Configurar as Comunicações de Rede Segura
O SNC (Secure Network Communications) aumenta a segurança da sua integração SAP com o Power Platform ao encriptar os dados entre um gateway de dados no local e um sistema SAP. Este artigo guia-o na configuração da SNC como uma prova de conceito.
Importante
As definições e recomendações apresentadas neste artigo não se destinam a utilização em produção. Consulte a sua equipa de segurança, as políticas internas e o Parceiro Microsoft para obter orientação sobre como configurar a SNC num ambiente de produção.
Pré-requisitos
- Tem uma ligação SAP que usa o conector ERP SAP.
- Tem acesso a uma instância SAP que pode ser reiniciada e administrada.
- O SAP GUI é instalado e configurado.
- Está familiarizado com as principais tecnologias públicas e privadas.
- O OpenSSL é instalado e configurado. Se tiver o Git para Windows, adicione
C:\Program Files\Git\usr\bin\ao seu sistema PATH para que possa usar o comandoopenssl.
Instalar a Biblioteca Cripto Comum SAP
A Biblioteca Cripto Comum SAP permite que o Conector SAP para Microsoft .NET (NCo) encripte comunicações entre o gateway de dados no local e o SAP. Para extrair a biblioteca, precisa de um utilitário de descompressão proprietária chamado SAPCAR.
Obtenha a SAPCAR
- Aceda ao Centro de Transferência de Software SAP e inicie sessão com as suas credenciais SAP.
- Pesquise por SAPCAR e selecione a versão não arquivada mais recente.
- Selecione o seu sistema operativo.
- Transfira o ficheiro .EXE para
C:\sap\SAR.
Obter a Biblioteca Cripto Comum SAP
- No Centro de Transferência de Software SAP, pesquise por "COMMONCRYPTOLIB" e selecione a versão mais recente.
- Selecione o seu sistema operativo.
- Transfira o ficheiro .SAR com a data de lançamento mais recente para
C:\sap\SAR.
Extrair a Biblioteca Cripto Comum SAP
Abra o PowerShell e aceda a
C:\sap\SAR.Introduza o seguinte comando, substituindo
xxxxpelos seus valores:.\SAPCAR_xxxx.EXE -xvf .\SAPCRYPTOLIBP_xxxx.SAR -R .\..\libs\sapcryptolibConfirme que
sapgenpse.exeestá no diretórioC:\sap\libs\sapcryptolib.
Gerar certificados
Agora que instalou a Biblioteca Cripto Comum SAP, pode gerar certificados para estabelecer confiança e encriptação entre o seu gateway de dados no local e o sistema SAP.
Aviso
Este método é apenas para fins de demonstração e não é recomendado para sistemas de produção. Para sistemas de produção, consulte a sua orientação interna de PKI ou equipa de segurança.
Neste exemplo, os nossos certificados são estruturados como mostrado no diagrama a seguir. A AC Raiz [O=Contoso, CN=AC Raiz] assina o certificado de encriptação SNC [O=Contoso, CN=SNC] e os certificados de utilizador [O=Contoso, CN=UserIDs].
Este artigo foca-se na configuração dos certificados AC Raiz e SNC.
Criar certificados
Configurar a estrutura da pasta:
mkdir rootCA mkdir sncCert # Create the necessary serial and index files if they don't exist if (-Not (Test-Path "rootCA\index.txt")) { New-Item -Path "rootCA\index.txt" -ItemType File } if (-Not (Test-Path "rootCA\serial")) { Set-Content -Path "rootCA\serial" -Value "01" }Gerar uma AC Raiz:
openssl genpkey -algorithm RSA -out rootCA/ca.key.pem -pkeyopt rsa_keygen_bits:2048 openssl req -x509 -new -key rootCA/ca.key.pem -days 7305 -sha256 -extensions v3_ca -out rootCA/ca.cert.pem -subj "/O=Contoso/CN=Root CA"Gerar o certificado SNC:
openssl genrsa -out sncCert/snc.key.pem 2048 openssl req -key sncCert/snc.key.pem -new -sha256 -out sncCert/snc.csr.pem -subj "/O=Contoso/CN=SNC"Crie um ficheiro de configuração OpenSSL,
sncCert/extensions.cnf, para assinar:subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer basicConstraints = critical,CA:false keyUsage = critical,digitalSignature,keyEncipherment,dataEncipherment extendedKeyUsage = clientAuth,emailProtectionAssine o certificado SNC com a AC Raiz:
openssl x509 -req ` -in sncCert/snc.csr.pem ` -CA rootCA/ca.cert.pem ` -CAkey rootCA/ca.key.pem ` -CAcreateserial ` -out sncCert/snc.cert.pem ` -days 3650 ` -sha256 ` -extfile sncCert\extensions.cnf ` -extensions v3_leaf
Criar um Ambiente Seguro Pessoal
Crie um Ambiente Seguro Pessoal (PSE) para o gateway de dados no local. A biblioteca NCo procura pelo certificado SNC dentro do PSE.
Criar um contentor PKCS#12:
openssl pkcs12 -export -out snc.p12 -inkey sncCert\snc.key.pem -in sncCert\snc.cert.pem -certfile rootCA\ca.cert.pemCriar a variável de ambiente SECUDIR:
- Abra Propriedades do Sistema: No Explorador de Ficheiros, clique com o botão direito do rato em Este PC e, em seguida, selecione Propriedades>Definições avançadas do sistema.
- Selecione Variáveis de Ambiente.
- Em Variáveis de sistema, selecione Nova.
- Defina o nome da variável como
SECUDIR. - Defina o valor como
C:\sapsecudir. - Selecione OK.
Importe o contentor PKCS#12 para um PSE:
C:\sap\libs\sapcryptolib\sapgenpse.exe import_p12 -p SAPSNCSKERB.pse C:\pki-certs\snc.p12
Configurar o SAP para SNC
Inicie sessão no SAP GUI.
Aceda ao código da transação
SNC0.Introduza E como a área de trabalho.
Selecione Nova Entrada na barra superior e preencha as informações necessárias.
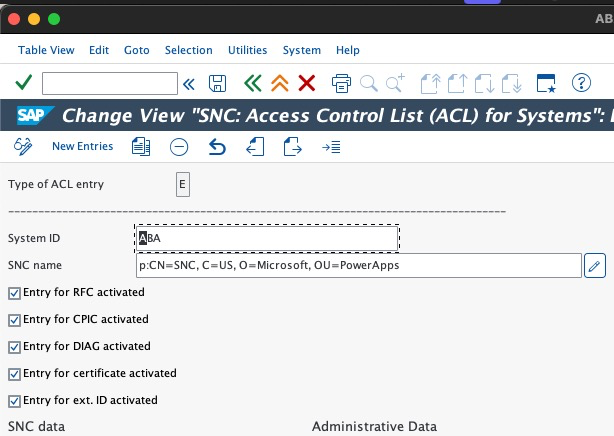
Selecione Guardar.
Regresse ao ecrã principal do SAP GUI.
Aceda ao código da transação
RZ10.Defina estes parâmetros de perfil:
snc/accept_insecure_gui: 1 snc/accept_insecure_rfc: 1 snc/enable: 1 snc/extid_login_diag: 1 snc/extid_login_rfc: 1 snc/gssapi_lib: $(SAPCRYPTOLIB) snc/identity/as: p:CN=ID3, O=Contoso snc/permit_insecure_start: 1 snc/data_protection/max: 3```Guarde os parâmetros do perfil e reinicie o sistema SAP.
Trocar certificados entre o SAP e o gateway de dados no local
Para estabelecer confiança, precisa de trocar certificados entre o gateway de dados no local e o SAP.
Adicionar o certificado SNC do gateway ao SAP
- No SAP GUI, aceda ao código da transação
STRUST. - Se SNC SAPCryptolib tiver um X vermelho, clique com o botão direito do rato nele e selecione Criar.
- Caso contrário, clique duas vezes em SNC SAPCryptolib e, em seguida, clique duas vezes no seu Próprio Certificado.
- Selecione Importar Certificado e escolha o seu certificado público
sncCert\snc.cert.pem. - Selecione Adicionar à Lista de Certificados.
Adicionar o certificado SAP SNC ao gateway de dados local
No SAP GUI, aceda ao código da transação
STRUST.Clique duas vezes em SNC SAPCryptolib e, em seguida, clique duas vezes no seu Próprio Certificado.
Exportar o certificado público.
Mova o certificado público para o computador do gateway (por exemplo,
C:\sap\contoso-public-key.crt).Importe o certificado para o PSE do seu gateway:
C:\sap\libs\sapcryptolib\sapgenpse.exe maintain_pk -p SAPSNCSKERB.pse -v -a C:\pki-certs\sncCert\sapkerb.public.cert
Testar a ligação segura
Siga os passos para testar a ligação segura. Depois de concluir o teste com êxito, estará pronto para implementar o SNC no seu ambiente de produção.
Crie um fluxo instantâneo no Power Automate.
Adicione uma ação
SAP ERP Call Function.Adicione os seguintes parâmetros SNC à cadeia de Ligação SAP:
{ "AppServerHost": "xxx", "Client": "xx", "SystemNumber": "xx", "LogonType": "ApplicationServer", "SncLibraryPath": "C:\\sap\\libs\\sapcryptolib\\sapcrypto.dll", "SncMyName": "p:CN=SNC, O=Contoso", "SncPartnerName": "p:CN=ID3, O=Contoso", "SncQop": "Default", "UseSnc": "true", "SncSso": "Off" }```Teste a ligação usando a função RFC
STFC_CONNECTION.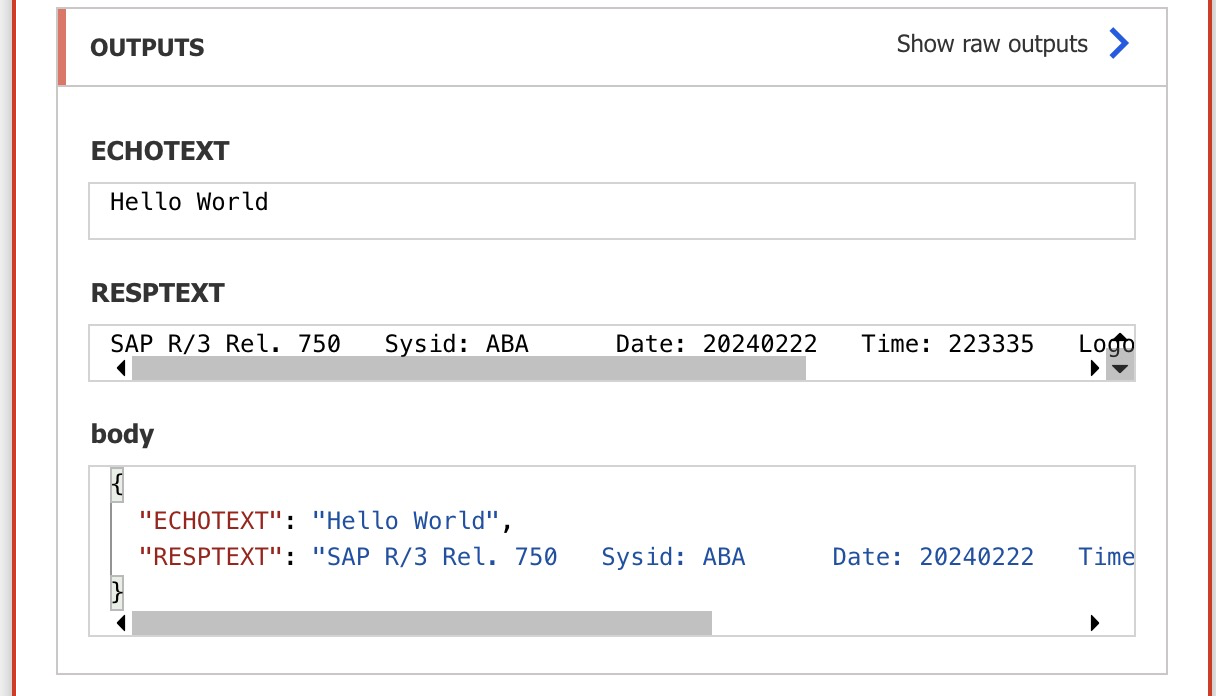
Importante
Certifique-se de que processa as chaves privadas de forma segura e de que as elimine após a conclusão desta configuração.