Understand privileged access management
Privileged Access Management (PAM) in Microsoft Purview helps organizations control access to sensitive data and critical configurations in Microsoft Exchange Online. Traditional administrative accounts often have standing permissions, increasing the risk of misuse or compromise. PAM mitigates these risks by introducing structured access controls:
- Zero standing access: Administrative permissions aren't permanently assigned. Users request access only when necessary.
- Just-in-time access: Temporary permissions are granted for specific tasks, limiting the window of exposure.
- Just-enough access: Access is scoped to the minimum permissions needed for the task at hand.
These controls ensure that administrative permissions are only granted when necessary and only for as long as required.
Why use privileged access management?
Standing administrative permissions increase the risk of data breaches and unauthorized changes. For example, if an administrative account is compromised, it could provide attackers with continuous access to sensitive data and systems.
PAM reduces these risks by:
- Ensuring that permissions are temporary and specific to the task.
- Requiring justification for access requests.
- Providing detailed records of access activities for audits and accountability.
By adopting PAM, organizations strengthen their security posture while maintaining operational efficiency.
How does privileged access management work?
PAM uses a structured process to manage administrative access securely. Here's how the workflow operates:
- Request access: A user submits a request for a specific administrative task, specifying the task type, scope, and duration. This ensures access is only requested when necessary and for a clearly defined purpose.
- Approval: Designated approvers review the request and decide whether to grant or deny access based on its necessity and scope. This step ensures permissions are thoughtfully reviewed before being granted.
- Perform the task: Once approved, the user completes the task within the granted time and scope. Permissions are automatically removed after the task is finished or the access expires, reducing the risk of unauthorized actions.
- Audit: All actions, including requests, approvals, and task executions, are logged for compliance and accountability. These records help identify any anomalies and support regulatory audits.
This process ensures that access is only granted when justified and always closely monitored.
Layers of protection
Privileged Access Management (PAM) complements other security features within the Microsoft 365 architecture to provide a layered defense against unauthorized access and data breaches. By incorporating PAM as part of an integrated security model, organizations can better protect sensitive data and critical configuration settings.
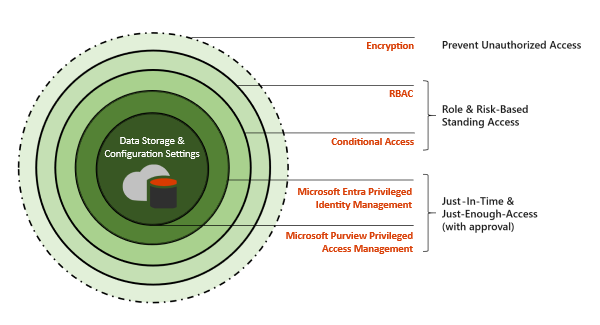
Layered security model
As shown in the diagram, the Microsoft 365 security architecture builds on multiple layers of protection:
- Encryption: Protects data at rest and in transit to prevent unauthorized access.
- Role-based access control (RBAC): Establishes standing access permissions based on roles to control user access.
- Conditional access: Enforces access policies based on factors such as user location, device state, and behavior patterns.
- Privileged identity and access management:
- Microsoft Entra Privileged Identity Management (PIM): Provides just-in-time, role-level access management, allowing users to execute multiple tasks within specific roles.
- Microsoft Purview Privileged Access Management: Focuses on task-specific access control, enforcing just-in-time and just-enough-access principles with approval workflows.
Integration with other security tools
PAM and Microsoft Entra PIM address different aspects of privileged access:
- PAM: Scopes access at the task level, ensuring granular control and approval for specific administrative actions in Microsoft 365.
- PIM: Scopes access at the role level, enabling just-in-time permissions for broader administrative functions across Active Directory roles and role groups.
Complementary use cases
- Using PAM alongside Microsoft Entra PIM: Adding PAM provides granular control over specific administrative tasks in Microsoft 365, enhancing protection and audit capabilities.
- Adding PIM to an existing PAM setup: PIM extends privileged access to systems and data outside Microsoft 365, offering broader coverage defined by roles or identity.
By combining PAM with tools like Microsoft Entra PIM, encryption, and RBAC, organizations can enforce a robust security posture while adhering to the principles of least privilege and just-in-time access.
Where does PAM fit into a security strategy?
PAM is one layer in a broader Microsoft 365 security strategy. It works alongside tools like:
- Encryption: Protects data at rest and in transit.
- Microsoft Entra Privileged Identity Management (PIM): Manages access at the role level, while PAM focuses on task-specific access.
These tools work together to:
- Strengthen defenses against unauthorized access.
- Provide detailed records to support compliance with security regulations.
- Simplify the enforcement of security principles, such as limiting access based on role or task.
Privileged Access Management (PAM) in Microsoft Purview is a critical tool for securing administrative access. By ensuring permissions are temporary, specific, and auditable, PAM helps organizations balance security and efficiency.