Security – One of the Key Reasons to Migrate to Windows Vista (part 2)
In my last post, I briefly touched on different features of Windows Vista, which I think are important with regards to the view on Windows XP vs. Windows Vista. Let’s take a different approach now: I recently was on a panel in Eastern Europe where I was asked, which model generates more secure software: The shared source (like ours) or the Open Source. I asked back, whether they could define “more secure” for me. It turned out, that we were talking about vulnerabilities.
Let’s look at some statistics now and let’s start with vulnerabilities:
In Jeff Jones’ Desktop OS Vulnerability Report we published figures on vulnerabilities between Desktop OS Vendors and it turns out that this view already gives you a reason to migrate to Windows Vista:

But this is the view on an industry problem giving us confidence that our Security Development Lifecycle works. But how is the comparison between Widows XP and Windows Vista? He has a really interesting chart in there:
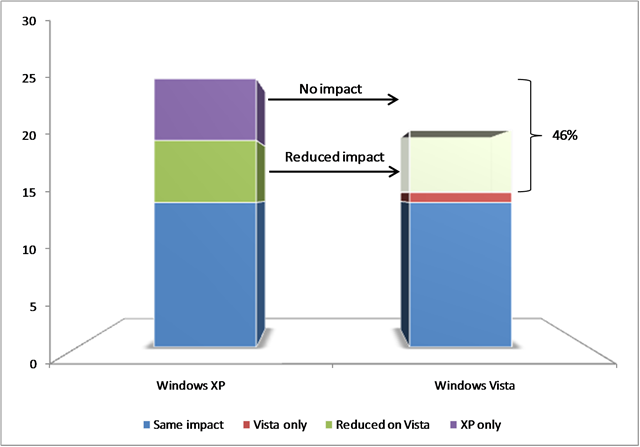
If we compare Windows XP and Windows Vista, we see different things:
- There are vulnerabilities we had to address in Windows XP which were not in Windows Vista anymore.
- There are vulnerabilities which had less impact on Windows Vista compared to Windows XP. A good example for this was the latest Out of Band Security Update we had to release, called MS08-067, which was Critical for all the OSs except Windows Vista and Windows Server 2008, where we rated it Important. The reason for that is UAC – even if you would have switched off the UI!
- Finally, there was one vulnerability which was introduced in new code in Windows Vista.
So, this picture shows very well that defense in depth in Windows Vista (with technologies like ASLR, DEP, UAC etc.) actually pays off.
An other view on this is the attack/malware side. In our Security Intelligence Report v5 we talk about browser-based exploits and where the criminals attack the victims on Windows XP and Windows Vista. If you look at the XP picture you see the following:

With regards to browser-based exploits, 58% of the time, Microsoft software was attacked and 42% 3rd party. This changes drastically in Windows Vista:

Here our software drops to 6%!
In the Security Intelligence Report we have some other figures as well (like the malware infection rate on the different OS) but I want to leave it with that.
We once discussed in our community an interesting question: If we could give our customers just one advice, what would that be? I think it would be to stay on the latest versions of all your software. The reason is not license fees or anything like that. The reason is that this is the only way to cope with the changing threat landscape!
Roger
Comments
Anonymous
January 01, 2003
My impression was that Vista faired better then XP with respect to the MS08-067 bug mostly because of the DEP/ASLR combination. I'm not sure UAC really figures into it. I went into this in more detail in this blog: http://blogs.pcmag.com/securitywatch/2008/11/why_vista_looks_good_after_the.phpAnonymous
January 01, 2003
The comment has been removedAnonymous
January 01, 2003
I hadn't really thought much about UAC with respect to this vuln. As Mark Russinovich says, it's not a security barrier. If the user clicks Continiue then it hasn't done anything. As I say in my own blog, DEP is a barrier here, but there are ways around DEP. But those ways around DEP themselves run into ASLR. There are ways around ASLR but they are long shots. Nobody is probably going to go to the trouble of building an exploit that might, in rare circumstances, exploit a Vista system by getting through DEP and ASLR, even if it may work a small percentage of the time. The defense-in-depth in Vista, as you say, is formidable. Your odds of getting through with social engineering are much better than a technical exploit of even a serious bug like this.