Securing remote connections
Consider the following scenario: a standard user was tricked to run a malicious code and his device was compromised. Typically, standard users do not have high privileges, so the next thing for the attackers is getting their hands on privileged accounts. How? They can delete an important file required by Office or by slowing down the operating system. Eventually, the user will contact the helpdesk and to troubleshoot the issue they will need to login with privileged accounts.
But if the end-user device is compromised, the attacker can harvest these precious credentials and use them to attack additional resources in the network.
Why the credentials are available on the remote host? By default, Remote Desktop is using Remote Interactive process to authenticate: the user’s credentials are sent (over a secure channel) to the remote device and if the login successful then the user can access the remote desktop.
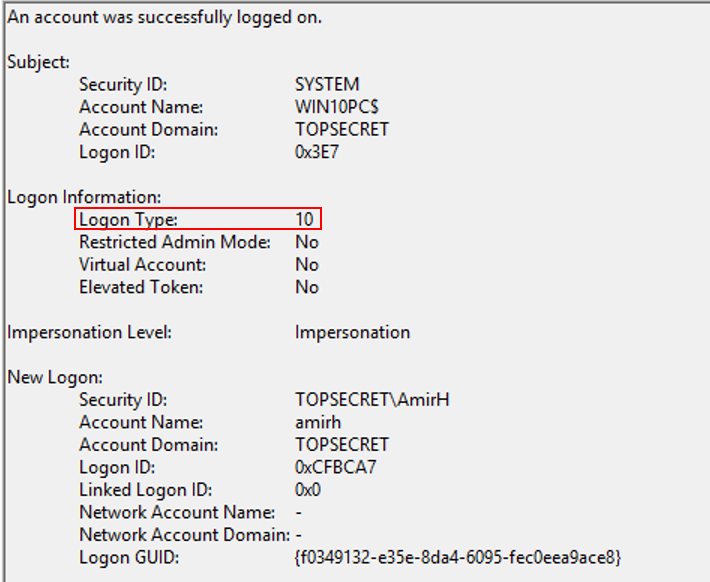
A view from the security event log (Type 10 means Remote Interactive logon) after remote desktop login
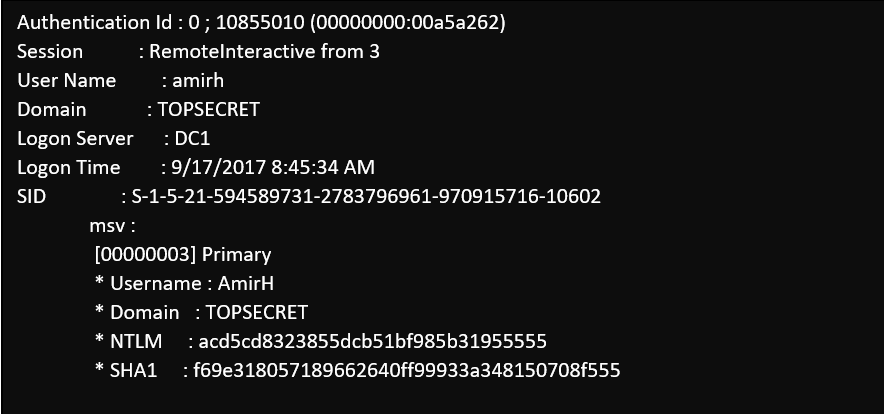
A view from common hacking tool running on the target device after the user was successfully authenticated
As we can see, now the attacker can obtain the privileged user credentials (NTLM hash or Kerberos tickets) from memory, and start moving laterally inside the network. Furthermore, rebooting the target device after use is the only way to ensure that credentials from stale or leaked logon sessions are removed completely from memory.
Restricted admin mode
Microsoft introduced restricted admin mode to address this issue in Windows 2012 R2 (and it was back-ported to any supported operating system later).
Using restricted admin mode, RDP is using a network logon process, instead of remote interactive. Using network logon ensures that the user’s credentials are never sent to the target device, therefore they are not available for theft.
To use restricted admin mode the remote target need to support it (see below), and you need to use the following command line:
mstsc /v:<server name> /restirctedAdmin
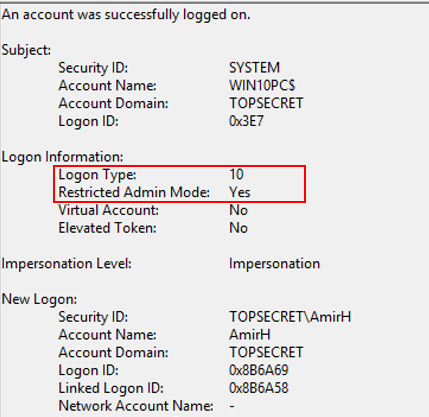
A view from the security event log after using restirctedAdmin switch:
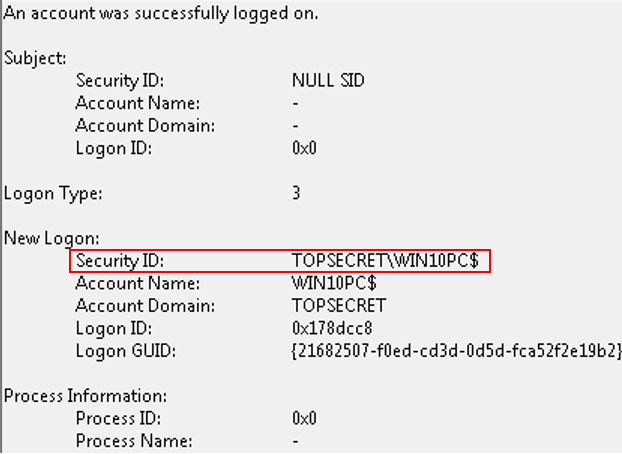
And now for something interesting, running the same hacking tool on the system reveals that the user token is there, but it’s populated with the target device computer account details!
When we are trying to access other network resources while connected to the remote session we can see “access denied” errors, and that’s because we are authenticating (and try to access resources) using the computer account, not the user account.
Restricted admin is disabled by default, and you need to explicitly add the switch /restrictedAdmin to mstsc command line, and enable it on the target device (see Step-By-Step: Enabling Restricted Admin Mode for Remote Desktop Connections).
Windows Defender Remote Credential Guard
Remote Credential Guard enables you to protect your privileged credentials and access network resources from within the remote session.
To use the remote Credential Guard mode the remote target need to support it (see below), and you need to use the following command line:
mstsc /v:<server name> /remoteguard
A view from common hacking tool running on the target device after the user was successfully authenticated using Remote Credential Guard
As we can see the NTLM hashes are encrypted and not reusable.
Comparison between Remote Desktop security modes
| Connection option | Minimum version | Reusable NTLM credentials | Multi-hop |
| Remote Desktop | Any supported version of Windows | Yes | Yes |
| Remote Desktop with RestictedAdmin | Any supported version of Windows | No | No |
| Remote Desktop with RemoteGuard | Windows 10 (version 1607) | No | Yes |
Group Policy
Using Group Policy you can require that all outbound Remote Desktop requests will use RestrictedAdmin mode.
The setting is under Computer Configuration\Policies\Administrative Templates\System\Credentials Delegation
Further reading and resources:
- /en-us/windows/access-protection/remote-credential-guard
- https://blogs.technet.microsoft.com/johnromsft/2016/06/14/why-you-should-use-rdp-restrictedadmin/
Comments
- Anonymous
September 21, 2017
Feels like the final of the post was rushed - where is Mimikatz screenshot for Remote Credential Guard?- Anonymous
September 22, 2017
Updated
- Anonymous
- Anonymous
September 22, 2017
The comment has been removed- Anonymous
September 22, 2017
Sure you need administrative privileges for accessing the credentials, the correct term should be standard domain user.
- Anonymous
- Anonymous
September 28, 2017
Thanks! - Anonymous
October 14, 2017
Great info, thanks. I realize this article refers to mstsc.exe, but now that the modern Remote Desktop client supports .rdp files could you suggest a place to find supported vs ignored .rdp file settings, or a roadmap for support?