Configure a Site-to-Site VPN connection over ExpressRoute private peering
You can configure a Site-to-Site VPN to a virtual network gateway over an ExpressRoute private peering using an RFC 1918 IP address. This configuration provides the following benefits:
Traffic over private peering is encrypted.
Point-to-site users connecting to a virtual network gateway can use ExpressRoute (via the Site-to-Site tunnel) to access on-premises resources.
It's possible to deploy Site-to-Site VPN connections over ExpressRoute private peering at the same time as Site-to-Site VPN connections via the Internet on the same VPN gateway.
This feature is only available for standard-IP based gateways.
Prerequisites
To complete this configuration, verify that you meet the following prerequisites:
You have a functioning ExpressRoute circuit that is linked to the virtual network where the VPN gateway is (or will be) created.
You can reach resources over RFC1918 (private) IP in the virtual network over the ExpressRoute circuit.
Routing
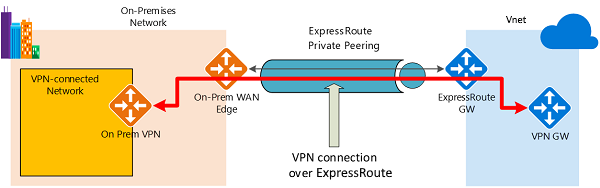
Figure 1 shows an example of VPN connectivity over ExpressRoute private peering. In this example, you see a network within the on-premises network that is connected to the Azure hub VPN gateway over ExpressRoute private peering. An important aspect of this configuration is the routing between the on-premises networks and Azure over both the ExpressRoute and VPN paths.
Figure 1
Establishing connectivity is straightforward:
Establish ExpressRoute connectivity with an ExpressRoute circuit and private peering.
Establish the VPN connectivity using the steps in this article.
Traffic from on-premises networks to Azure
For traffic from on-premises networks to Azure, the Azure prefixes are advertised via both the ExpressRoute private peering BGP, and the VPN BGP if BGP is configured on your VPN gateway. The result is two network routes (paths) toward Azure from the on-premises networks:
• One network route over the IPsec-protected path.
• One network route directly over ExpressRoute without IPsec protection.
To apply encryption to the communication, you must make sure that for the VPN-connected network in Figure 1, Azure routes via the on-premises VPN gateway are preferred over the direct ExpressRoute path.
Traffic from Azure to on-premises networks
The same requirement applies to the traffic from Azure to on-premises networks. To ensure that the IPsec path is preferred over the direct ExpressRoute path (without IPsec), you have two options:
• Advertise more specific prefixes on the VPN BGP session for the VPN-connected network. You can advertise a larger range that encompasses the VPN-connected network over ExpressRoute private peering, then more specific ranges in the VPN BGP session. For example, advertise 10.0.0.0/16 over ExpressRoute, and 10.0.1.0/24 over VPN.
• Advertise disjoint prefixes for VPN and ExpressRoute. If the VPN-connected network ranges are disjoint from other ExpressRoute connected networks, you can advertise the prefixes in the VPN and ExpressRoute BGP sessions respectively. For example, advertise 10.0.0.0/24 over ExpressRoute, and 10.0.1.0/24 over VPN.
In both of these examples, Azure will send traffic to 10.0.1.0/24 over the VPN connection rather than directly over ExpressRoute without VPN protection.
Warning
If you advertise the same prefixes over both ExpressRoute and VPN connections, Azure will use the ExpressRoute path directly without VPN protection.
Portal steps
Configure a Site-to-Site connection. For steps, see the Site-to-site configuration article. Be sure to pick a gateway with a Standard Public IP.
Enable Private IPs on the gateway. Select Configuration, then set Gateway Private IPs to Enabled. Select Save to save your changes.
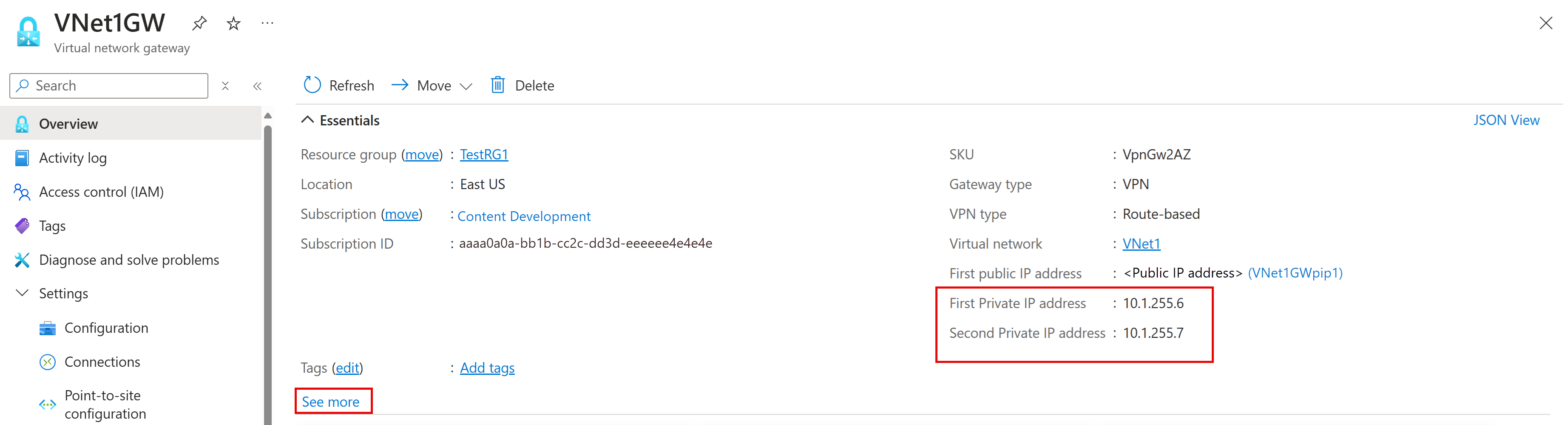
On the Overview page, select See More to view the private IP address. Write down this information to use later in the configuration steps. If you have an active-active mode VPN gateway, you'll see two private IP addresses.
To enable Use Azure Private IP Address on the connection, go to the Configuration page. Set Use Azure Private IP Address to Enabled, then select Save.
Use the private IP address that you wrote down in step 3 as the remote IP on your on-premises firewall to establish the Site-to-Site tunnel over the ExpressRoute private peering.
Note
Configuring BGP on your VPN gateway is not required to achieve a VPN connection over ExpressRoute private peering.
PowerShell steps
Configure a Site-to-Site connection. For steps, see the Configure a Site-to-Site VPN article. Be sure to pick a gateway with a Standard Public IP.
Set the flag to use the private IP on the gateway using the following PowerShell commands:
$Gateway = Get-AzVirtualNetworkGateway -Name <name of gateway> -ResourceGroup <name of resource group> Set-AzVirtualNetworkGateway -VirtualNetworkGateway $Gateway -EnablePrivateIpAddress $trueYou should see a public and a private IP address. Write down the IP address under the “TunnelIpAddresses” section of the output. You'll use this information in a later step.
Set the connection to use the private IP address by using the following PowerShell command:
$Connection = get-AzVirtualNetworkGatewayConnection -Name <name of the connection> -ResourceGroupName <name of resource group> Set-AzVirtualNetworkGatewayConnection --VirtualNetworkGatewayConnection $Connection -UseLocalAzureIpAddress $trueFrom your firewall, ping the private IP that you wrote down in step 2. It should be reachable over the ExpressRoute private peering.
Use this private IP as the remote IP on your on-premises firewall to establish the Site-to-Site tunnel over the ExpressRoute private peering.
Next steps
For more information about VPN Gateway, see What is VPN Gateway?