Auditing Changes in Azure Security Center Configuration
Azure Security Center uses Role-Based Access Control (RBAC), which provides built-in roles that can be assigned to users, groups, and services in Azure. When planning to adopt Security Center, make sure to read the Permissions in Azure Security Center article for more information about the key roles and the actions that these roles can perform.
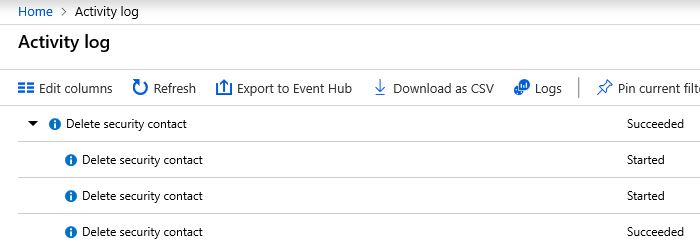
A question that comes up very often is: how can I check who changed my Security Center configuration? Let’s use a very simple example: I noticed that my security contact information only has one email, and used to be three. When that happen? To investigate when this change took place, you can use Azure Activity Log. For this particular case, you should see an entry similar to the one below:
If you click in the Delete security contact action that succeeded, you will have access to the JSON content, and there you will be able to see more info regarding who performed this action and when it was done.
The use of Activity Log can be also very useful to see who made changes in the Azure Security Center Security Policy. Let’s use as an example the policy below. This policy in the past was configured as AuditIfNotExists and now is showing as disabled:
Again, you want to understand: when this change was done and who did it. Using Azure Activity Log, looks for the operation below:
Note: if you have a lot of activities, you should add a filter where Operation is Create policy assignment.
Open the JSON for this operation, and there investigate the requestbody, and you will see that the MFA policy that was changed to disabled is there: