Chasing Adversaries with Autoruns - evading techniques and countermeasures
Abstract
Sysinternals Autoruns is a great utility for defenders to discover and disable malware and adversaries' persistence points. There are similar programs, but as the author of Autoruns says: "(Autoruns) has the most comprehensive knowledge of auto-starting locations ", therefore the focus here is on Autoruns.
In the last weeks couple of security researches (Kyle - @KyleHanslovan, Chris - @ChrisBisnett HASHEREZADE @hasherezade) have discovered that it's possible to evade from autoruns when using it with a default configuration. Always remember that determined attackers will work actively on hiding their activities within your network.
To better understand these techniques, we can use two categories "Direct manipulation" and "Indirect manipulation".
Direct manipulation
Put simply, an attacker will try to enter a specifically crafted autorun entry into the registry instead of the expected information. The intent is to hide a malicious executable behind a legitimate (usually signed) executable.
Examples:
Nested commands technique
By using conditional processing symbols the attacker can chain multiple commands. Examples for processing symbols can include:
| Character | Syntax | Definition |
| & [...] | command1 & command2 | Use to separate multiple commands on one command line. Cmd.exe runs the first command, and then the second command. |
| && [...] | command1 && command2 | Use to run the command following && only if the command preceding the symbol is successful. |
| || [...] | command1 || command2 | Use to run the command following || only if the command preceding || fails. |
The advantage here is that Autoruns will display the entry by the name of the first command.
For example, this entry appears as MSASCuIL (part of Windows Defender antivirus): 
Closer look on the command line (chaining commands): 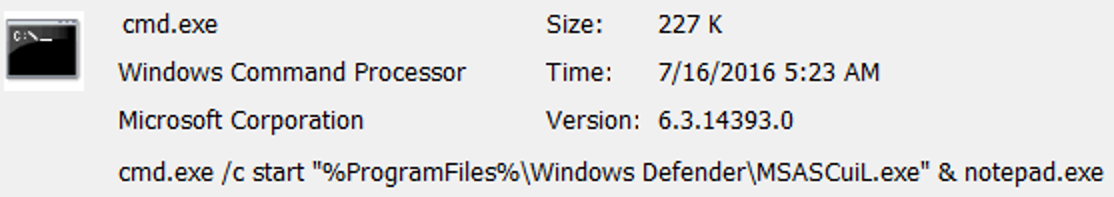
-
Abusing legitimate executables
By using legitimate executables (with the ability to execute arbitrary programs or commands) the attacker can disguise the real commands. Here are few examples for abusing built-in signed executables:
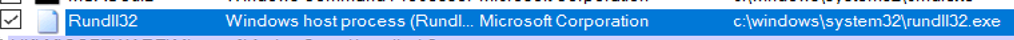
Rundll32.exe – this program, used to execute code stored in .dll files can be used with shell command to run any program. For example:
rundll32.exe shell32.dll,ShellExec_RunDLL notepad.exe (This will execute notepad.exe)
For example:
Closer look on the command line:
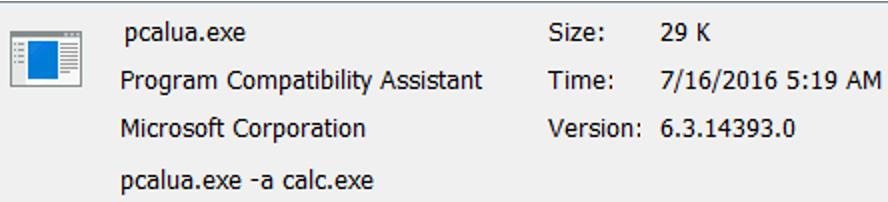
Program Compatibility Assistant (pcalua), same as previuos, but more dangerous because when "Hide Windows entries" is selected (which is a default setting) it is completely hidden from Autoruns.
SyncAppvPublishingServer.vbs or SyncAppvPublishingServer.exe used for initiates the App-V Publishing Refresh operation.
For example: SyncAppvPublishingServer.exe "n; Start-Process notepad.exe"
Indirect manipulation
These techniques include DLL search order, Extension Search Order hijacking and using legacy COM objects. These are just the tip of the iceberg though, and need to be addressed in additional post (maybe in the future )
Lessons Learned for defenders
- Unselect "Hide Microsoft Entries" and "Hide Windows Entries"
- In Scan Options enable "Verify code signatures" and "Check VirusTotal.com"
- Carefully review any entry that include cmd.exe, pcalua or SyncAppvPublishingServer.
- Carefully review any entry with multiple parameters and piping
- Implement Application whitelisting (AppLocker or Device Guard)
- Install and configure Sysinternals Sysmon to review the actual list of running processes during startup.
Link to security researchers talk: https://github.com/huntresslabs/evading-autoruns/blob/master/Evading_Autoruns_Slides.pdf
Comments
- Anonymous
November 07, 2017
But there is a clue that there is something fishy. In the first example, the icon is using the icon in cmd.exe and not something you would expect.- Anonymous
November 07, 2017
you are right, there is a clue for some techniques, but you need to spot it.
- Anonymous