Solucionar problemas de gerenciamento de VM do Azure Arc para o Azure Local
Aplica-se a: Azure Local 2311.2 e posterior
Este artigo fornece orientação sobre como coletar logs e solucionar problemas com máquinas virtuais (VMs) do Azure Arc em sua instância local do Azure. Ele também lista as limitações e os problemas conhecidos que existem atualmente com o gerenciamento de VM do Azure Arc.
Solucionar problemas de VMs do Azure Arc
Esta seção descreve os erros relacionados ao gerenciamento de VM do Azure Arc e suas resoluções recomendadas.
Falha ao tentar ativar o gerenciamento de convidados
Ao tentar executar o comando para habilitar o gerenciamento de convidados, você verá o seguinte erro:
Erro:Deployment failed. Correlation ID: aaaa0000-bb11-2222-33cc-444444dddddd. VM Spec validation failed for guest agent provisioning: Invalid managed identity. A system-assigned managed identity must be enabled in parent resource: Invalid Configuration
Essa falha ocorre porque a identidade gerenciada não foi criada para essa VM. A Identidade Gerenciada atribuída pelo sistema é necessária para habilitar o gerenciamento de convidados.
Resolução:
Siga estas etapas para verificar se a Identidade Gerenciada não foi criada para essa VM e, em seguida, habilite a Identidade Gerenciada atribuída pelo Sistema.
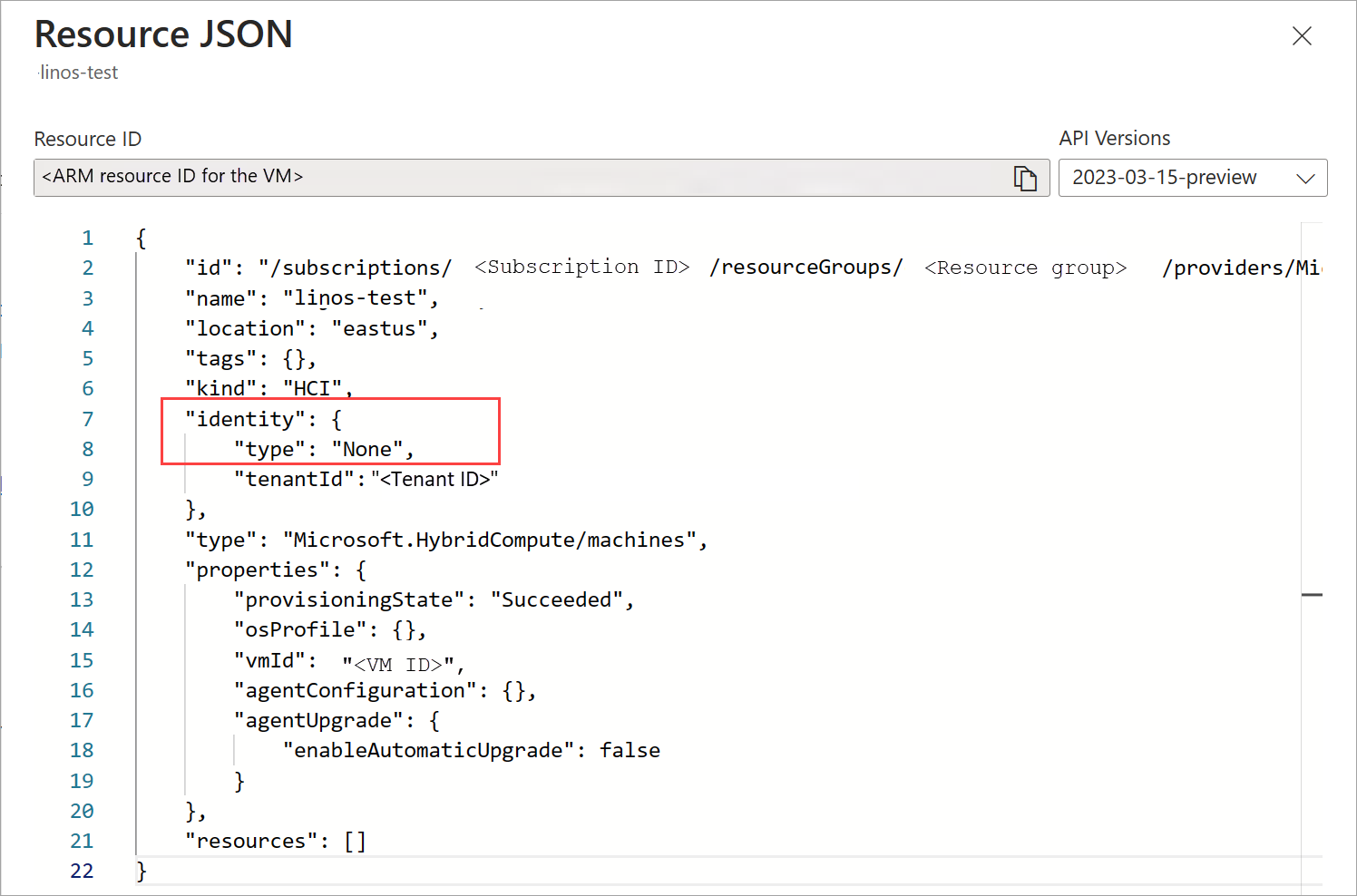
No portal do Azure, vá para a VM. Navegue até a página Visão geral . Na guia Propriedades, em Configuração, o gerenciamento de convidados deve ser exibido como Desabilitado. Selecione a Visualização JSON no canto superior direito.
Sob o parâmetro
Identity, otypedeve ser mostrado comoNone.Para criar identidade gerenciada, conecte-se à máquina Local do Azure via RDP. Execute o seguinte comando:
az extension add --name connectedmachineVerifique se a extensão da CLI da máquina conectada está instalada no sistema. Aqui está uma saída de exemplo com a extensão instalada com êxito.
connectedmachineindica que a versão 0.7.0 está instalada.[v-hostl]: PS C:\Clusterstorage\lnfrastructure_l\ArcHci> az version { "azure-cli": "2.53.0", "azure-cli-core": "2.53.0", "azure-cli-telemetry": "1.1.0", "extensions": { "akshybrid": "0.1.1", "arcappliance"^ "1.0.2", "connectedk8s": "1.5.4", "connectedmachine": "0.7.0", "customlocation": "0.1.3", "hybridaks": "0.2.4", "k8s-extension": "1.4.5", "stack-hci-vm": "0.1.8" } } [v-hostl]: PS C:\ClusterStorage\Infrastructure_l\ArcHci> ```Execute o seguinte comando para atribuir uma identidade gerenciada pelo sistema à VM.
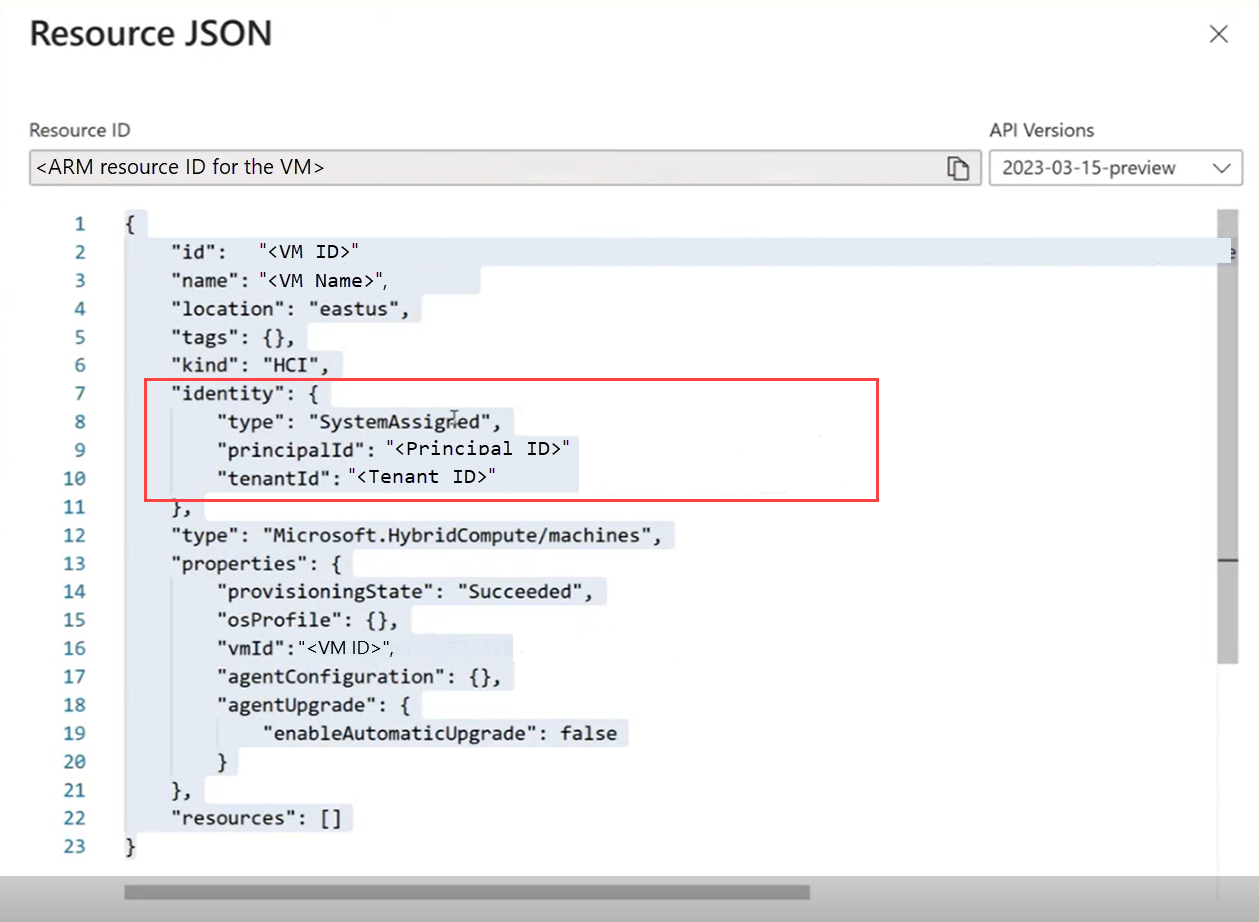
az connectedmachine update --ids "<Resource Manager ID for the VM>" --set identity.type="SystemAssigned"Vá para o portal do Azure e navegue até a página Visão geral . A vista JSON deve indicar que a identidade gerida pelo sistema agora está atribuída à VM.
Falha ao implantar uma imagem de VM de uma conta de armazenamento
Você vê o seguinte erro ao tentar implantar uma imagem de VM de uma conta de armazenamento em seu Azure Local:
Erro:{"code":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=AuthorizationPermissionMismatch) =====\nDescription=, Details: (none)\n","message":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=AuthorizationPermissionMismatch) =====\nDescription=, Details: (none)\n"}
Ou, você vê este erro:
Erro:{"code":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=NoAuthenticationInformation) =====\nDescription=, Details: (none)\n","message":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=NoAuthenticationInformation) =====\nDescription=, Details: (none)\n"}
A falha ocorre porque o usuário que cria a imagem não tem as permissões corretas para acessar a imagem da conta de armazenamento. O usuário deve ter a função de Colaborador de Dados de Blob de Armazenamento na conta de armazenamento que você usa para a imagem. Para obter mais informações, consulte Atribuir funções no Azure para acesso a dados de blobs.
Resolução:
Adicione a função de Colaborador de Dados de Blob de Armazenamento ao usuário que precisa criar uma imagem a partir dessa conta de armazenamento. Depois que a função tiver sido adicionada, tente implantar novamente a imagem.
Você também pode ver o seguinte erro ao tentar implantar uma imagem de VM de uma conta de armazenamento:
Erro:{"code":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=InvalidBlobType) =====\nDescription=The blob type is invalid for this operation.\nRequestId:5e74055f-e01e-0033-66eb-ff9734000000\nTime:2024-09-05T23:32:56.3001852Z, Details: (none)\n","message":"moc-operator galleryimage serviceClient returned an error while reconciling: rpc error: code = Unknown desc = ===== RESPONSE ERROR (ErrorCode=InvalidBlobType) =====\nDescription=The blob type is invalid for this operation.\nRequestId:5e74055f-e01e-0033-66eb-ff9734000000\nTime:2024-09-05T23:32:56.3001852Z, Details: (none)\n","additionalInfo":[{"type":"ErrorInfo","info":{"category":"Uncategorized","recommendedAction":"","troubleshootingURL":""}}]}
Essa falha ocorre porque o tipo de blob não está correto na conta de armazenamento. A imagem deve ser do page blob tipo.
Resolução:
Carregue a imagem na sua conta de armazenamento em page blob format e tente desdobrar a imagem novamente.
Verifique se o usuário tem as permissões corretas e se o blob está no formato correto. Para obter mais informações, consulte Adicionar imagem de VM da conta de Armazenamento do Azure.
Falha ao implantar uma VM Arc
Você vê o seguinte erro ao tentar implantar uma VM do Arc em seu Azure Local:
Erro:{"code":"ConflictingOperation","message":"Unable to process request 'Microsoft.AzureStackHCI/virtualMachineInstances'. There is already a previous running operation for resource '/subscriptions/<subscription ID>/resourceGroups/<Resource group name>/providers/Microsoft.HybridCompute/machines/<VM name>/providers/Microsoft.AzureStackHCI/virtualMachineInstances/default'. Please wait for the previous operation to complete."}
Essa falha ocorre porque o SystemAssigned objeto de identidade gerenciado não está sob o Microsoft.HybridCompute/machines tipo de recurso.
Resolução:
Verifique em seu modelo de implantação se:
O SystemAssigned objeto de identidade gerido está sob o tipo de recurso Microsoft.HybridCompute/machines e não sob o tipo de recurso Microsoft.AzureStackHCI/VirtualMachineInstances.
O modelo de implantação deve corresponder ao modelo de exemplo fornecido. Para obter mais informações, consulte o modelo de exemplo em Criar máquinas virtuais Arc no Azure Local.
Falha ao excluir o caminho de armazenamento
Ao tentar excluir um caminho de armazenamento em sua instância Local do Azure, você pode ver um erro semelhante à seguinte mensagem. Os números e versões dos recursos podem variar no seu cenário.
Erro:"errorMessage" serviceClient returned an error during deletion: The storage container service returned an error during deletion: rpc error: code = Unknown desc = Container is in ACTIVE use by Resources [6:
- linux-cblmariner-0.2.0.10503
- windows-windows2019-0.2.0.10503
- windows-windows2022-0.2.0.10503
].
Remove all the Resources from this container, before trying to delete: In Use: Failed,
Resolução:
As imagens listadas na mensagem de erro diferem das cargas de trabalho típicas, que são representadas como objetos do Azure Resource Manager (ARM) no portal do Azure e na CLI. Esse erro ocorre porque essas imagens são baixadas diretamente no sistema de arquivos, que o Azure não pôde reconhecer.
Siga estas etapas antes de tentar remover um caminho de armazenamento:
- Remova as cargas de trabalho associadas e as imagens presentes no caminho de armazenamento que você deseja excluir. Procure os seguintes prefixos nos nomes das imagens:
linux-cblmariner,windows-windows2019,windows-windows2022,windows_k8s,aks-image-merged,linux-K8s. - Submeta um pedido de suporte no portal do Azure.
A instalação da CLI do Azure não é reconhecida
Se seu ambiente não reconhecer a CLI do Azure depois de instalá-la, execute o seguinte bloco de código para adicionar o caminho de instalação da CLI do Azure ao caminho do ambiente.
if ( -not( $env:PATH -like '*C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\wbin*') ) {
$env:PATH += "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\wbin;"
Write-Host "Updated path $env:PATH"
}