Part II: How to protect your HTTPS communication from Man-In-the-Middle's decryption in Windows Store App–about which certificate should be included for “Exclusive Trust”
Months ago we wrote a blog article about How to protect your HTTPS communication from Man-In-the-Middle's decryption in Windows Store App, which was also demoed during TechEd 2013 China last December. However, everything ran smoothly until last week… We reviewed the demo again but it failed with an error message that we’ve never seen when it tries to post some content to a HTTPS endpoint:
Exception.Message = "The text associated with this error code could not be found. The certificate authority is invalid or incorrect"
It is strange because we’ve never modified any code, certification, configuration on server or client app, neither our certification was expired. After hundreds of attempts and tests, in short, we finally made it by including only the root certificate instead of the certificate issued to the target domain.
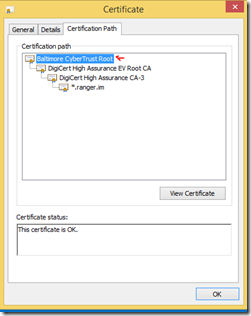
For example, if we want to protect your communication with https://ranger.im, whose SSL certificate path is like below
For now, let’s view and copy its Root CA “Baltimore CyberTrust Root” to your Store App project and forget previous one for *.ranger.im. Then everything will work fine like before.
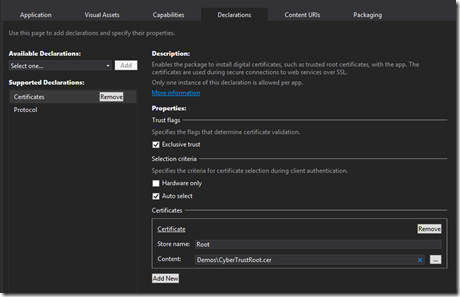
In our previous practice, we just put the .CER file issued to *.ranger.im into Package.appxmanifest/Declarations/Certificates and it ran well. However it no longer works and we may see errors saying the CA is invalid. We thought that Windows may have changed some logic of the certification exclusive trust in some patch after last December, but we so far haven’t found any clue about that.
Then, if Fiddler tries to capture the https traffic and acts a “man-in-the-middle” by changing the certificate chain, the Web operation in code will throw the same error message The certificate authority is invalid or incorrect. Although our previously expected error HttpRequestException whose message {"The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel."} looks more suitable may never appear again, now it just works.
It seems that we are the only one discussing about the “Exclusive Trust” mechanism for store app on the internet. Hope it helps if anyone encounters the same problem or scenario.