Habilitar o Insights para o Azure Local em escala usando as políticas do Azure
Aplica-se a: Azure Local 2311.2 e posterior
Este documento descreve como habilitar o Insights para sistemas locais do Azure em escala usando as políticas do Azure. Para habilitar o Insights para um único sistema Local do Azure, consulte Monitorar um único sistema Local do Azure com o Insights.
Para obter uma visão geral da Política do Azure, consulte O que é a Política do Azure?
Sobre o uso de políticas do Azure para habilitar o Insights em escala
Para monitorar vários sistemas locais do Azure com o Insights, você precisa habilitar o Insights para cada sistema individualmente. Para simplificar esse processo, você pode usar as políticas do Azure para habilitar automaticamente o Insights no nível da assinatura ou do grupo de recursos. Essas políticas verificam a conformidade dos recursos dentro de seu escopo com base nas regras definidas. Se algum recurso não compatível for encontrado após a atribuição das políticas, você poderá corrigi-los por meio de tarefas de correção.
Esta seção descreve as políticas do Azure a serem usadas para habilitar o Insights em escala. Para cada política, ele também fornece um modelo de definição de política em JSON que você pode usar como está para criar definições de política ou como ponto de partida para personalização adicional.
Política para reparar AMA
Para sistemas locais do Azure registrados antes de novembro de 2023, você precisa reparar o registro de cluster e o Azure Monitor Agent (AMA) antes de configurar o Insights novamente. Para obter detalhes, consulte Solucionar problemas de clusters registrados antes de novembro de 2023.
A política para reparar o AMA executa a seguinte função:
- Remove a chave do Registro, se presente, que determina a ID do recurso para a qual o AMA coleta dados.
Antes de aplicar esta política, tenha em mente o seguinte:
- Esta política aplica-se apenas aos sistemas Azure Local, versão 22H2. Aplique-o antes de quaisquer outras políticas para garantir que o AMA pegue o ID de recurso correto.
- Desinstale o AMA antes de aplicar esta política para definir a ID de recurso correta. Se o AMA não for desinstalado primeiro, os dados podem não aparecer. Para obter mais informações, consulte Desinstalar o AMA.
Aqui está a definição de política em JSON:
{
"mode": "INDEXED",
"policyRule": {
"then": {
"effect": "deployIfNotExists",
"details": {
"type": "Microsoft.GuestConfiguration/guestConfigurationAssignments",
"existenceCondition": {
"allOf": [
{
"field": "Microsoft.GuestConfiguration/guestConfigurationAssignments/complianceStatus",
"equals": "Compliant"
},
{
"field": "Microsoft.GuestConfiguration/guestConfigurationAssignments/parameterHash",
"equals": "[base64(concat('[RepairClusterAMA]RepairClusterAMAInstanceName;Path', '=', parameters('Path'), ',', '[RepairClusterAMA]RepairClusterAMAInstanceName;Content', '=', parameters('Content')))]"
}
]
},
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/088ab73d-1256-47ae-bea9-9de8e7131f31"
],
"deployment": {
"properties": {
"parameters": {
"type": {
"value": "[field('type')]"
},
"location": {
"value": "[field('location')]"
},
"vmName": {
"value": "[field('name')]"
},
"assignmentName": {
"value": "[concat('RepairClusterAMA$pid', uniqueString(policy().assignmentId, policy().definitionReferenceId))]"
},
"Content": {
"value": "[parameters('Content')]"
},
"Path": {
"value": "[parameters('Path')]"
}
},
"mode": "incremental",
"template": {
"parameters": {
"type": {
"type": "string"
},
"location": {
"type": "string"
},
"vmName": {
"type": "string"
},
"assignmentName": {
"type": "string"
},
"Content": {
"type": "string"
},
"Path": {
"type": "string"
}
},
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Compute/virtualMachines/providers/guestConfigurationAssignments",
"properties": {
"guestConfiguration": {
"version": "1.0.0",
"name": "RepairClusterAMA",
"configurationParameter": [
{
"value": "[parameters('Path')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Path"
},
{
"value": "[parameters('Content')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Content"
}
],
"contentHash": "7EA99B10AE79EA5C1456A134441270BC48F5208F3521BFBFDCAE5EF7B6A9D9BD",
"contentUri": "https://guestconfiguration4.blob.core.windows.net/guestconfiguration/RepairClusterAMA.zip",
"contentType": "Custom",
"assignmentType": "ApplyAndAutoCorrect"
}
},
"location": "[parameters('location')]",
"apiVersion": "2018-11-20",
"name": "[concat(parameters('vmName'), '/Microsoft.GuestConfiguration/', parameters('assignmentName'))]",
"condition": "[equals(toLower(parameters('type')), toLower('Microsoft.Compute/virtualMachines'))]"
},
{
"type": "Microsoft.HybridCompute/machines/providers/guestConfigurationAssignments",
"properties": {
"guestConfiguration": {
"version": "1.0.0",
"name": "RepairClusterAMA",
"configurationParameter": [
{
"value": "[parameters('Path')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Path"
},
{
"value": "[parameters('Content')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Content"
}
],
"contentHash": "7EA99B10AE79EA5C1456A134441270BC48F5208F3521BFBFDCAE5EF7B6A9D9BD",
"contentUri": "https://guestconfiguration4.blob.core.windows.net/guestconfiguration/RepairClusterAMA.zip",
"contentType": "Custom",
"assignmentType": "ApplyAndAutoCorrect"
}
},
"location": "[parameters('location')]",
"apiVersion": "2018-11-20",
"name": "[concat(parameters('vmName'), '/Microsoft.GuestConfiguration/', parameters('assignmentName'))]",
"condition": "[equals(toLower(parameters('type')), toLower('Microsoft.HybridCompute/machines'))]"
},
{
"type": "Microsoft.Compute/virtualMachineScaleSets/providers/guestConfigurationAssignments",
"properties": {
"guestConfiguration": {
"version": "1.0.0",
"name": "RepairClusterAMA",
"configurationParameter": [
{
"value": "[parameters('Path')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Path"
},
{
"value": "[parameters('Content')]",
"name": "[RepairClusterAMA]RepairClusterAMAInstanceName;Content"
}
],
"contentHash": "7EA99B10AE79EA5C1456A134441270BC48F5208F3521BFBFDCAE5EF7B6A9D9BD",
"contentUri": "https://guestconfiguration4.blob.core.windows.net/guestconfiguration/RepairClusterAMA.zip",
"contentType": "Custom",
"assignmentType": "ApplyAndAutoCorrect"
}
},
"location": "[parameters('location')]",
"apiVersion": "2018-11-20",
"name": "[concat(parameters('vmName'), '/Microsoft.GuestConfiguration/', parameters('assignmentName'))]",
"condition": "[equals(toLower(parameters('type')), toLower('Microsoft.Compute/virtualMachineScaleSets'))]"
}
],
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#"
}
}
},
"name": "[concat('RepairClusterAMA$pid', uniqueString(policy().assignmentId, policy().definitionReferenceId))]"
}
},
"if": {
"anyOf": [
{
"allOf": [
{
"anyOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachineScaleSets"
}
]
},
{
"field": "tags['aks-managed-orchestrator']",
"exists": "false"
},
{
"field": "tags['aks-managed-poolName']",
"exists": "false"
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"in": [
"esri",
"incredibuild",
"MicrosoftDynamicsAX",
"MicrosoftSharepoint",
"MicrosoftVisualStudio",
"MicrosoftWindowsDesktop",
"MicrosoftWindowsServerHPCPack"
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftWindowsServer"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftSQLServer"
},
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-dsvm"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "dsvm-win*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-ads"
},
{
"field": "Microsoft.Compute/imageOffer",
"in": [
"standard-data-science-vm",
"windows-data-science-vm"
]
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "batch"
},
{
"field": "Microsoft.Compute/imageOffer",
"equals": "rendering-windows2016"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "center-for-internet-security-inc"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "cis-windows-server-201*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "pivotal"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "bosh-windows-server*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "cloud-infrastructure-services"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "ad*"
}
]
},
{
"allOf": [
{
"anyOf": [
{
"field": "Microsoft.Compute/virtualMachines/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachines/storageProfile.osDisk.osType",
"like": "Windows*"
},
{
"field": "Microsoft.Compute/VirtualMachineScaleSets/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachineScaleSets/virtualMachineProfile.storageProfile.osDisk.osType",
"like": "Windows*"
}
]
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imageSKU",
"exists": false
},
{
"allOf": [
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
}
]
}
]
}
]
}
]
},
{
"allOf": [
{
"equals": true,
"value": "[parameters('IncludeArcMachines')]"
},
{
"anyOf": [
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.HybridCompute/machines"
},
{
"field": "Microsoft.HybridCompute/imageOffer",
"like": "windows*"
}
]
},
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.ConnectedVMwarevSphere/virtualMachines"
},
{
"field": "Microsoft.ConnectedVMwarevSphere/virtualMachines/osProfile.osType",
"like": "windows*"
}
]
}
]
}
]
}
]
}
},
"parameters": {
"IncludeArcMachines": {
"allowedValues": [
"true",
"false"
],
"defaultValue": "false",
"metadata": {
"description": "By selecting this option, you agree to be charged monthly per Arc connected machine.",
"displayName": "Include Arc connected machines",
"portalReview": true
},
"type": "String"
},
"Content": {
"defaultValue": "File content XYZ",
"metadata": {
"description": "File content",
"displayName": "Content"
},
"type": "String"
},
"Path": {
"defaultValue": "C:\\DSC\\CreateFileXYZ.txt",
"metadata": {
"description": "Path including file name and extension",
"displayName": "Path"
},
"type": "String"
}
}
}
Política para instalar o AMA
A política para instalar o AMA executa as seguintes funções:
Avalia se os sistemas locais do Azure têm a
AzureMonitoringAgentextensão instalada.Instala o AMA em sistemas que não estão em conformidade com a política por meio de uma tarefa de correção.
Aqui está a definição de política em JSON:
{
"mode": "Indexed",
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.AzureStackHCI/clusters"
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.AzureStackHCI/clusters/arcSettings/extensions",
"name": "[concat(field('name'), '/default/AzureMonitorWindowsAgent')]",
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c"
],
"existenceCondition": {
"field": "Microsoft.AzureStackHCI/clusters/arcSettings/extensions/extensionParameters.type",
"equals": "AzureMonitorWindowsAgent"
},
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"clusterName": {
"type": "string",
"metadata": {
"description": "The name of Cluster."
}
}
},
"resources": [
{
"type": "Microsoft.AzureStackHCI/clusters/arcSettings/extensions",
"apiVersion": "2023-08-01",
"name": "[concat(parameters('clusterName'), '/default/AzureMonitorWindowsAgent')]",
"properties": {
"extensionParameters": {
"publisher": "Microsoft.Azure.Monitor",
"type": "AzureMonitorWindowsAgent",
"autoUpgradeMinorVersion": false,
"enableAutomaticUpgrade": false
}
}
}
]
},
"parameters": {
"clusterName": {
"value": "[field('Name')]"
}
}
}
}
}
}
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"DeployIfNotExists",
"Disabled"
],
"defaultValue": "DeployIfNotExists"
}
}
}
Política para configurar a associação DCR
Esta política é aplicada a cada nó no sistema Local do Azure e executa a seguinte função:
Usa a
dataCollectionResourceIdentrada como e associa a Regra de Coleta de Dados (DCR) a cada nó.Nota
Esta política não cria o Ponto de Extremidade de Coleta de Dados (DCE). Se você estiver usando links privados, deverá criar DCE para garantir que haja dados disponíveis no Insights. Para obter mais informações, consulte Habilitar o isolamento de rede para o Azure Monitor Agent usando o Private Link.
Aqui está a definição de política em JSON:
{
"mode": "INDEXED",
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.HybridCompute/machines"
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.Insights/dataCollectionRuleAssociations",
"name": "[concat(field('name'), '-dataCollectionRuleAssociations')]",
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c"
],
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"machineName": {
"type": "string",
"metadata": {
"description": "The name of the machine."
}
},
"dataCollectionResourceId": {
"type": "string",
"metadata": {
"description": "Resource Id of the DCR"
}
}
},
"resources": [
{
"type": "Microsoft.Insights/dataCollectionRuleAssociations",
"apiVersion": "2022-06-01",
"name": "[concat(parameters('machineName'), '-dataCollectionRuleAssociations')]",
"scope": "[format('Microsoft.HybridCompute/machines/{0}', parameters('machineName'))]",
"properties": {
"description": "Association of data collection rule. Deleting this association will break the data collection for this machine",
"dataCollectionRuleId": "[parameters('dataCollectionResourceId')]"
}
}
]
},
"parameters": {
"machineName": {
"value": "[field('Name')]"
},
"dataCollectionResourceId": {
"value": "[parameters('dcrResourceId')]"
}
}
}
}
}
}
},
"parameters": { "effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"DeployIfNotExists",
"Disabled"
],
"defaultValue": "DeployIfNotExists"
},
"dcrResourceId": {
"type": "String",
"metadata": {
"displayName": "dcrResourceId",
"description": "Resource Id of the DCR"
}
}
}
}
Habilitar o Insights em escala usando políticas do Azure
Esta seção descreve como habilitar o Insights for Azure Local em escala usando as políticas do Azure.
Pré-requisitos
Antes de habilitar o Insights for Azure Local em escala usando as políticas do Azure, preencha os seguintes pré-requisitos:
- Você deve ter acesso aos sistemas locais do Azure implantados e registrados nos quais habilitará o Insights.
- Você deve ter a identidade gerenciada para os recursos do Azure habilitada. Para obter mais informações, consulte Gerenciamento avançado habilitado.
- Você deve ter a função de Colaborador de Recurso de Configuração de Convidado em sua assinatura do Azure.
- (Apenas para sistemas Azure Local, versão 22H2) Você deve desinstalar o AMA antes de começar a aplicar as políticas do Azure.
Ordem de aplicação da política
Para habilitar o Insights em escala para sistemas locais do Azure, aplique as políticas do Azure na seguinte ordem:
Reparar AMA (apenas para sistemas Azure Local, versão 22H2):
- Se você estiver usando o Azure Stack HCI, sistemas versão 22H2, comece aplicando a política para reparar a AMA. Esta etapa não é necessária para o Azure Local 2311.2 e sistemas posteriores.
- Para obter o modelo de definição de política, consulte Política para reparar AMA.
Instale o AMA:
- Aplique a política para instalar o AMA.
- Para obter o modelo de definição de política, consulte Política para instalar o AMA.
Configure a associação DCR.
- Aplique a política para configurar a associação DCR.
- Para obter o modelo de definição de política, consulte Política para configurar a associação DCR.
Fluxo de trabalho para aplicar políticas para habilitar o Insights em escala
Siga estas etapas para cada política para habilitar o Insights em escala:
- Criar uma definição de política. Defina as regras e condições de conformidade usando o modelo de definição de política. Consulte Criar uma definição de política.
- Crie uma atribuição de política. Defina o escopo da política, exclusões, se houver, e parâmetros para aplicação. Use a definição de política definida na etapa anterior. Consulte Criar uma atribuição de política.
- Veja o status de conformidade. Monitore o status de conformidade da atribuição de política. Verifique se há recursos não compatíveis. Consulte Exibir status de conformidade.
- Corrija recursos não compatíveis. Crie tarefas de correção para corrigir recursos não compatíveis. Consulte Corrigir recursos não compatíveis.
Criar uma definição de política
Para criar uma definição de política, siga estas etapas:
No portal do Azure, navegue para o serviço Azure Policy.
Na seção Criação, selecione Definições.
Selecione + Definição de política para criar uma nova definição de política.
Na página Definição de política , especifique os seguintes valores:
Campo Ação Localização da definição Selecione as reticências ( ...) para especificar onde o recurso de política está localizado. No painel Local de definição , selecione a assinatura do Azure e, em seguida, selecione Selecionar.Nome Especifique um nome amigável para a definição de política. Opcionalmente, pode especificar uma descrição e uma categoria. REGRA DE POLÍTICA A caixa de edição JSON é preenchida previamente com um modelo de definição de política. Substitua este modelo pelo modelo de definição de política que você deseja aplicar. Para obter os modelos de definição para políticas do Insights no formato JSON, consulte a seção Sobre o uso de políticas do Azure para habilitar o Insights em escala . Definições de função Este campo é apresentado depois de copiar e colar a definição de política no campo REGRA DE POLÍTICA. Selecione a função Colaborador de Recurso de Configuração de Convidado na lista. Selecione Guardar.
Você recebe uma notificação de que a criação da definição de política foi bem-sucedida e a página de definição de política é exibida. Agora você pode continuar a criar a atribuição de política.
Criar uma atribuição de política
Em seguida, você cria uma atribuição de política e atribui a definição de política no nível da assinatura ou do grupo de recursos. Para obter mais informações sobre atribuição de política, consulte Estrutura de atribuição de política do Azure.
Para criar uma atribuição de política, siga estas etapas:
Sobre a Política | Página Definições para a definição de política que você criou na etapa anterior, selecione Atribuir política.
Na guia > básica, especifique os seguintes valores:
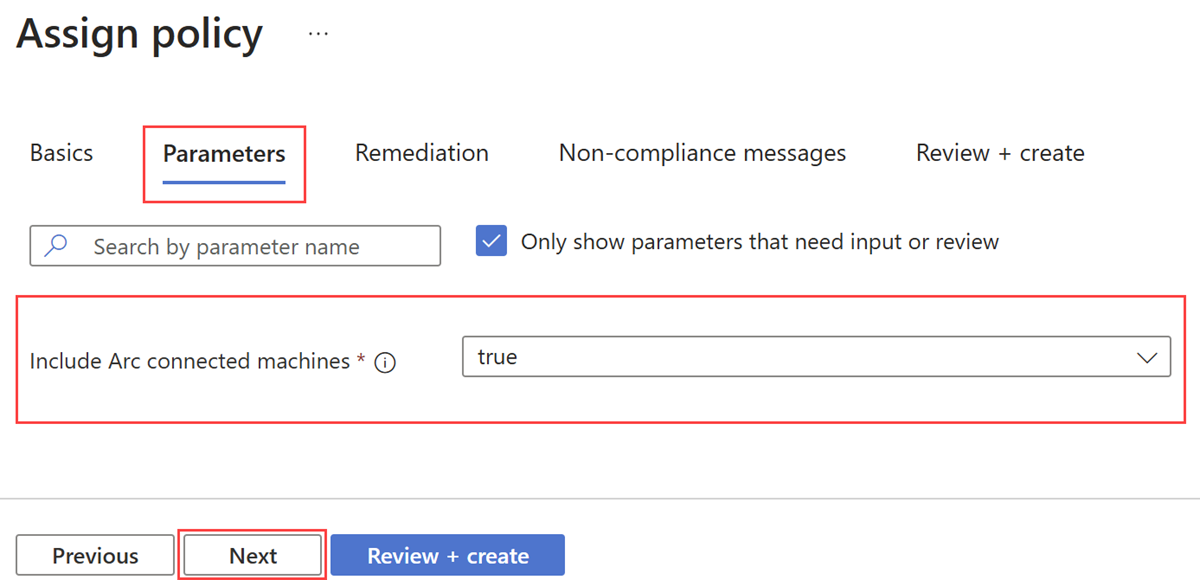
Campo Ação Scope Este campo é preenchido previamente com o escopo que você definiu durante a criação da definição de política. Se quiser alterar o escopo da atribuição de políticas, você pode usar as reticências ( ...) e, em seguida, selecionar uma assinatura e, opcionalmente, um grupo de recursos. Em seguida, selecione Selecionar para aplicar o escopo.Exclusões Opcional. Use as reticências ( ...) para selecionar os recursos a serem excluídos da atribuição de política.Definição de política Este campo é preenchido previamente com o nome da definição de política criado na etapa Criar uma definição de política. Nome da atribuição Este campo é preenchido previamente com o nome da definição de política selecionada. Você pode alterá-lo se necessário. Imposição de políticas O padrão é Enabled. Para obter mais informações, consulte modo de imposição. Selecione Avançar para exibir a guia Parâmetros. Se a definição de política selecionada na guia Noções básicas incluir parâmetros, eles aparecerão na guia Parâmetros.
Por exemplo, a política para reparar o AMA mostra o parâmetro Include Arc connected machines . Selecione True para incluir máquinas conectadas Arc na atribuição de política.
Selecione Avançar para exibir a guia Correção . Nenhuma ação é necessária nesta guia. Os modelos de definição de política suportam o efeito deployIfNotExists , de modo que os recursos que não estão em conformidade com a regra de política são corrigidos automaticamente. Além disso, observe que o parâmetro Create a Managed Identity é selecionado por padrão, já que os modelos de definição de política usam o efeito deployIfNotExists .
Selecione Rever + criar para rever a atribuição.
Selecione Criar para criar a atribuição.
Você recebe notificações de que a atribuição de função e as criações de atribuição de política foram bem-sucedidas. Depois que a atribuição é criada, o mecanismo de Política do Azure identifica todos os sistemas locais do Azure localizados no escopo e aplica a configuração de política a cada sistema. Normalmente, leva de 5 a 15 minutos para que a atribuição de política entre em vigor.
Exibir status de conformidade
Depois de criar a atribuição de política, você pode monitorar a conformidade dos recursos em Status de conformidade e correção em Correção na home page da Política do Azure. O estado de conformidade de uma nova atribuição de política leva alguns minutos para se tornar ativo e fornecer resultados sobre o estado da política.
Para exibir o status de conformidade da política, siga estas etapas:
No portal do Azure, navegue para o serviço Azure Policy.
Selecione Conformidade.
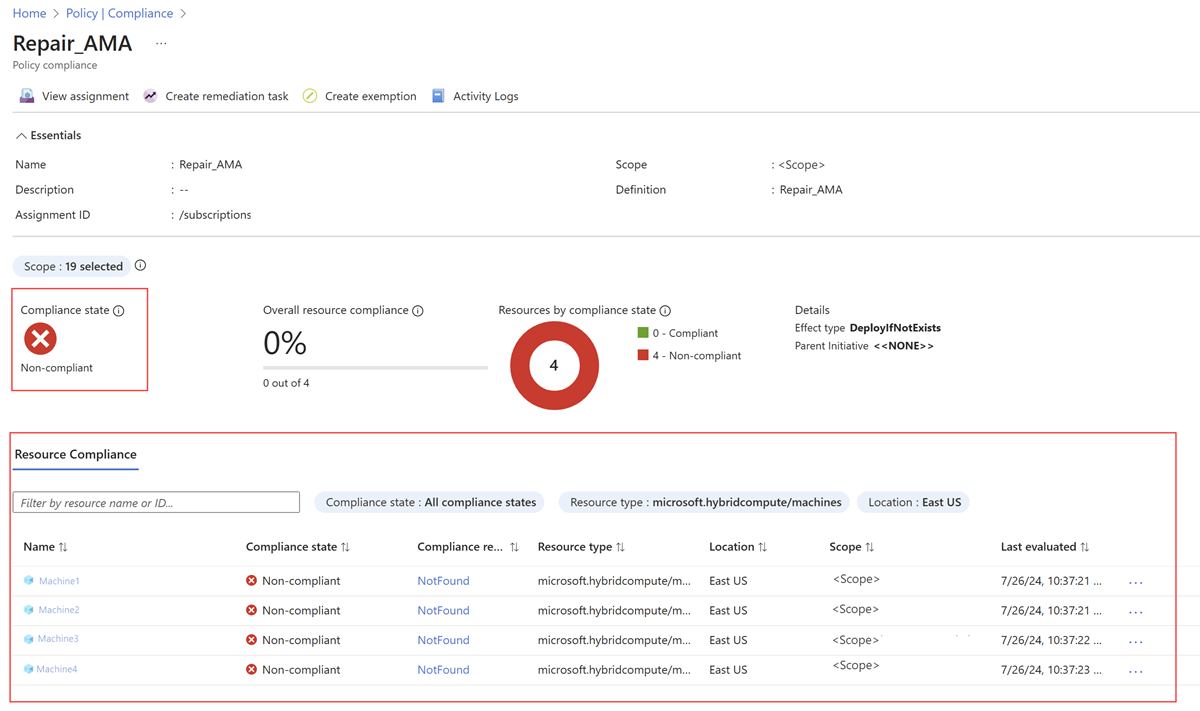
Filtre os resultados para o nome da atribuição de política que você criou na etapa Criar uma atribuição de política. A coluna Estado de conformidade exibe o estado de conformidade como Compatível ou Não compatível.
Selecione o nome da atribuição de política para exibir o status de Conformidade de Recursos . Por exemplo, o relatório de conformidade para a política AMA de reparo mostra os nós que precisam ser reparados:
Depois de saber quais recursos não estão em conformidade, você pode criar a tarefa de correção para colocá-los em conformidade.
Remediar recursos não conformes
Para corrigir recursos não compatíveis e acompanhar o progresso da tarefa de correção, siga estas etapas:
No portal do Azure, navegue para o serviço Azure Policy.
Selecione Remediação.
A página Correção exibe a lista de políticas atribuídas que têm recursos não compatíveis. Filtre os resultados para o nome da atribuição de política que você criou na etapa Criar uma atribuição de política.
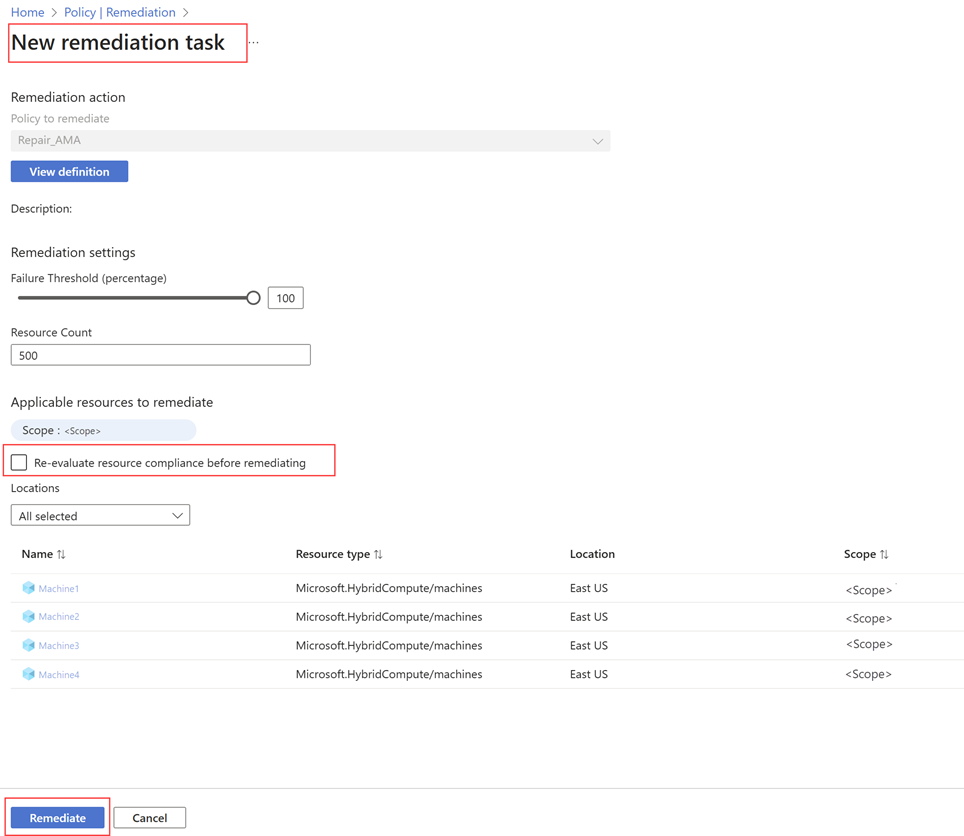
Selecione o link Definição de política.
A página Nova tarefa de correção exibe os recursos que precisam de correção. Marque a caixa de seleção Reavaliar a conformidade dos recursos antes de corrigir e, em seguida, selecione Corrigir.
Você recebe uma notificação de que uma tarefa de correção foi criada e é direcionado para a guia Tarefas de correção. Esta guia mostra o status de diferentes tarefas de correção. O que você criou pode estar no estado Avaliando ou Em andamento .
Quando a correção estiver concluída, o estado mudará para Concluído.
Para obter mais informações sobre correção, consulte Corrigir recursos não compatíveis com a Política do Azure.