Guidance on migrating virtual machines from Microsoft Configuration Manager to Azure Update Manager
Applies to: ✔️ Windows VMs ✔️ Linux VMs ✔️ On-premises environment ✔️ Azure Arc-enabled servers.
This article provides a guide to modernize management of servers for which you are currently using Microsoft Configuration Manager (MCM). We shall focus on Azure Update Manager that provides Azure based experiences for patch management, the major capability of MCM.
To start with, let us list the Azure Services that provide equivalent capabilities for the different System Center components.
| System Center Component | Azure equivalent service |
|---|---|
| System Center Operations Manager (SCOM) | Azure Monitor SCOM Managed Instance |
| System Center Configuration Manager (SCCM), now called Microsoft Configuration Manager (MCM) | Azure Update Manager, Change Tracking and Inventory, Azure Machine Configuration (formerly called Azure Policy Guest Configuration), Azure Automation, Microsoft Defender for Cloud |
| System Center Data Protection Manager (SCDPM) | Azure Backup |
| System Center Orchestrator (SCORCH) | Azure Automation |
| System Center Service Manager (SCSM) | - |
Note
As part of your migration journey, we recommend the following options:
- Fully migrate your virtual machines to Azure and replace System Center with Azure native services.
- Take a hybrid approach and replace System Center with Azure native services. Where both Azure and on-premises virtual machines are managed using Azure native services. For on-premises virtual machines, the capabilities of the Azure platform are extended to on-premises via Azure Arc.
Migrate to Azure Update Manager
MCM helps you to manage PCs and servers, keep software up to date, set configuration and security policies, and monitor system status. MCM offers multiple features and capabilities and software update management is one of these.
Specifically for update management or patching, as per your requirements, you can use the native Azure Update Manager to manage and govern update compliance for Windows and Linux machines across your deployments in a consistent manner. Unlike MCM which needs maintaining Azure virtual machines for hosting the different Configuration Manager roles, Azure Update Manager is designed as a standalone Azure service to provide SaaS experience on Azure to manage hybrid environments. You don't need a license to use Azure Update Manager.
Note
- To manage clients/devices, Intune is the recommended Microsoft solution.
- Azure Update Manager does not provide migration support for Azure VMs in MCM. For example, configurations.
Software update management capability map
The following table maps the software update management capabilities of MCM to Azure Update Manager.
| Capability | Microsoft Configuration Manager | Azure Update Manager |
|---|---|---|
| Synchronize software updates between sites (Central Admin site, Primary, Secondary sites) | The top site (either central admin site or stand-alone primary site) connects to Microsoft Update to retrieve software update. Learn more. After the top sites are synchronized, the child sites are synchronized. | There's no hierarchy of machines in Azure and therefore all machines connected to Azure receive updates from the source repository. |
| Synchronize software updates/check for updates (retrieve patch metadata) | You can scan for updates periodically by setting configuration on the Software update point. Learn more | You can enable periodic assessment to enable scan of patches every 24 hours. Learn more |
| Configuring classifications/products to synchronize/scan/assess | You can choose the update classifications (security or critical updates) to synchronize/scan/assess. Learn more | There's no such capability here. The entire software metadata is scanned. |
| Deploy software updates (install patches) | Provides three modes of deploying updates: Manual deployment Automatic deployment Phased deployment Learn more |
- Manual deployment is mapped to deploy one-time updates - Automatic deployment is mapped to scheduled updates - There's no phased deployment option. |
| Deploy software updates on Windows and Linux machines (in Azure or on-premises or other clouds) | SCCM helps manage tracking and applying software updates to Windows machines (Currently, we don't support Linux machines.) | Azure Update Manager supports software updates on both Windows and Linux machines. |
Guidance to use Azure Update Manager on MCM managed machines
As a first step in MCM user's journey towards Azure Update Manager, you need to enable Azure Update Manager on your existing MCM managed servers (i.e. ensure that Azure Update Manager and MCM co-existence is achieved). The following section address few challenges that you might encounter in this first step.
Prerequisites for Azure Update Manager and MCM co-existence
Ensure that the Auto updates are disabled on the machine. For more information, see Manage additional Windows Update settings - Configuring Automatic Updates by editing the registry.
Ensure that the NoAutoUpdate registry key is set to 1 in the following registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AUAzure Update Manager can get updates from WSUS server and for this, ensure to configure WSUS server as part of SCCM.
- Ensure that the WSUS server has enough space.
- Ensure to update language option to download the packages in WSUS config. We recommend that you select the languages that are required. For more information, see Step 2 - Configure WSUS.
- Ensure to create a rule for auto approving updates in WSUS to download the applicable packages on the WSUS server so that Azure Update Manager can get the updates from this WSUS server.
- Select classifications you want as per your requirements or keep them same as selected in SCCM.
- Select products as per requirements or keep them same as selected in SCCM.
- To start, create a test computer group and apply this rule to it, to test these changes.
- After testing the test group, you can expand it to all computer groups.
- Create an exclusion computer group in WSUS if needed.
Overview of current MCM setup
MCM client uses WSUS server to scan for first-party updates, therefore you have WSUS server configured as part of the initial setup.
Third-party updates content is published to this WSUS server as well. Azure Update Manager has the capability of scanning & installing updates from WSUS, so we would leverage the WSUS server configured as part of MCM setup to make Azure Update Manager work along with MCM.
First party updates
For Azure Update Manager to scan and install first party updates (Windows and Microsoft updates), you should start approving the required updates in the configured WSUS server. This is done by configuring an auto approval rule in WSUS like what users have configured on MCM server.
Third party updates
Third party updates should work as expected with Azure Update Manager provided you have already configured MCM for third party patching and it is able to successfully patch Third party updates via MCM. Ensure that you continue to publish third party updates to WSUS from MCM Step 3 in Enable third-party updates. After you publish to WSUS, Azure Update Manager will be able to detect and install these updates from WSUS server.
Manage software updates using Azure Update Manager
Sign in to the Azure portal and search for Azure Update Manager.
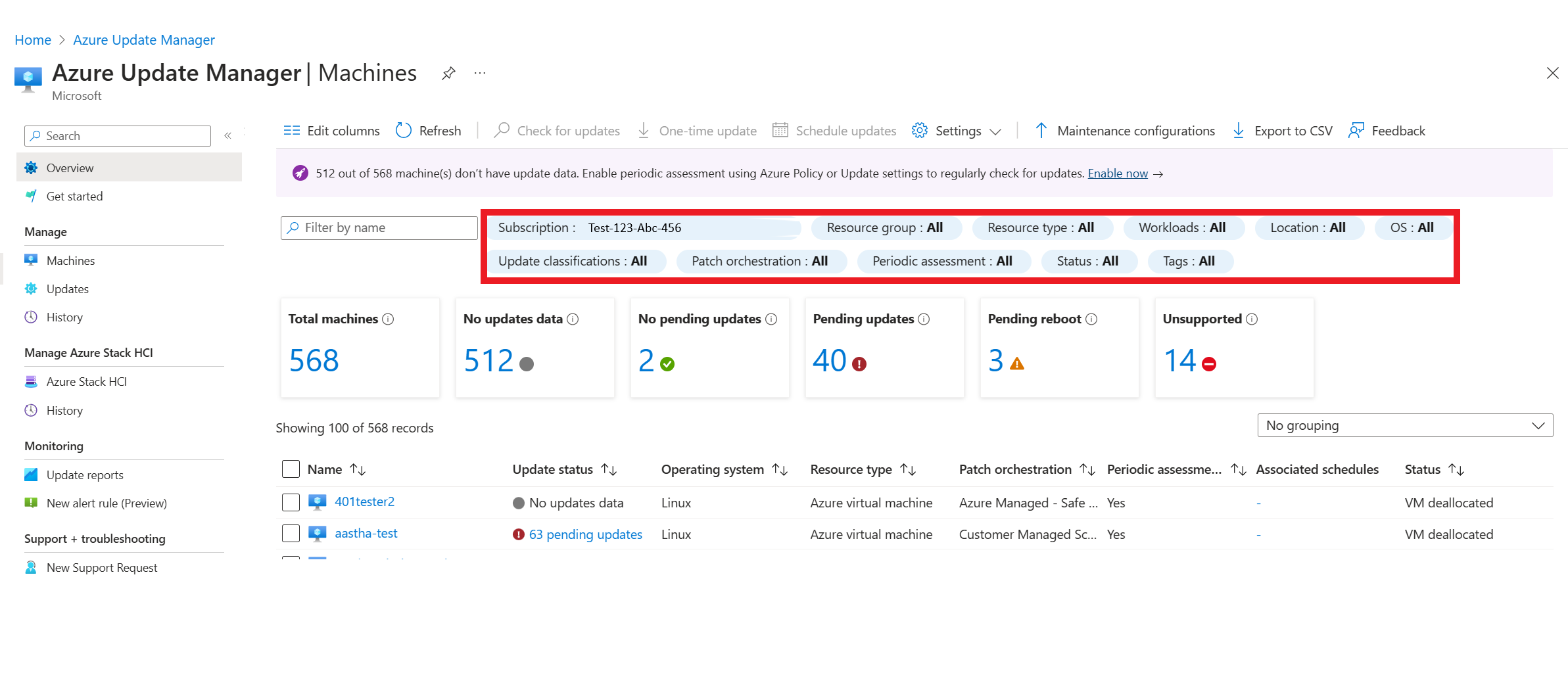
In the Azure Update Manager home page, under Manage > Machines, select your subscription to view all your machines.
Filter as per the available options to know the status of your specific machines.
Select the suitable assessment and patching options as per your requirement.
Patch machines
After you set up configuration for assessment and patching, you can deploy/install either through on-demand updates (One-time or manual update) or schedule updates (automatic update) only. You can also deploy updates using Azure Update Manager's API.
Limitations in Azure Update Manager
The following are the current limitations:
- Orchestration groups with Pre/Post scripts - Orchestration groups can't be created in Azure Update Manager to specify a maintenance sequence, allow some machines for updates at the same time and so on. (The orchestration groups allow you to use the pre/post scripts to run tasks before and after a patch deployment).
Frequently asked questions
Where does Azure Update Manager get its updates from?
Azure Update Manager refers to the repository that the machines point to. Most Windows machines by default point to the Windows Update catalog and Linux machines are configured to get updates from the apt or yum repositories. If the machines point to another repository such as WSUS or a local repository then Azure Update Manager gets the updates from that repository.
Can Azure Update Manager patch OS, SQL and Third party software?
Azure Update Manager refers to the repositories (or endpoints) that the VMs point to. If the repository (or endpoints) contains updates for Microsoft products, third party software etc. then Azure Update Manager can install these patches.
By default, Windows VMs point to Windows Update server. Windows Update server doesn't contain updates for Microsoft products, and third party software. If the VMs point to Microsoft Update, Azure Update Manager patches OS and Microsoft products.
For the third party software patching, Azure Update Manager should be connected to WSUS and you must publish the third party updates. We can't patch third party software for Windows VMs unless they're available in WSUS.
Do I need to configure WSUS to use Azure Update Manager?
WSUS is a way to manage patches. Azure Update Manager will refer to whichever endpoint it's pointed to. (Windows Update, Microsoft Update, or WSUS).
Should I deploy the monthly patch through MCM?
No, only approving patches in WSUS monthly or setting the Automatic Deployment Rules (ADRs) will scan and install patches on your servers.
How Azure Update Manager can be used to manage on-premises virtual machines?
Azure Update Manager can be used on-premises by using Azure Arc. Azure Arc is a bridge that extends the Azure platform to help you build applications and services with the flexibility to run across datacenters, at the edge, and in multicloud environments. Azure Arc VM management lets you provision and manage Windows and Linux VMs hosted on-premises. This feature enables IT admins to manage Arc VMs by using Azure management tools, including Azure portal, Azure CLI, Azure PowerShell, and Azure Resource Manager (ARM) templates.