Shielded Virtual Machines - Protect your workloads
When Microsoft launched Windows Server 2016, there were many new features and technologies released into the community. One of the three primary design criteria for this release was Security. Microsoft adopt an "assume breach" posture for security.
One of the three key security principles is securing the infrastructure. You can read all about Windows Server 2016 security in the Microsoft Trust Center 
It would be fair to say that a large proportion of the workloads running in on-premises datacentres are virtualized, that is running on either Hyper-V or VMWare hypervisors (other hypervisors are available). This allows a single physical server to run many different virtual servers, saving space, energy and cost.
A little known fact is that the vast majority of these workloads are accessible to the administrators of the Hypervisor, when in most cases they have no need to see or use the VMs running on their hardware.
Even if you have the privileges necessary to back up a Hyper-V or VMWare host, you can actually gain access to the VMs running on them. In most businesses this does not impact upon security or data integrity, however, if you rare responsible for hosting VMs for other departments with higher security needs or for external customers then this can be a major flaw in the security of those workloads.
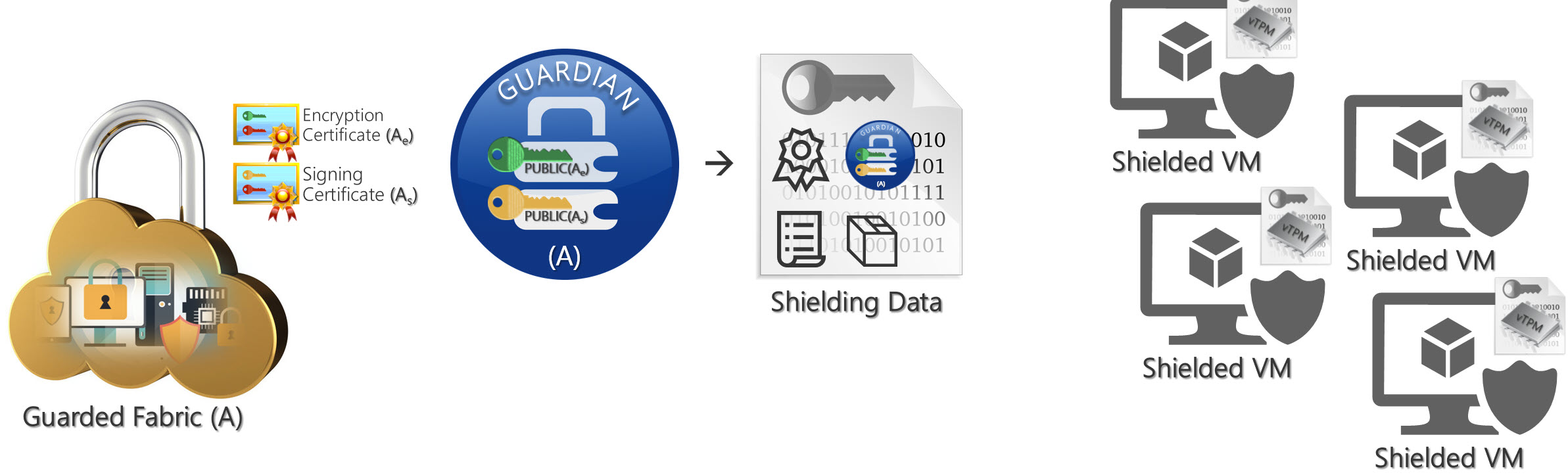
Microsoft have produced a feature set that allows for a Guarded Fabric, preventing fabric administrators from interfering with VMs running on their hosts. There are several ways of achieving this to varying degrees of cost and security, all of which are outside the scope of this introductory post.
In short to run Shielded VMs on a Hyper-V host, you need to buy the Datacenter edition of Windows Server 2016. This host can then connect to a Host Guardian Service (another new server role in Windows Server 2016). The Host Guardian service can be installed on a Standard edition server, reducing the cost of licensing this solution. It is best practice to have a highly available solution for the host guardian service to prevent all of your shielded workloads from becoming inaccessible if the host guardian service should fail.
The effect of deploying this solution is immediate and complete.
- The VM can only be started on a guarded host.
- The host must be healthy and uncompromised
- The VM is then secure from tampering (all disks run BitLocker drive encryption)
- The only access to the VM is through a secure remote session with correct credentials (unknown to the host administrator)
- All live migration traffic is encrypted
- All memory dumps in the event of a crash are encrypted
- Hyper-V manager cannot be used to access the VM
Why not take a look at this Microsoft Mechanics Video to see it in action.
[embed]https://www.youtube.com/embed/Vp5E1-4Ks8E[/embed]