You get a Security Alert when you try to access an SSL enabled web site when certificate has been issued by an internal root CA...
Let's say you have your own internal Root Certificate Authority (CA) and you use it to grant server certificates to your Web sites.
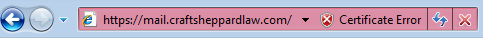
You are able to browse to your web site over SSL and can access the page. Things look good so far.
However you get an unwanted security alert all the time while accessing the page, stating the following:
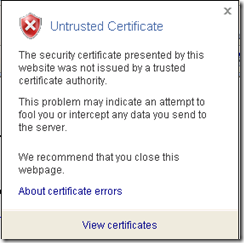
"The security certificate was issued by a company you have not chosen to trust.
View the certificate to determine whether you want to trust the certifying authority"
or,
"This certificate cannot be verified up to a trusted certification authority" in the Certificate ->General tab.
And if you have mobile access users they won't be able to access the page at all :-(, forget the Security alert.
Also if your Web site is Internet-facing, that means both internal as well as external users should be able to access the web site, then you will see a little different behavior.
What does it mean? Well, as the message description above clearly states we do not have information about the Root CA to verify whether it can be trusted for SSL transactions. Since you are using an internal Root CA for your Web site certificates, IE on the external client has no way to verify whether the root CA is trusted or not. IE has a list of default trusted root CA's.
If you check IE->Tools->Internet Options->Content->Certificates->Trusted Root Certification Authorities, you will see a list of all the public Root CA's that are trusted by IE client like VeriSign, Go Daddy, Thawte etc.
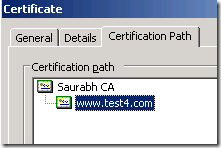
From an external IE (here assuming IE7) client, If you go to the Certificate Error->View certificates->"Certification Path" as in the above screenshot you should only see the Web site certificate listed.
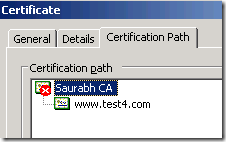
If you check the above from an intranet client you will see an hierarchy showing both the Root CA and the Web site certificates.
Resolution:
Why the above difference?
Since Intranet client has access to the Internal Root CA they (IE) see the hierarchy of Root CA and the Web site certificate in the Certificate->"Certification Path",
You will be able to see both the root CA and the Web site certificate as above.
But since root CA is not accessible for the Internet users they will only see the Web site certificate and not the Root CA certificate in the tree in the "Certification Path". Root CA will be absent altogether in the tree. Or else you will see an entry for the root CA but with a RED X meaning that CA Root certificate is not trusted as it is not in the Trusted Root Certification Authorities store on the client.
You get "This certificate cannot be verified up to a trusted certification authority" when the Certificate Authority is not running or is not visible to the client (IE). This generally happens when client cannot access CA for e.g. running your internal CA and users accessing the web site over Internet.
We will have to install the root CA certificate on to the client computer in order to get rid of the security alert.
For intranet users downloading and installing the .cer of the Root CA into the Trusted Root Certification Authority MAY resolve the issue.
Else, here are the steps to successfully install the root certificate authority on to the client's trusted CA store:
- On the IIS or Certificate Server, open MMC (Start->Run and type MMC) and add the Certificates snap-in using the Computer Account.
-- Expand Certificates
-- Expand Trusted Root Certification Authority.
-- Right click on the correct Root Certification Authority -> Click Export, which opens the wizard. Choose the following in the wizard:
a) Check "Cryptographic Message Syntax Standard - PKCS #7 Certificates (.P7B)"
b) Check "Include all certificates in the certification path if possible" --> click Next
c) Give it a relevant file name (in our case, say RootCAFileName) and choose the location --> Click Next
d) Click Finish
This will create RootCAFileName.p7b.
-- Copy RootCAFileName.p7b to the client.
-- It can be installed on the client machine in two ways:By Right click on the RootCAFileName.p7b file or by using IE via Import.
a)
- Right-click on RootCAFileName.p7b -> Click "Install Certificate" -> Next
- Click "Place all certificates in the following store" -> Browse
- Select "Trusted Root Certification Authorities" -> Ok -> Next- Click Finish
b)- Open IE -> Tools menu -> Internet Options
- Go to the Content tab -> Click Certificates
- Go to the "Trusted Root Certification Authorities" tab -> Click Import
- Follow steps in the wizard to browse to the RootCAFileName.p7b file and place it in "Trusted Root Certification Authorities" -> Next
- Finish
Hope this helps...
Comments
Anonymous
November 07, 2007
Let's say you have your own internal Root Certificate Authority (CA) and you use it to grant serverAnonymous
March 16, 2008
Hello Saurabh Good to listen to you. Anyway to make the CA visible to Internet user, so that all of them can click in the CA certificate to install. It is not an option to install CA certificate into every client in my environment.Anonymous
March 16, 2008
Hi Yap Sok Chuan, If your clients are external users this as you may know is an expected behavior. CA will not be visible to your internet users. My best bet would be to have Certificates from a known vendor such that your client's browser recognizes it. Or else you may want to provide a default page in your wesbite such that a user can download and install the cert themselves the first time. Let me know if this helps or if you have any further question. ~SaurabhAnonymous
March 03, 2009
hi this is great tutorial on security.thanks alotAnonymous
June 15, 2009
The comment has been removedAnonymous
July 08, 2009
The comment has been removedAnonymous
July 08, 2009
Sunil, yes you can send the file to the clients via email. That should work.Anonymous
April 01, 2011
I have a similar kind of a situation.
- IIS Server/Web Server is in X Domain
- Users in Y Domain who open the SSL page to login to Citrix Console.
- SSL cert is issued from a IIS/Web Server
- Users can access the Web Server through IP and not hostname.
- When Users try to access the SSL page, they can't see anything
- When try to access with IP, they see the cert error page.
- Root Cert is missing in the Certification Path. What I did to resolve this on the client:
- Added the entry in host file.
- Manualy imported the Root Cert in the "Trusted Root Certification Authority" What I want is:
- I have multiple clients.
- I don't want to use Group Policy to push the Root Cert.
- I want an exe file which can install the Root Cert on the Client.
- I have a .bat file to update the host entry echo <IP Address> <Hostname/FQDN>>>c:WindowsSystem32driversetchosts
- It'll be great if someone can assist me with a script.
Anonymous
August 03, 2012
Thanks Man, Much Help!Anonymous
October 09, 2013
How do I get Thawte off my computer?Anonymous
January 15, 2014
The comment has been removedAnonymous
October 07, 2014
Please assist! Real Time Protection has been compromised. I require your immediate assistance please.Anonymous
February 14, 2017
The comment has been removedAnonymous
March 25, 2017
Wow! This could be one particular of the most beneficial blogs We've ever arrive across on this subject. Actually Wonderful. I'm also an expert in this topic therefore I can understand your effort.