Azure landing zones Terraform module
Azure provides native services for building your Azure landing zones. Other tools can also help with this effort. One tool that customers and partners often use to deploy landing zones is Terraform by HashiCorp.
Deployment of resources to application landing zones is outside the scope of the module. Decisions on the deployment method and tooling are for the team that's responsible for the application.
The Azure landing zones Terraform module provides a rapid implementation of the platform resources that you need to manage Azure landing zones at scale by using Terraform. The module is designed to simplify the deployment of the management group hierarchy, policies, and resources in the connectivity and management subscriptions.
Prerequisites
If you're new to Terraform and you want information about installing and using it, see the Install Terraform tutorial on HashiCorp Learn.
For information on how to set up the Terraform provider and authenticate with Azure, see the AzureRM provider guides on the Terraform website. To learn how to set up the provider for deploying across multiple subscriptions, see the Provider Configuration wiki page.
Importance of using standard modules
Reuse of components is a fundamental principle of infrastructure as code. Modules are instrumental in defining standards and consistency across resource deployment within and across environments.
The Azure landing zones Terraform module is published to the official Terraform Registry and is verified by HashiCorp.
Deploying the module from the Terraform Registry provides:
- An accelerated delivery of Azure landing zones in your environment.
- A tested upgrade path to the latest version of the module, along with strict version control.
Benefits of using the module
Benefits of using the Azure landing zones Terraform module include:
- A managed and extensible core resource hierarchy for subscription organization through management groups.
- Scalable security governance and compliance through Azure identity and access management (IAM) controls, with an extensive library of custom definitions ready to assign.
- Enforcement of policy across subscriptions through management group inheritance.
- Managed resources for management and connectivity landing zones. These resources provide:
- Assured policy compliance through tight integration of resources managed by the module and corresponding policy assignments.
- Integration between resources to reduce management overhead and provide an improved user experience, like automatic creation of virtual network links for Azure Private DNS.
Tip
The template library is updated programmatically from the Azure/Enterprise-Scale GitHub repository. To stay up to date with the latest archetype configuration, policies, and roles, make sure you're using the latest version of the module.
Resource deployment
You can configure the module to deploy sets of resources that align with the following critical design areas in Azure landing zones. Customize these resources to meet the requirements of your organization.
| Resource category | Critical design area |
|---|---|
| Core resources | Resource organization Security Governance |
| Management resources | Management and monitoring |
| Connectivity resources | Network topology and connectivity |
| Identity resources | Identity and access management |
Packaging these capabilities into a single Terraform module makes it easier to build and enforce consistency across the Azure platform when you're operating at scale.
These resources align with the Azure landing zones conceptual architecture:
You can deploy these resources, by capability, across multiple subscriptions by using the Provider Configuration on the module block.
The following sections outline the resource types and configuration options.
Core resources
The core capability of this module deploys the foundations of the conceptual architecture for Azure landing zones, with a focus on the central resource organization.
When you enable deployment of core resources (enabled by default), the module deploys and manages the following resource types:
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Management groups | Microsoft.Management/managementGroups |
azurerm_management_group |
| Management group subscriptions | Microsoft.Management/managementGroups/subscriptions |
azurerm_management_group |
| Policy assignments | Microsoft.Authorization/policyAssignments |
azurerm_management_group_policy_assignment |
| Policy definitions | Microsoft.Authorization/policyDefinitions |
azurerm_policy_definition |
| Policy set definitions | Microsoft.Authorization/policySetDefinitions |
azurerm_policy_set_definition |
| Role assignments | Microsoft.Authorization/roleAssignments |
azurerm_role_assignment |
| Role definitions | Microsoft.Authorization/roleDefinitions |
azurerm_role_definition |
The exact number of resources that the module creates depends on the module configuration. For a default configuration, you can expect the module to create approximately 180 resources.
Tip
None of these resources are deployed at the subscription scope, but Terraform still requires a subscription to establish an authenticated session with Azure. For more information on authenticating with Azure, see the Azure Provider: Authenticating to Azure documentation.
Management resources
The module provides an option to enable deployment of management and monitoring resources from the conceptual architecture for Azure landing zones into the specified subscription, as described on the Provider Configuration wiki page. The module also ensures that the specified subscription is placed in the right management group.
When you enable deployment of management resources, the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Log Analytics workspace | Microsoft.OperationalInsights/workspaces |
azurerm_log_analytics_workspace |
| Log Analytics solutions | Microsoft.OperationsManagement/solutions |
azurerm_log_analytics_solution |
| Automation account | Microsoft.Automation/automationAccounts |
azurerm_automation_account |
| Log Analytics linked service | Microsoft.OperationalInsights/workspaces /linkedServices |
azurerm_log_analytics_linked_service |
In addition to deploying the above resources, the module provides native integration into the corresponding policy assignments to ensure full policy compliance.
For more information about how to use this capability, see the Deploy Management Resources wiki page.
Connectivity resources
The module provides an option to enable deployment of network topology and connectivity resources from the conceptual architecture for Azure landing zones into the current subscription context. It also ensures that the specified subscription is placed in the right management group.
This capability enables deployment of multiple hub networks based on any combination of traditional Azure networking topology (hub and spoke), and Virtual WAN network topology (Microsoft-managed).
The module can also create and link DDoS Network Protection to Virtual Networks, and manage centralized public and private DNS zones.
Note
We don't currently recommend DDoS IP Protection in Azure Landing Zones and recommend using this option in specific circumstances. Review the product documentation About Azure DDoS Protection SKU Comparison
Traditional Azure networking topology (hub and spoke)
The module can optionally deploy one or more hub networks based on the traditional Azure networking topology (hub and spoke).
Note
The module currently configures only the networking hub and dependent resources for the connectivity subscription. Although there's an option to enable outbound virtual network peering from hub to spoke, users still need to initiate peering from spoke to hub. This is due to limitations in how the AzureRM provider targets a specific subscription for deployment.
When you deploy resources based on a traditional Azure networking topology (hub and spoke), the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Virtual networks | Microsoft.Network/virtualNetworks |
azurerm_virtual_network |
| Subnets | Microsoft.Network/virtualNetworks/subnets |
azurerm_subnet |
| Virtual network gateways | Microsoft.Network/virtualNetworkGateways |
azurerm_virtual_network_gateway |
| Azure firewalls | Microsoft.Network/azureFirewalls |
azurerm_firewall |
| Public IP addresses | Microsoft.Network/publicIPAddresses |
azurerm_public_ip |
| Virtual network peerings | Microsoft.Network/virtualNetworks/virtualNetworkPeerings |
azurerm_virtual_network_peering |
For more information about how to use this capability, see the Deploy Connectivity Resources wiki page.
Virtual WAN network topology (Microsoft-managed)
The module can optionally deploy one or more hub networks based on the Virtual WAN network topology (Microsoft-managed).
Note
Due to the different capabilities of Virtual WAN network resources over traditional, peering for Virtual WAN spokes is bi-directional when using this capability.
When you deploy resources based on a Virtual WAN network topology (Microsoft-managed), the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Virtual WANs | Microsoft.Network/virtualWans |
azurerm_virtual_wan |
| Virtual Hubs | Microsoft.Network/virtualHubs |
azurerm_virtual_hub |
| Express Route Gateways | Microsoft.Network/expressRouteGateways |
azurerm_express_route_gateway |
| VPN Gateways | Microsoft.Network/vpnGateways |
azurerm_vpn_gateway |
| Azure Firewalls | Microsoft.Network/azureFirewalls |
azurerm_firewall |
| Azure Firewall Policies | Microsoft.Network/firewallPolicies |
azurerm_firewall_policy |
| Virtual Hub Connections | Microsoft.Network/virtualHubs/hubVirtualNetworkConnections |
azurerm_virtual_hub_connection |
For more information about how to use this capability, see the Deploy Virtual WAN Resources wiki page.
DDoS Protection plan
The module can optionally deploy DDoS Network Protection, and link Virtual Networks to the plan if needed.
Note
Due to platform limitations, DDoS Protection plans can only be enabled for traditional virtual networks. Virtual Hub support is not currently available.
Important
The Azure landing zones guidance recommends enabling DDoS Network Protection to increase protection of your Azure platform. To prevent unexpected costs in non-production and MVP deployments, this capability is disabled in the Azure landing zones Terraform module due to the cost associated with this resource.
For production environments, we strongly recommend enabling this capability.
When you enable deployment of deployment of DDoS Protection plan resources, the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| DDoS Protection plans | Microsoft.Network/ddosProtectionPlans |
azurerm_network_ddos_protection_plan |
DNS
The module can optionally deploy Private DNS zones to support Private Endpoints and link them to hub and/or spoke Virtual Networks. User-specified public and private DNS zones can also be deployed and linked as needed.
When you enable deployment of deployment of DNS resources, the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| DNS Zones | Microsoft.Network/dnsZones |
azurerm_dns_zone |
| Private DNS Zones | Microsoft.Network/privateDnsZones |
azurerm_private_dns_zone |
| Private DNS Zone Virtual Network Link | Microsoft.Network/privatednszones/virtualnetworklinks |
azurerm_private_dns_zone_virtual_network_link |
Identity resources
The module provides an option to configure policies relating to the identity and access management landing zone. It also ensures that the specified subscription is placed in the right management group.
Note
This capability doesn't deploy any resources. If you want to update policy settings related to the identity management group, use the configure_identity_resources input variable.
For more information about how to use this capability, see the Deploy Identity Resources wiki page.
Getting started
Requirements for getting started with the module are documented on the Getting Started Wiki page.
To simplify getting started, the module has been published to the Terraform Registry. You can reference it directly within your code, as shown in the simple example later in this article. Running terraform init will automatically download the module and all dependencies.
You can view the latest module and provider dependencies on the Dependencies tab in the Terraform Registry.
Important
There are known issues with some Terraform and AzureRM provider version combinations. You can resolve some known issues by upgrading to the latest Terraform and AzureRM provider versions. Other known issues are transient errors that you can typically fix by rerunning your deployment.
We generally recommend pinning to specific versions, and testing thoroughly before upgrading.
We'll release new versions of the module when changes are needed. New releases will ensure compatibility with the latest Terraform and AzureRM provider versions. Please refer to our Module releases guidance for more information.
To get the latest features, ensure that the module version is set to the latest version. If you're upgrading to a later version of the module, run terraform init -upgrade.
Simple example
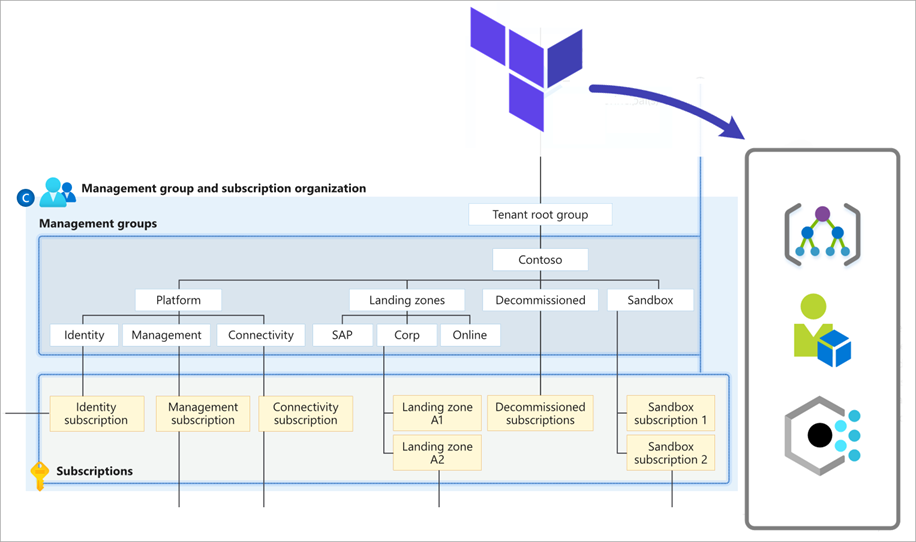
This example code deploys the minimum recommended management group and subscription organization from the enterprise-scale reference architecture. After you have this simple example up and running, you can start to customize your deployment.
Tip
Even though root_parent_id is the module's only mandatory variable, we also recommend setting root_id. Changing the root_id value will start a full redeployment of all resources that the module manages, including downstream dependencies.
The following code is a simple starting configuration for your main.tf root module:
# Configure Terraform to set the required AzureRM provider
# version and features{} block.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = ">= 2.77.0"
}
}
}
provider "azurerm" {
features {}
}
# Get the current client configuration from the AzureRM provider.
# This configuration is used to populate the root_parent_id variable with the
# current tenant ID used as the ID for the "Tenant Root Group"
# management group.
data "azurerm_client_config" "core" {}
# Use variables to customize the deployment
variable "root_id" {
type = string
default = "es"
}
variable "root_name" {
type = string
default = "Enterprise-Scale"
}
# Declare the Terraform Module for Cloud Adoption Framework
# Enterprise-scale and provide a base configuration.
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = ">= 1.0.0"
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = var.root_id
root_name = var.root_name
}
Next steps
The Terraform module for Cloud Adoption Framework Enterprise-scale provides an accelerated path to building out your enterprise-scale landing zones. It also provides the flexibility to expand and customize your deployment while maintaining a simplified approach to managing the configuration of each landing zone.
To find out more, review the module on the Terraform Registry and explore the module documentation on GitHub. In the documentation, you find more examples and tutorials about how to customize your deployment.
Learn how to deploy the Azure landing zones Terraform module through HashiCorp Learn. From there, you can also discover how some parts of the module work.