Configure P2S User VPN for Microsoft Entra ID authentication – Microsoft-registered app
This article helps you configure point-to-site User VPN connection to Virtual WAN that uses Microsoft Entra ID authentication and the new Microsoft-registered Azure VPN Client App ID.
Note
The steps in this article apply to Microsoft Entra ID authentication using the new Microsoft-registered Azure VPN Client App ID and associated Audience values. This article doesn't apply to the older, manually registered Azure VPN Client app for your tenant. For the manually registered Azure VPN Client steps, see Configure P2S User VPN using manually registered VPN client.
Virtual WAN now supports a new Microsoft-registered App ID and corresponding Audience values for the latest versions of the Azure VPN Client. When you configure a P2S User VPN VPN gateway using the new Audience values, you skip the Azure VPN Client app manual registration process for your Microsoft Entra tenant. The App ID is already created and your tenant is automatically able to use it with no extra registration steps. This process is more secure than manually registering the Azure VPN Client because you don't need to authorize the app or assign permissions via the Global administrator role.
Previously, you were required to manually register (integrate) the Azure VPN Client app with your Microsoft Entra tenant. Registering the client app creates an App ID representing the identity of the Azure VPN Client application and requires authorization using the Global Administrator role. To better understand the difference between the types of application objects, see How and why applications are added to Microsoft Entra ID.
When possible, we recommend that you configure new P2S User VPN gateways using the Microsoft-registered Azure VPN client App ID and its corresponding Audience values instead of manually registering the Azure VPN Client app with your tenant. If you have a previously configured a P2S User VPN gateway that uses Microsoft Entra ID authentication, you can update the gateway and clients to take advantage of the new Microsoft-registered App ID. Updating the P2S gateway with the new Audience value is required if you want Linux clients to connect. The Azure VPN Client for Linux isn't backward compatible with the older Audience values.
Considerations
A P2S User VPN gateway can only support one Audience value. It can't support multiple Audience values simultaneously.
The Azure VPN Client for Linux isn't backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. However, the Azure VPN Client for Linux does support Custom Audience values.
-
While it's possible that the Azure VPN Client for Linux might work on other Linux distributions and releases, the Azure VPN Client for Linux is only supported on the following releases:
- Ubuntu 20.04
- Ubuntu 22.04
The latest versions of the Azure VPN Clients for macOS and Windows are backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. These clients also support Custom Audience values.
Azure VPN Client Audience values
The following table shows the versions of the Azure VPN Client that are supported for each App ID and the corresponding available Audience values.
| App ID | Supported Audience values | Supported clients |
|---|---|---|
| Microsoft-registered | The audience value c632b3df-fb67-4d84-bdcf-b95ad541b5c8 applies to:- Azure Public - Azure Government - Azure Germany - Microsoft Azure operated by 21Vianet |
- Linux - Windows - macOS |
| Manually registered | - Azure Public: 41b23e61-6c1e-4545-b367-cd054e0ed4b4- Azure Government: 51bb15d4-3a4f-4ebf-9dca-40096fe32426- Azure Germany: 538ee9e6-310a-468d-afef-ea97365856a9- Microsoft Azure operated by 21Vianet: 49f817b6-84ae-4cc0-928c-73f27289b3aa |
- Windows - macOS |
| Custom | <custom-app-id> |
- Linux - Windows - macOS |
Note
Microsoft Entra ID authentication is supported only for OpenVPN® protocol connections and requires the Azure VPN Client.
In this article, you learn how to:
- Create a virtual WAN
- Create a User VPN configuration
- Download a virtual WAN User VPN profile
- Create a virtual hub
- Edit a hub to add P2S gateway
- Connect a virtual network to a virtual hub
- Download and apply the User VPN client configuration
- View your virtual WAN
Before you begin
Verify that you've met the following criteria before beginning your configuration:
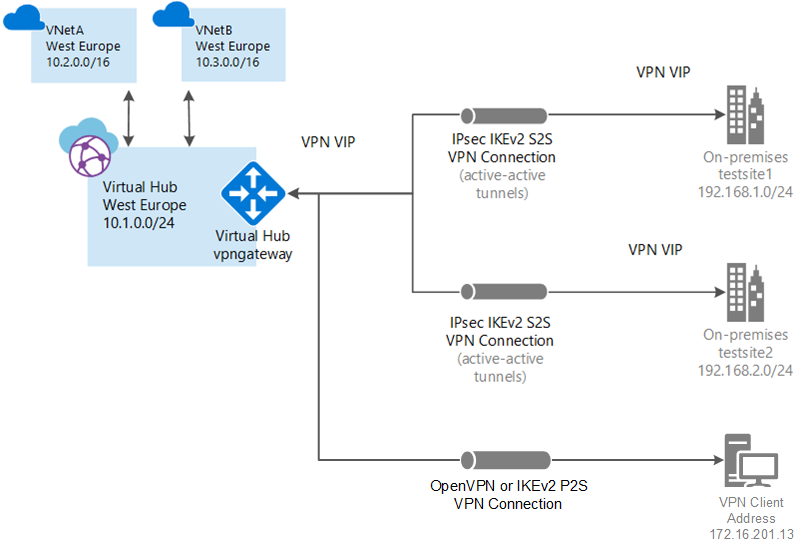
You have a virtual network that you want to connect to. Verify that none of the subnets of your on-premises networks overlap with the virtual networks that you want to connect to. To create a virtual network in the Azure portal, see the Quickstart.
Your virtual network doesn't have any virtual network gateways. If your virtual network has a gateway (either VPN or ExpressRoute), you must remove all gateways. The steps for this configuration help you connect your virtual network to the Virtual WAN virtual hub gateway.
Obtain an IP address range for your hub region. The hub is a virtual network that is created and used by Virtual WAN. The address range that you specify for the hub can't overlap with any of your existing virtual networks that you connect to. It also can't overlap with your address ranges that you connect to on premises. If you're unfamiliar with the IP address ranges located in your on-premises network configuration, coordinate with someone who can provide those details for you.
You need a Microsoft Entra ID tenant for this configuration. If you don't have one, you can create one by following the instructions in Create a new tenant.
If you want to use a custom audience value, see Create or modify custom audience app ID.
Create a virtual WAN
From a browser, navigate to the Azure portal and sign in with your Azure account.
In the portal, in the Search resources bar, type Virtual WAN in the search box and select Enter.
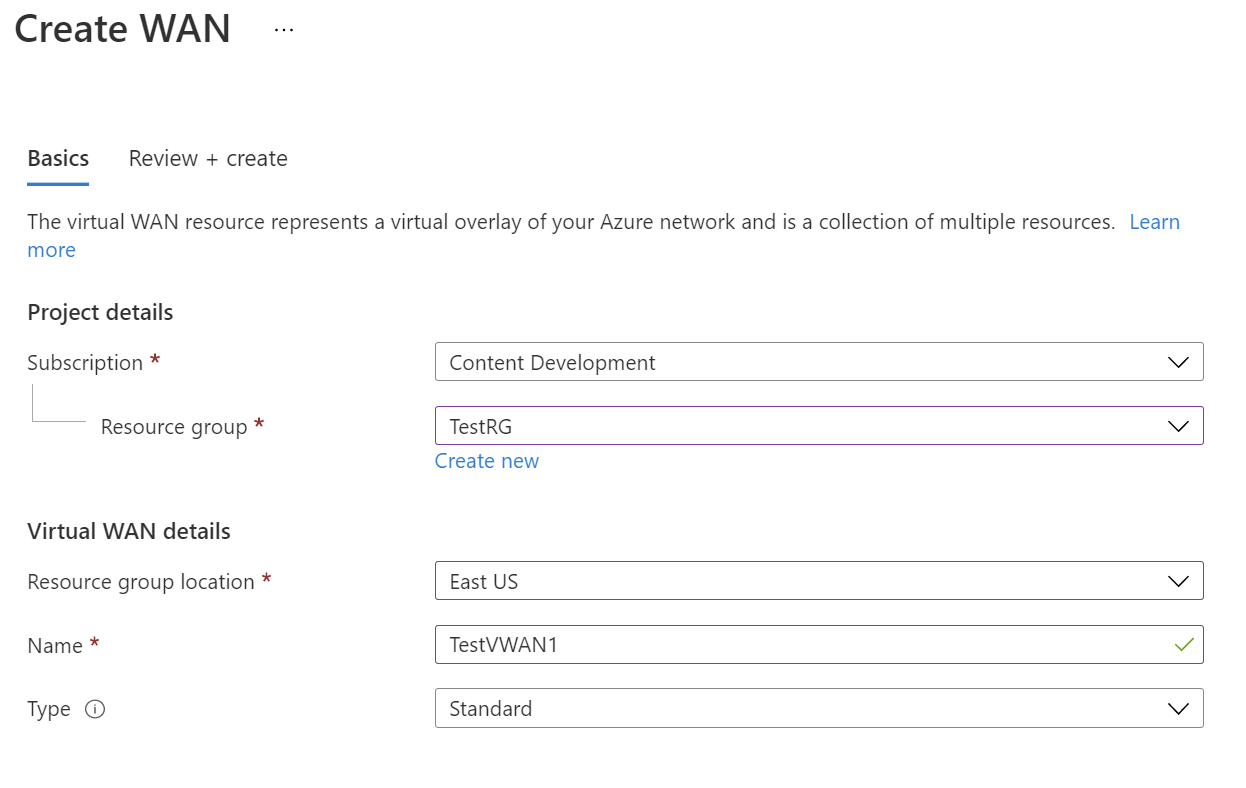
Select Virtual WANs from the results. On the Virtual WANs page, select + Create to open the Create WAN page.
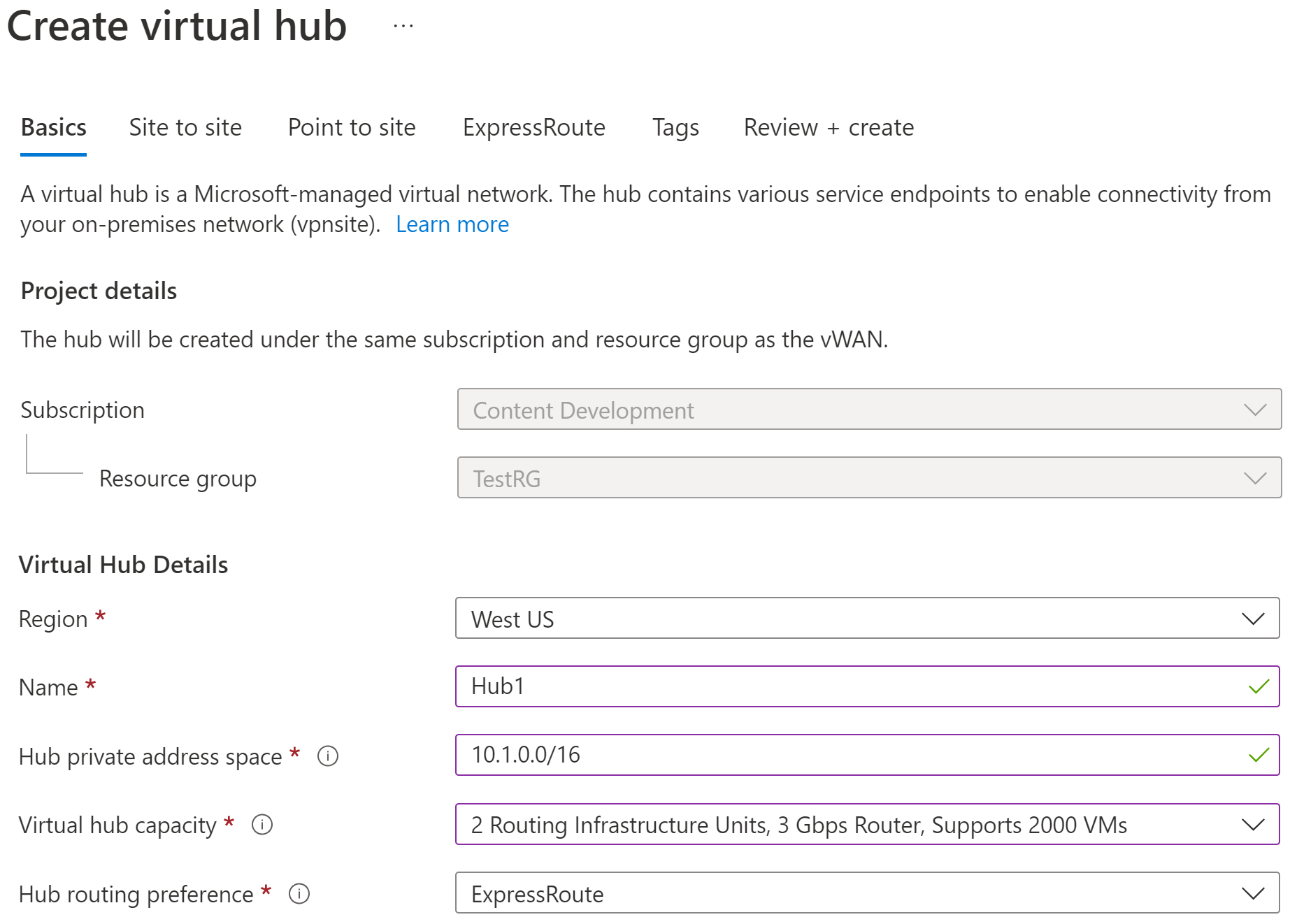
On the Create WAN page, on the Basics tab, fill in the fields. Modify the example values to apply to your environment.
- Subscription: Select the subscription that you want to use.
- Resource group: Create new or use existing.
- Resource group location: Choose a resource location from the dropdown. A WAN is a global resource and doesn't live in a particular region. However, you must select a region in order to manage and locate the WAN resource that you create.
- Name: Type the Name that you want to call your virtual WAN.
- Type: Basic or Standard. Select Standard. If you select Basic, understand that Basic virtual WANs can only contain Basic hubs. Basic hubs can only be used for site-to-site connections.
After you finish filling out the fields, at the bottom of the page, select Review +Create.
Once validation passes, click Create to create the virtual WAN.
Create a User VPN configuration
A User VPN configuration defines the parameters for connecting remote clients. It's important to create the User VPN configuration before configuring your virtual hub with P2S settings, as you must specify the User VPN configuration you want to use.
Important
The Azure portal is in the process of updating Azure Active Directory fields to Entra. If you see Microsoft Entra ID referenced and you don't see those values in the portal yet, you can select Azure Active Directory values.
Go to your Virtual WAN. In the left pane, expand Connectivity and select the User VPN configurations page. On the User VPN configurations page, click +Create user VPN config.
On the Basics page, specify the following parameters.
- Configuration name - Enter the name you want to call your User VPN Configuration. For example, TestConfig1.
- Tunnel type - Select OpenVPN from the dropdown menu.
At the top of the page, click Azure Active Directory. You can view the necessary values on the Microsoft Entra ID page for Enterprise applications in the portal.
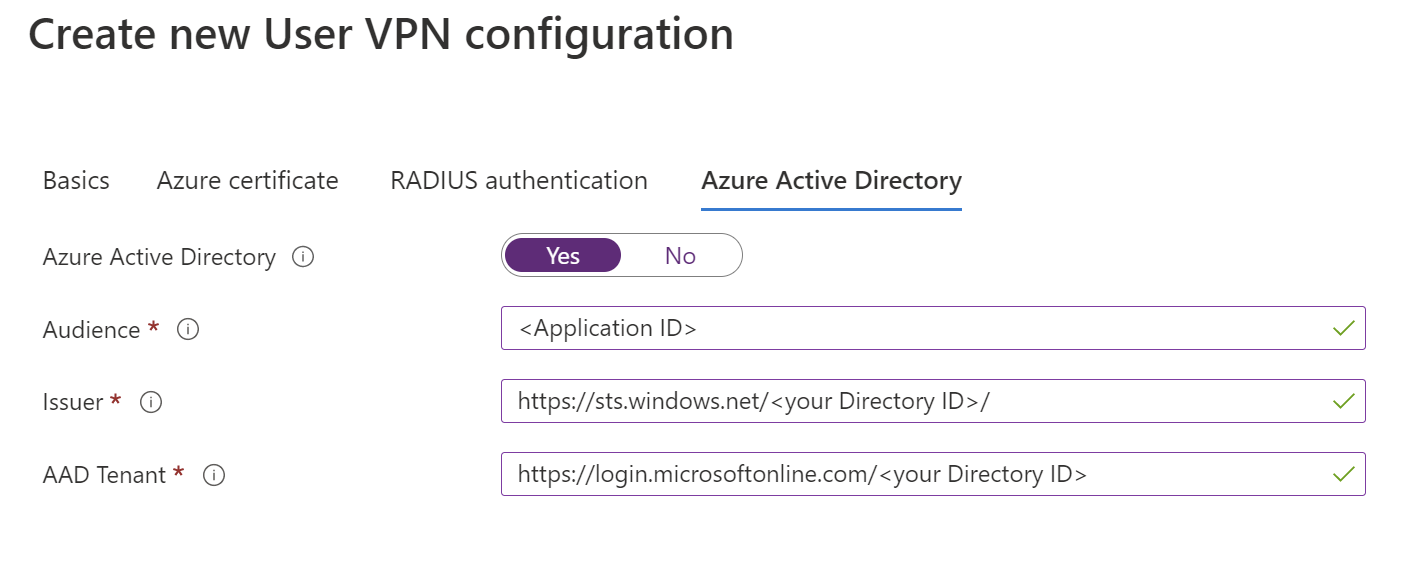 Configure the following values:
Configure the following values:- Azure Active Directory - Select Yes.
- Audience - Enter the corresponding value for the Microsoft-registered Azure VPN Client App ID, Azure Public:
c632b3df-fb67-4d84-bdcf-b95ad541b5c8. Custom audience is also supported for this field. - Issuer - Enter
https://sts.windows.net/<your Directory ID>/. - AAD Tenant - Enter the TenantID for the Microsoft Entra tenant. Make sure there isn't an
/at the end of the Microsoft Entra tenant URL.
Click Create to create the User VPN configuration. You'll select this configuration later in the exercise.
Create an empty hub
Next, create the virtual hub. The steps in this section create an empty virtual hub to which you can later add the P2S gateway. However, it's always much more efficient to combine creating the hub along with the gateway because each time you make a configuration change to the hub, you have to wait for the hub settings to build.
For demonstration purposes, we'll create an empty hub first, then add the P2S gateway in the next section. But, you can choose to incorporate the P2S gateway settings from the next section at the same time you configure the hub.
Go to the virtual WAN that you created. On the virtual WAN page left pane, under the Connectivity, select Hubs.
On the Hubs page, select +New Hub to open the Create virtual hub page.
On the Create virtual hub page Basics tab, complete the following fields:
- Region: Select the region in which you want to deploy the virtual hub.
- Name: The name by which you want the virtual hub to be known.
- Hub private address space: The hub's address range in CIDR notation. The minimum address space is /24 to create a hub.
- Virtual hub capacity: Select from the dropdown. For more information, see Virtual hub settings.
- Hub routing preference: Leave the setting as the default, ExpressRoute unless you have a specific need to change this field. For more information, see Virtual hub routing preference.
After configuring the settings, click Review + create to validate, then Create the hub. It can take up to 30 minutes to create a hub.
Add a P2S gateway to a hub
This section shows you how to add a gateway to an already existing virtual hub. It can take up to 30 minutes to update a hub.
Go to your Virtual WAN. In the left pane, expand Settings and select Hubs.
Click the name of the hub that you want to edit.
Click Edit virtual hub at the top of the page to open the Edit virtual hub page.
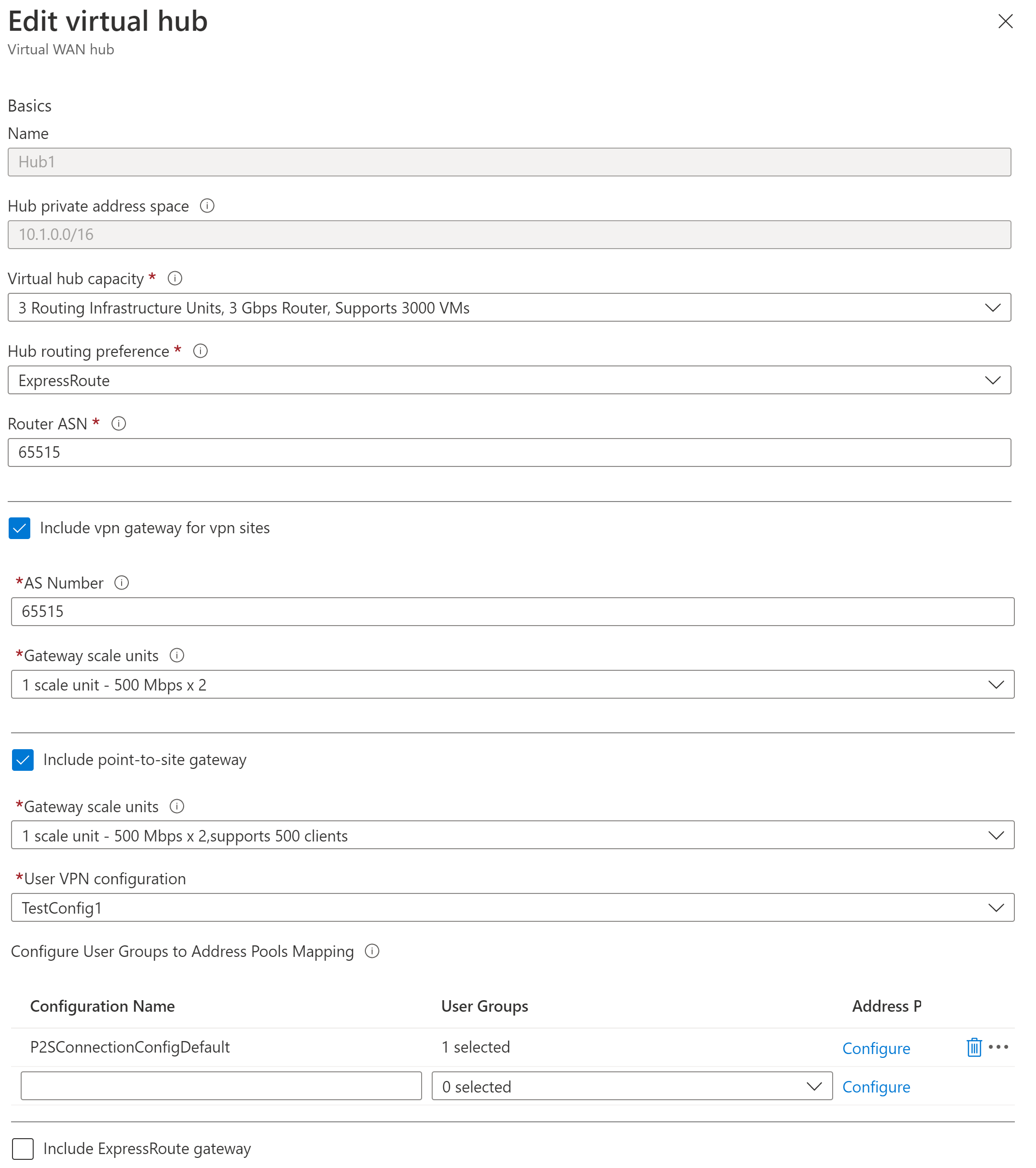
On the Edit virtual hub page, check the checkboxes for Include vpn gateway for vpn sites and Include point-to-site gateway to reveal the settings. Then configure the values.
- Gateway scale units: Select the Gateway scale units. Scale units represent the aggregate capacity of the User VPN gateway. If you select 40 or more gateway scale units, plan your client address pool accordingly. For information about how this setting impacts the client address pool, see About client address pools. For information about gateway scale units, see the FAQ.
- User VPN configuration: Select the configuration that you created earlier.
- User Groups to Address Pools Mapping: Specify address pools. For information about this setting, see Configure user groups and IP address pools for P2S User VPNs.
After configuring the settings, click Confirm to update the hub. It can take up to 30 minutes to update a hub.
Connect virtual network to hub
In this section, you create a connection between your virtual hub and your virtual network.
In the Azure portal, go to your Virtual WAN In the left pane, select Virtual network connections.
On the Virtual network connections page, select + Add connection.
On the Add connection page, configure the connection settings. For information about routing settings, see About routing.
- Connection name: Name your connection.
- Hubs: Select the hub you want to associate with this connection.
- Subscription: Verify the subscription.
- Resource group: Select the resource group that contains the virtual network to which you want to connect.
- Virtual network: Select the virtual network you want to connect to this hub. The virtual network you select can't have an already existing virtual network gateway.
- Propagate to none: This is set to No by default. Changing the switch to Yes makes the configuration options for Propagate to Route Tables and Propagate to labels unavailable for configuration.
- Associate Route Table: From the dropdown, you can select a route table that you want to associate.
- Propagate to labels: Labels are a logical group of route tables. For this setting, select from the dropdown.
- Static routes: Configure static routes, if necessary. Configure static routes for Network Virtual Appliances (if applicable). Virtual WAN supports a single next hop IP for static route in a virtual network connection. For example, if you have a separate virtual appliance for ingress and egress traffic flows, it would be best to have the virtual appliances in separate VNets and attach the VNets to the virtual hub.
- Bypass Next Hop IP for workloads within this VNet: This setting lets you deploy NVAs and other workloads into the same VNet without forcing all the traffic through the NVA. This setting can only be configured when you're configuring a new connection. If you want to use this setting for a connection you've already created, delete the connection, then add a new connection.
- Propagate static route: This setting is currently being rolled out. This setting lets you propagate static routes defined in the Static routes section to route tables specified in Propagate to Route Tables. Additionally, routes will be propagated to route tables that have labels specified as Propagate to labels. These routes can be propagated inter-hub, except for the default route 0/0.
Once you've completed the settings you want to configure, click Create to create the connection.
Download User VPN profile
All of the necessary configuration settings for the VPN clients are contained in a VPN client configuration zip file. The settings in the zip file help you easily configure the VPN clients. The VPN client configuration files that you generate are specific to the User VPN configuration for your gateway. You can download global (WAN-level) profiles, or a profile for a specific hub. For information and additional instructions, see Download global and hub profiles. The following steps walk you through downloading a global WAN-level profile.
To generate a WAN-level global profile VPN client configuration package, go to the virtual WAN (not the virtual hub).
In the left pane, select User VPN configurations.
Select the configuration for which you want to download the profile. If you have multiple hubs assigned to the same profile, expand the profile to show the hubs, then select one of the hubs that uses the profile.
Select Download virtual WAN user VPN profile.
On the download page, select EAPTLS, then Generate and download profile. A profile package (zip file) containing the client configuration settings is generated and downloads to your computer. The contents of the package depend on the authentication and tunnel choices for your configuration.
Configure the Azure VPN Client
Next, you examine the profile configuration package, configure the Azure VPN Client for the client computers, and connect to Azure. See the articles listed in the Next steps section.
Next steps
Configure the Azure VPN Client. You can use the steps in the VPN Gateway client documentation to configure the Azure VPN Client for Virtual WAN.