Prepare Active Directory for Azure Local, version 23H2 deployment
Applies to: Azure Local 2311.2 and later
This article describes how to prepare your Active Directory environment before you deploy Azure Local, version 23H2.
Active Directory requirements for Azure Local include:
- A dedicated Organization Unit (OU).
- Group policy inheritance that is blocked for the applicable Group Policy Object (GPO).
- A user account that has all rights to the OU in the Active Directory.
- Machines must not be joined to Active Directory before deployment.
Note
- You can use your existing process to meet the above requirements. The script used in this article is optional and is provided to simplify the preparation.
- When group policy inheritance is blocked at the OU level, GPOs with enforced option enabled aren't blocked. If applicable, ensure that these GPOs are blocked using other methods, for example using a Windows Management Instrumentation (WMI) Filter. Apply the WMI filter to any enforced GPOs, to exclude machine computer accounts for your Azure Local instances from applying the GPOs. Once the filter is applied, enforced GPOs won't apply, based on the logic defined in the WMI filter.
To manually assign the required permissions for Active Directory, create an OU, and block GPO inheritance, see Custom Active Directory configuration for your Azure Local, version 23H2.
Prerequisites
Complete the prerequisites for new deployments of Azure Local.
Install version 2402 of the 'AsHciADArtifactsPreCreationTool' module. Run the following command to install the module from PowerShell Gallery:
Install-Module AsHciADArtifactsPreCreationTool -Repository PSGallery -ForceNote
Make sure to uninstall any previous versions of the module before installing the new version.
You require permissions to create an OU. If you don't have permissions, contact your Active Directory administrator.
If you have a firewall between your Azure Local system and Active Directory, ensure that the proper firewall rules are configured. For specific guidance, see Firewall requirements for Active Directory Web Services and Active Directory Gateway Management Service. See also How to configure a firewall for Active Directory domains and trusts.
Active Directory preparation module
The New-HciAdObjectsPreCreation cmdlet of the AsHciADArtifactsPreCreationTool PowerShell module is used to prepare Active Directory for Azure Local deployments. Here are the required parameters associated with the cmdlet:
| Parameter | Description |
|---|---|
-AzureStackLCMUserCredential |
A new user object that is created with the appropriate permissions for deployment. This account is the same as the user account used by the Azure Local deployment. Make sure that only the username is provided. The name shouldn't include the domain name, for example, contoso\username.The password must conform to the length and complexity requirements. Use a password that is at least 12 characters long. The password must also contain three out of the four requirements: a lowercase character, an uppercase character, a numeral, and a special character. For more information, see password complexity requirements. The name can't be exactly the same as the local admin user. The name can use admin as the username. |
-AsHciOUName |
A new Organizational Unit (OU) to store all the objects for the Azure Local deployment. Existing group policies and inheritance are blocked in this OU to ensure there's no conflict of settings. The OU must be specified as the distinguished name (DN). For more information, see the format of Distinguished Names. |
Note
- The
-AsHciOUNamepath doesn't support the following special characters anywhere within the path:&,",',<,>. - After the deployment is complete, moving the computer objects to a different OU isn't supported.
Prepare Active Directory
When you prepare Active Directory, you create a dedicated Organizational Unit (OU) to place the Azure Local related objects such as deployment user.
To create a dedicated OU, follow these steps:
Sign in to a computer that is joined to your Active Directory domain.
Run PowerShell as administrator.
Run the following command to create the dedicated OU.
New-HciAdObjectsPreCreation -AzureStackLCMUserCredential (Get-Credential) -AsHciOUName "<OU name or distinguished name including the domain components>"When prompted, provide the username and password for the deployment.
- Make sure that only the username is provided. The name shouldn't include the domain name, for example,
contoso\username. Username must be between 1 to 64 characters and only contain letters, numbers, hyphens, and underscores and may not start with a hyphen or number. - Make sure that the password meets complexity and length requirements. Use a password that is at least 12 characters long and contains: a lowercase character, an uppercase character, a numeral, and a special character.
Here's a sample output from a successful completion of the script:
PS C:\work> $password = ConvertTo-SecureString '<password>' -AsPlainText -Force PS C:\work> $user = "ms309deployuser" PS C:\work> $credential = New-Object System.Management.Automation.PSCredential ($user, $password) PS C:\work> New-HciAdObjectsPreCreation -AzureStackLCMUserCredential $credential -AsHciOUName "OU=ms309,DC=PLab8,DC=nttest,DC=microsoft,DC=com" PS C:\work>- Make sure that only the username is provided. The name shouldn't include the domain name, for example,
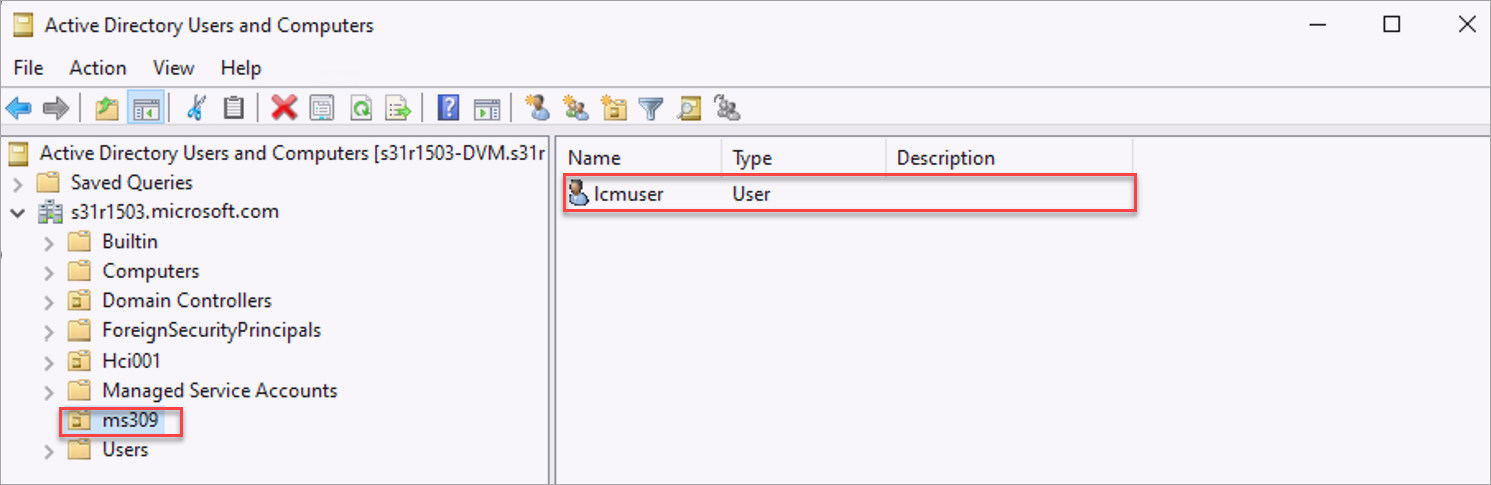
Verify that the OU is created. If using a Windows Server client, go to Server Manager > Tools > Active Directory Users and Computers.
An OU with the specified name is created. This OU contains the new LCM deployment user account.
Note
If you're repairing a single machine, don't delete the existing OU. If the machine volumes are encrypted, deleting the OU removes the BitLocker recovery keys.
Considerations for large scale deployments
The Lifecycle Manager (LCM) user account is utilized during Azure Local instance deployments that use Active Directory (AD), or for any add-node/repair operations for existing instances. The LCM user account is responsible for performing domain join actions, which necessitates the LCM user identity having delegated permissions to add computer accounts to the target Organizational Unit (OU) in the on-premises domain. During the deployment of Azure Local, the LCM user account is added to the local administrators' group of the physical machines.
To mitigate the risk of a compromised LCM user account credential, we advise that for each Azure Local instance, you have a dedicated LCM user account with a unique password.
We recommend that you follow these best practices for OU creation:
- For each Azure Local instance, create an individual OU within Active Directory. This approach helps manage computer account, CNO, LCM user account, and physical machine computer accounts within the scope of a single OU for each instance.
- When deploying multiple instances at-scale, for easier management:
- Create an OU under a single parent OU for each instance.
- Disable GPO inheritance at the parent OU level.
The preceding recommendations are automated, when you use the New-HciAdObjectsPreCreation cmdlet to Prepare Active Directory.
Next steps
- Download Azure Stack HCI OS, version 23H2 software on each machine in your system.