Configure data encryption
APPLIES TO:  Azure Database for PostgreSQL - Flexible Server
Azure Database for PostgreSQL - Flexible Server
This article provides step-by-step instructions to configure data encryption for an Azure Database for PostgreSQL flexible server.
Important
Selection of system or customer managed encryption key for data encryption of an Azure Database for PostgreSQL flexible server, can only be made when the server is deployed.
In this article, you learn how to create a new server and configure its data encryption options. For existing servers, whose data encryption is configured to use customer managed encryption key, you learn:
- How to select a different user assigned managed identity with which the service accesses the encryption key.
- How to specify a different encryption key or how to rotate the encryption key currently used for data encryption.
To learn about data encryption in the context of Azure Database for PostgreSQL - Flexible Server, see the data encryption.
Configure data encryption with system managed key during server provisioning
Using the Azure portal:
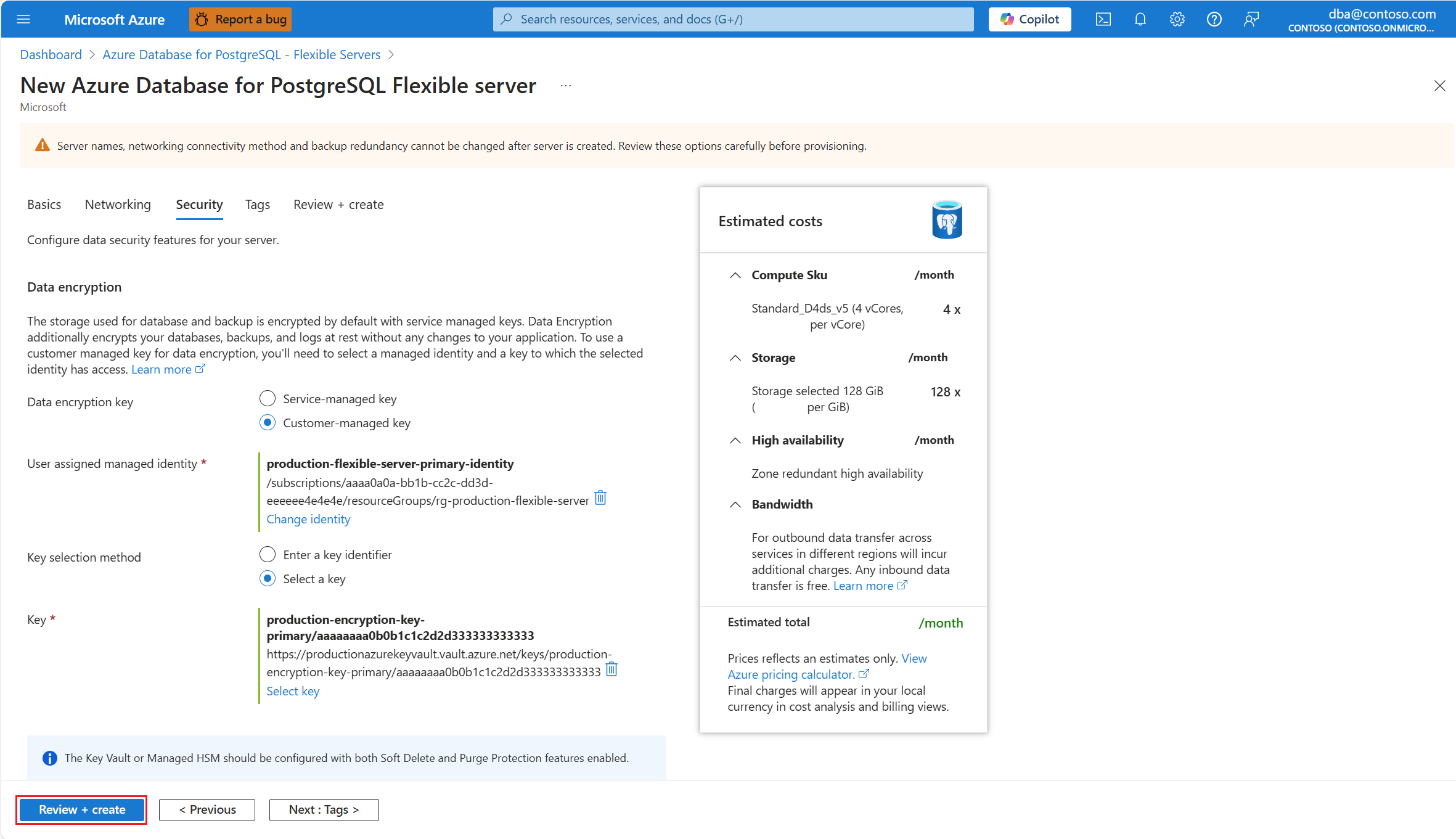
During provisioning of a new instance of Azure Database for PostgreSQL Flexible Server, in the Security tab.
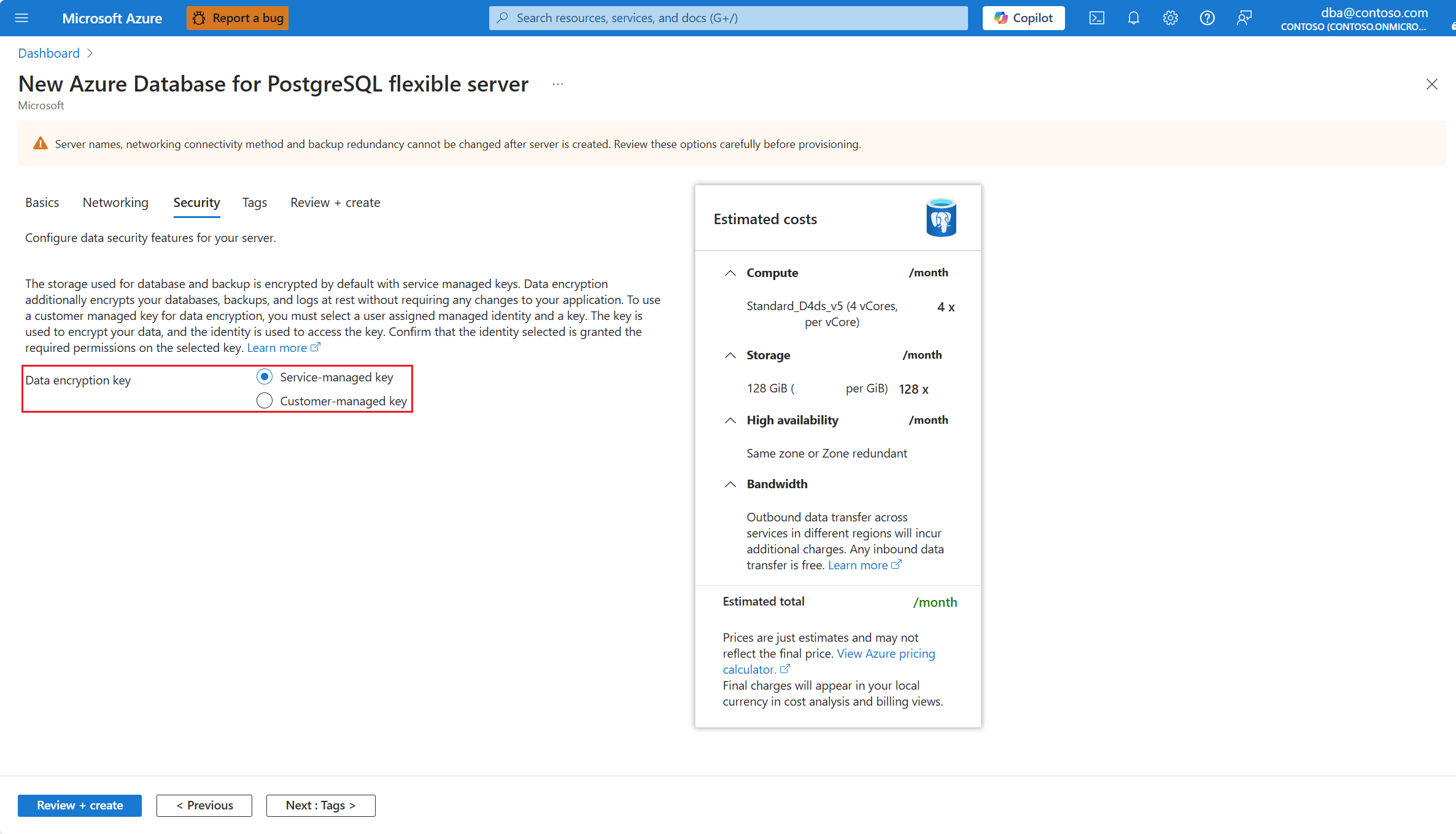
In the Data encryption key, select the Service-managed key radio button.
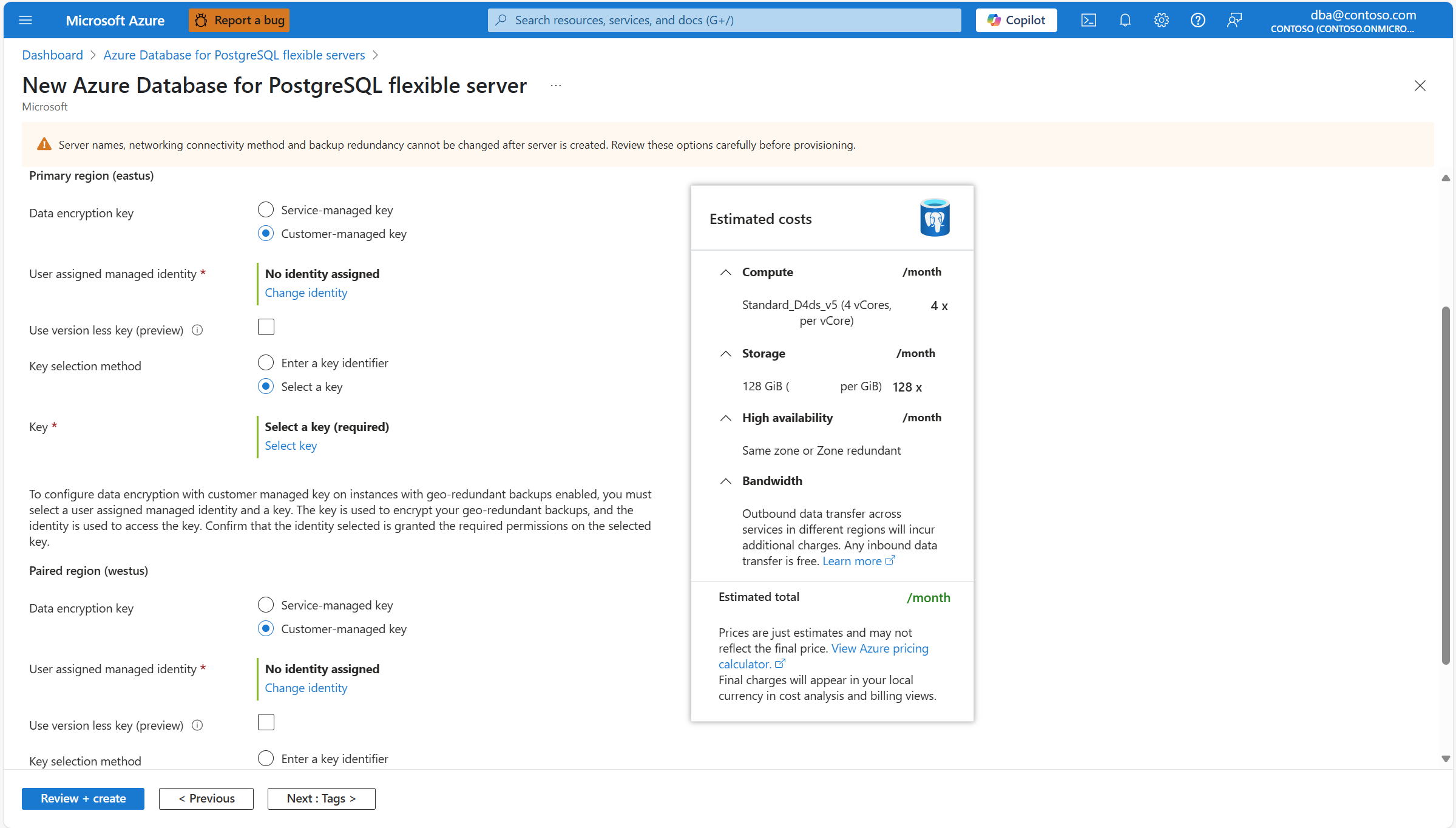
If you enable geo-redundant backup storage to be provisioned together with the server, the aspect of the Security tab changes slightly because the server uses two separate encryption keys. One for the primary region in which you're deploying your server, and one for the paired region to which the server backups are asynchronously replicated.
Configure data encryption with customer managed key during server provisioning
Using the Azure portal:
Create one user assigned managed identity, if you don't have one yet. If your server has geo-redundant backups enabled, you need to create to different identities. Each of those identities is used to access each of the two data encryption keys.
Note
Although it isn't required, to maintain regional resiliency, we recommend that you create the user managed identity in the same region as your server. And if your server has geo-backup redundancy enabled, we recommend that the second user managed identity, used to access the data encryption key for geo-redundant backups, is created in the paired region of the server.
Create one Azure Key Vault or create one Managed HSM, if you don't have one key store created yet. Make sure that you meet the requirements. Also, follow the recommendations before you configure the key store, and before you create the key and assign the required permissions to the user assigned managed identity. If your server has geo-redundant backups enabled, you need to create a second key store. That second key store is used to keep the data encryption key with which your backups copied to the paired region of the server are encrypted.
Note
The key store used to keep the data encryption key must be deployed in the same region as your server. And if your server has geo-backup redundancy enabled, the key store that keeps the data encryption key for geo-redundant backups must be created in the paired region of the server.
Create one key in your key store. If your server has geo-redundant backups enabled, you need one key on each of the key stores. With one of these keys, we encrypt all your server's data (including all system and user databases, temporary files, server logs, write-ahead log segments, and backups). With the second key, we encrypt the copies of the backups which are asynchronously copied over the paired region of your server.
During provisioning of a new instance of Azure Database for PostgreSQL Flexible Server, in the Security tab.
In the Data encryption key, select the Service-managed key radio button.
If you enable geo-redundant backup storage to be provisioned together with the server, the aspect of the Security tab changes slightly because the server uses two separate encryption keys. One for the primary region in which you're deploying your server, and one for the paired region to which the server backups are asynchronously replicated.
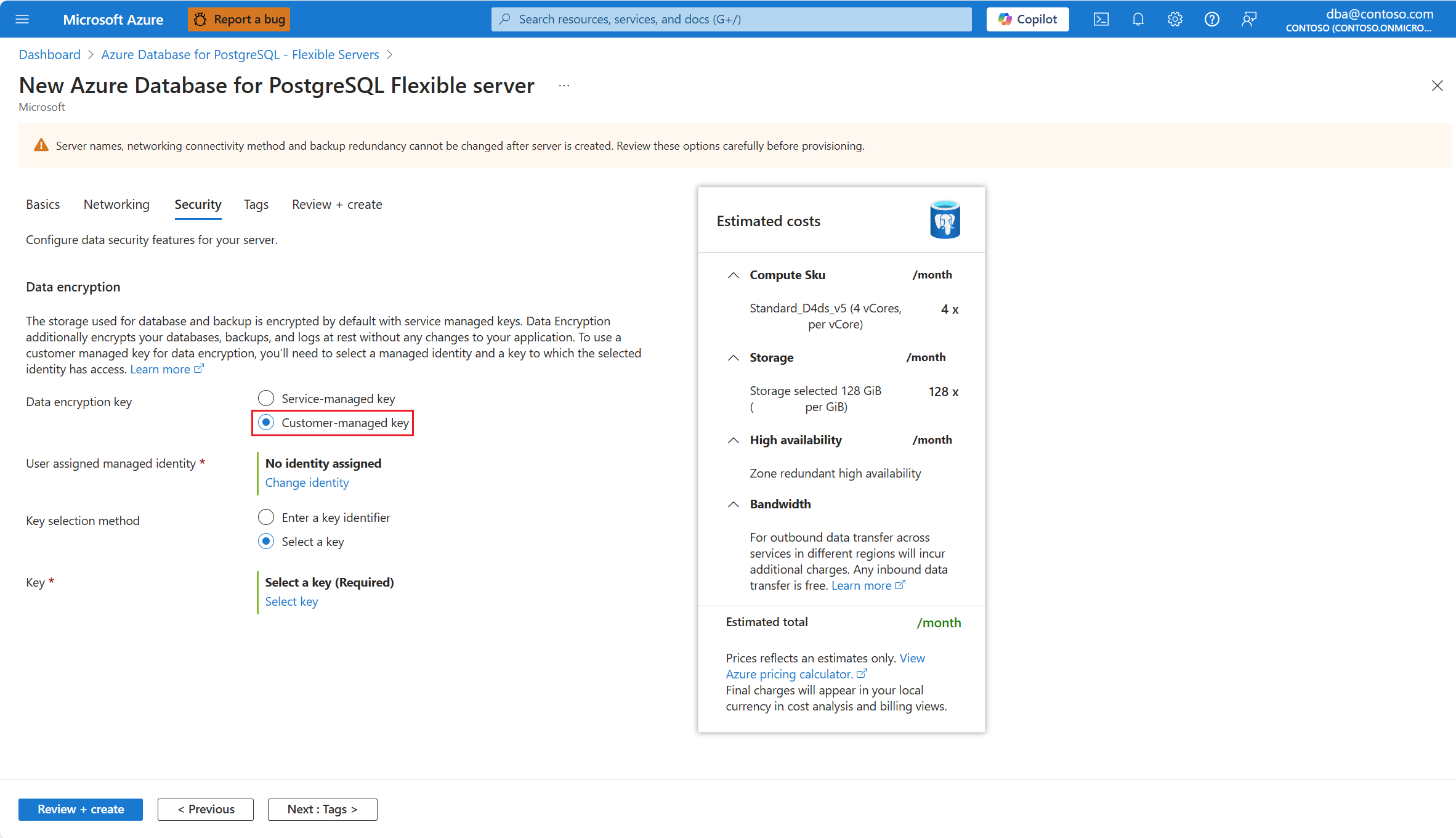
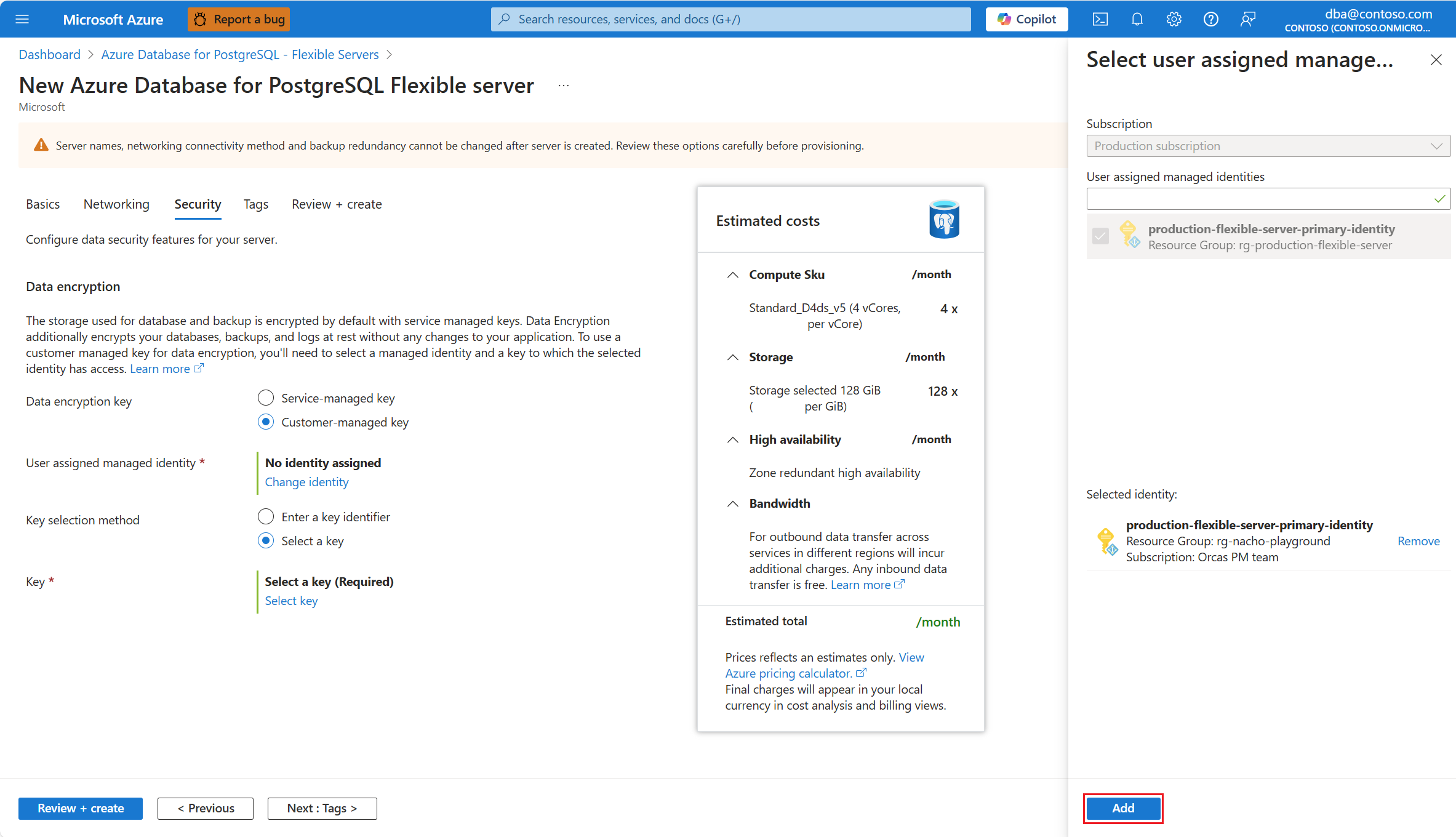
In User assigned managed identity, select Change identity.
Among the list of user assigned managed identities, select the one you want your server to use to access the data encryption key stored in an Azure Key Vault.
Select Add.
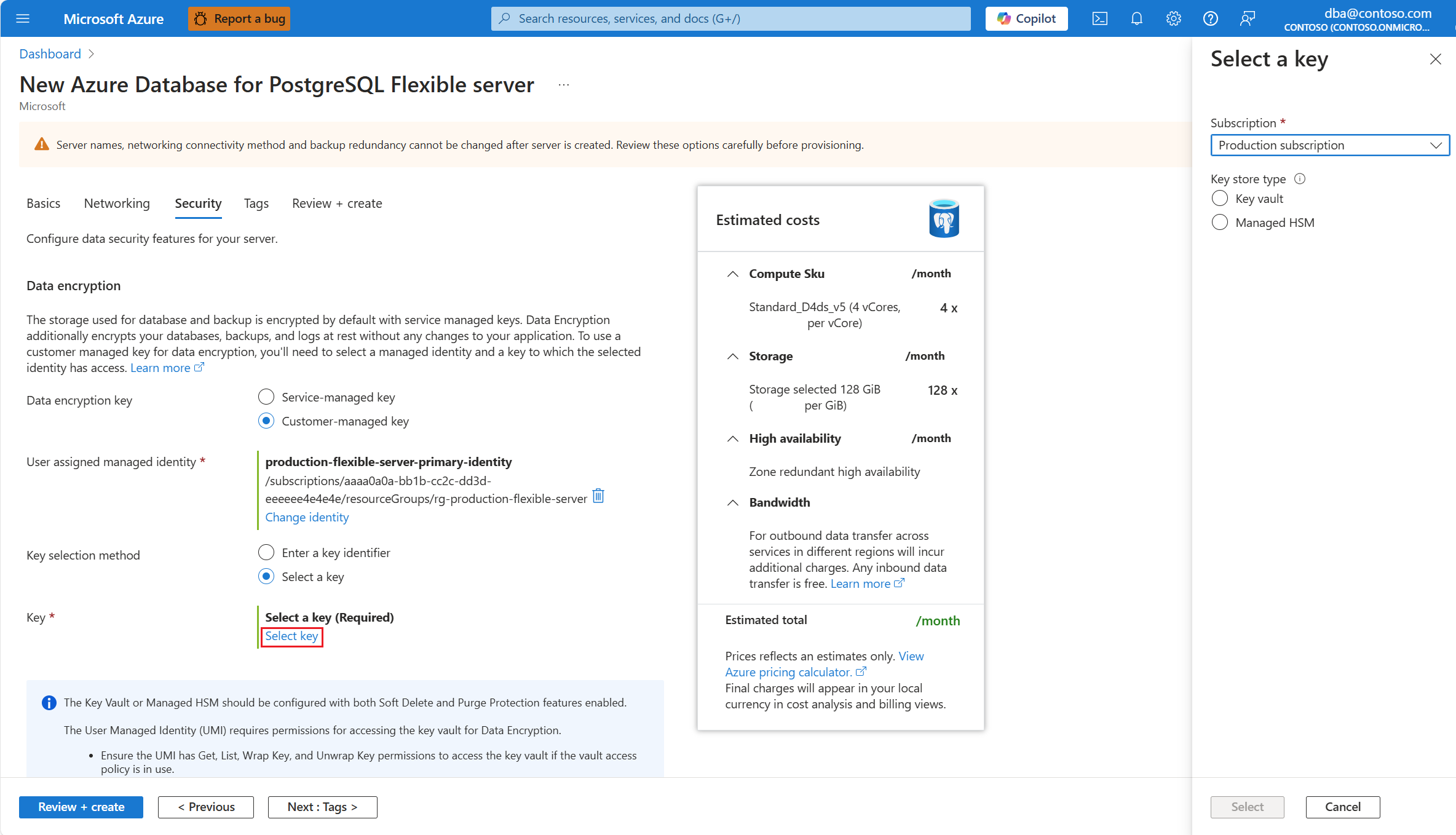
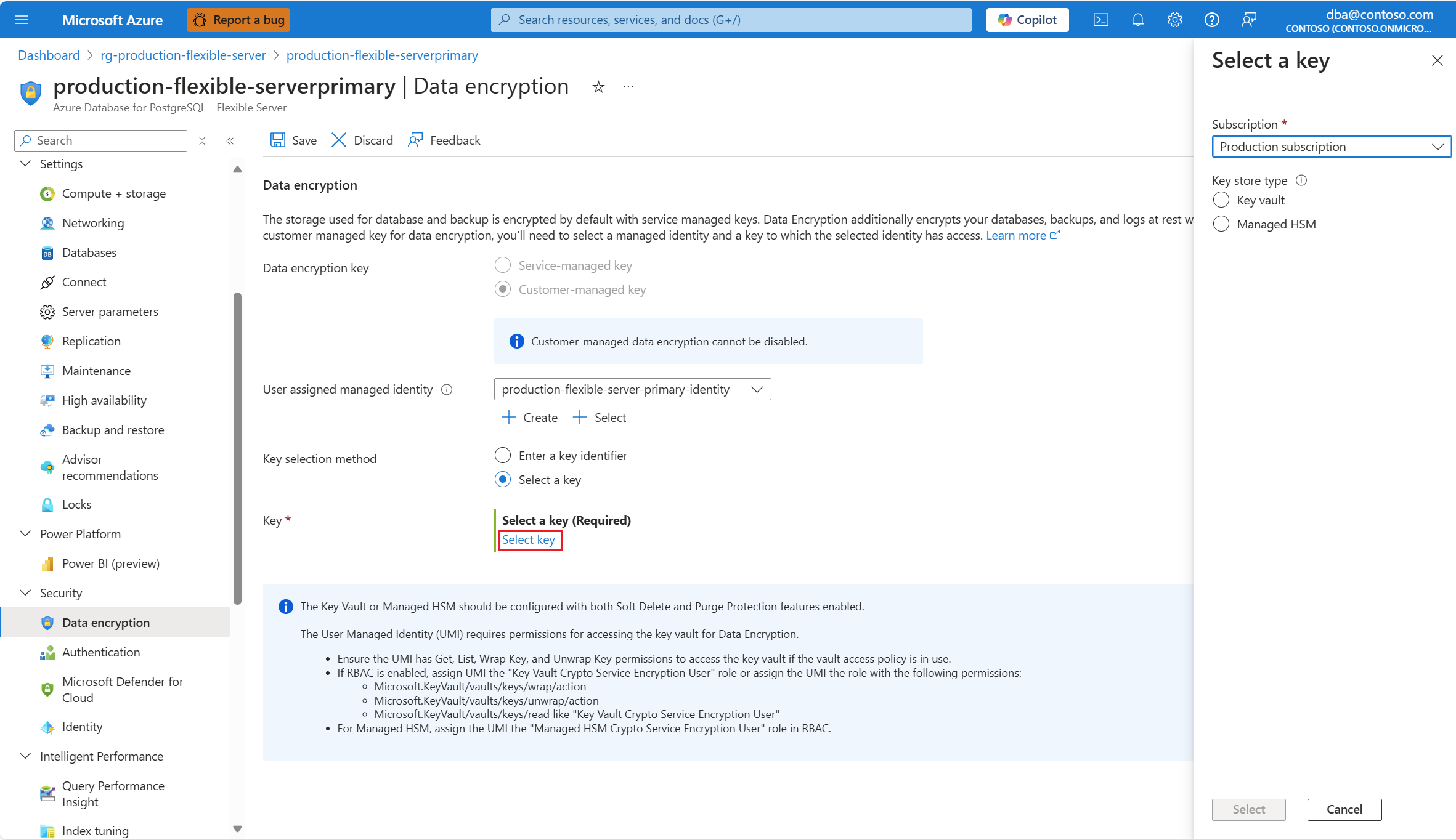
Select Select a key.
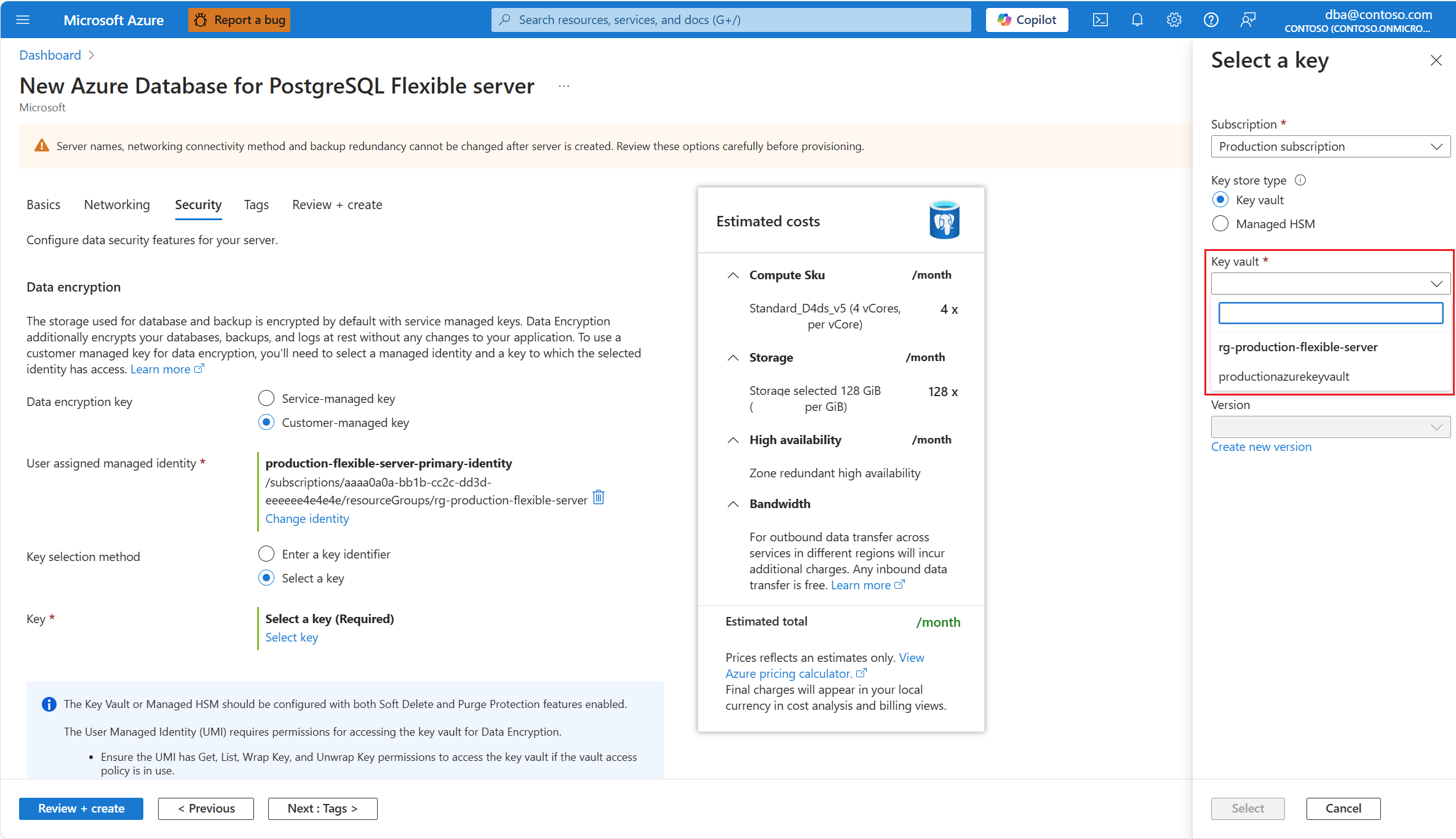
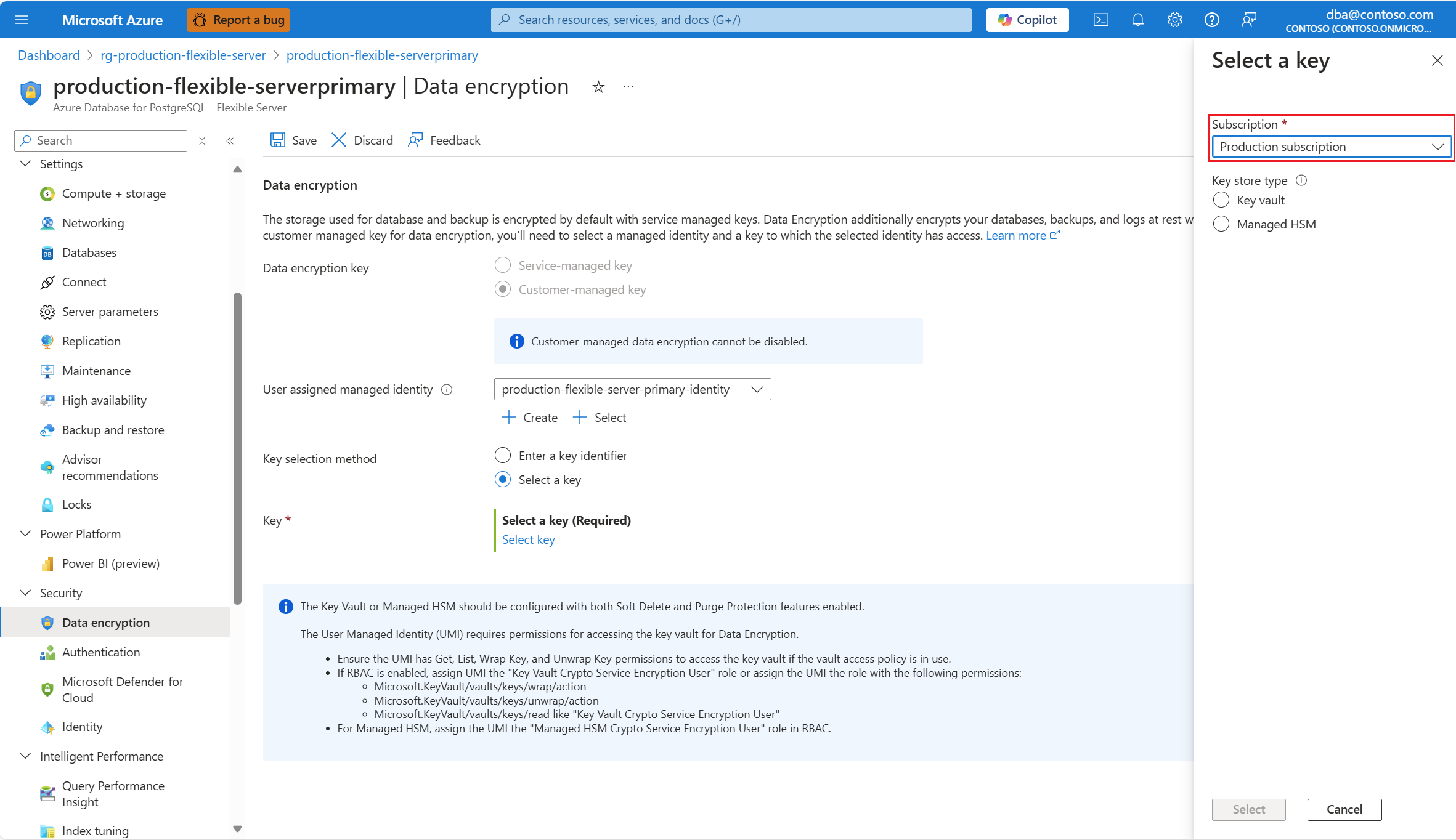
Subscription is automatically populated with the name of the subscription on which your server is about to be created. The key store that keeps the data encryption key must exist in the same subscription as the server.
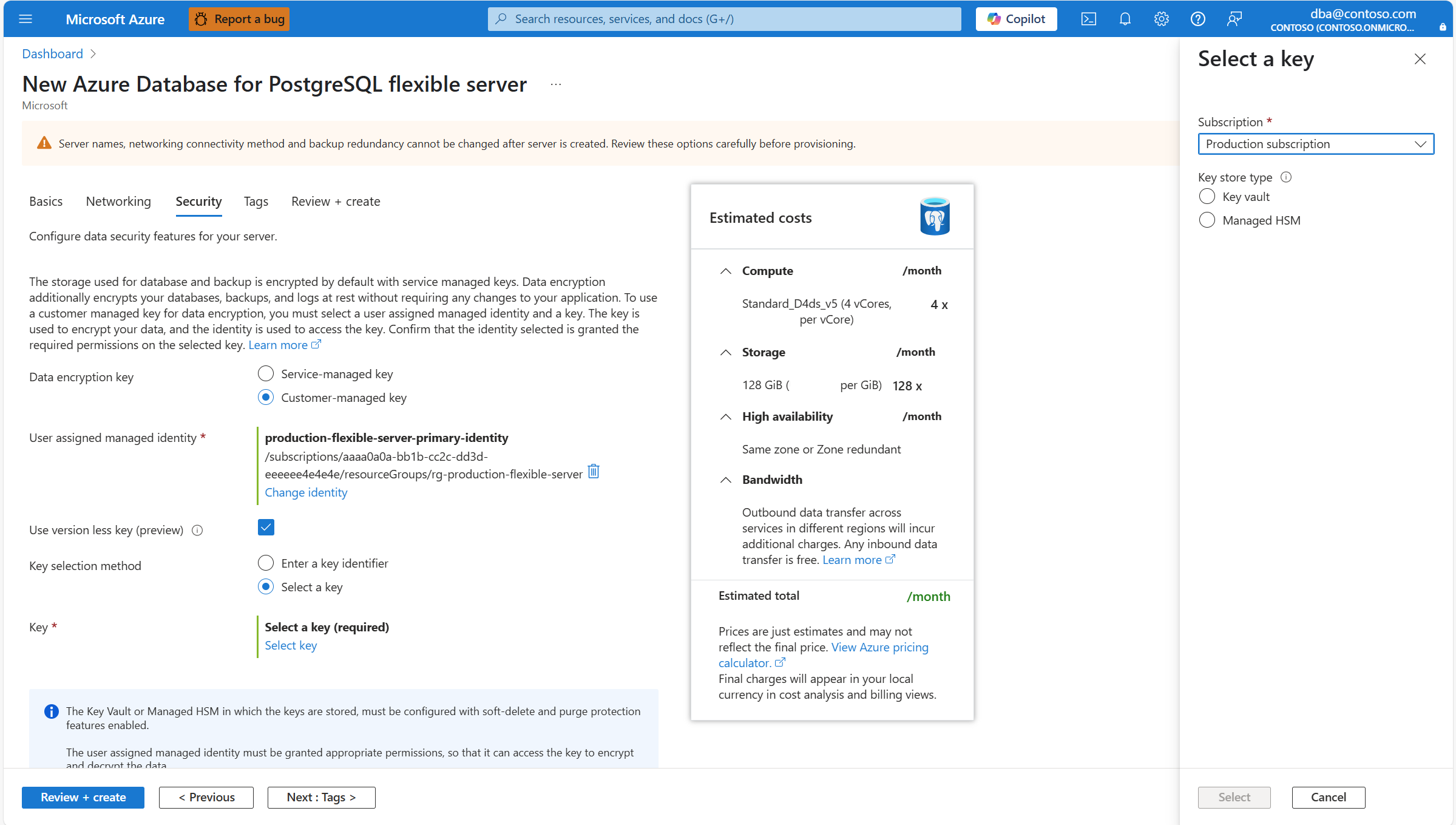
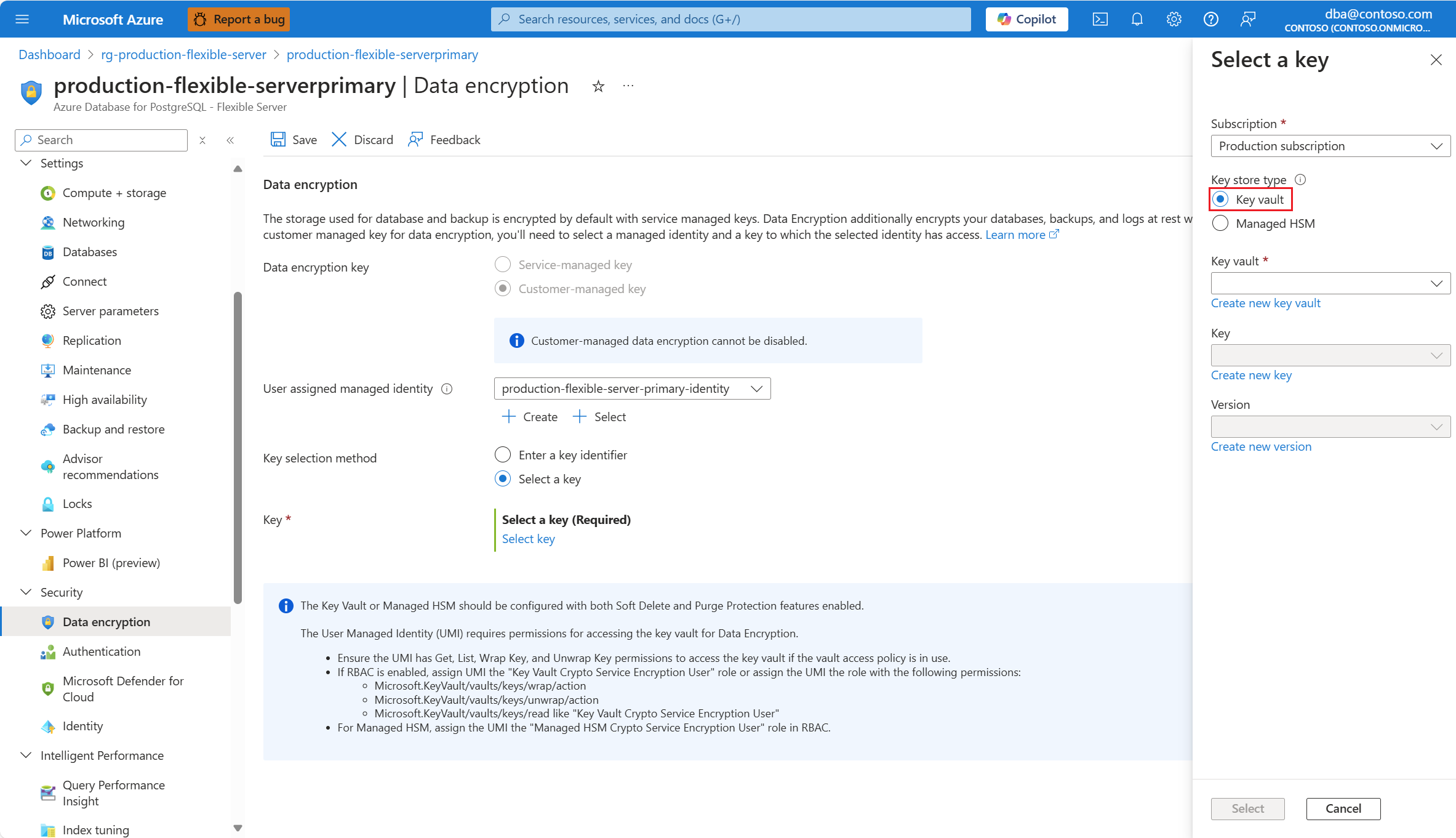
In Key store type, select the radio button corresponding to the type of key store in which you plan to store the data encryption key. In this example, we choose Key vault, but the experience is similar if you choose Managed HSM.
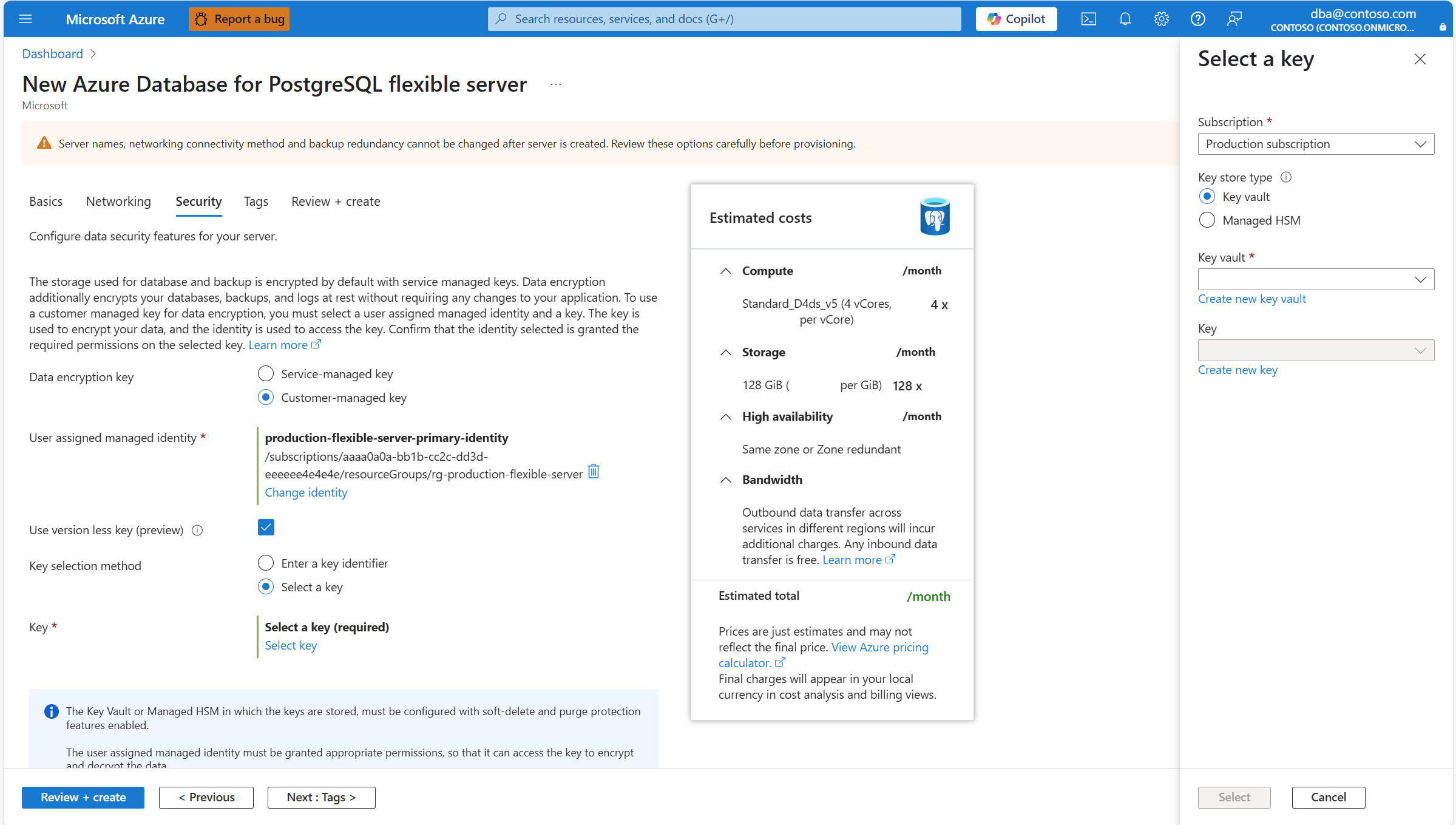
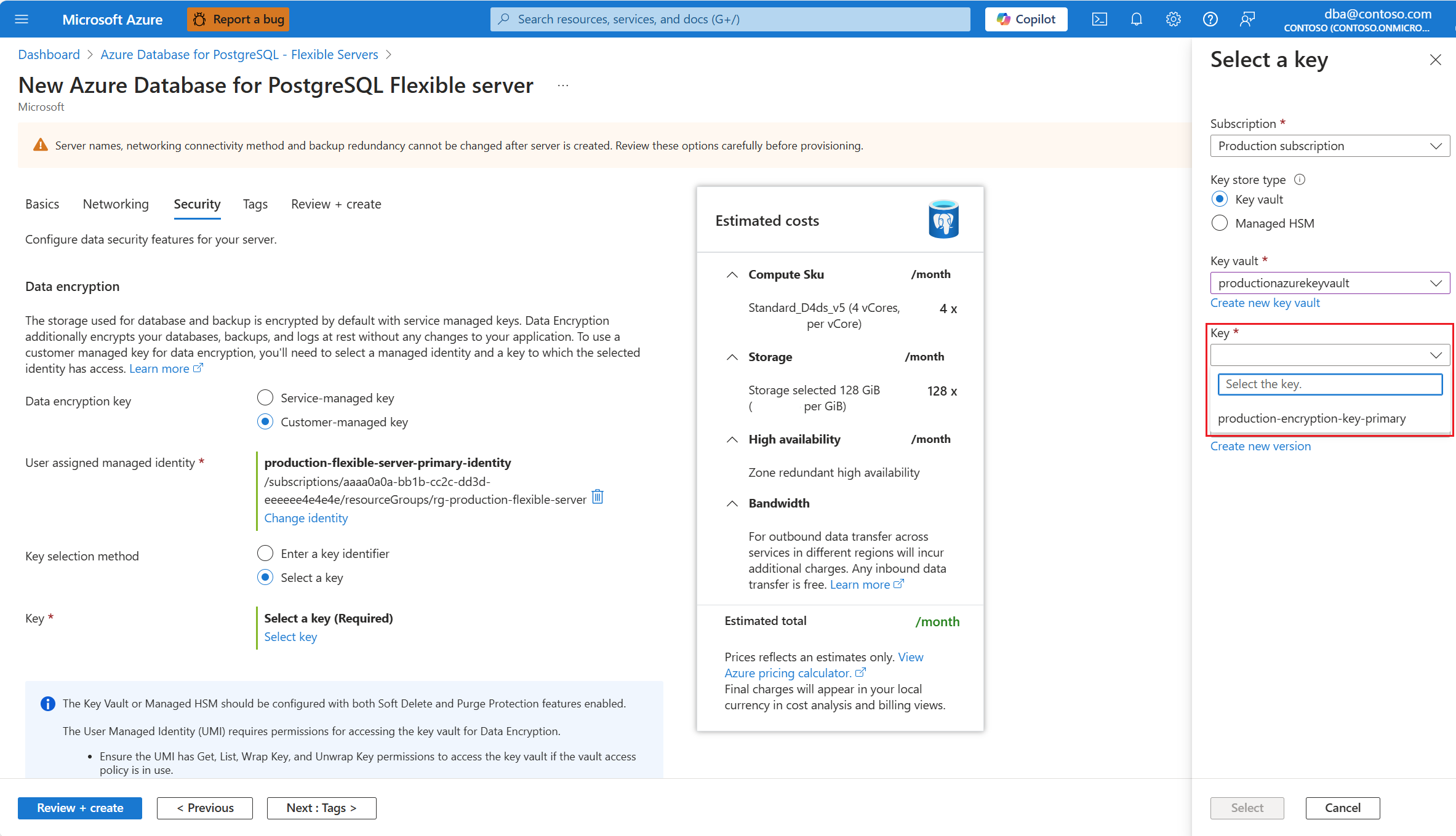
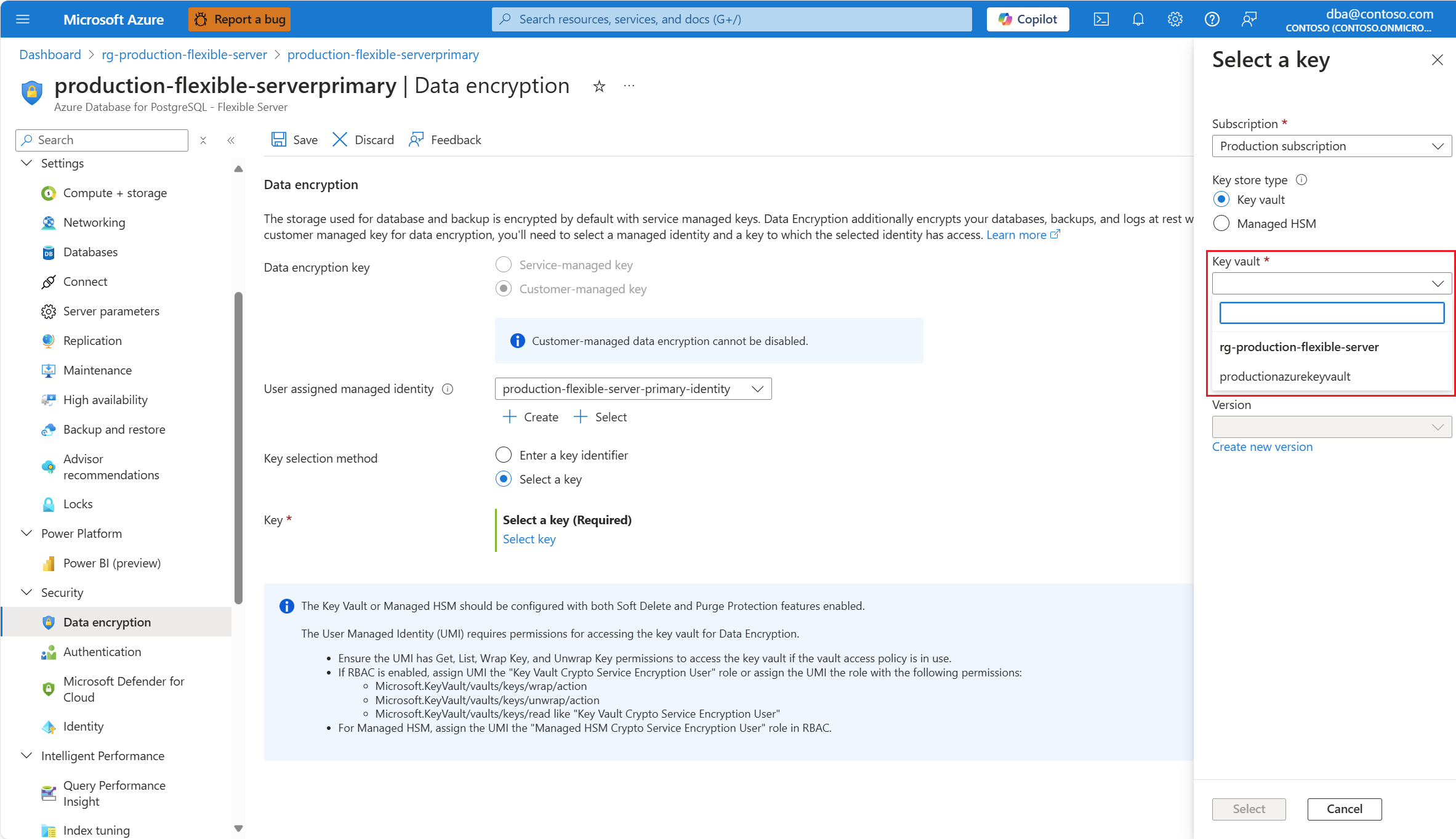
Expand Key vault (or Managed HSM, if you selected that storage type), and select the instance where the data encryption key exists.
Note
When you expand the drop-down box, it shows No available items. It takes a few seconds until it lists all the instances of key vault which are deployed in the same region as the server.
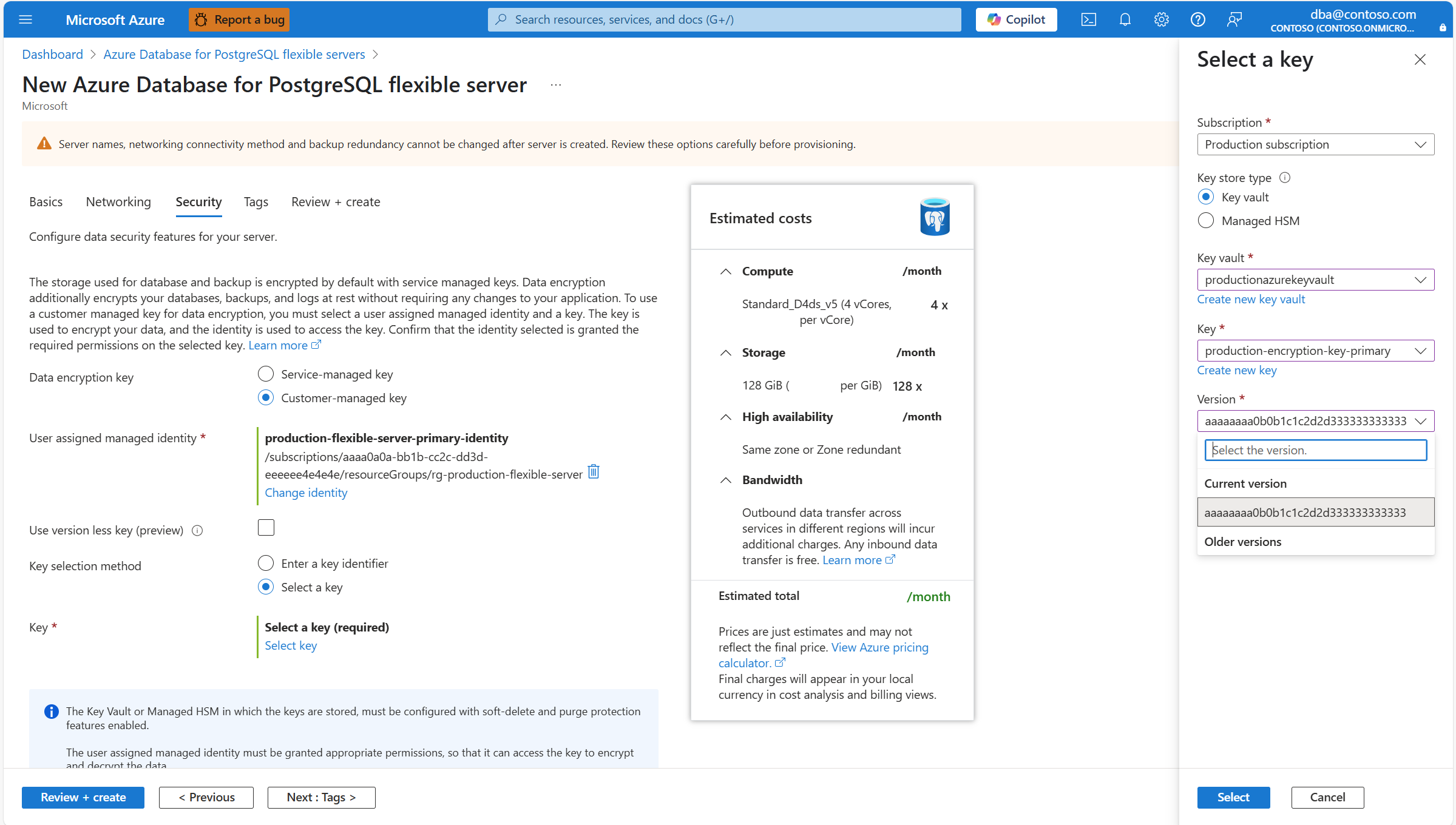
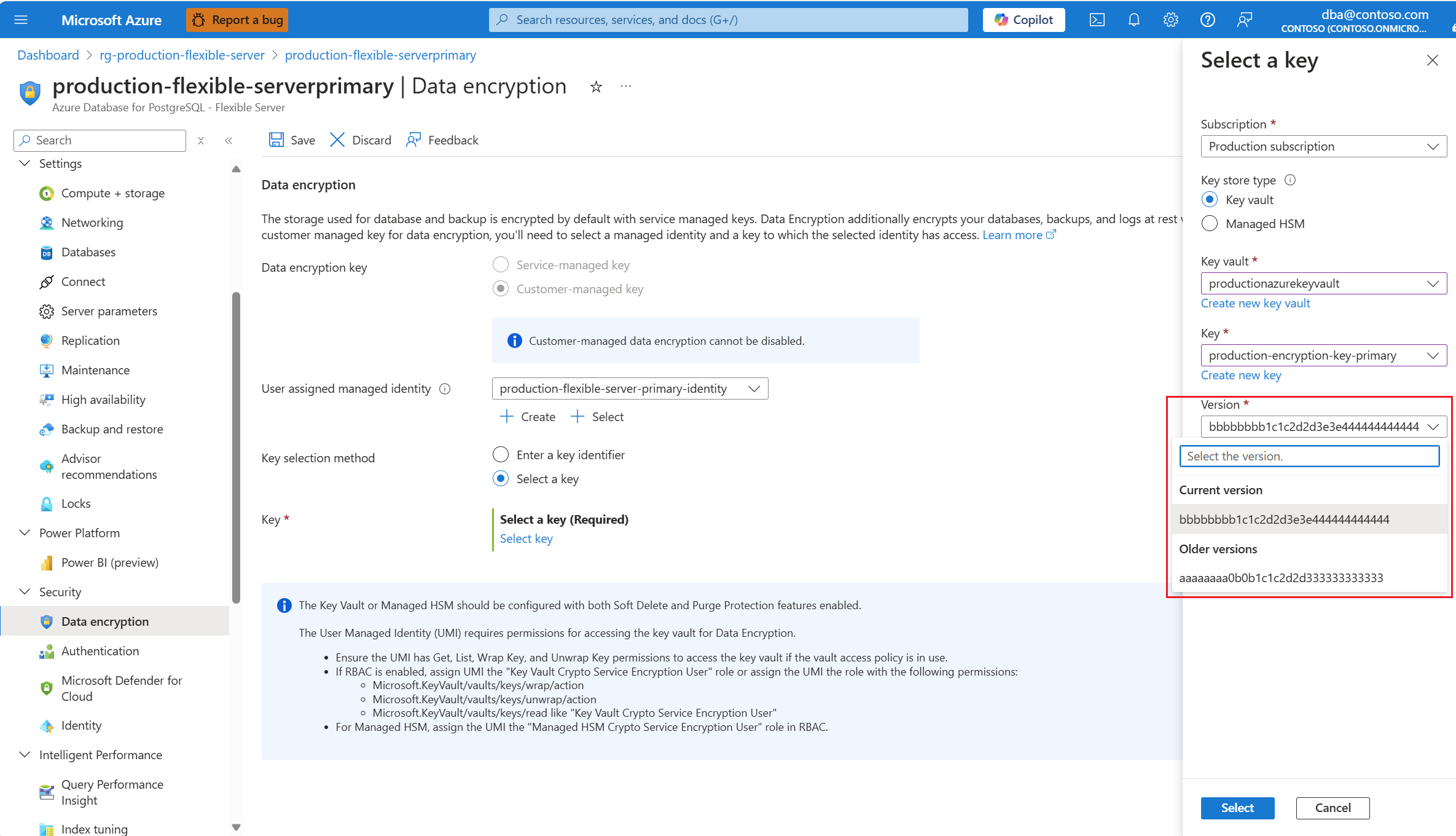
Expand Key, and select the name of the key that you want to use for data encryption.
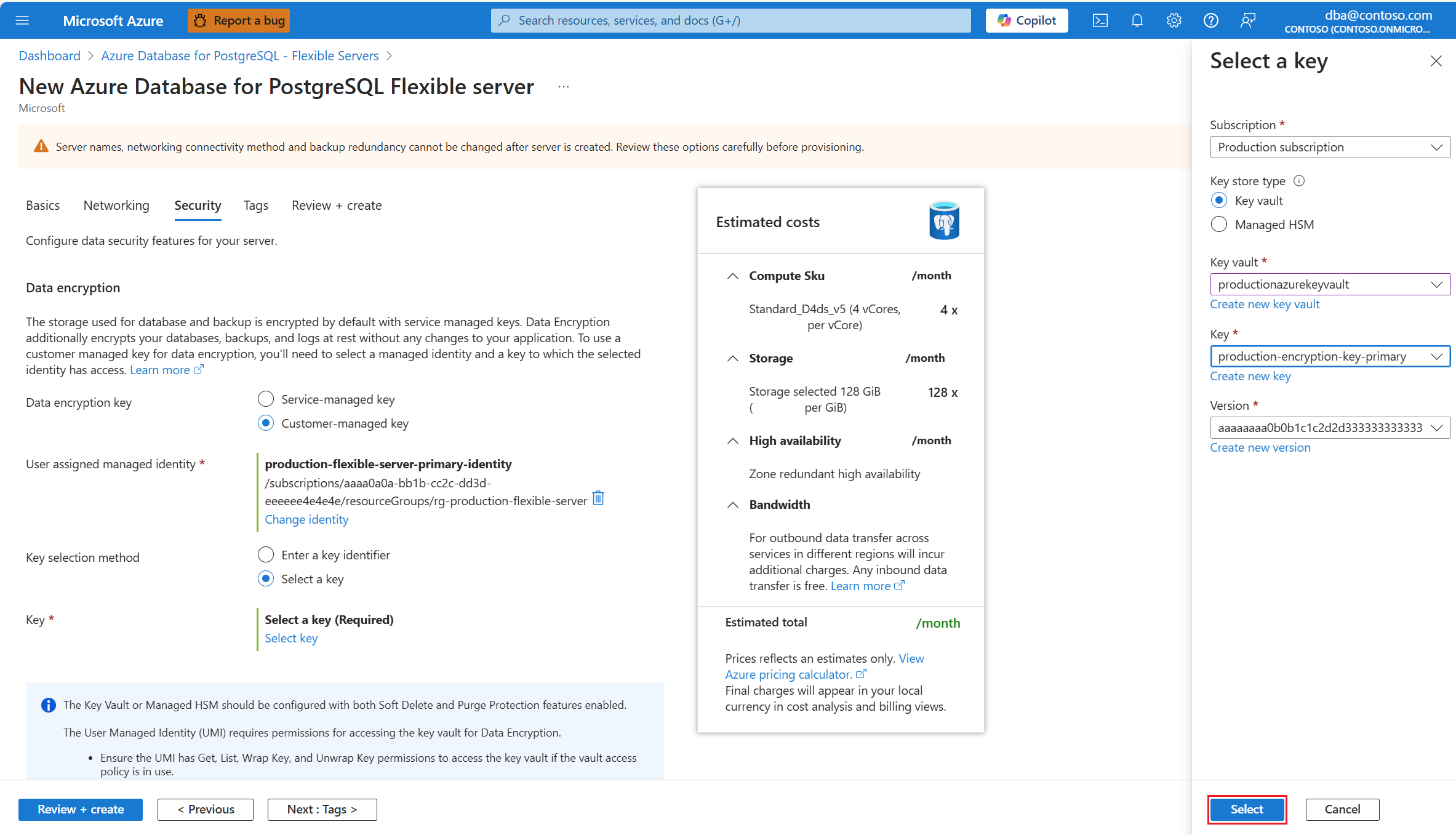
Expand Version, and select the identifier of the version of the key that you want to use for data encryption.
Select Select.
Configure all other settings of the new server and select Review + create.
Configure data encryption with customer managed key on existing servers
The only point at which you can decide if you want to use a system managed key or a customer managed key for data encryption, is at server creation. Once you make that decision and create the server, you can't switch between the two options. The only alternative, if you want to change from one to the other, requires restoring any of the backups available of server onto a new server. While configuring the restore, you're allowed to change the data encryption configuration of the new server.
For existing servers that were deployed with data encryption using a customer managed key, you're allowed to do several configuration changes. Things that can be changed are the references to the keys used for encryption, and references to the user assigned managed identities used by the service to access the keys kept in the key stores.
You must update references that your Azure Database for PostgreSQL flexible server has to a key:
- When the key stored in the key store is rotated, either manually or automatically.
- When you want to use the same or a different key stored in a different key store.
You must update the user assigned managed identities which are used by your Azure Database for PostgreSQL flexible server to access the encryption keys:
- Whenever you want to use a different identity
Using the Azure portal:
Select your Azure Database for PostgreSQL flexible server.
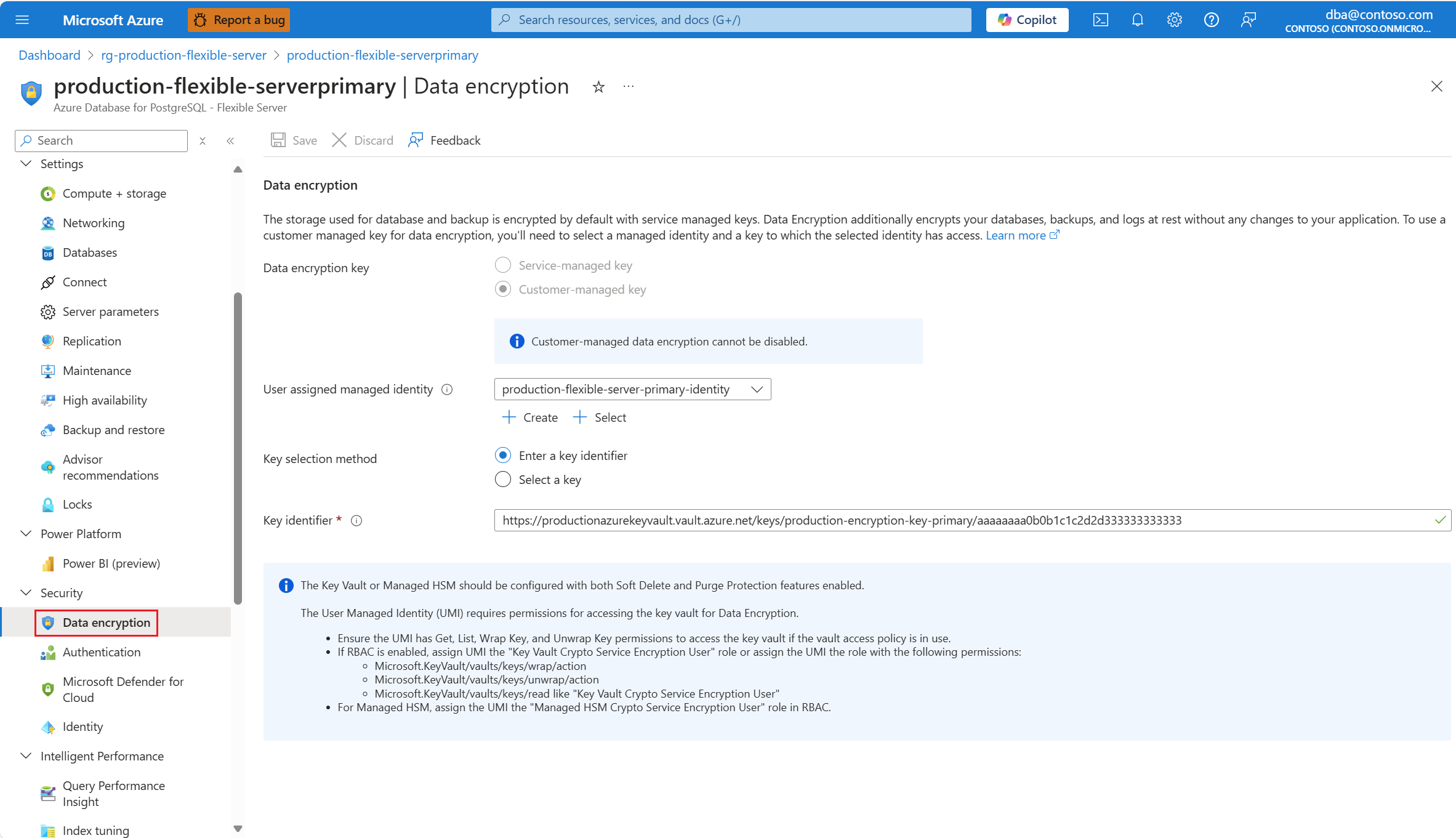
In the resource menu, under the Security section, select Data encryption.
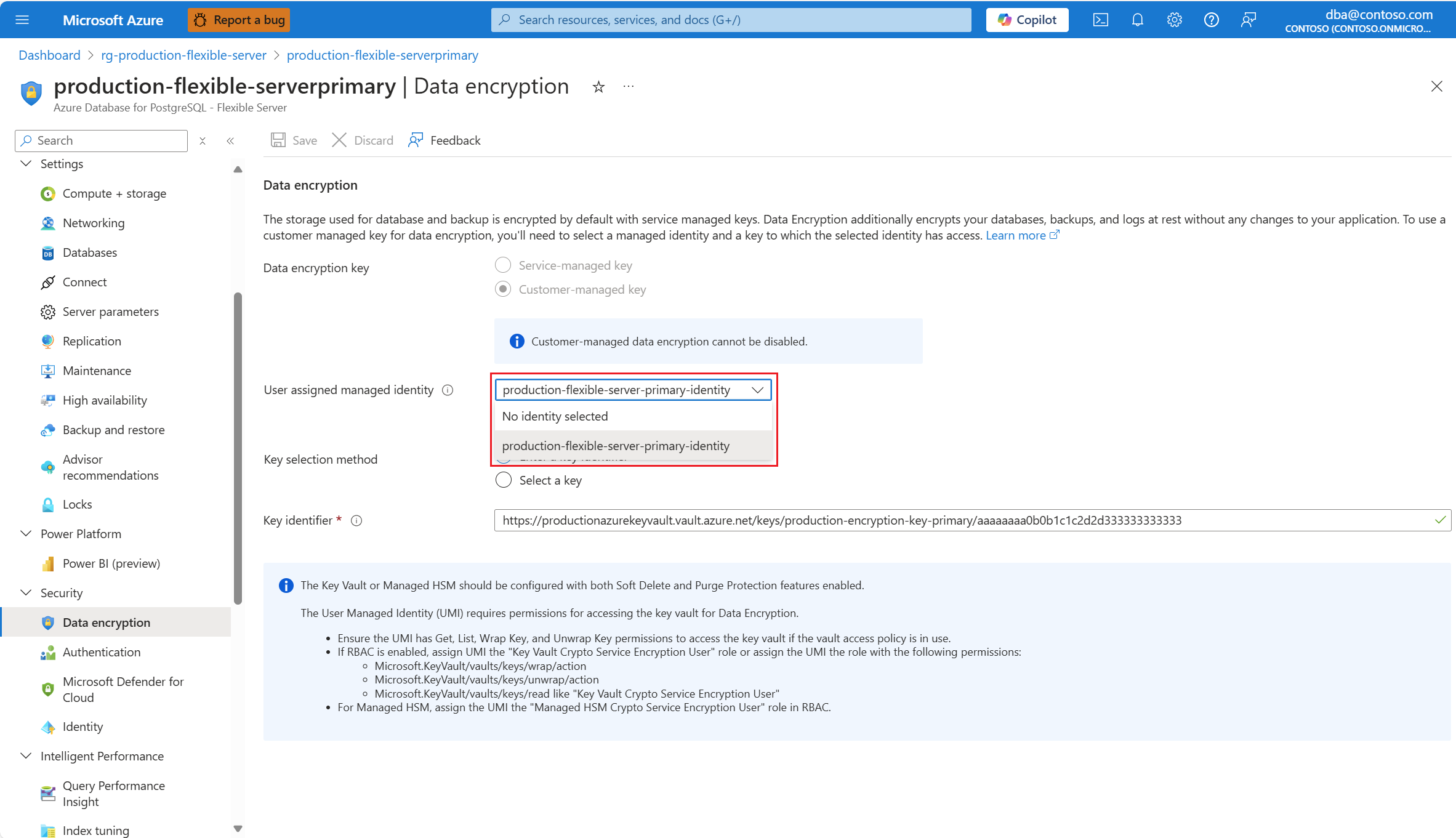
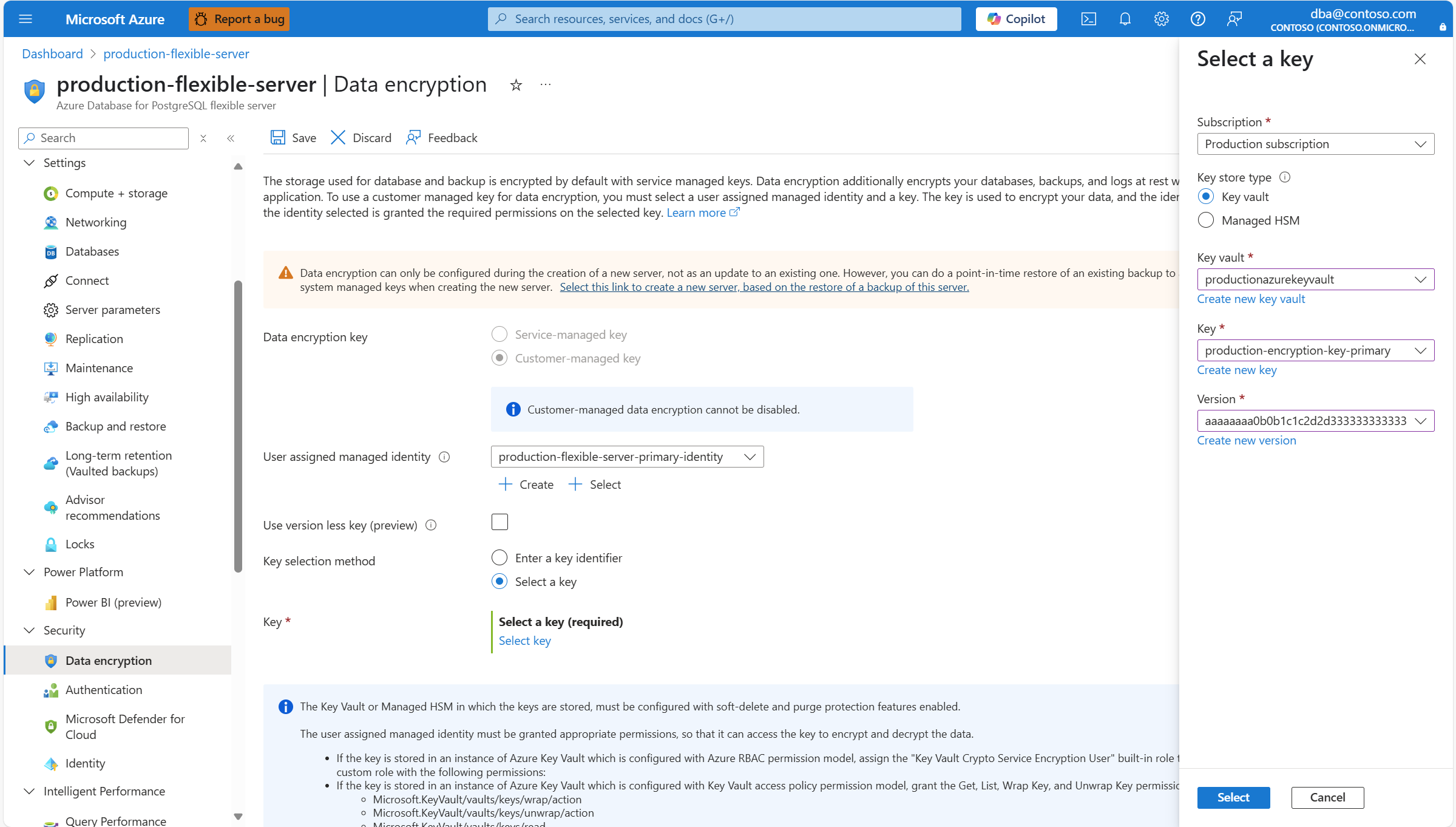
To change the user assigned managed identity with which the server accesses the key store in which the key is kept, expand the User assigned managed identity drop-down, and select any of the identities available.
Note
Identities shown in the combo-box are only the ones that your Azure Database for PostgreSQL flexible server was assigned. Although it isn't required, to maintain regional resiliency, we recommend that you select user managed identities in the same region as your server. And if your server has geo-backup redundancy enabled, we recommend that the second user managed identity, used to access the data encryption key for geo-redundant backups, exists in the paired region of the server.
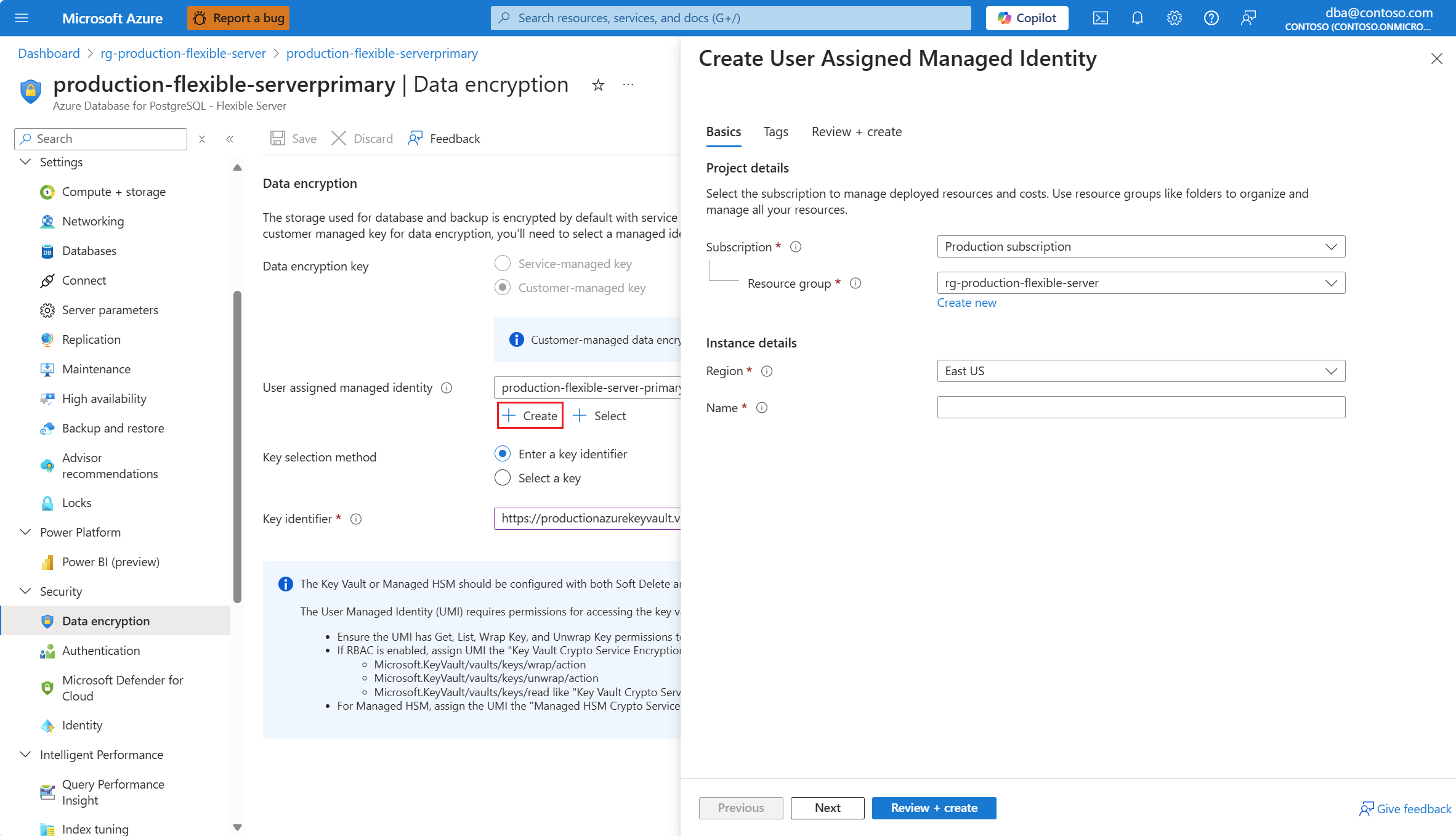
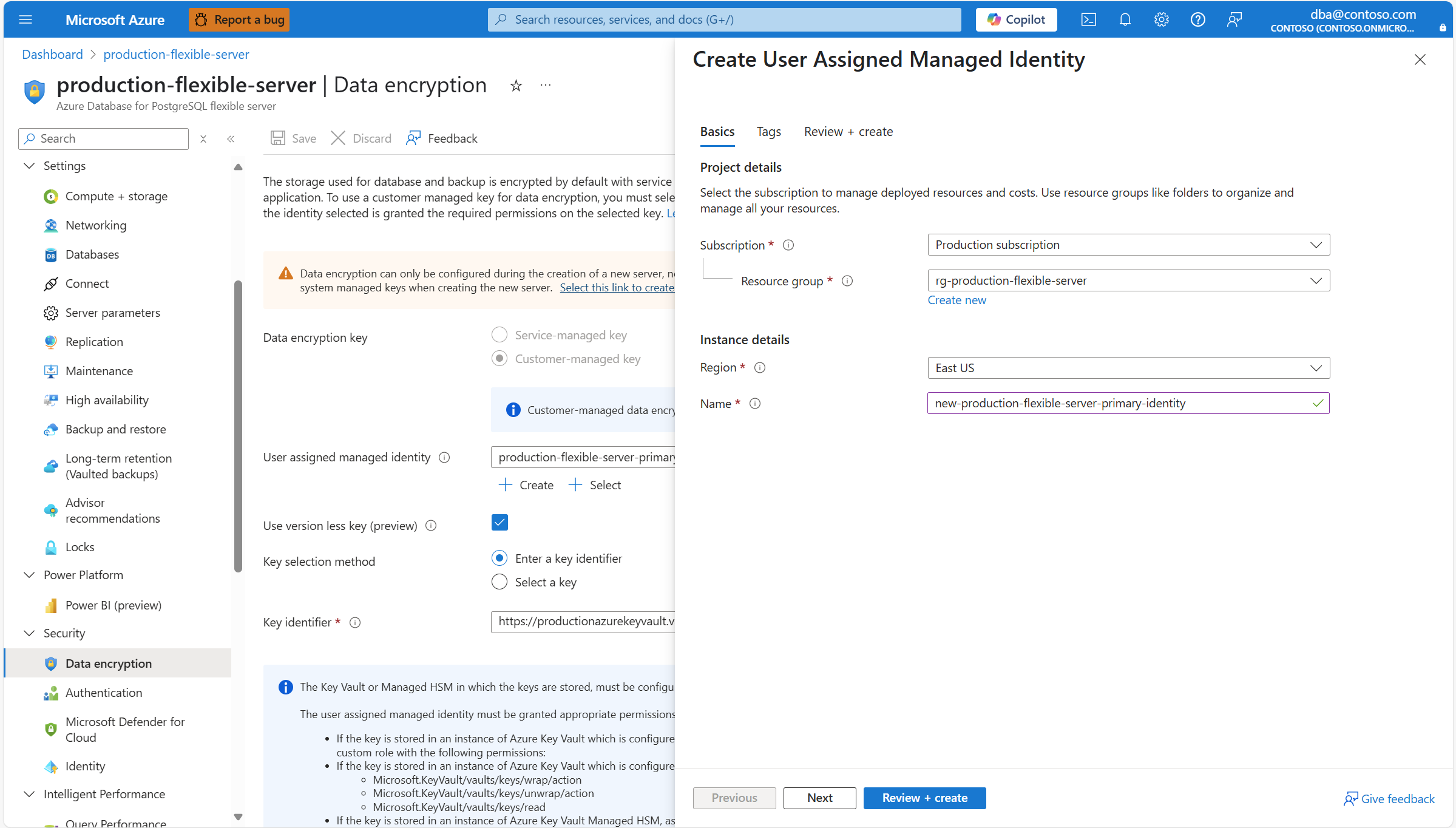
If the user assigned managed identity that you want to use to access the data encryption key isn't assigned to your Azure Database for PostgreSQL flexible server, and it doesn't even exist as an Azure resource with its corresponding object in Microsoft Entra ID, you can create it by selecting Create.
In the Create User Assigned Managed Identity panel, complete the details of the user assigned managed identity that you want to create, and automatically assign to your Azure Database for PostgreSQL flexible server to access the data encryption key.
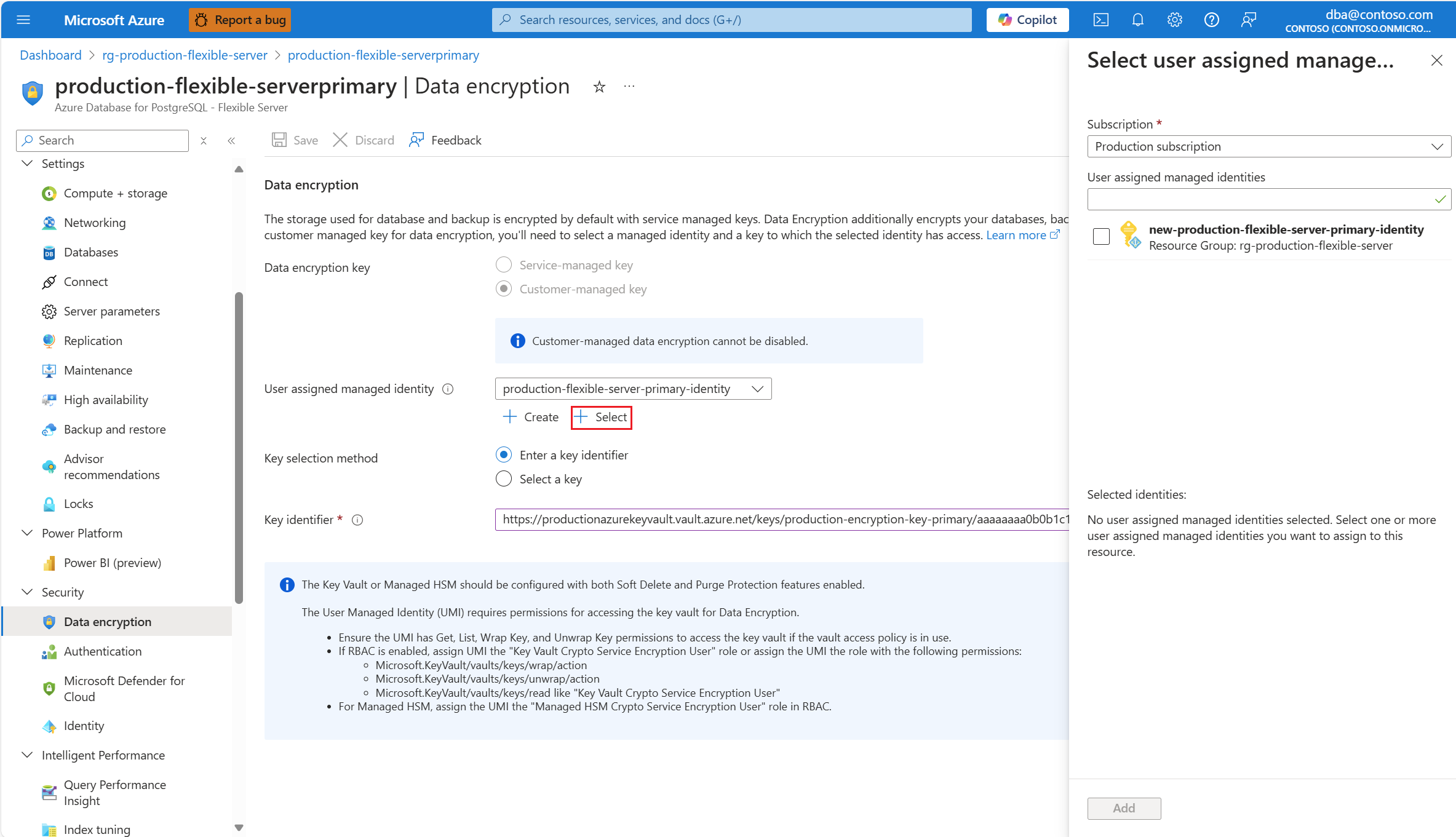
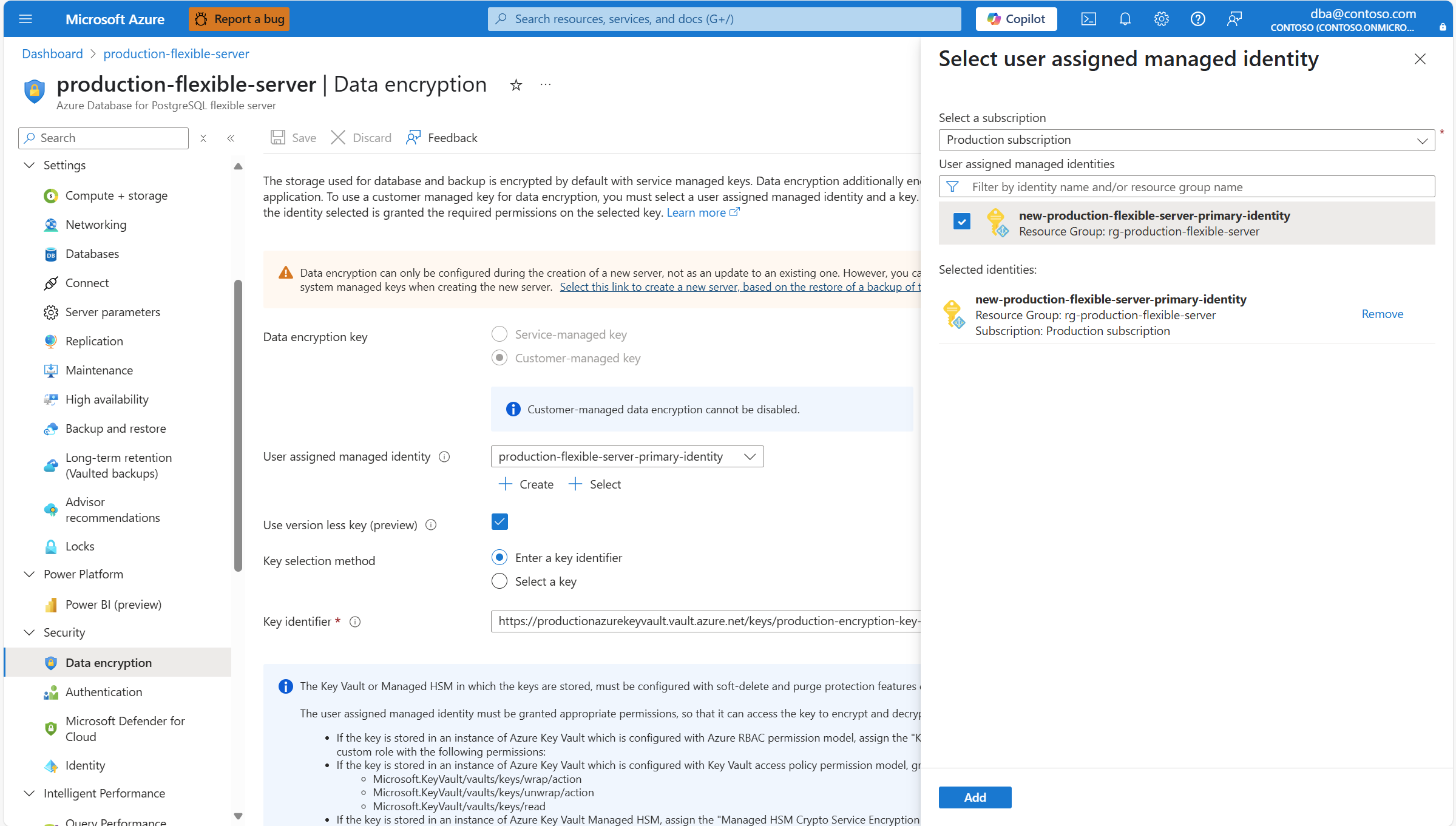
If the user assigned managed identity that you want to use to access the data encryption key isn't assigned to your Azure Database for PostgreSQL flexible server, but it does exist as an Azure resource with its corresponding object in Microsoft Entra ID, you can assign it by selecting Select.
Among the list of user assigned managed identities, select the one you want your server to use to access the data encryption key stored in an Azure Key Vault.
Select Add.
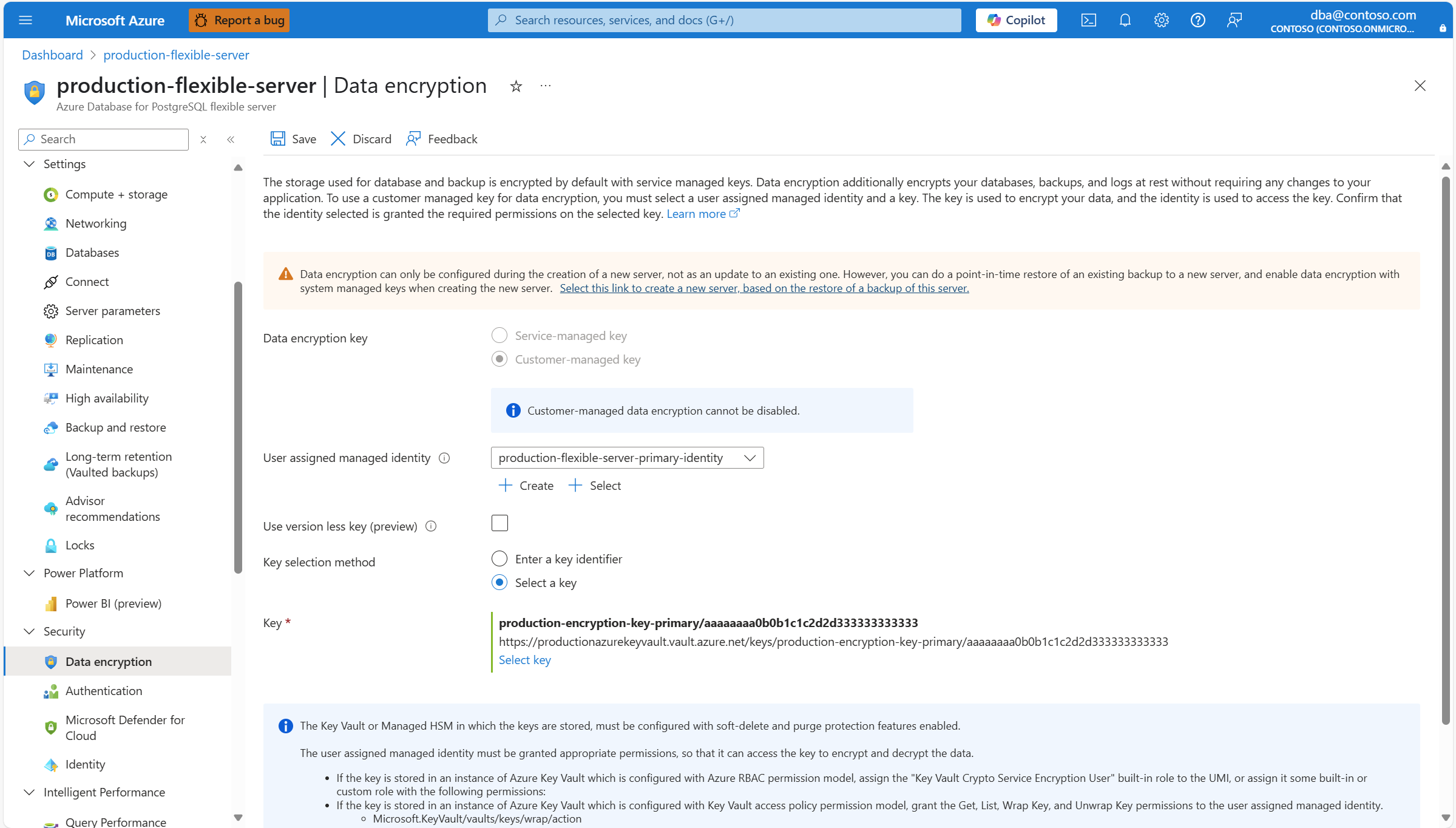
If you rotate the key, or you want to use a different key, you must update your Azure Database for PostgreSQL flexible server so that it points to the new key version or new key. To do that, you can copy the resource identifier of the key, and paste it in the Key identifier box.
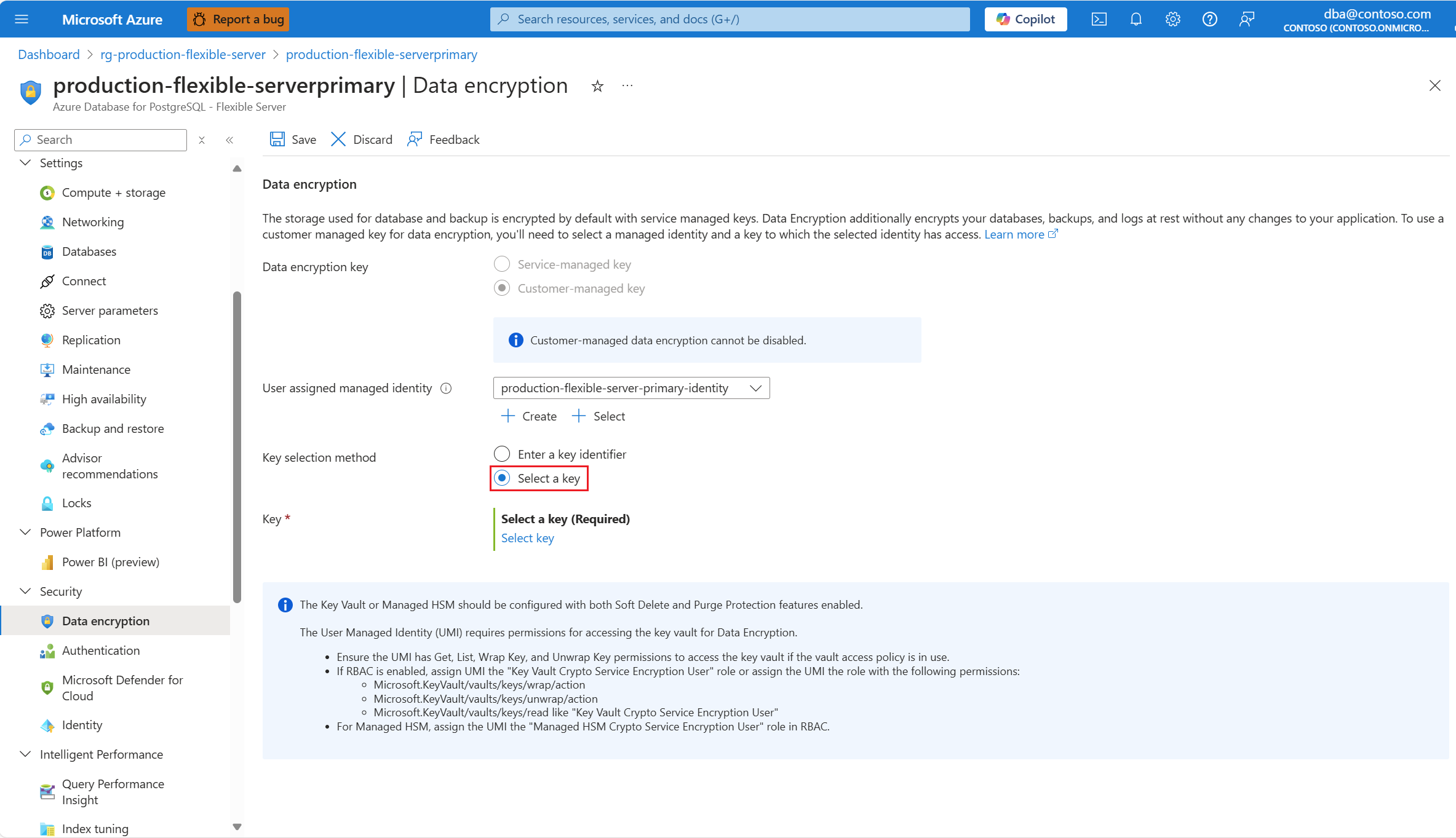
If the user accessing Azure portal has permissions to access the key stored in the key store, you can use an alternative approach to choose the new key or new key version. To do that, in Key selection method, select the Select a key radio button.
Select Select key.
Subscription is automatically populated with the name of the subscription on which your server is about to be created. The key store that keeps the data encryption key must exist in the same subscription as the server.
In Key store type, select the radio button corresponding to the type of key store in which you plan to store the data encryption key. In this example, we choose Key vault, but the experience is similar if you choose Managed HSM.
Expand Key vault (or Managed HSM, if you selected that storage type), and select the instance where the data encryption key exists.
Note
When you expand the drop-down box, it shows No available items. It takes a few seconds until it lists all the instances of key vault which are deployed in the same region as the server.
Expand Key, and select the name of the key that you want to use for data encryption.
Expand Version, and select the identifier of the version of the key that you want to use for data encryption.
Select Select.
Once satisfied with the changes made, select Save.