Automating Azure Just In Time VM Access
RDP Brute force
When it comes to managing Azure virtual machines, administrators are usually using Remote Desktop (Windows) or SSH (Linux) to remotely connect and manage.
We have seen cases where virtual machines were infected with ransomware, cryptocurrency miners, and other types of malware.
The initial method to get access to these virtual machines was RDP brute force attacks. Brute force attack is checking all possible usernames or passwords until the correct one is found (Not the most sophisticated form of attack, but relatively simple to perform and given enough time it works).
How to protect against RDP brute force attacks
Administrators can take multiple measures such as:
- Disabling the public IP address, and using one of these connection methods:
- Point-to-site VPN
- Site-to-site VPN
- ExpressRoute
- Require two-factor authentication
- Use complex passwords
- Limit the amount of time that the port are open
The last method is implemented in a new Azure Security Center service called JIT VM Access, which allows you to secure remote access to one or more virtual machines. By using Just-in-Time VM Access (JIT), one could dramatically reduce the attack surface to Azure environment and it is highly recommend to implement it as well.
How JIT VM Access works
- First, you need to be in the Standard Pricing tier of Azure Security Center
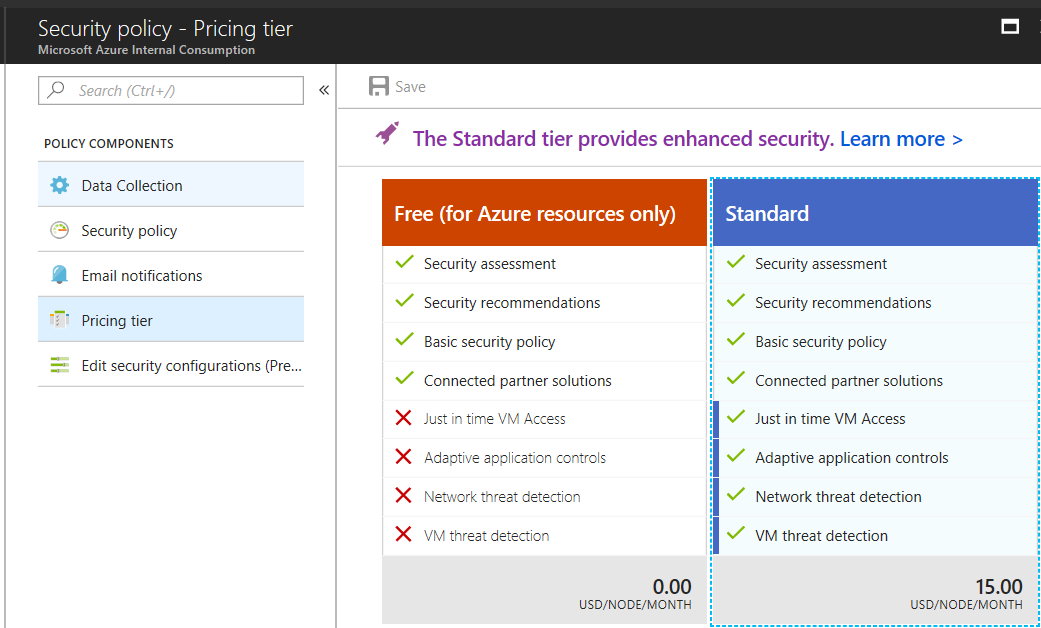
- Enable JIT access for the selected Azure virtual machine(s)

- At this point, the Network Security Group (NSG) of the virtual machine(s) is updated with rules to block remote management access
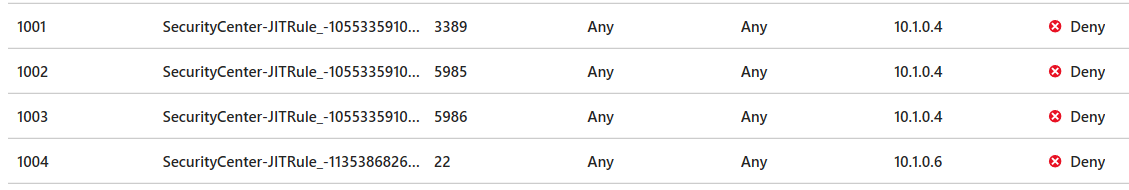
- Use Azure Security Center to request access to a virtual machine using one of the protocols in the policy
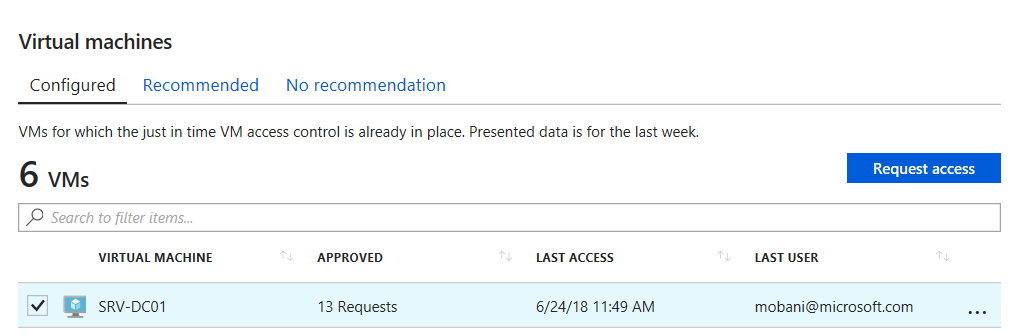
- The required NSG is updated to allow inbound access for that protocol
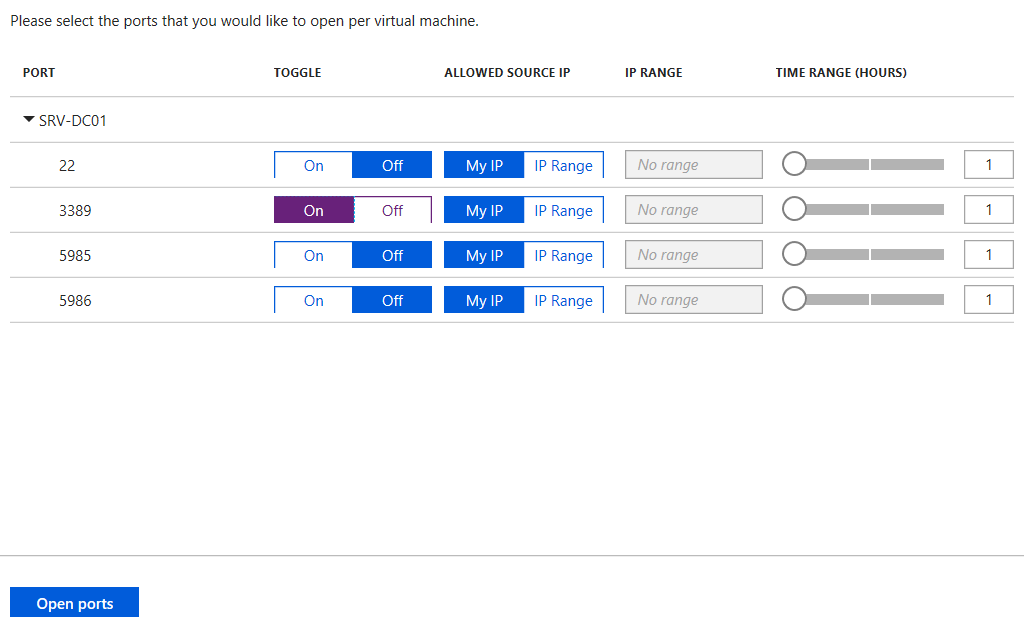
- Admin/Dev can remote into the virtual machine
- Security Center will remove the allow rule in the NSG after the predetermined amount of time that is specified in the policy
Automating JIT VM Access
I wrote a PowerShell script (inspired by Azure Security Center PowerShell repository) to automate the entire process for multiple machines. The script will connect to Azure Security Center endpoint, and then will open the ports temporarily (per your configuration).
For example, let's build the following JIT VM Access request:
- Request RDP port (3389) access
- Limit the time to one and a half hours
- Allow connections only from the source IP address where the script was running
Will result in the following command line:
Enable-JustInTimeAccess -Hours 1.5 -Port 3389 -UseCurrentIP
- Connecting to Azure Security Center (you can use SubscriptionId parameter, or select during runtime)
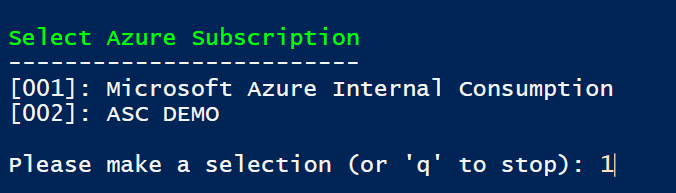
- Then, select the Resource Group
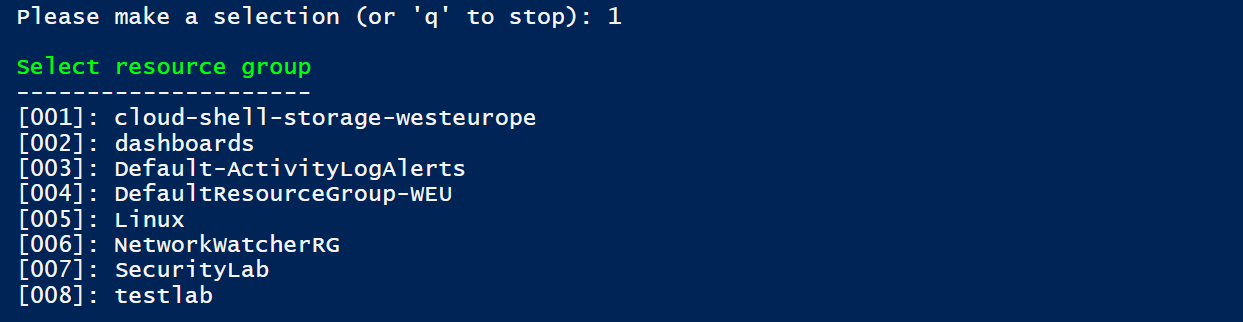
- The script will enable the JIT Access VM for all the virtual machines in the Resource Group
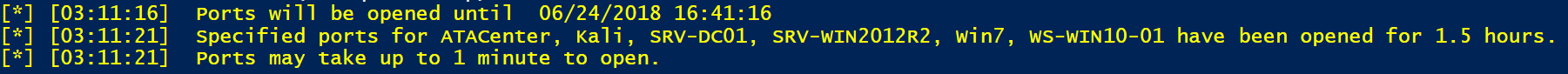
How to run the script
- Copy the script from the gallery into Visual Studio Code and save it as a .ps1 file
- Configure the command line at the bottom of the script to suit your needs
- Run it by pressing F5
- Enter the credentials of an Azure Admin (or contributor) into the password prompt
- Select the appropriate Azure subscription, resource group and other parameters
Link to script
https://gallery.technet.microsoft.com/Automating-Azure-Just-In-e7e1a13b