Connect your threat intelligence platform to Microsoft Sentinel with the upload API (Preview)
Many organizations use threat intelligence platform (TIP) solutions to aggregate threat intelligence feeds from various sources. From the aggregated feed, the data is curated to apply to security solutions such as network devices, EDR/XDR solutions, or security information and event management (SIEM) solutions such as Microsoft Sentinel. The industry standard for describing cyberthreat information is called, "Structured Threat Information Expression" or STIX. By using the upload API which supports STIX objects, you use a more expressive way to import threat intelligence into Microsoft Sentinel.
The upload API ingests threat intelligence into Microsoft Sentinel without the need for a data connector. This article describes what you need to connect. For more information on the API details, see the reference document Microsoft Sentinel upload API.
For more information about threat intelligence, see Threat intelligence.
Important
The Microsoft Sentinel threat intelligence upload API is in preview. See the Supplemental Terms of Use for Microsoft Azure Previews for more legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal. For preview, Microsoft Sentinel is available in the Defender portal without Microsoft Defender XDR or an E5 license. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
Prerequisites
- You must have read and write permissions to the Microsoft Sentinel workspace to store your threat intelligence STIX objects.
- You must be able to register a Microsoft Entra application.
- Your Microsoft Entra application must be granted the Microsoft Sentinel Contributor role at the workspace level.
Instructions
Follow these steps to import threat intelligence STIX objects to Microsoft Sentinel from your integrated TIP or custom threat intelligence solution:
- Register a Microsoft Entra application, and then record its application ID.
- Generate and record a client secret for your Microsoft Entra application.
- Assign your Microsoft Entra application the Microsoft Sentinel Contributor role or the equivalent.
- Configure your TIP solution or custom application.
Register a Microsoft Entra application
The default user role permissions allow users to create application registrations. If this setting was switched to No, you need permission to manage applications in Microsoft Entra. Any of the following Microsoft Entra roles include the required permissions:
- Application administrator
- Application developer
- Cloud application administrator
For more information on registering your Microsoft Entra application, see Register an application.
After you register your application, record its application (client) ID from the application's Overview tab.
Assign a role to the application
The upload API ingests threat intelligence objects at the workspace level and requires the role of Microsoft Sentinel Contributor.
From the Azure portal, go to Log Analytics workspaces.
Select Access control (IAM).
Select Add > Add role assignment.
On the Role tab, select the Microsoft Sentinel Contributor role, and then select Next.
On the Members tab, select Assign access to > User, group, or service principal.
Select members. By default, Microsoft Entra applications aren't displayed in the available options. To find your application, search for it by name.
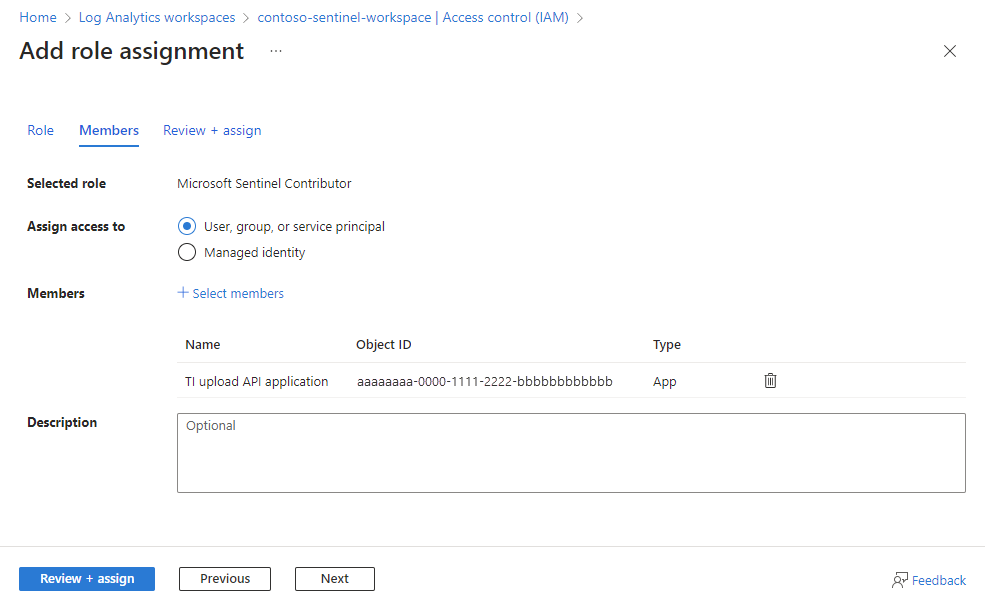
Select Review + assign.
For more information on assigning roles to applications, see Assign a role to the application.
Configure your threat intelligence platform solution or custom application
The following configuration information is required by the upload API:
- Application (client) ID
- Microsoft Entra access token with OAuth 2.0 authentication
- Microsoft Sentinel workspace ID
Enter these values in the configuration of your integrated TIP or custom solution where required.
- Submit the threat intelligence to the upload API. For more information, see Microsoft Sentinel upload API.
- Within a few minutes, threat intelligence objects should begin flowing into your Microsoft Sentinel workspace. Find the new STIX objects on the Threat intelligence page, which is accessible from the Microsoft Sentinel menu.
Related content
In this article, you learned how to connect your TIP to Microsoft Sentinel. To learn more about using threat intelligence in Microsoft Sentinel, see the following articles:
- Understand threat intelligence.
- Work with threat indicators throughout the Microsoft Sentinel experience.
- Get started detecting threats with built-in or custom analytics rules in Microsoft Sentinel.