Windows 365 opções de implementação de rede
Tem duas opções para a implementação de rede do serviço Windows 365:
- Utilizar uma rede alojada na Microsoft
- Opção recomendada.
- Ideal para o Windows 365 funcionalidades de Software como Serviço (SaaS) de simplicidade, fiabilidade e escalabilidade.
- Suporta o modelo de identidade de associação Microsoft Entra.
- Sem requisitos de experiência ou subscrição do Azure.
- Utilizar o Azure Network Connections (ANC)
- Suporta modelos de identidade de associação híbrida Microsoft Entra e Microsoft Entra.
Rede alojada na Microsoft
Esta opção é simples, fiável e dimensionável, oferecendo conectividade ao Cloud PC em que a Microsoft fornece o serviço numa abordagem SaaS verdadeira. Com esta opção, a Microsoft:
- Configura e gere totalmente a infraestrutura e os serviços relacionados necessários para fornecer PCs em Nuvem funcionais aos seus utilizadores.
- Gere a rede que os PCs na Cloud ocupam.
- Fornece um modelo Confiança Zero alinhado com o Framework de um ambiente de Computação de UtilizadorEs Finais (EUC). Para obter mais informações, veja Saiba mais sobre os pontos finais nativos da cloud.
A única responsabilidade do cliente é a configuração e gestão dos PCs na Cloud.
A Microsoft recomenda que os clientes utilizem esta opção para a implementação Windows 365.
Não tem de introduzir as suas próprias subscrições do Azure, planear, estruturar, implementar ou gerir a infraestrutura. Os clientes podem dedicar a equipa do EUC a concentrarem-se na gestão de configurações e segurança do Cloud PC a partir de um único console de gerenciamento fornecido pelo Intune.
Esta opção é análoga ao fornecimento de um portátil a um funcionário para utilizar em casa. O utilizador, enquanto organização, não controla a rede em que o dispositivo se encontra. Controla totalmente a forma como o dispositivo Windows está configurado, protegido e como se liga à sua rede no local. Com Windows 365, este controlo é possível graças às configurações e controlos de segurança adaptáveis alinhados com a Arquitetura de Segurança Confiança Zero ponto a ponto.
Por exemplo, os utilizadores podem ser autenticados com controlos adaptáveis do Acesso Condicional Microsoft Entra. A conectividade empresarial pode ser fornecida através da VPN. A segurança da Internet pode utilizar um gateway Web seguro (SWG) baseado na cloud. A vantagem é que os dispositivos podem ser implementados em escala num curto período de tempo sempre que necessário numa rede resiliente e de largura de banda elevada.
Diagrama: opção de rede alojada na Microsoft - apenas Microsoft Entra associação
Este diagrama mostra a rede alojada na Microsoft com o CLOUD PC e a rede virtual card numa subscrição gerida pela Microsoft.
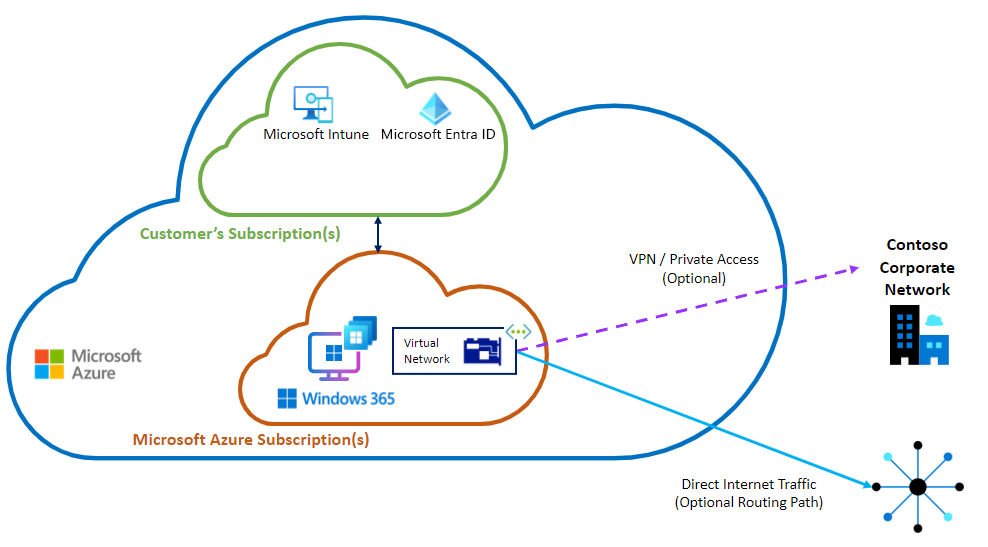
Benefícios da opção de rede alojada na Microsoft
- Não é necessária nenhuma subscrição do Azure. A Microsoft fornece e gere totalmente a infraestrutura necessária para que o CLOUD PC funcione. Tudo o que precisa são as licenças necessárias.
- Sem custos adicionais para a infraestrutura de rede. Os custos do Azure de operar a sua própria rede virtual (VNet) e aplicações virtuais não se aplicam. A Microsoft trata da infraestrutura de rede.
- Não são necessários conhecimentos ou gestão de rede do Azure. A VNet é totalmente gerida pela Microsoft.
- Baixa complexidade e implementação rápida. Há pouca complexidade na implementação devido a dependências mínimas em elementos do lado do cliente.
- Alinhamento de confiança zero. Os Confiança Zero modelo de operação para os sinais de utilizador, ponto final, carga de trabalho e dados são utilizados para verificação em vez de aplicar confiança à localização de rede.
- Resolução de problemas e operações mais simples. É mais fácil resolver e identificar problemas de rede e adotar a gestão de dispositivos moderna com base em políticas de Intune, controlos de segurança e capacidades de relatórios incorporadas.
Considerações
Antes de utilizar a opção de rede alojada na Microsoft, reveja estas considerações:
- Esta opção não é compatível com o modelo de associação híbrida Microsoft Entra. Esta opção é uma implementação apenas na Cloud sem conectividade à infraestrutura Active Directory local Domain Services. Se tiver Política de Grupo políticas de gestão baseadas em objetos que não podem ser convertidas em Intune, esta opção não é a mais adequada para si.
- Sem controlo da VNet. A NIC virtual é gerida pela Microsoft. Por conseguinte, todos os controlos de rede têm de ser implementados no próprio PC cloud, semelhante aos dispositivos físicos num cenário de trabalho a partir de casa.
- Sem acesso direto a recursos no local. É necessária uma solução de acesso privado ou VPN para aceder a estes recursos. Ao utilizar VPNs com um PC na Cloud, utilize o túnel dividido para garantir que o tráfego RDP não é encaminhado através da VPN.
- Requer um modelo de operação de gestão nativo da cloud, como Intune.
- A porta 25 está bloqueada.
- Ping/ICMP está bloqueado.
- As comunicações de rede local entre PCs na Cloud estão bloqueadas.
- Não é possível conectividade de entrada direta para PCs na Cloud.
- Os administradores não podem controlar os intervalos de endereços IP e/ou o espaço de endereços atribuído aos PCs na Cloud. Windows 365 processa automaticamente os endereços IP.
Opção Ligação de Rede do Azure
Com a opção de implementação da Ligação de Rede do Azure (ANC), está completamente encarregue da VNet e da respetiva configuração. Se estiver a utilizar um modelo de associação híbrida Microsoft Entra, tem de utilizar esta opção de implementação. Esta opção fornece linha de visão para os seus recursos do Azure Directory no local e permite-lhe personalizar objetivos de rede e segurança como:
- Rotas de tráfego.
- Portas e protocolos.
- DS do Active Directory e conectividade de aplicações de linha de negócio.
- Ligações de gateway com VPN ou ExpressRoute.
- Espaço de endereços utilizado pelos PCs na Cloud.
- Permissões de comunicação entre PCs na Cloud.
- Ligações RDP diretas a PCs na Cloud.
Selecione a VNet nas subscrições do Azure. Irá configurar políticas de aprovisionamento que criam os PCs na Cloud na sua vNet. Irá gerir a conectividade do CLOUD PC, incluindo qualquer saída direta da VNet e o caminho de acesso à Internet pretendido.
A Ligação de Rede do Azure suporta dois modelos de implementação de identidade:
- Ingresso Microsoft Entra
- Ingresso Microsoft Entra hibrído
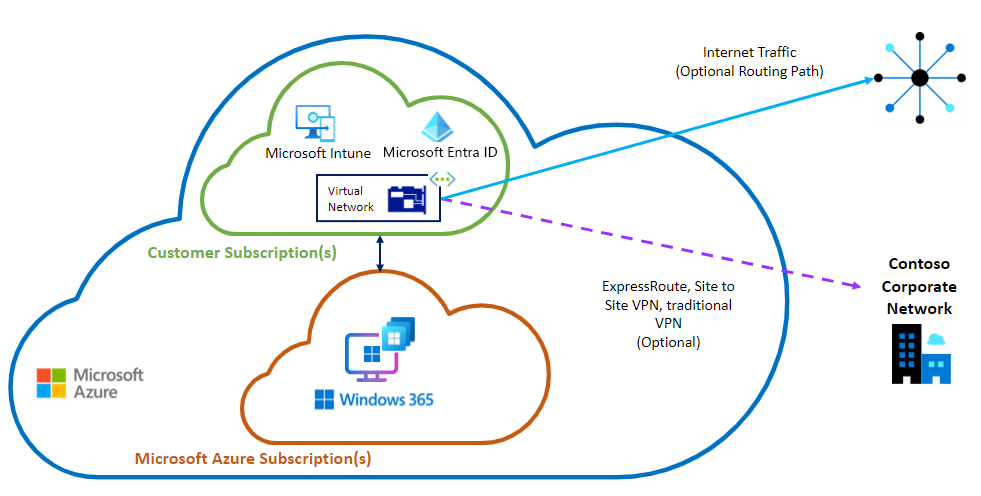
Ingresso Microsoft Entra
Ao utilizar Microsoft Entra associação, não é necessário criar uma ligação da VNet para a sua rede no local. Tem apenas de se certificar de que existe conectividade internet de saída para os pontos finais necessários. No entanto, poderá querer adicionar uma ligação no local para aceder a recursos localizados nos seus servidores de ficheiros e aplicações no local. Pode criar a ligação com o ExpressRoute ou a VPN site a site, mas estas opções apresentam um custo e complexidade adicionais.
Para simplificar, ao utilizar Microsoft Entra associação, recomendamos que utilize a opção de rede alojada na Microsoft anteriormente explicada. Nesse caso, pode utilizar uma solução de acesso privado ou VPN através da Internet para aceder aos recursos empresariais.
Diagrama: opção ANC – associação Microsoft Entra
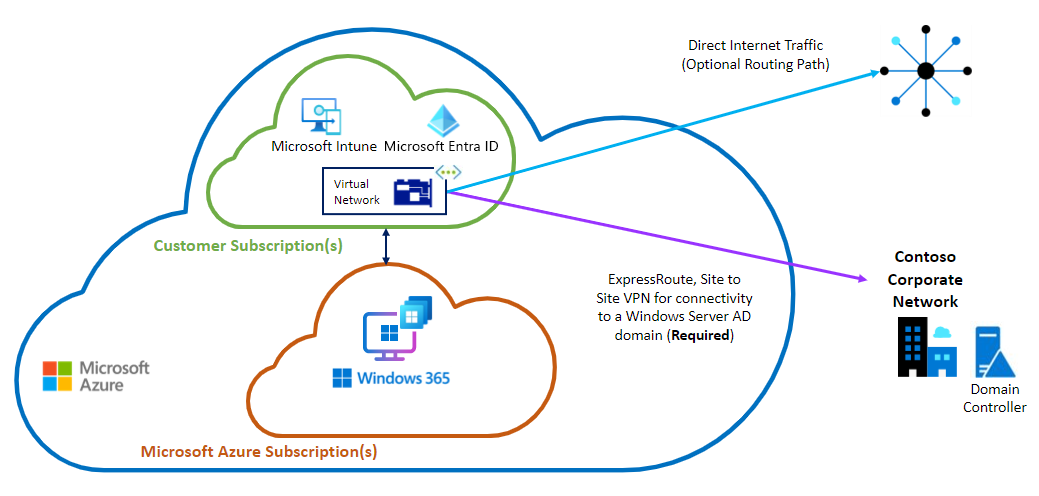
Ingresso Microsoft Entra hibrído
Com Microsoft Entra associação híbrida, é necessária uma ligação à rede no local a partir da VNet. A única forma de aceder à infraestrutura dc aí localizada é utilizar a opção de implementação do ANC. Esta ligação é um componente crítico, pelo que deve ter cuidado para garantir a fiabilidade e a redundância.
Diagrama: opção ANC - Microsoft Entra associação híbrida
Benefícios da opção ANC
- Controlo total da VNet. O NIC do Cloud PC está dentro da sua própria VNet gerida.
- Linha de visão direta para a infraestrutura no local. A vNet pode ser configurada com uma ligação VPN site a site ou ExpressRoute de volta à rede no local para conectividade direta com a infraestrutura do Diretório do Azure ou serviços e aplicações localizados no mesmo.
- O CLOUD PC funcionava como se estivesse numa localização no local. A extensão da rede empresarial para a vNet significa que o CLOUD PC pode funcionar como se estivesse dentro dos limites da rede empresarial.
- Peering simples para outras VNets. Conectividade cruzada simples entre a VNet do CLOUD PC e outras vNets no Azure. Isto suporta a conectividade direta a outros recursos alojados no Azure que a organização utiliza.
Considerações
Antes de utilizar a opção de implementação do ANC, reveja estas considerações:
Subscrição do Azure necessária. A VNet utilizada neste cenário está na sua própria subscrição do Azure. Por conseguinte, tem de ter uma subscrição do Azure e as licenças necessárias.
Custos de saída. Uma vez que a VNet está associada à sua própria conta do Azure, são incorridos quaisquer custos de saída na sua subscrição do Azure.
Custos adicionais para a infraestrutura de rede. Os custos do Azure de operar a sua própria VNet são aplicados à subscrição associada à vNet.
São necessários conhecimentos ou gestão de rede do Azure. Tem de fornecer os conhecimentos e a gestão para manter a sua VNet.
Maior complexidade. Tem de gerir e manter a sua rede, o que é uma tarefa mais complexa do que utilizar uma rede alojada na Microsoft.
Implementação mais longa. Normalmente, a implementação é mais longa do que a opção de rede alojada na Microsoft. Este tempo extra é causado pelo elevado número de elementos do lado do cliente que têm de ser configurados primeiro.
Maior Risco. Uma implementação do ANC é mais complexa do que uma implementação de rede alojada na Microsoft. Esta complexidade aumenta o risco de problemas de conectividade.
As redes alojadas na Microsoft não suportam endereços IP fixos para ligações de saída do Cloud PC. Como resultado, podem ser observados diferentes endereços IP ao utilizar aplicações diferentes ou até mesmo a mesma aplicação em alturas diferentes.
Opções simultâneas
As opções de rede alojada na Microsoft e anc podem ser utilizadas em simultâneo. Por exemplo, pode utilizar a opção ANC para um subconjunto das suas implementações que tenham requisitos legados exclusivos. Para o resto da sua implementação sem esses requisitos, pode utilizar a opção de rede alojada na Microsoft.