Exploring Notable Events in Security Incidents
Azure Security Center is able to identify threats that may compromise your system in different phases of the kill chain. Security Center will use different detection capabilities prior to trigger an alert, and the content of this alert can also vary according to its type. If Security Center identifies that there is a correlation between these alerts, it creates a Security Incident. A Security Incident will appear under the Security Alerts dashboard with a different icon (fusion icon): 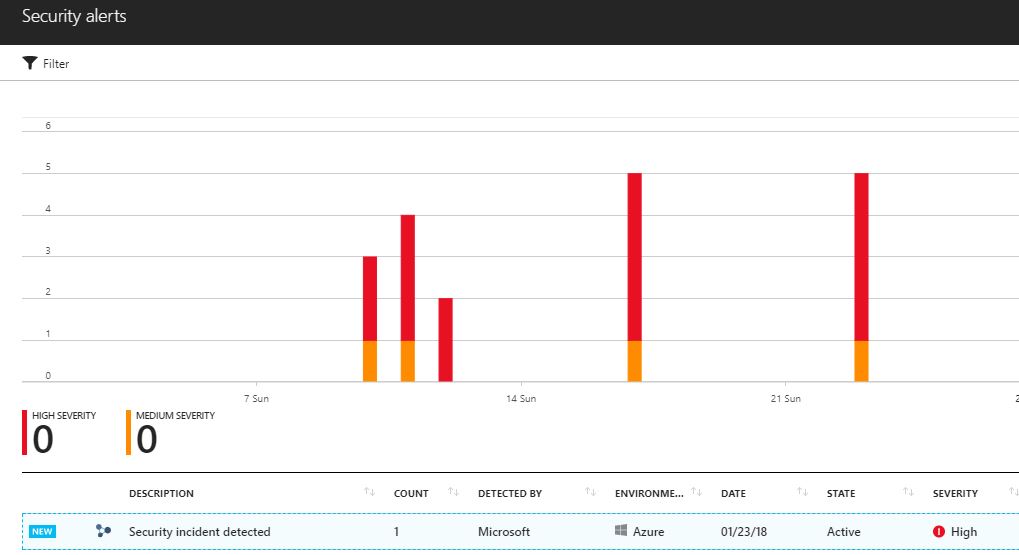
When you click on this Security Incident, it will open a page that contains all alerts that are part of this Incident. In some scenarios, Security Center may also include a contextual information (or notable event), that is located in the bottom of the page, as shown below: 
In this case, this notable event tells me that the PsExec tool was used against the ASCBOOKSRV2012, but it doesn’t tell me the source, as shown below: 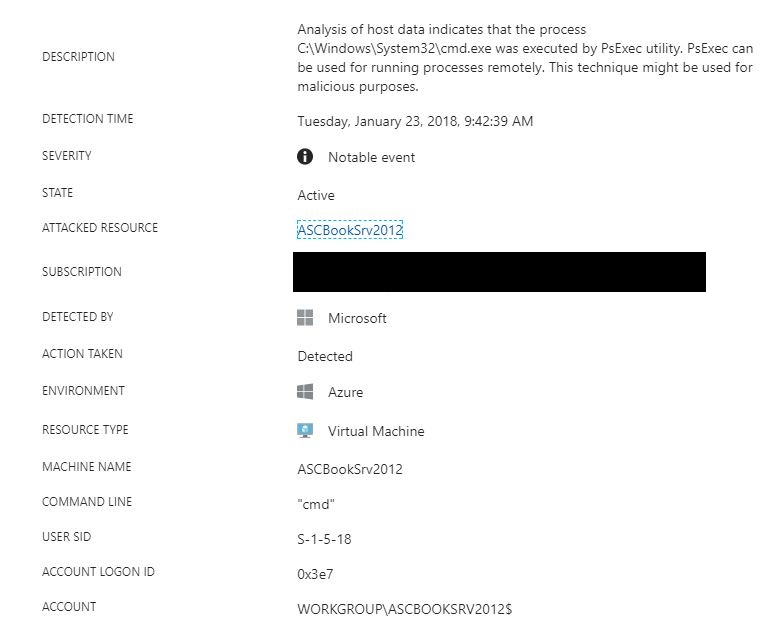
While this a valuable information, you still need to understand which machine initiated this operation, and for that you can use the Search capability in Security Center. One example of a search query that you can use for this scenario is: SecurityEvent | where CommandLine contains "psexec" . In this case the result was: 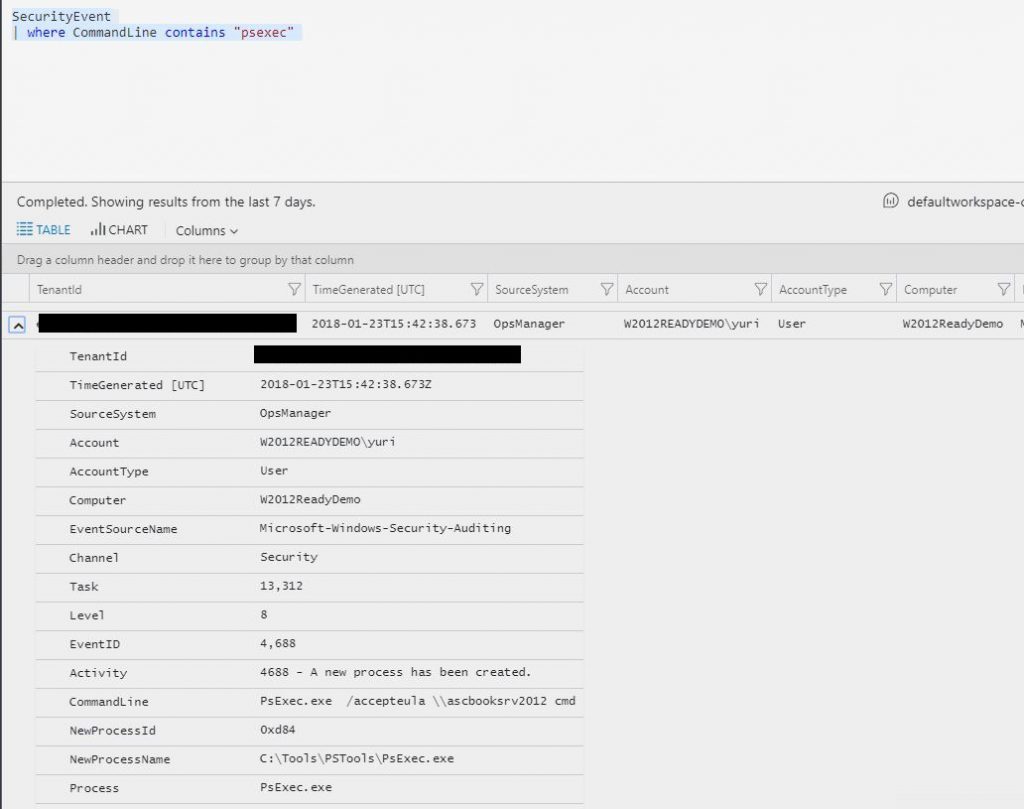
OK, now we have the end-to-end result (source and destination), in other words, now we know that the execution came from W2012ReadyDemo. With this information we can investigate this machine to understand what’s going on.  Pre-order the upcoming Azure Security Center book here.
Pre-order the upcoming Azure Security Center book here.