Configurar o reencaminhamento de eventos do Windows para o sensor autónomo do Defender para Identidade
Este artigo descreve um exemplo de como configurar o reencaminhamento de eventos do Windows para o sensor autónomo Microsoft Defender para Identidade. O reencaminhamento de eventos é um método para melhorar as suas capacidades de deteção com eventos adicionais do Windows que não estão disponíveis na rede do controlador de domínio. Para obter mais informações, consulte Descrição geral da coleção de eventos do Windows.
Importante
Os sensores autónomos do Defender para Identidade não suportam a recolha de entradas de registo do Rastreio de Eventos para Windows (ETW) que fornecem os dados para várias deteções. Para uma cobertura completa do seu ambiente, recomendamos a implementação do sensor do Defender para Identidade.
Pré-requisitos
Antes de começar:
- Certifique-se de que o controlador de domínio está configurado corretamente para capturar os eventos necessários. Para obter mais informações, veja Recolha de eventos com Microsoft Defender para Identidade.
- Configurar o espelhamento de porta
Passo 1: adicionar a conta de serviço de rede ao domínio
Este procedimento descreve como adicionar a conta de serviço de rede ao domínio do Grupo de Leitores do Registo de Eventos . Para este cenário, suponha que o sensor autónomo do Defender para Identidade é um membro do domínio.
Em Utilizadores e Computadores do Active Directory, aceda à pasta Incorporada e faça duplo clique em Leitores do Registo de Eventos.
Selecione Membros.
Se o Serviço de Rede não estiver listado, selecione Adicionar e, em seguida, introduza Serviço de Rede no campo Introduzir os nomes dos objetos a selecionar .
Selecione Verificar Nomes e selecione OK duas vezes.
Depois de adicionar o Serviço de Rede ao grupo Leitores do Registo de Eventos , reinicie os controladores de domínio para que a alteração entre em vigor.
Para obter mais informações, veja Contas do Active Directory.
Passo 2: Criar uma política que define a definição Configurar destino
Este procedimento descreve como criar uma política nos controladores de domínio para definir a definição Configurar Gestor de Subscrições de destino
Sugestão
Pode criar uma política de grupo para estas definições e aplicar a política de grupo a cada controlador de domínio monitorizado pelo sensor autónomo do Defender para Identidade. Os passos seguintes modificam a política local do controlador de domínio.
Em cada controlador de domínio, execute:
winrm quickconfigA partir de uma linha de comandos, introduza
gpedit.mscExpanda Configuração > do Computador Modelos Administrativos > Componentes do Windows Reencaminhamento de Eventos>. Por exemplo:
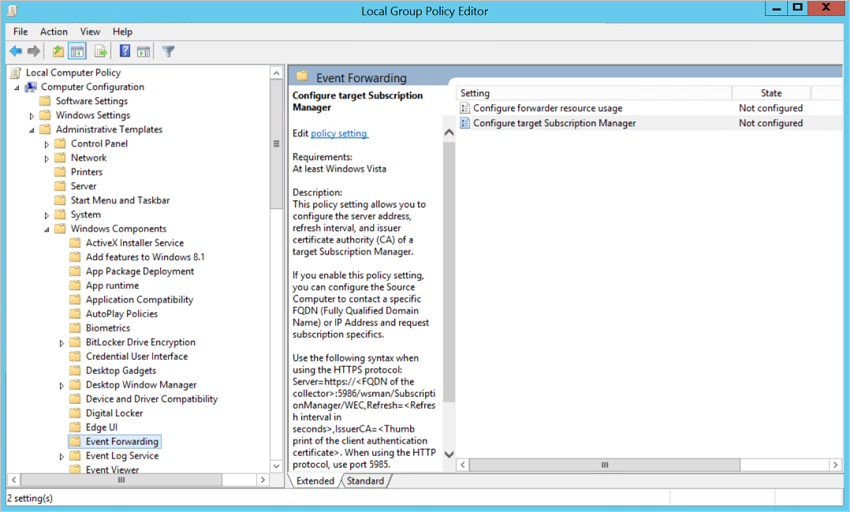
Faça duplo clique em Configurar Gestor de Subscrições de destino e, em seguida:
Selecione Ativado.
Em Opções, selecione Mostrar.
Em SubscriptionManagers, introduza o seguinte valor e selecione OK:
Server=http://
<fqdnMicrosoftDefenderForIdentitySensor>:5985/wsman/SubscriptionManager/WEC,Refresh=10Por exemplo, com Server=http://atpsensor.contoso.com:5985/wsman/SubscriptionManager/WEC,Refresh=10:
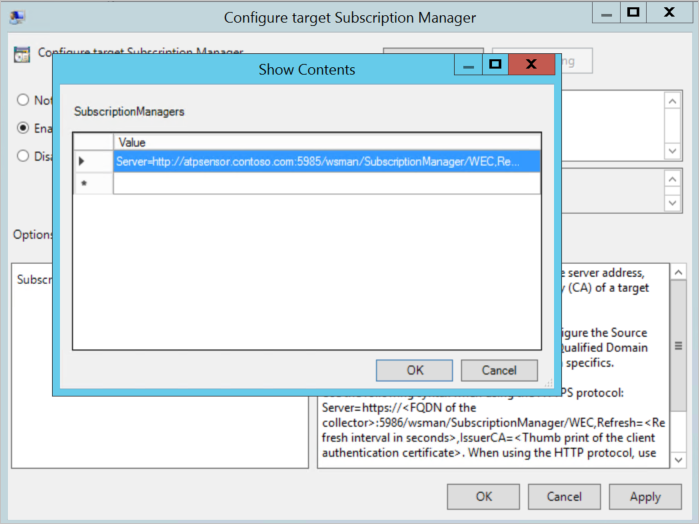
Selecione OK.
A partir de uma linha de comandos elevada, introduza:
gpupdate /force
Passo 3: Criar e selecionar uma subscrição no sensor
Este procedimento descreve como criar uma subscrição para utilização com o Defender para Identidade e, em seguida, selecioná-la a partir do sensor autónomo.
Abra uma linha de comandos elevada e introduza
wecutil qcAbra Visualizador de Eventos.
Clique com o botão direito do rato em Subscrições e selecione Criar Subscrição.
Introduza um nome e uma descrição para a subscrição.
Para o Registo de Destino, confirme que a opção Eventos Reencaminhados está selecionada. Para que o Defender para Identidade leia os eventos, o registo de destino tem de ser Eventos Reencaminhados.
Selecione Computador de origem iniciado>Selecione Computadores Grupos>Adicionar Computador de Domínio.
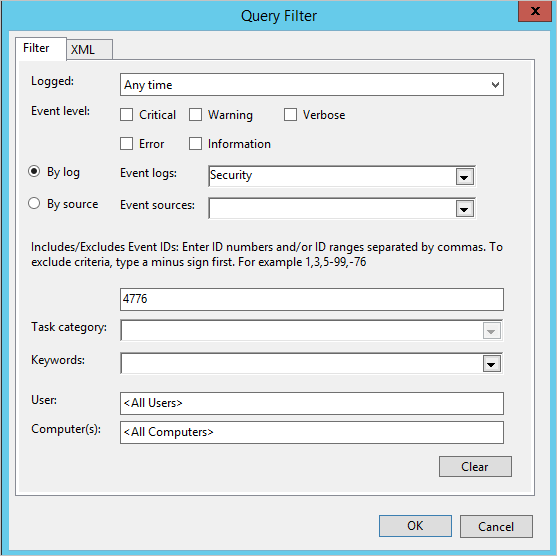
Selecione Selecionar Eventos> Porsegurançade registo>.
No campo Inclui/Exclui ID do Evento , escreva o número do evento e selecione OK. Por exemplo, introduza 4776:
Regresse à janela de comandos aberta no primeiro passo. Execute os seguintes comandos, substituindo SubscriptionName pelo nome que criou para a subscrição.
wecutil ss "SubscriptionName" /cm:"Custom" wecutil ss "SubscriptionName" /HeartbeatInterval:5000Regresse à consola do Visualizador de Eventos. Clique com o botão direito do rato na subscrição criada e selecione Estado do Runtime para ver se existem problemas com o estado.
Após alguns minutos, verifique se os eventos que definiu para serem reencaminhados são apresentados nos Eventos Reencaminhados no sensor autónomo do Defender para Identidade.
Para obter mais informações, veja: Configurar os computadores para reencaminhar e recolher eventos.
Conteúdos relacionados
Para mais informações, consulte:
