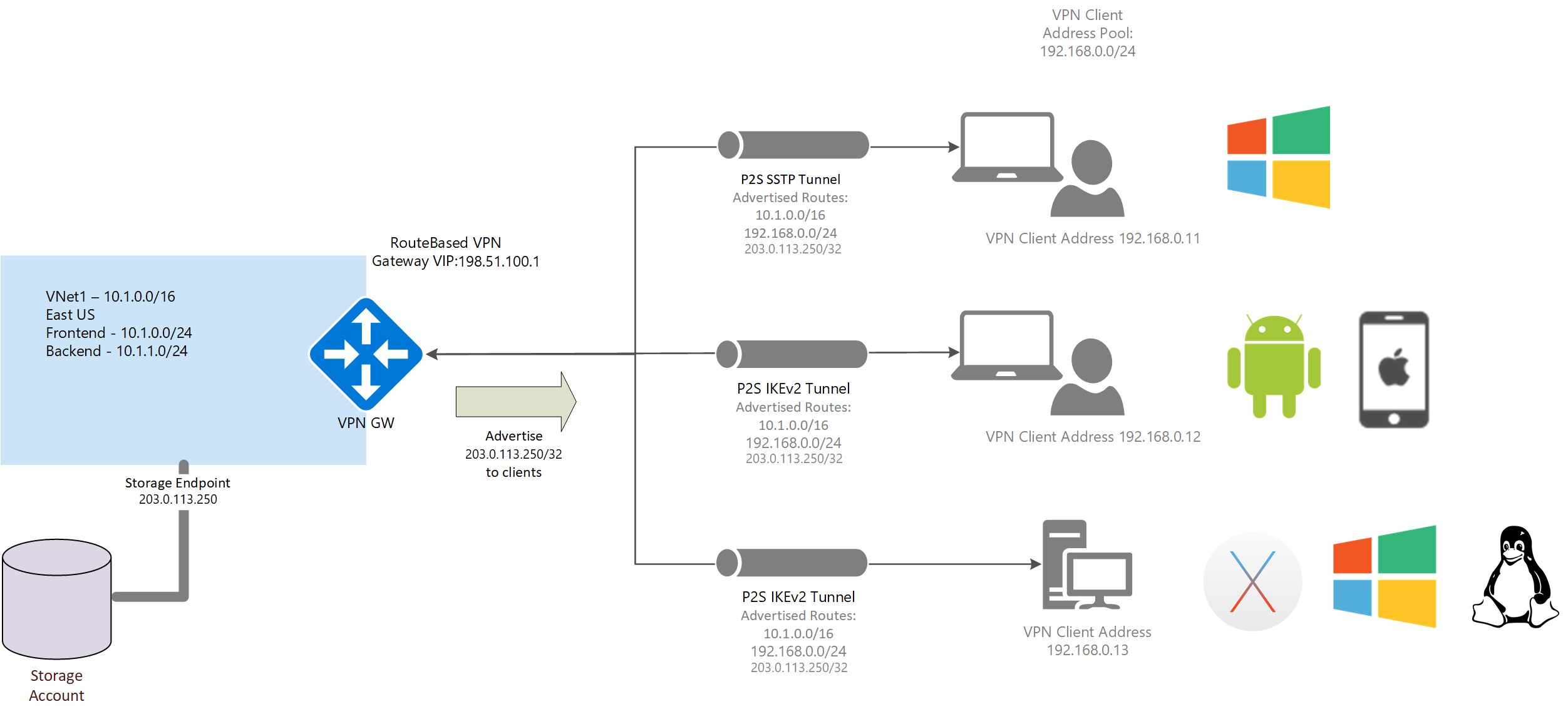
Advertise custom routes for P2S VPN clients
You may want to advertise custom routes to all of your point-to-site VPN clients. For example, when you have enabled storage endpoints in your VNet and want the remote users to be able to access these storage accounts over the VPN connection. You can advertise the IP address of the storage end point to all your remote users so that the traffic to the storage account goes over the VPN tunnel, and not the public Internet. You can also use custom routes in order to configure forced tunneling for VPN clients.
Azure portal
You can advertise custom routes using the Azure portal on the point-to-site configuration page. You can also view and modify/delete custom routes as needed using these steps. If you want to configure forced tunneling, see the Forced tunneling section in this article.
- Go to the virtual network gateway.
- Select Point-to-site configuration in the left pane.
- On the Point-to-site configuration page, add the routes. Don't use any spaces.
- Select Save at the top of the page.
PowerShell
To advertise custom routes, use the Set-AzVirtualNetworkGateway cmdlet. The following example shows you how to advertise the IP for the Contoso storage account tables (contoso.table.core.windows.net).
Ping contoso.table.core.windows.net and note the IP address. For example:
C:\>ping contoso.table.core.windows.net Pinging table.by4prdstr05a.store.core.windows.net [203.0.113.250] with 32 bytes of data:Run the following PowerShell commands:
$gw = Get-AzVirtualNetworkGateway -Name <name of gateway> -ResourceGroupName <name of resource group> Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw -CustomRoute 203.0.113.250/32To add multiple custom routes, use a comma and spaces to separate the addresses. For example:
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw -CustomRoute x.x.x.x/xx , y.y.y.y/yy
View custom routes
Use the following example to view custom routes:
$gw = Get-AzVirtualNetworkGateway -Name <name of gateway> -ResourceGroupName <name of resource group>
$gw.CustomRoutes | Format-List
Delete custom routes
Use the following example to delete custom routes:
$gw = Get-AzVirtualNetworkGateway -Name <name of gateway> -ResourceGroupName <name of resource group>
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw -CustomRoute @0
Forced tunneling
You can direct all traffic to the VPN tunnel by advertising 0.0.0.0/1 and 128.0.0.0/1 as custom routes to the clients. The reason for breaking 0.0.0.0/0 into two smaller subnets is that these smaller prefixes are more specific than the default route that may already be configured on the local network adapter and, as such, will be preferred when routing traffic.
Note
Internet connectivity is not provided through the VPN gateway. As a result, all traffic bound for the Internet is dropped.
To enable forced tunneling, use the following commands:
$gw = Get-AzVirtualNetworkGateway -Name <name of gateway> -ResourceGroupName <name of resource group>
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw -CustomRoute 0.0.0.0/1 , 128.0.0.0/1
Next steps
For more P2S routing information, see About point-to-site routing.