Service Principal Name (SPN) checklist for Kerberos authentication with IIS 7.0/7.5
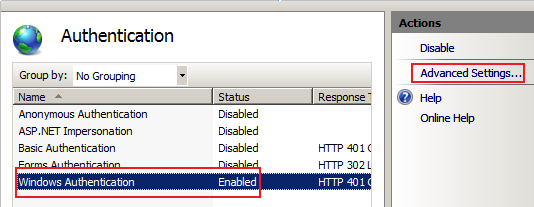
This post is more about the confusion that may arise around SPNs for setting up Kerberos authentication in IIS 7.0. IIS 7.0 has a new Kernel-mode authentication feature using which the ticket for the requested service is decrypted using Machine account (Local system) of the IIS server. It no longer depends upon the application pool Identity for this purpose by default and in turn improves the performance.
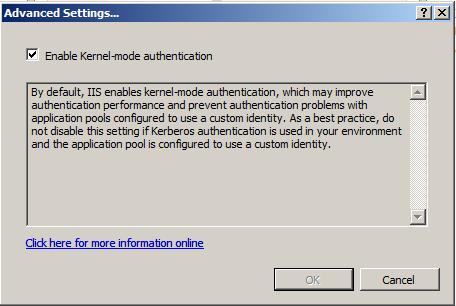
Here is how it looks like.
So what does this mean?
You no longer need to worry about the correlation between HTTP SPNs and the Application pool Identity that was required in the earlier version i.e. IIS 6.0. But that's not blindly true. There has been some confusion whether we don't have to care at all about SPNs or may have to depending upon the settings. Here is a checklist to give more clarity for different scenarios that you may fall under:
SCENARIO 1a
| IIS 7.0 Web Site/Application | |
| Authentication | Integrated Windows authentication |
| Application Pool Identity | NETWORK SERVICE |
| Kernel-Mode authentication | Enabled (<attribute name="useKernelMode" type="bool" defaultValue="true" /> in the ApplicationHost.config file) |
| Site URL | Accessed with the NetBIOS name, like https:// <myIISserver-NetBIOS-name> /Default.aspx |
SPNs will be required ONLY for the IIS machine account:
| HOST/<myIISserver-NetBIOS-name> |
| HOST/<myIISserver-NetBIOS-name.fully-qualified-domainname> for e.g. HOST/myIISserver.mydomain.com |
***Note: By default HOST/<myIISserver-NetBIOS-name> and HOST/<myIISserver-NetBIOS-name.fully-qualified-name> is already added for the machine account when a machine is added to a domain and HTTP forms a part of HOST. So you may not have to do anything special here for SPNs. Everything should be set by default.
You can check the set of existing SPNs for the machine account by running the following command:
> Setspn.exe -L <myIISserver-NetBIOS-name> or directly using a Snap-in like Adsiedit.msc.
SCENARIO 1b
| IIS 7.0 Web Site/Application | |
| Authentication | Integrated Windows authentication |
| Application Pool Identity | Custom account for e.g. Domain1\Username1 |
| Kernel-Mode authentication | Enabled (<attribute name="useKernelMode" type="bool" defaultValue="true" /> in the ApplicationHost.config file) |
| Site URL | Accessed with the NetBIOS name, like https:// <myIISserver-NetBIOS-name> /Default.aspx |
The SPN requirements remain the same as above. You don't have to add SPNs like http/ <myIISserver-NetBIOS-name> for the Domain1\Username1 unlike in IIS 6.0 (where we had to add an SPN of the form http/<myIISserver-NetBIOS-name> for the Application Pool identity).
SPNs will be required ONLY for the IIS machine account:
| HOST/<myIISserver-NetBIOS-name> |
| HOST/<myIISserver-NetBIOS-name.fully-qualified-domainname> for e.g. HOST/myIISserver.mydomain.com |
***Note: By default HOST/<myIISserver-NetBIOS-name> and HOST/<myIISserver-NetBIOS-name.fully-qualified-name> is already added for the machine account when a machine is added to a domain and HTTP forms a part of HOST. So you may not have to do anything special here for SPNs. Everything should be set by default.
You can check the set of existing SPNs for the machine account by running the following command:
> Setspn.exe -L <myIISserver-NetBIOS-name> or directly using Snap-in like Adsiedit.msc.
SCENARIO 2a
| IIS 7.0 Web Site/Application | |
| Authentication | Integrated Windows authentication |
| Application Pool Identity | NETWORK SERVICE |
| Kernel-Mode authentication | Enabled (<attribute name="useKernelMode" type="bool" defaultValue="true" /> in the ApplicationHost.config file) |
| Site URL | Accessed with a Custom Host name, like https://www.mysite.com |
SPNs will be required ONLY for the IIS machine account in the following format:
| HTTP/ <site-custom-name> for e.g. HTTP/www.mysite.com |
You can add an SPN using Setspn.exe like
> Setspn -a http/ <site-custom-name> <myIISserver-NetBIOS-name>
where <myIISserver-NetBIOS-name> is the IIS machine account and <site-custom-name> is the custom host/host header name for the Web Site URL.
e.g. > Setspn -a http/www.mysite.com <myIISserver-NetBIOS-name>
*The command is NOT case sensitive
You can check the existing set of SPNs for the machine account by running the following command:
> Setspn.exe -L <myIISserver-NetBIOS-name>
SCENARIO 2b
| IIS 7.0 Web Site/Application | |
| Authentication | Integrated Windows authentication |
| Application Pool Identity | Custom account for e.g. Domain1\Username1 |
| Kernel-Mode authentication | Enabled (<attribute name="useKernelMode" type="bool" defaultValue="true" /> in the ApplicationHost.config file) |
| Site URL | Accessed with a Custom host/Host header name, like https://www.mysite.com |
SPNs will be required ONLY for the IIS machine account and NOT for Domain1\Username1 account unlike in IIS 6.0.
| HTTP/ <site-custom-name> for e.g. HTTP/www.mysite.com |
You can add an SPN using Setspn.exe like
> Setspn -a http/<site-custom-name> <myIISserver-NetBIOS-name> where <myIISserver-NetBIOS-name> is the IIS machine account and <site-custom-name> is the custom host/host header name for the Web Site URL.
e.g. > Setspn -a http/www.mysite.com <myIISserver-NetBIOS-name>
*The command is NOT case sensitive
You can check the existing set of SPNs for the machine account by running the following command:
> Setspn.exe -L <myIISserver-NetBIOS-name>
Special case of running IIS 7.0 in a WEB FARM
If you are running IIS 7.0 server in a Web farm the KDC will not know in advance which individual server the request may go to and hence ticket decryption may fail. Hence in such a scenario instead of registering SPNs under a specific machine account use a domain account. I am not a SharePoint guy but based on what I have read on the Web this scenario is also applicable to a single SharePoint server configuration.
There are two ways to go:
Either
Disable Kernel mode authentication and follow the general steps for Kerberos as in the previous IIS 6.0 version. Refer this.
Or,
[Recommended for Performance reasons]
Let Kernel mode authentication be enabled and the Application pool's identity be used for Kerberos ticket decryption. The only thing you need to do here is:
1. Run the Application pool under a common custom domain account.
2. Add this attribute "useAppPoolCredentials" in the ApplicationHost.config file.
<system.webServer>
<security>
<authentication>
<windowsAuthentication enabled="true" useKernelMode="true" useAppPoolCredentials="true" />
</authentication>
</security>
</system.webServer>
Remember there is no GUI setting for this. You need to modify the ApplicationHost.config file from
<%SystemDrive%>/Windows/System32/inetsrv/config folder on the IIS 7.0 machine.
3. Add the SPNs in the form:
http/<virtualhost-name> and
http/<virtualhost-name.fully-qualified-name> for the Application Pool Identity.
Ensure that we don't have such an entry for SPNs for any other account including IIS server machine account.
*If we have the same SPN mapped to multiple accounts (be it a machine or an user account) it leads to Duplicate SPNs and will break Kerberos.
Hope this helps!
Cross Posted from here
Comments
Anonymous
March 06, 2009
PingBack from http://www.qsupport.org/windows-vista-enterprise-64-bit-edition-fix-you-receive-a-stop-0x0000007e-error-message-on-a-blue-screen-when-the-apppoolcredentials-attribute-is-set-to-true-and-you-use-a-domain-account-as-the-appl/Anonymous
March 17, 2009
There has been a known issue around Server going into a blue screen (OS crash) when you have Windows Authentication and Kernel Mode authentication enabled plus you have the useAppPoolCredentials attribute set to true in the authentication section in the Applicationhost.config file. *Ensure that you apply the following hotfix to the IIS 7.0 Server. http://support.microsoft.com/kb/962943Anonymous
June 24, 2009
The comment has been removedAnonymous
February 22, 2010
Excellent post! Got a little bit confused about the SPN:s when running IIS 7.5Anonymous
March 23, 2010
Wonderful Post. Cleared lot of confusion. There are very less article on spn and IIS 7. This was most useful.Anonymous
April 05, 2010
hello, how about IIS 7.5. The change in the config-File does not work. There are some entries to windowsauthentication. The only thing which is working: Disable in IIS the kernel mode authentication.Anonymous
April 07, 2010
I didn't have luck with this useAppPoolCredentials="true" on IIS 7.5 either. Is there something special required for R2 or are we just missing something?Anonymous
April 07, 2010
Not that I remember that there should be any difference. I will get back with an update by tomorrow if there is something speical with IIS 7.5.Anonymous
April 08, 2010
Okay just an update, the above post regarding SPNs is no different in between IIS 7 and IIS 7.5. I feel you are geting into a different issues with regard to Kerberos in general. Ensure all other configuration settings with regard to Kerberos is well configured.Anonymous
April 12, 2010
I am sorry, that does not work, especially with CRM 4.0. IE 8.0/CRM works if deacitivaed kernel mode authenication BUT Outlook-Plugin/CRM cannot be installed. If no NLB, only single hosts, with apporpriate SPNs, it does not work IE/CRM 4.0 if kernel mode is activated. I have a BIG problem. With IIS 6.0 CRM 4.0, NLB, SPNs, etc it had worked.Anonymous
June 09, 2010
This post is very helpful. ThanksAnonymous
September 10, 2010
I followed IIS 7.5 in a Web Farm and could not get Kerberos to work until I added provider Negotiate in Authentication section under IIS for the SharePoint website.Anonymous
September 10, 2010
I followed the IIS 7.0 in a Web Farm section (My environment IIS 7.5) and could not get Kerberos to work until I added provider Negotiate in Authentication section under IIS for the SharePoint website.Anonymous
September 10, 2010
Negotiate and NTLM are added by default at the server level. I wonder why you had to manually add it at your site level. It could have been because of someone removing it from global level or sharepoint clearing out all the entries and adding just NTLM to be the only provider.Anonymous
September 28, 2010
Very useful, we have this working in a mixed 2003/2008 environment and this post was just the information we needed to fill in the gaps and get it working.Anonymous
February 03, 2011
There's a white paper published on Microsoft Downloads (Configuring Kerberos Authentication for Microsoft SharePoint 2010 Products) that states: !Verify Kernel Mode Authentication is disabled Kernel mode authentication is not supported in SharePoint Server 2010. By default all SharePoint Web Applications should have Kernel Mode Authentication disabled by default on their corresponding IIS web sites. Even in situations where the web application was configured on an existing IIS web site, SharePoint will disable kernel mode authentication as it provisions a new web application on the existing IIS site." but this post say's to ehable it?Anonymous
April 18, 2011
Since the SPN is now registered with the machine account, you may want to mention that the machine account need be marked as "Trust this computer for delegation to any service (Kerberos only)" or "Trus this computer to delegation to specified services only". I bet it will fix many people's problems here.Anonymous
May 20, 2011
What does it mean...
Add the SPNs in the form: http/<virtualhost-name> and http/<virtualhost-name.fully-qualified-name> for the Application Pool Identity.
Where is this supposed to be added? In the ApplicationHost.config file ? If yes then where in that file? thanks.
Anonymous
August 23, 2011
@Roy Davis Where is this supposed to be added? You don't add those lines to a file. It is simply showing you the syntax when issuing the command setspn,exe . Example: setspn.exe http/<virtualhost-name> setspn.exe http/<virtualhost-name.fully-qualified-name>Anonymous
September 02, 2011
@Shaun @Roy Davis This means that you need to had following SPNs on the service account eg: Domain/Username on which Application Pool is running. setspn.exe http/<virtualhost-name> setspn.exe http/<virtualhost-name.fully-qualified-name>Anonymous
September 02, 2011
@Shaun Use asked this question:- In the ApplicationHost.config file ? If yes then where in that file? You can find this file in following location:- Start -> Run -> %windir%system32inetsrvconfig I hope that will help...Anonymous
September 06, 2011
The article below shows the easy way to set up the ApplicationHost.config file: blogs.technet.com/.../useapppoolcredentials-true-with-kerberos-delegation-on-2008.aspxAnonymous
December 07, 2011
Updating to the UseAppPoolCredentials can also be scripted out using the appcmd.exe program as per the steps in this article, technet.microsoft.com/.../dd759186.aspx, i.e. "Set the IIS useAppPoolCredentials value to True
Open an elevated command prompt window. To open an elevated Command Prompt window, click Start, point to All Programs, click Accessories, right-click Command Prompt, and then click Run as administrator. 2. Navigate to %windir%system32inetsrv. 3. Type appcmd.exe set config -section:system.webServer/security/authentication/windowsAuthentication -useAppPoolCredentials:true. "
Anonymous
January 02, 2012
We have an installation with a F5 hardware load balancer that also offloads SSL from two CRM 2011 servers on IIS 7.5 with kernel Mode Authentication enabled. SPN's for the CRM Service Account have been set on the SSL host header and the F5 machine name. All seems to work but one URL which is an ODATA REST endpoint. Traces show evidence of failing Kerberos delegation but we're stuck here.Anonymous
May 14, 2012
Using CRM with NTLM authentication and Kernel mode authentication. Seems when users accounts expire then they can no longer login. Seems it cannot pass through a password change or expirey. Affects Internally or external via ISA. Help on this would be awsomeAnonymous
May 21, 2012
Great article. We had spn's set against the app pool account and this was breaking the app. I removed the SPN's after reading the above and this fixed it. Thanks again!.Anonymous
October 30, 2012
you save my life))) Thank you!