Updating GPO Monitoring in Security Monitoring for MSFT AGPM
Disclaimer: Due to changes in the MSFT corporate blogging policy, I’m moving all of my content to the following location. Please reference all future content from that location. Thanks.
This is something that was brought to my attention in regards to my security monitoring MP in regards to GPO modifications. Microsoft has a product called AGPM which allows administrators to control GPO modifications via an AGPM server. My understanding is that GPOs can still be modified by domain admins, but that (if setup right), one can exclude alerting from the AGPM service account so as to alert when GPOs are modified outside of APGM. There are a few things worth noting for this assumption to be valid:
- The service account cannot be used elsewhere. If this is logged on to another machine, anywhere in the environment, it is at risk to credential theft.
- Accounts that need to access the AGPM server must also be tightly controlled. This would be, in my opinion at least, a Tier 0 account. This means that only domain admins can access this service, and if these accounts access anything other than Tier 0 systems (which means you must have good account tiers in place, or else you are at risk for credential theft), you are again at risk for credential theft.
I cannot emphasize these points enough. If this is something you are interested in setting up correctly, consider engaging a security expert in this endeavor.
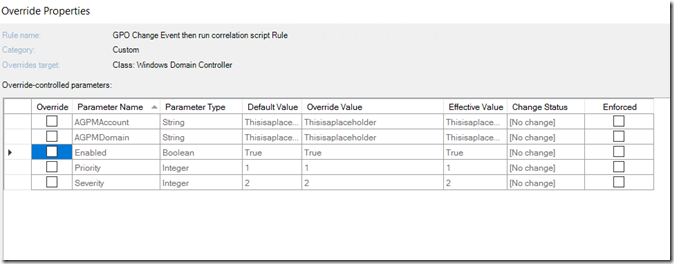
If this is done right, my changes to the original data source are fairly easy to implement. As it stands, GPO modifications are recorded in event ID 5136. As you can see, the service account generating the event is recorded. This is a parameter in the event log, and as such, I’ve updated the data source to allow for an overrideable parameter for both the AGPM Account and AGPM Domain. Currently, it is set to check if said parameter does not equal the value “thisisaplaceholder”. This means that any account will flag by default, but you can override by the service account making the change. Only one service account can be overridden, so this only works if you have AGPM setup. I highly recommend that said override also have the enforced check box selected.
I’ve added re-written the GPO Creation and Deletion rules with the same ability to be overridden, as AGPM can create and delete GPOs as a part of the tool. This should drastically reduce noise for customers using AGPM and generate alerts only when GPOs are modified outside of AGPM.
It is worth noting that these override values must exactly match that of what is in the event description, or else the override will not work. The rules in place do show the entire event description, so there’s no need to look up the individual events.