Configurar grupos de segurança de rede com o Windows Admin Center
Aplica-se a: Azure Local 2311.2 e posterior; Windows Server 2022, Windows Server 2019, Windows Server 2016
Este tópico fornece instruções passo a passo sobre como usar o Windows Admin Center para criar e configurar NSGs (grupos de segurança de rede) para gerenciar o fluxo de tráfego de dados usando o Firewall do Datacenter. Ele também fornece instruções sobre como gerenciar grupos de segurança de rede em redes virtuais e lógicas de Rede Definida por Software (SDN). Você habilita e configura o Datacenter Firewall criando grupos de segurança de rede e aplicando-os a uma sub-rede ou a uma interface de rede. Para saber mais, consulte O que é o Datacenter Firewall? Para usar scripts do PowerShell para fazer isso, consulte Configurar grupos de segurança de rede com o PowerShell.
Antes de configurar grupos de segurança de rede, você precisa implantar o Controlador de Rede. Para saber mais sobre o Controlador de Rede, consulte O que é o Controlador de Rede? Para implantar o Controlador de Rede usando scripts do PowerShell, consulte Implantar uma infraestrutura SDN.
Além disso, se você quiser aplicar grupos de segurança de rede a uma rede lógica SDN, você precisa primeiro criar uma rede lógica. Da mesma forma, se você quiser aplicar grupos de segurança de rede a uma rede virtual SDN, você precisa primeiro criar uma rede virtual. Para saber mais, veja:
Criar um grupo de segurança de rede
Você pode criar um grupo de segurança de rede no Windows Admin Center.
No ecrã inicial do Windows Admin Center, em Todas as ligações, selecione o sistema no qual pretende criar o grupo de segurança de rede.
Em Ferramentas, role para baixo até a área Rede e selecione Grupos de segurança de rede.
No grupos de segurança de rede, selecione o separador Inventário e, em seguida, selecione Novo.
No painel Grupo de Segurança de Rede, digite um nome para o grupo de segurança de rede e selecione Enviar.
Em Grupos de segurança de rede, verifique se o estado de provisionamento do novo grupo de segurança de rede mostra Bem-sucedido.
Criar regras do grupo de segurança de rede
Depois de criar um grupo de segurança de rede, você estará pronto para criar regras de grupos de segurança de rede. Se quiser aplicar regras de grupo de segurança de rede ao tráfego de entrada e de saída, você precisará criar duas regras.
No ecrã inicial do Windows Admin Center, em Todas as ligações, selecione o sistema no qual pretende criar o grupo de segurança de rede.
Em Ferramentas, role para baixo até a área Rede e selecione Grupos de segurança de rede.
Em Network security groups, selecione a aba Inventário e, em seguida, selecione o grupo de segurança de rede que acabou de criar.
Em Regra de segurança de rede, selecione Novo.
No painel Regra de segurança de rede, forneça as seguintes informações:
- Nome da regra.
- Prioridade da regra – Os valores aceitáveis são de 101 a 65000. Um valor mais baixo indica uma prioridade mais elevada.
- Tipos – Pode ser de entrada ou de saída.
- Protocolo – Especifique o protocolo para corresponder a um pacote de entrada ou de saída. Os valores aceitáveis são Todos, TCP e UDP.
- Prefixo do endereço de origem – Especifique o prefixo do endereço de origem para corresponder a um pacote de entrada ou de saída. Se você fornecer *, isso indica todos os endereços de origem.
- Intervalo de portas de origem – Especifique o intervalo de portas de origem para corresponder a um pacote de entrada ou de saída. Se você fornecer *, isso indica todas as portas de origem.
- Prefixo do endereço de destino – Especifique o prefixo do endereço de destino para corresponder a um pacote de entrada ou de saída. Se você fornecer *, isso indica todos os endereços de destino.
- Intervalo de portas de destino – Especifique o intervalo de portas de destino para corresponder a um pacote de entrada ou saída. Se você fornecer *, isso indica todas as portas de destino.
- Ações – Se as condições acima forem correspondidas, especifique para permitir ou bloquear o pacote. Os valores aceitáveis são Permitir e Negar.
- Registo – Especifique se deseja ativar ou desativar o registo para a regra. Se o registo estiver ativado, todo o tráfego correspondente a esta regra é registado nos computadores anfitriãos.
Selecione Submeter.
Aplicar um grupo de segurança de rede a uma rede virtual
Depois de criar um grupo de segurança de rede e regras para ele, você precisa aplicar o grupo de segurança de rede a uma sub-rede de rede virtual, uma sub-rede de rede lógica ou uma interface de rede.
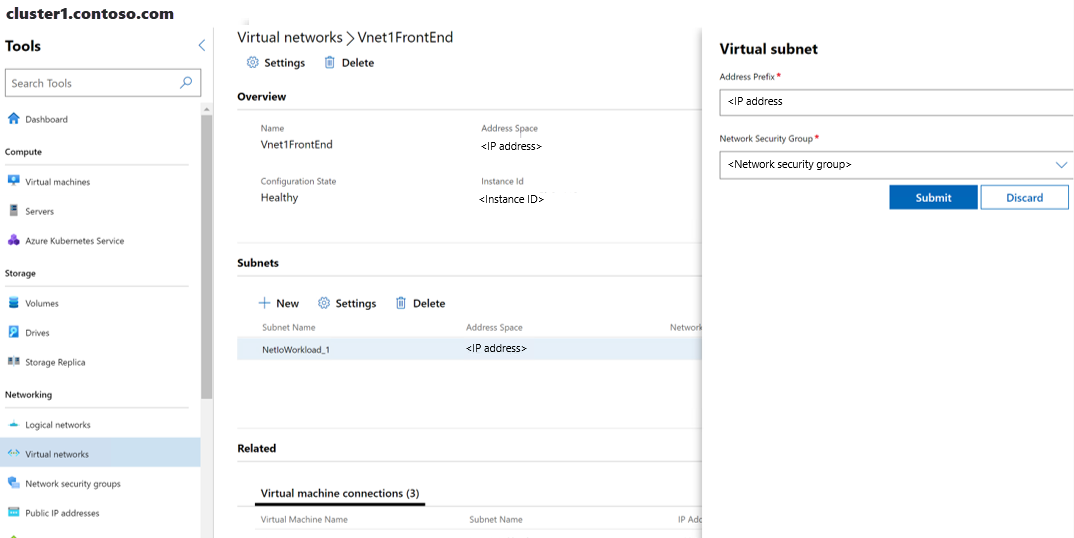
Em Ferramentas, role para baixo até a área Rede e selecione Redes virtuais.
Selecione a guia Inventário e, em seguida, selecione uma rede virtual. Na página subsequente, selecione uma sub-rede de rede virtual e, em seguida, selecione Configurações.
Selecione um grupo de segurança de rede na lista suspensa e, em seguida, selecione Enviar.
A conclusão da última etapa associa o grupo de segurança de rede à sub-rede virtual e aplica-a a todos os computadores conectados à sub-rede virtual.
Aplicar um grupo de segurança de rede a uma rede lógica
Você pode aplicar um grupo de segurança de rede a uma sub-rede de rede lógica.
Em Ferramentas, role para baixo até a área Rede e selecione Redes lógicas.
Selecione a guia Inventário e, em seguida, selecione uma rede lógica. Na página subsequente, selecione uma sub-rede lógica e, em seguida, selecione Configurações.
Selecione um grupo de segurança de rede na lista suspensa e, em seguida, selecione Adicionar.
A conclusão da última etapa associa o grupo de segurança de rede à sub-rede de rede lógica e aplica-a a todos os computadores conectados à sub-rede de rede lógica.
Aplicar um grupo de segurança de rede a uma interface de rede
Você pode aplicar um grupo de segurança de rede a uma interface de rede, durante a criação de uma máquina virtual (VM) ou posterior.
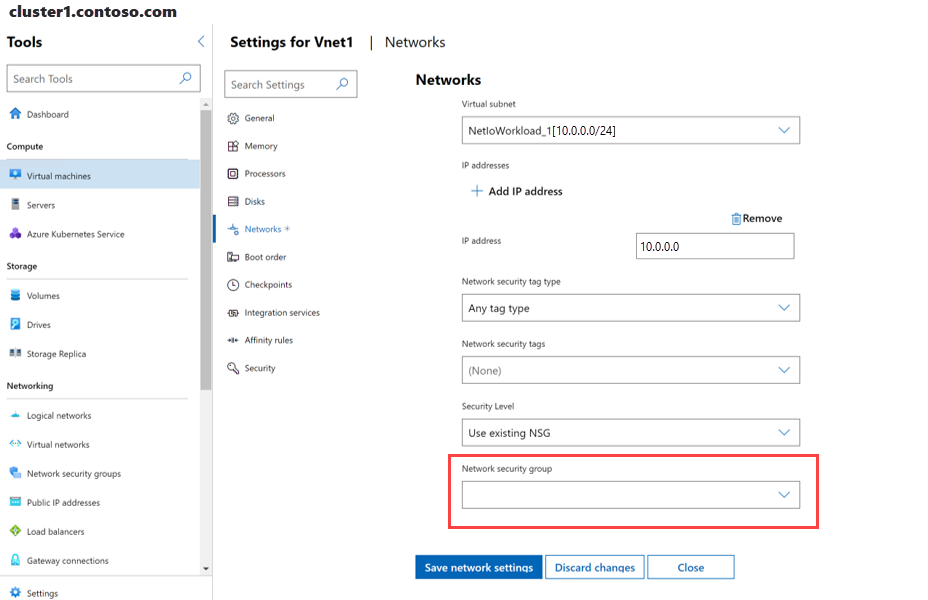
Em Ferramentas, role para baixo até a área Rede e selecione Máquinas virtuais.
Selecione a guia Inventário , selecione uma VM e selecione Configurações.
Na página Configurações, selecione Redes.
Desloque-se para baixo até Grupo de segurança de rede, expanda a lista pendente, selecione um grupo de segurança de rede e selecione Guardar definições de rede.
A conclusão da última etapa associa o grupo de segurança de rede à interface de rede e aplica-o a todo o tráfego de entrada e saída da interface de rede.
Obter uma lista de grupos de segurança de rede
Você pode visualizar facilmente uma lista dos grupos de segurança de rede em seu sistema.
- No ecrã inicial do Windows Admin Center, em Todas as ligações, selecione o sistema no qual pretende ver uma lista de grupos de segurança de rede.
- Em Ferramentas, role para baixo até a área Rede e selecione Grupos de segurança de rede.
- A guia Inventário exibe a lista dos grupos de segurança de rede disponíveis no sistema e fornece comandos que você pode usar para gerenciar grupos de segurança de rede individuais na lista. É possível:
Exiba a lista de grupos de segurança de rede.
Exiba o número de regras para cada grupo de segurança de rede e o número de sub-redes e NICs aplicadas a cada grupo de segurança de rede.
Exiba o Estado de Provisionamento de cada grupo de segurança de rede (Êxito, Falha).
Exclua um grupo de segurança de rede.
Se você selecionar um grupo de segurança de rede na lista, poderá exibir suas regras. Em seguida, você pode adicionar, excluir ou modificar as configurações de regra do grupo de segurança de rede.
Excluir um grupo de segurança de rede
Você pode excluir um grupo de segurança de rede se não precisar mais dele.
Nota
Depois de excluir um grupo de segurança de rede da lista de grupos de segurança de rede, verifique se ele não está associado a uma sub-rede ou a uma interface de rede.
Em Ferramentas, role para baixo até a área Rede e selecione Grupos de segurança de rede.
Selecione a guia Inventário , selecione um grupo de segurança de rede na lista e selecione Excluir.
No prompt Excluir confirmação, selecione Sim.
Ao lado da caixa de pesquisa, selecione Atualizar para garantir que o grupo de segurança de rede foi excluído.
Próximos passos
Para obter mais informações, consulte também: