The well-known SID -1000
It is not every day that you discover a new well-known SID, but today I got mine. I know... if I just discovered a well-known SID it can hardly be well-known, can it? Let me explain. If you have been around the (Windows) block a few times, you will know what a SID is: a security identifier owned by security principals such as users, computers and groups. It is the thing that gets left behind on permissions when the principal is deleted. If you need to read up on SIDs and RIDs, check this.
Some SIDs are reserved for particular objects and have the same value or at least the same RID in every forest or domain. These are called the well-known SIDs. A fairly up-to-date list is here. Just to remind you what this looks like, here are a few well-known examples of well-known SIDs:
| SID | Principal |
|---|---|
| S-1-5-11 | Authenticated Users |
| S-1-5-21-{domainSID}-500 | Administrator |
| S-1-5-21-{domainSID}-512 | Domain Admins |
In this table, the domainSID part is something like this "155359765-898420586-2118829354", and is unique for every domain. The number that follows it is a RID, and illustrates why renaming an account does not really hide it. For instance, to find the original, built-in administrator account of a domain you get the domain SID, append the "-500" RID and find the account with that SID.
So last week I was at a customer looking at a local policy, when I was looking at a very strange looking SID in a user right. You don't usually see a SID here, unless the corresponding security principal no longer exists. So whatever the object it represented, it was gone. This was the SID:
- S-1-5-21-155359765-898420586-2118829354-1000
The RID is exactly 1000, which is much higher than the usual well-known domain RIDs (which hover around 500), but also much lower than the RIDs of the usual users and groups. It strongly suggests something special. Any idea? Read on to find out.
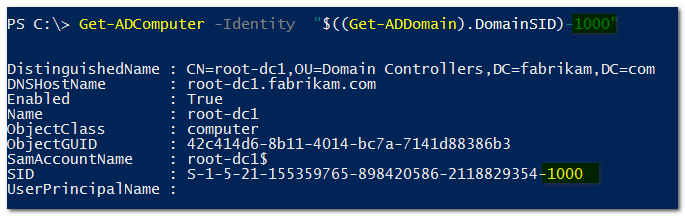
I went back to my lab, and typed a quick powershell command to find the object with RID 1000.:
And there you go: it's a domain controller. Specifically, the first created domain controller of the domain, which of course gets the first RID from the newly created RID pool: 1000. This must always be true, so -1000 is really a well-known RID.
Update 5/27/2018: my colleague Pierre Audonnet pointed out that this observation is no longer true if you create a user or group before you create the domain. The first such object would get the RID -1000... and of course he is right. Thanks Pierre!
Comments
- Anonymous
December 05, 2018
Willem, if you have a moment, could you please review and answer my forum query at: https://answers.microsoft.com/en-us/windows/forum/windows_7-security-winsec/should-i-be-concerned-about-sqmuploads-1-5-21/c8da0529-bab6-4e1e-ae14-23d4ae58c7be?tm=1544074549282. No need to spend much time on it, if you can't answer it easily. I assume from your article above that my -1000 is similar to your -1000 and thus harmless? I have limited skill in PowerShell but I tried to find out what I could (I couldn't get any of the commands you listed above to work for me, even after accessing the help function). I don't know if it helps but this is what I found:PS C:> Get-ItemProperty C:\Windows\system32\tasks\WPD\SqmUpload_S-1-5-21-2585291226-2271656789-3205841708-1000Thank you,Aurora- Anonymous
December 05, 2018
Hi, this is related but different. Your -1000 represents a user account. I have no clue what that file is or why it is uploaded, although a quick search reveals that it has to do with "Customer Experience Improvement Program (CEIP)"
- Anonymous