O que é Datacenter Firewall?
Aplica-se a: Azure Local 2311.2 e posterior; Windows Server 2022, Windows Server 2019, Windows Server 2016
O Datacenter Firewall é uma camada de rede, 5-tupla (protocolo, números de porta de origem e destino, endereços IP de origem e destino), um firewall stateful e multi-inquilino de Rede Definida por Software (SDN). O Datacenter Firewall protege os fluxos de tráfego leste-oeste e norte-sul através da camada de rede de redes virtuais e redes VLAN tradicionais.
Como funciona o Datacenter Firewall
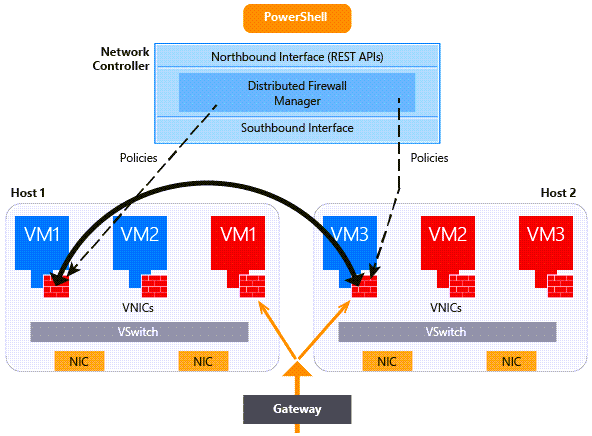
Você habilita e configura o Datacenter Firewall criando NSGs (grupos de segurança de rede) que são aplicados a uma sub-rede ou interface de rede. As políticas de firewall são aplicadas na porta vSwitch de cada máquina virtual (VM) do inquilino. As políticas são enviadas por push através do portal do locatário e o Controlador de Rede as distribui para todos os hosts aplicáveis.
Os administradores de locatários podem instalar e configurar políticas de firewall para ajudar a proteger suas redes contra tráfego indesejado originado de redes da Internet e intranet.
O administrador do provedor de serviços ou o administrador do locatário pode gerenciar as políticas do Firewall do Datacenter por meio do Controlador de Rede e das APIs para o norte. Você também pode configurar e gerenciar políticas de Firewall do Datacenter usando o Windows Admin Center.
Vantagens para os fornecedores de serviços na nuvem
O Datacenter Firewall oferece as seguintes vantagens para os provedores de serviços em nuvem:
Uma solução de firewall baseada em software altamente escalável, gerenciável e diagnosticável que pode ser oferecida aos locatários
Liberdade para mover VMs de locatário para hosts de computação diferentes sem quebrar as políticas de firewall do locatário
Implantado como um firewall do agente de host da porta vSwitch
As VMs do inquilino recebem as políticas atribuídas ao firewall do agente de host do vSwitch
As regras de firewall são configuradas em cada porta vSwitch, independentemente do host real que executa a VM
Oferece proteção às VMs do inquilino, independentemente do sistema operacional convidado do inquilino
Vantagens para os inquilinos
O Datacenter Firewall oferece as seguintes vantagens para os locatários:
Capacidade de definir regras de firewall para ajudar a proteger cargas de trabalho voltadas para a Internet e cargas de trabalho internas em redes
Capacidade de definir regras de firewall para ajudar a proteger o tráfego entre VMs na mesma sub-rede de Camada 2 (L2) e entre VMs em sub-redes L2 diferentes
Capacidade de definir regras de firewall para ajudar a proteger e isolar o tráfego de rede entre redes locais do locatário e suas redes virtuais no provedor de serviços
Capacidade de aplicar políticas de firewall a redes VLAN tradicionais e redes virtuais baseadas em sobreposição
Próximos passos
Para obter informações relacionadas, consulte também: